Logstash跟es加密通信
前提条件,es集群内部各节点已开启https访问,集群也已开启x-pack安全功能,并设置了系统默认的用户密码等,具体操作详见:https://www.cnblogs.com/sanduzxcvbnm/p/12046640.html
- 在ES节点上创建logstash_write_role角色
方法一:使用 Kibana Roles UI(Kibana 角色 UI)创建:
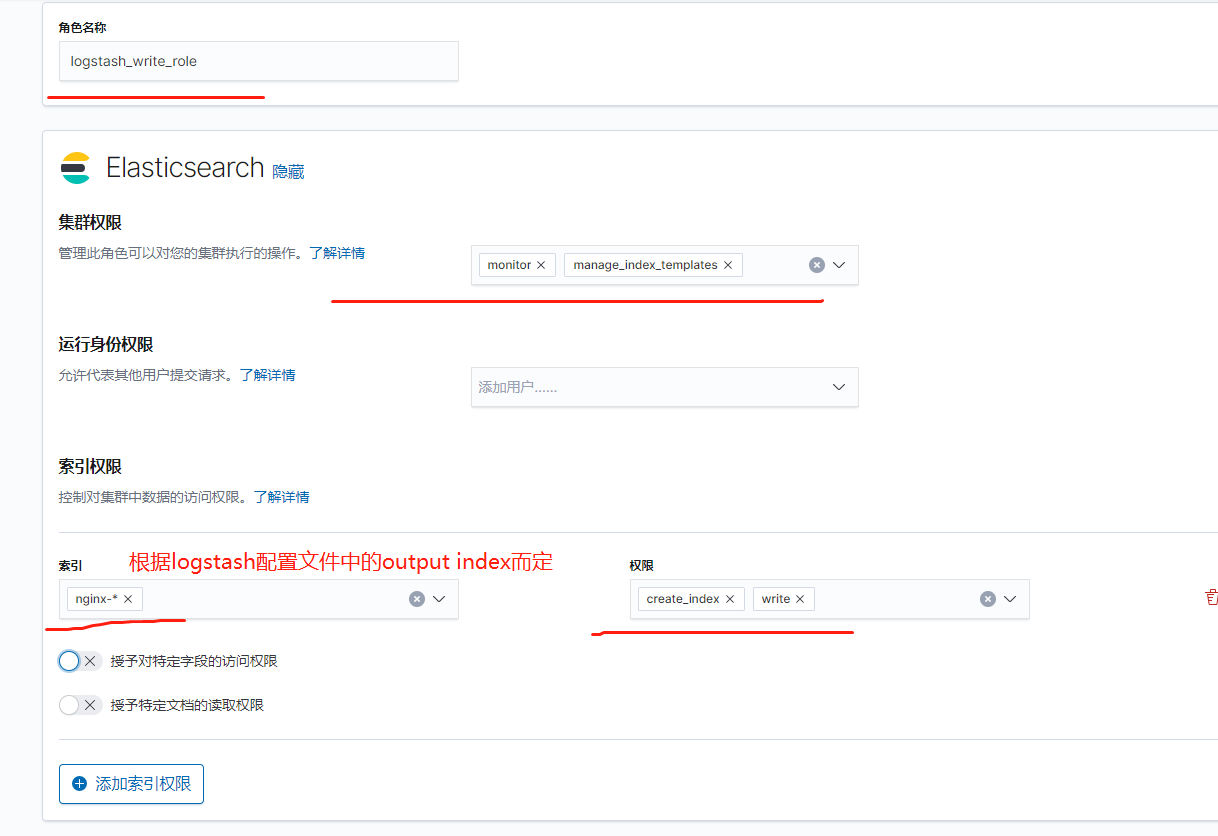
方法二:使用 Kibana Dev Tools(Kibana 开发工具)标签卡中的 API 创建:
POST /_security/role/logstash_write_role
{
"cluster": [
"monitor",
"manage_index_templates"
],
"indices": [
{
"names": [
"logstash*"
],
"privileges": [
"write",
"create_index"
],
"field_security": {
"grant": [
"*"
]
}
}
],
"run_as": [],
"metadata": {},
"transient_metadata": {
"enabled": true
}
}
# 返回结果
{"role":{"created":true}}
分配至此角色的用户将无法删除任何文档。此角色存在限制:只有用户在索引中以 logstash 或索引文档开始时,此角色才允许用户创建索引。
ILM 用户注意事项: 要使 logstash_writer_role 与索引生命周期管理 (ILM)(在 7.3+ 中默认启用)协同工作,必须包含以下权限:
"privileges": ["write","create","delete","create_index","manage","manage_ilm"]
- 创建 logstash_writer 用户(请为用户 logstash_writer 更改密码)
方法一:使用 Kibana Users UI(Kibana 用户 UI)创建:

方法二:使用 Kibana Dev Tools(Kibana 开发工具)标签卡中的 API 创建:
POST /_security/user/logstash_writer
{
"username": "logstash_writer",
"roles": [
"logstash_write_role"
],
"full_name": null,
"email": null,
"password": "",
"enabled": true
}
# 返回结果
{"user":{"created":true}}
# 修改用户密码,官方地址:https://www.elastic.co/guide/en/elasticsearch/reference/7.5/security-api-change-password.html
POST /_security/user/logstash_writer/_password
{
"password": "logstash_writer"
}
- 在es集群节点上为logstash使用ssl创建证书
可以参考这个文档,地址:https://www.cnblogs.com/sanduzxcvbnm/p/12055038.html
假设所需要的证书都在这个路径下:
ll /etc/logstash/certs
- 配置 logstash.yml
# grep -v '^#' logstash.yml
node.name: 192.168.75.20
path.data: /var/lib/logstash
path.config: /etc/logstash/conf.d/*.conf
path.logs: /var/log/logstash
xpack.monitoring.enabled: true
xpack.monitoring.elasticsearch.username: logstash_system # 根据实际情况而定,系统自带用户,不是上一步创建的用户
xpack.monitoring.elasticsearch.password: changeme # 根据实际情况而定
xpack.monitoring.elasticsearch.hosts: ["https://192.168.75.21:9200", "https://192.168.75.22:9200","https://192.168.75.23:9200"] # 根据实际情况而定
xpack.monitoring.elasticsearch.ssl.certificate_authority: "/etc/logstash/certs/ca.pem" # 根据实际情况而定
- 创建并配置 conf.d/example.conf
官方文档:https://www.elastic.co/guide/en/logstash/7.5/plugins-outputs-elasticsearch.html
https://www.elastic.co/guide/en/logstash/7.5/ls-security.html





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!