docker-compose安装harbor
目录
Harbor 安装环境说明
获取安装包(离线安装方式)
安装harbor
用docker-compose查看Harbor容器的运行状态
Harbor访问测试
上传镜像到Harbor服务器
Harbor配置HTTPS
浏览器访问Harbor,通过HTTPS协议访问
通过Docker命令来访问
一、Harbor 安装环境说明
Linux:CentOS Linux release 7.9.2009 (Core)
docker :20.10.17-3.el7
docker-compose :docker-compose version 1.29.1, build c34c88b2
harbor:2.3.4
获取安装包(离线安装方式)
Releases · goharbor/harbor · GitHub
https://github.com/goharbor/harbor/releases/download/v2.3.4/harbor-offline-installer-v2.3.4.tgz
安装harbor
wget https://github.com/goharbor/harbor/releases/download/v2.3.4/harbor-offline-installer-v2.3.4.tgz
tar xf harbor-offline-installer-v2.3.4.tgz -C /usr/local/
cd /usr/local/harbor
#修改配置文件
[root@localhost harbor]# ll
总用量 596292
-rw-r--r-- 1 root root 3361 11月 9 2021 common.sh
-rw-r--r-- 1 root root 610560420 11月 9 2021 harbor.v2.3.4.tar.gz
-rw-r--r-- 1 root root 7844 6月 13 12:31 harbor.yml
-rw-r--r-- 1 root root 7840 11月 9 2021 harbor.yml.tmpl
-rwxr-xr-x 1 root root 2500 11月 9 2021 install.sh
-rw-r--r-- 1 root root 11347 11月 9 2021 LICENSE
-rwxr-xr-x 1 root root 1881 11月 9 2021 prepare
cp harbor.yml.tmpl harbor.yml
#修改hostname、harbor登录密码、关闭https。
vim harbor.yml
hostname: www.myharbor.com
harbor_admin_password: harbor12345
#https:
# https port for harbor, default is 443
# port: 443
# The path of cert and key files for nginx
# certificate: /your/certificate/path
# private_key: /your/private/key/path
data_volume: /data #这个路径是宿主机的路径,根据实际情况修改成空间大的地方
完成以上操作后,保存退出
#执行安装程序,只安装harbor
./install.sh (前提条件:docker需要启动)
# 除了安装harbor外,还安装公正服务 notary 以及漏洞扫描器 trivy,
./install.sh --with-notary --with-trivy --with-chartmuseum
[root@localhost harbor]# ll
总用量 596300
drwxr-xr-x 3 root root 20 6月 13 12:34 common
-rw-r--r-- 1 root root 3361 11月 9 2021 common.sh
-rw-r--r-- 1 root root 5996 6月 13 12:34 docker-compose.yml
-rw-r--r-- 1 root root 610560420 11月 9 2021 harbor.v2.3.4.tar.gz
-rw-r--r-- 1 root root 7844 6月 13 12:31 harbor.yml
-rw-r--r-- 1 root root 7840 11月 9 2021 harbor.yml.tmpl
-rwxr-xr-x 1 root root 2500 11月 9 2021 install.sh
-rw-r--r-- 1 root root 11347 11月 9 2021 LICENSE
-rwxr-xr-x 1 root root 1881 11月 9 2021 prepare
这时候已经安装完成了!
