实验吧逆向catalyst-system——WP
0x0:
在linux里跑一下
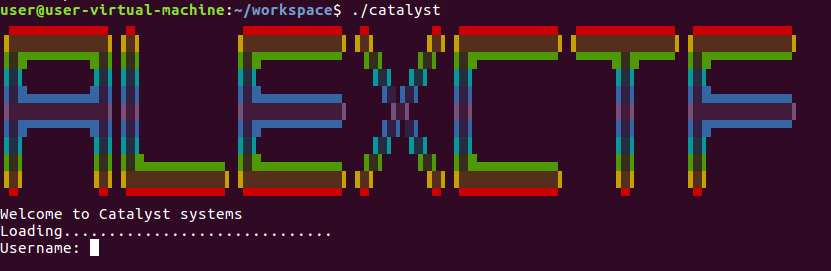
要求输入用户名 密码
0x1:
拖进IDA 查看关键字符串,找到关键函数F5查看伪代码。
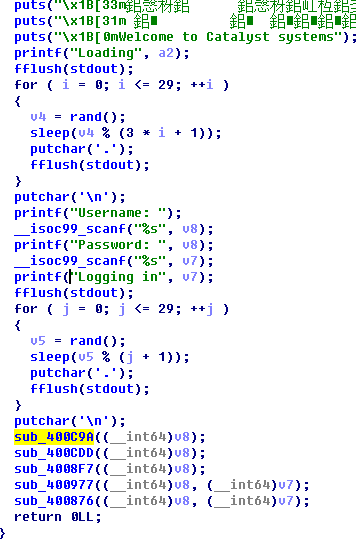
0x2:400C9A函数
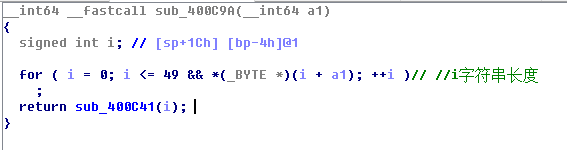
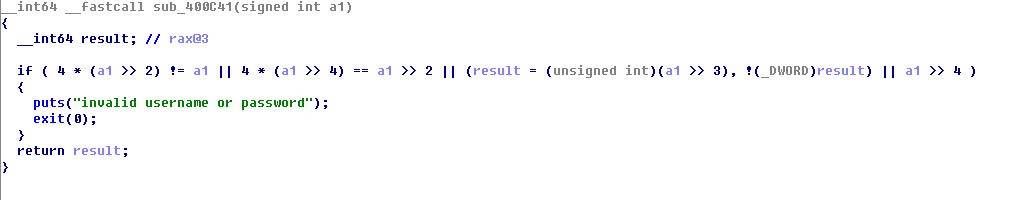
#include<stdio.h> #include<string.h> int main() { int i; for(i = 0 ;i<=49;i++){ if(4*(i >> 2) !=i || 4*(i >> 4) == i >>2 || !(i>>3) || i>>4 ) continue; else printf("%d ",i); } }
跑出结果 字符串长度若为12 或 8 符合00400C9A函数的校验。(8要舍去)
0x3:400CDD函数
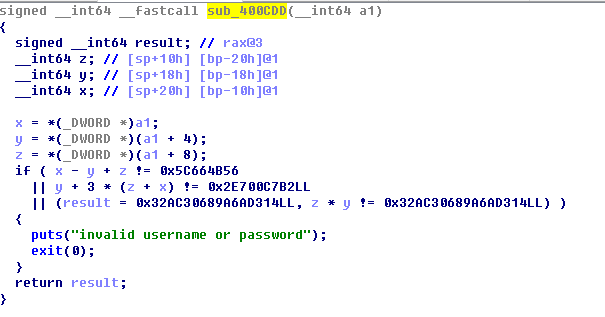
三元二次方程
x - y + z = 0x5C664B56 ==> x - y + z = a
y + 3 * (z + x) = 0x2E700C7B2LL ==> y + 3 * (z + x) = b
z * y = 0x32AC30689A6AD314LL ==> z * y = c
手解 orz。。。。。。
y = (b - 3a)/4 ==> y = 0x61746163
z = c/y ==> z = 0x6F65635F
x = a + y - z ==> x = 0x61746163
#include<stdio.h>
#include<string.h>
int main(){
unsigned int x = 0x61746163;
unsigned int y = 0x7473796c;
unsigned int z = 0x6f65635f;
unsigned int *p[3];
p[0] = &x;
p[1] = &y;
p[2] = &z;
for(int i =0 ;i<3;i++)
printf("%.*s",(int) sizeof(p[i])/2, (char *)p[i]);
(如果是32位 sizeof(p[i])/2 要改成 sizeof(p[i]))
跑出来结果为catalyst_ceo
