8.X 的安装配置简化体现
文章转载自:https://mp.weixin.qq.com/s/CEYYKUub81mk59B3lqAcBA
- 节点无需任何安全配置,即可实现 TLS 加密通信、Https 加密通信。
- TLS 应用于 节点间的通信。
- Https 应用于 Http访问,例如:浏览器访问 elasticsearch。
在第一次启动之后,elasticsearch 下的elasticsearch.yml 文件自动新增配置如下:
Enable security features
xpack.security.enabled: true
xpack.security.enrollment.enabled: true
Enable encryption for HTTP API client connections, such as Kibana, Logstash, and Agents
xpack.security.http.ssl:
enabled: true
keystore.path: certs/http.p12
Enable encryption and mutual authentication between cluster nodes
xpack.security.transport.ssl:
enabled: true
verification_mode: certificate
keystore.path: certs/transport.p12
truststore.path: certs/transport.p12
Create a new cluster with the current node only
Additional nodes can still join the cluster later
cluster.initialmasternodes: ["DESKTOP-TKQF337"]
Allow HTTP API connections from localhost and local networks
Connections are encrypted and require user authentication
http.host: [local, site]
Allow other nodes to join the cluster from localhost and local networks
Connections are encrypted and mutually authenticated
#transport.host: [local, site]
#----------------------- END SECURITY AUTO CONFIGURATION -------------------------
而 Kibana 下的配置在浏览器配置完毕后,自动新增配置如下:
# This section was automatically generated during setup.
elasticsearch.hosts: ['https://172.20.6.225:9200']
elasticsearch.serviceAccountToken: AAEAAWVsYXN0aWMva2liYW5hL2Vucm9sbC1wcm9jZXNzLXRva2VuLTE2NDUxMDI3NzQyOTg6VWszUEc1YUtTMkdXT1lxMkNaUVdXdw
elasticsearch.ssl.certificateAuthorities: ['D:\2.es_install\kibana-8.0.0-windows-x86_64\kibana-8.0.0\data\ca_1645102775117.crt']
xpack.fleet.outputs: [{id: fleet-default-output, name: default, is_default: true, is_default_monitoring: true, type: elasticsearch, hosts: ['https://172.20.6.225:9200'], ca_trusted_fingerprint: 264b58e0f92f1e7492cc4cd407aac886012b026af6a20d777a05cd0ddccb43b4}]
这和早期版本使用不太一样的。
我习惯配置成本地 ip 地址,然后再访问的,包括云服务的我也是先改配置再访问。
- 优点:这种自动化的方式,单节点本机无需配置即可启动,非常方便。
- 缺点:对于云服务器方式,这种方式是不凑效的
关于云服务器的不生效,本质原因,看官方文档:
https://www.elastic.co/guide/en/elasticsearch/reference/current/configuring-stack-security.html
When Elasticsearch starts for the first time, the security auto-configuration process binds the HTTP layer to both _site_ and _local_, but only binds the transport layer to _local_. This intended behavior ensures that you can start a single-node cluster with security enabled by default without any additional configuration.
# _site_
Any site-local addresses on the system, for example 192.168.0.1.
# _local_
Any loopback addresses on the system, for example 127.0.0.1.
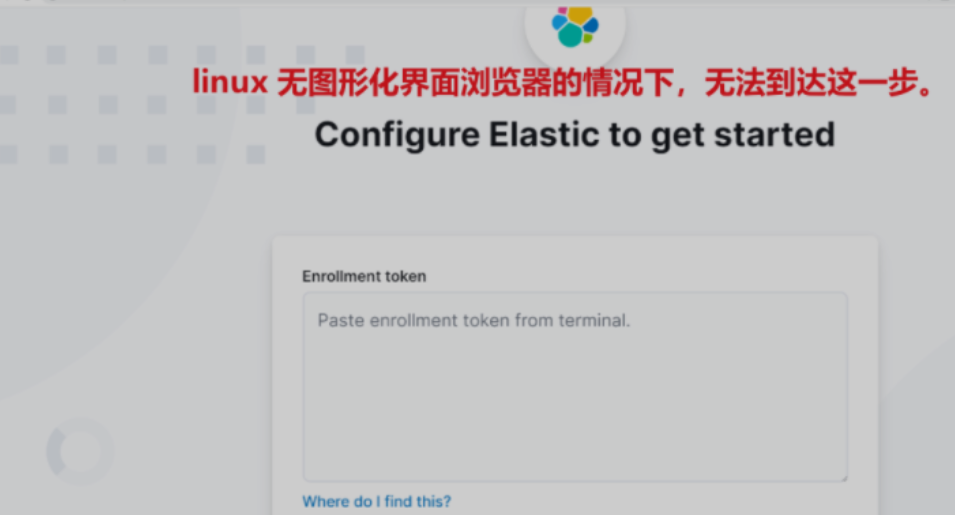
目前看 linux 云服务器在无图形化桌面浏览器的情况下无法通过浏览器实现。
分类:
ELK Stack





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!
2021-03-24 Docker安装部署Rancher
2021-03-24 Jenkins解决Host key verification failed
2021-03-24 Centos 7 安装 Haproxy
2021-03-24 阿里云下配置keepalive,利用HAVIP实现HA
2021-03-24 keepalived 实现双机热备
2021-03-24 HAproxy + keepalived 实现双机热备
2021-03-24 Keepalived设置master故障恢复后不重新抢回VIP