用docker-compose查看Harbor容器的运行状态
[root@localhost harbor]# docker-compose ps
Name Command State Ports
--------------------------------------------------------------------------------------------------------
harbor-core /harbor/entrypoint.sh Up (healthy)
harbor-db /docker-entrypoint.sh 96 13 Up (healthy)
harbor-jobservice /harbor/entrypoint.sh Up (healthy)
harbor-log /bin/sh -c /usr/local/bin/ ... Up (healthy) 127.0.0.1:1514->10514/tcp
harbor-portal nginx -g daemon off; Up (healthy)
nginx nginx -g daemon off; Up (healthy) 0.0.0.0:80->8080/tcp,:::80->8080/tcp
redis redis-server /etc/redis.conf Up (healthy)
registry /home/harbor/entrypoint.sh Up (healthy)
registryctl /home/harbor/start.sh Up (healthy)
docker-compose基本命令
# 启动Harbor容器
docker-compose start
# 停止Harbor容器
docker-compose stop
# 暂停Harbor容器
docker-compose pause
# 继续运行Harbor容器
docker-compose unpause
# 重启Harbor容器
docker-compose restart
# 停止并删除Harbor容器,加上-v参数可以同时移除挂载在容器上的目录
docker-compose down
# 创建并启动Harbo容器,参数“-d”表示后台运行命令
docker-compose up -d
Harbor访问测试
浏览器输入以下地址或者域名访问Harbor的Web界面,账号密码:admin/harbor12345
本机设置hosts解析
创建用户账号并测试上传镜像
创建test用户,新建项目mytest
test:Test123456
在该项目中添加成员:test,开发者角色
在docker客户端机器上设置/etc/docker/daemon.json文件,指向harbor服务器地址
修改为http方式访问(非加密方式)
"insecure-registries":["www.myharbor.com"]
{
"registry-mirrors": ["https://y9lmbx5j.mirror.aliyuncs.com"],
"log-driver":"json-file",
"log-opts":{
"max-size" :"50m",
"max-file":"1"
},
"insecure-registries":["www.myharbor.com"]
}
# 启动harbor后再修改docker配置文件添加日志,重启harbor会报错,可以在创建harbor之前,修改docker配置文件添加日志
[root@localhost harbor]# docker-compose restart
Restarting harbor-jobservice ... done
Restarting nginx ... done
Restarting harbor-core ... error
Restarting redis ... done
Restarting harbor-db ... done
Restarting registry ... error
Restarting harbor-portal ... done
Restarting registryctl ... error
Restarting harbor-log ... done
ERROR: for registry Cannot restart container 784741e36027bf192a4fcd7f55a87c3c46a5edb2d260bbe6c99b1539667e4b77: failed to initialize logging driver: dial tcp [::1]:1514: connect: connection refused
ERROR: for registryctl Cannot restart container 1e0e79c308e72ea81a24fa3cdf8eeb38722d5fa59a9115d9ca95c37f29a7417d: failed to initialize logging driver: dial tcp [::1]:1514: connect: connection refused
ERROR: for harbor-core Cannot restart container f447ea4319f63e8991efd34c6c0cff0b477321897ed8706e9dcd66ab8e2fa281: failed to initialize logging driver: dial tcp [::1]:1514: connect: connection refused
上传镜像到Harbor服务器
#打标签
docker tag busybox:latest www.myharbor.com/mytest/busybox:v0.1
#登录Harbor服务器
docker login www.myharbor.com
#输入我们在harbor新创建的用户名密码进行登录
#上传镜像
# docker push www.myharbor.com/mytest/busybox:v0.1
The push refers to repository [www.myharbor.com/mytest/busybox]
01fd6df81c8e: Pushed
v0.1: digest: sha256:62ffc2ed7554e4c6d360bce40bbcf196573dd27c4ce080641a2c59867e732dee size: 527
在Harbor上可以看到我们上传的镜像
Harbor配置HTTPS
生成TSL证书
# 创建存放证书的临时目录
mkdir -p /data/harbor/cert
cd /data/harbor/cert
# 创建自签名根证书
openssl genrsa -out ca.key 4096
openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=www.myharbor.com" -key ca.key -out ca.crt
# 查看创建的证书
ca.crt ca.key
# 产生证书签名请求
openssl genrsa -out www.myharbor.com.key 4096
openssl req -sha512 -new -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=www.myharbor.com" -key www.myharbor.com.key -out www.myharbor.com.csr
# 查看证书
# ll
总用量 16
-rw-r--r-- 1 root root 2041 6月 13 12:53 ca.crt
-rw-r--r-- 1 root root 3243 6月 13 12:53 ca.key
-rw-r--r-- 1 root root 1712 6月 13 12:54 www.myharbor.com.csr
-rw-r--r-- 1 root root 3247 6月 13 12:54 www.myharbor.com.key
# 为Registry主机产生证书
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=www.myharbor.com