0x4:4008F7函数
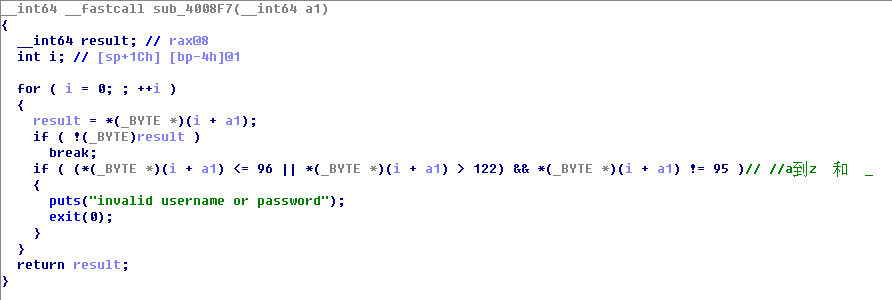
校验用户名 a 到 z 或者 是 ‘_’
0x5:400977函数
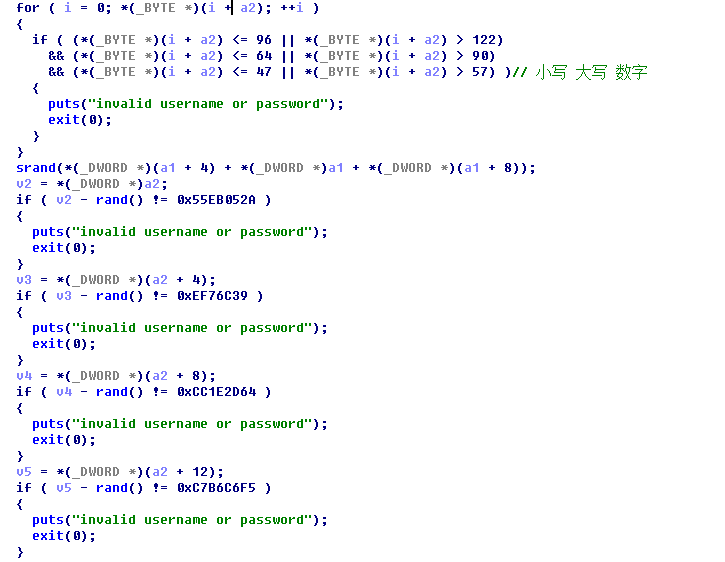
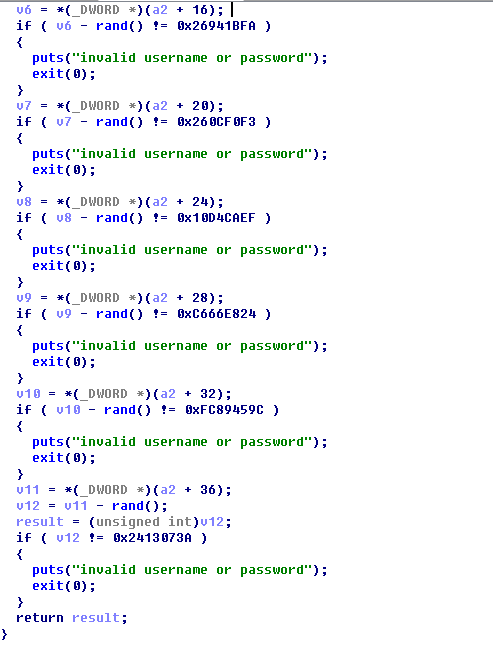
伪随机数验证password
#include<stdio.h>
#include<stdlib.h>
#include<time.h>
int main(){
unsigned int a[14];
srand(0x454D3E2E); //前面解出来的x + y + z
a[0] = 0x55EB052A + rand();
a[1] = 0x0EF76C39 + rand();
a[2] = 0xCC1E2D64 + rand();
a[3] = 0xC7B6C6F5 + rand();
a[4] = 0x26941BFA + rand();
a[5] = 0x260CF0F3 + rand();
a[6] = 0x10D4CAEF + rand();
a[7] = 0xC666E824 + rand();
a[8] = 0xFC89459C + rand();
a[9] = 0x2413073A + rand();
unsigned int *p [10];
for(int i = 0 ;i < 10; i++){
p[i] = &a[i];
}
for(int i = 0;i<10;i++){
printf("%.*s",(int)sizeof(p[i])/2,(char *)p[i]);
}
return 0;
}
跑出来password的结果为:sLSVpQ4vK3cGWyW86AiZhggwLHBjmx9CRspVGggj
Windows 下运行有问题 应在linux下运行
rand()函数产生的随机是不一样
linux下的 a[0] 到 a[9]
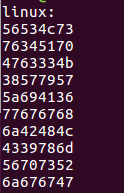
Windows下的a[0] 到 a[9]

0x6:400876()函数
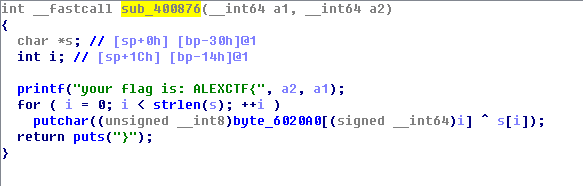
400876函数输出flag
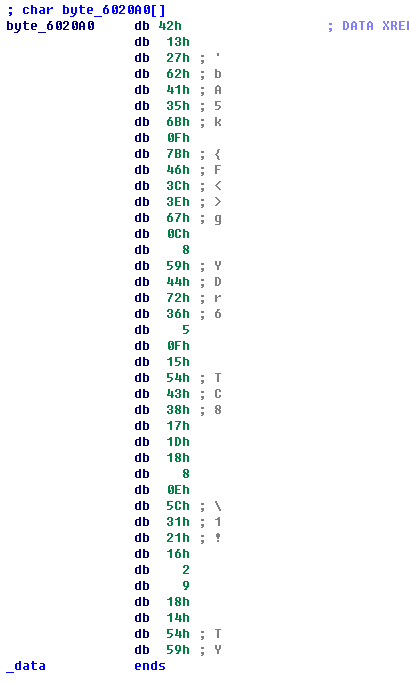
将password的每个字节和 byte_6020A0的每个元素异或得到flag
0x4 和 0x5 一起实现代码如下:
#include<stdio.h> #include<stdlib.h> #include<time.h> int main(){ unsigned int a[14]; srand(0x454D3E2E); a[0] = 0x55EB052A + rand(); a[1] = 0x0EF76C39 + rand(); a[2] = 0xCC1E2D64 + rand(); a[3] = 0xC7B6C6F5 + rand(); a[4] = 0x26941BFA + rand(); a[5] = 0x260CF0F3 + rand(); a[6] = 0x10D4CAEF + rand(); a[7] = 0xC666E824 + rand(); a[8] = 0xFC89459C + rand(); a[9] = 0x2413073A + rand(); unsigned char b[] = {0x42, 0x13, 0x27, 0x62, 0x41, 0x35, 0x6b, 0x0f, 0x7b, 0x46, 0x3c, 0x3e, 0x67, 0x0c, 0x08, 0x59, 0x44, 0x72, 0x36, 0x05, 0x0f, 0x15, 0x54, 0x43, 0x38, 0x17, 0x1d, 0x18, 0x08, 0x0e, 0x5c, 0x31, 0x21, 0x16, 0x02, 0x09, 0x18, 0x14, 0x54, 0x59}; unsigned int *p [10]; for(int i = 0 ;i < 10; i++){ p[i] = &a[i]; } char *p1 = (char *)p[0]; for(int i = 0;i<10;i++){ printf("%.*s",(int)sizeof(p[i])/2,(char *)p[i]); } printf("\n"); for (int j = 0 ;j < 40 ;j++){ printf("%c",b[j] ^ p1[j] ); } return 0; }
跑出来结果为
sLSVpQ4vK3cGWyW86AiZhggwLHBjmx9CRspVGggj
1_t41d_y0u_y0u_ar3__gr34t__reverser__s33
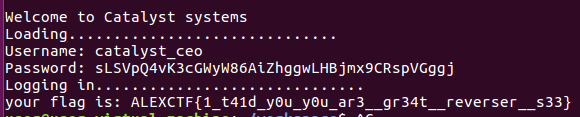
综上flag:ALEXCTF{1_t41d_y0u_y0u_ar3__gr34t__reverser__s33}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号