DNS.2=localhost
EOF
openssl x509 -req -sha512 -days 3650 -extfile v3.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in www.myharbor.com.csr -out www.myharbor.com.crt
openssl x509 -inform PEM -in www.myharbor.com.crt -out www.myharbor.com..cert
# 查看证书
# ll
总用量 32
-rw-r--r-- 1 root root 2041 6月 13 12:53 ca.crt
-rw-r--r-- 1 root root 3243 6月 13 12:53 ca.key
-rw-r--r-- 1 root root 17 6月 13 12:55 ca.srl
-rw-r--r-- 1 root root 251 6月 13 12:55 v3.ext
-rw-r--r-- 1 root root 2094 6月 13 12:55 www.myharbor.com..cert
-rw-r--r-- 1 root root 2094 6月 13 12:55 www.myharbor.com.crt
-rw-r--r-- 1 root root 1712 6月 13 12:54 www.myharbor.com.csr
-rw-r--r-- 1 root root 3247 6月 13 12:54 www.myharbor.com.key
# 创建Harbor的证书目录
mkdir -p /data/harbor/harbor-cert
# 拷贝harbor-registry证书到Harbor的证书目录
cp www.myharbor.com.crt /data/harbor/harbor-cert
cp www.myharbor.com.key /data/harbor/harbor-cert
# 进入Harbor的安装目录
cd /usr/local/harbor
# 停止并删除Harbor容器,加上-v参数可以同时移除挂载在容器上的目录
docker-compose down
# 修改harbor.yml配置文件
## 打开https配置
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /data/harbor/harbor-cert/www.myharbor.com.crt
private_key: /data/harbor/harbor-cert/www.myharbor.com.key
# 重新生成配置文件
./prepare
# 让Docker客户端默认使用Https协议访问Registry,需要去掉“insecure-registries”相关配置项
# 查看daemon.json文件中是否有"insecure-registries":["harbor.test.com"],如果有则将其删除掉
# 重新加载Docker的配置文件
systemctl daemon-reload
# 重启Docker
systemctl restart docker
# 创建并启动Harbor容器
docker-compose up -d
# docker-compose ps
Name Command State Ports
---------------------------------------------------------------------------------------------------------------
chartmuseum ./docker-entrypoint.sh Up (healthy)
harbor-core /harbor/entrypoint.sh Up (healthy)
harbor-db /docker-entrypoint.sh 96 13 Up (healthy)
harbor-jobservice /harbor/entrypoint.sh Up (healthy)
harbor-log /bin/sh -c /usr/local/bin/ ... Up (healthy) 127.0.0.1:1514->10514/tcp
harbor-portal nginx -g daemon off; Up (healthy)
nginx nginx -g daemon off; Up (healthy) 0.0.0.0:80->8080/tcp, 0.0.0.0:443->8443/tcp
redis redis-server /etc/redis.conf Up (healthy)
registry /home/harbor/entrypoint.sh Up (healthy)
registryctl /home/harbor/start.sh Up (healthy)
trivy-adapter /home/scanner/entrypoint.sh Up (healthy)
问题:原先harbor.yml文件中使用的端口是80,现在把80端口给注释掉,使用443端口了,但是harbor程序还在监听80端口,原因是使用的docker-compose.yml中nginx容器中有个如下的配置:
ports:
- 80:8080
- 443:8443
把80端口的注释掉,然后重启,就只监听443端口了
docker-compose down
docker-compose up -d
# docker-compose ps
Name Command State Ports
---------------------------------------------------------------------------------------------
chartmuseum ./docker-entrypoint.sh Up (healthy)
harbor-core /harbor/entrypoint.sh Up (healthy)
harbor-db /docker-entrypoint.sh 96 13 Up (healthy)
harbor-jobservice /harbor/entrypoint.sh Up (healthy)
harbor-log /bin/sh -c /usr/local/bin/ ... Up (healthy) 127.0.0.1:1514->10514/tcp
harbor-portal nginx -g daemon off; Up (healthy)
nginx nginx -g daemon off; Up (healthy) 0.0.0.0:443->8443/tcp
redis redis-server /etc/redis.conf Up (healthy)
registry /home/harbor/entrypoint.sh Up (healthy)
registryctl /home/harbor/start.sh Up (healthy)
trivy-adapter /home/scanner/entrypoint.sh Up (healthy)
浏览器访问Harbor,通过HTTPS协议访问
通过Docker命令来访问
# 在harbor主机或内网其他机器上
mkdir -p /etc/docker/certs.d/www.myharbor.com
scp ca.crt root@yzg01.com:///etc/docker/certs.d/www.myharbor.com/
# 实践操作:只需要ca.crt文件就行了
#scp www.myharbor.com.cert root@yzg01.com:///etc/docker/certs.d/www.myharbor.com/
#scp www.myharbor.com.key root@yzg01.com:///etc/docker/certs.d/www.myharbor.com/
# 无需重启docker即可生效
docker login www.myharbor.com
Authenticating with existing credentials...
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
docker tag busybox:latest www.myharbor.com/mytest/busybox:v0.2
docker push www.myharbor.com/mytest/busybox:v0.2
The push refers to repository [www.myharbor.com/mytest/busybox]
01fd6df81c8e: Layer already exists
v0.2: digest: sha256:62ffc2ed7554e4c6d360bce40bbcf196573dd27c4ce080641a2c59867e732dee size: 527
Harbor仓库忘记管理员密码如何重置
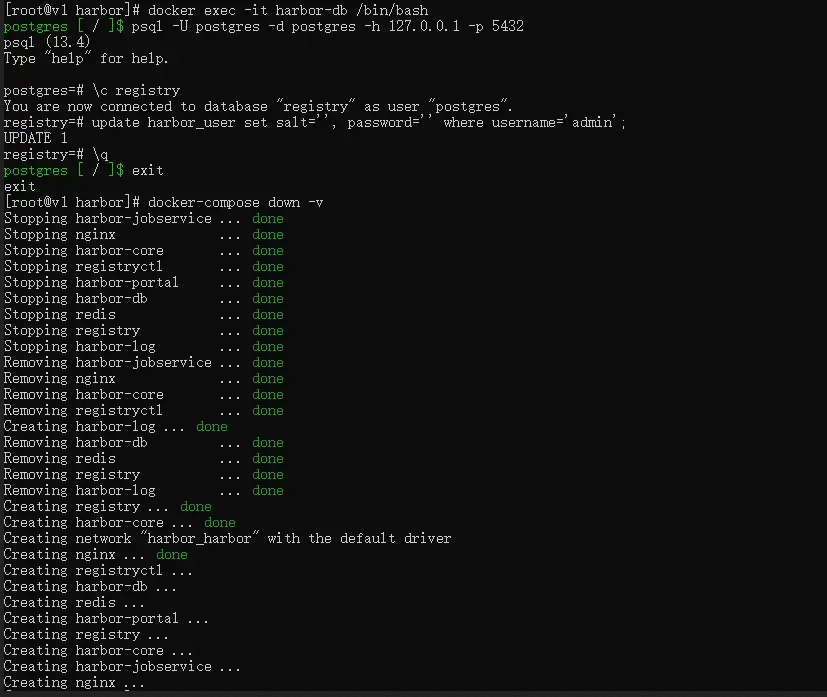
步骤01.通过docker exec -it harbor-db /bin/bash命令进入harbor-db容器内部
步骤02.执行如下postgresql命令行
psql -h postgresql -d postgres -U postgres # 这要输入默认密码:root123
psql -U postgres -d postgres -h 127.0.0.1 -p 5432 # 或者用这个可以不输入密码
步骤03.然后切换到harbor所在的数据库,执行 \c registry 命令
步骤04.执行SQL语句select * from harbor_user;查看harbor_user表
步骤05.例如修改admin的密码,修改为初始化密码 Harbor12345 修改好了之后再可以从web ui上再改一次。
# 如下此方法不行
update harbor_user set password='a71a7d0df981a61cbb53a97ed8d78f3e',salt='ah3fdh5b7yxepalg9z45bu8zb36sszmr' where username='admin';
# 正确做法
update harbor_user set salt='', password='' where username='admin';
步骤06.执行 \q 退出postgresql,再执行 exit 退出容器。
步骤07.重启harbor服务,以配置中的默认密码进行登陆。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!