在Istio Ingress Gateway上实现SSO
kubectl edit svc istio-ingressgateway -n istio-system
更改端口为 80
kubectl edit svc keycloak -nkeycloak
更改为8080
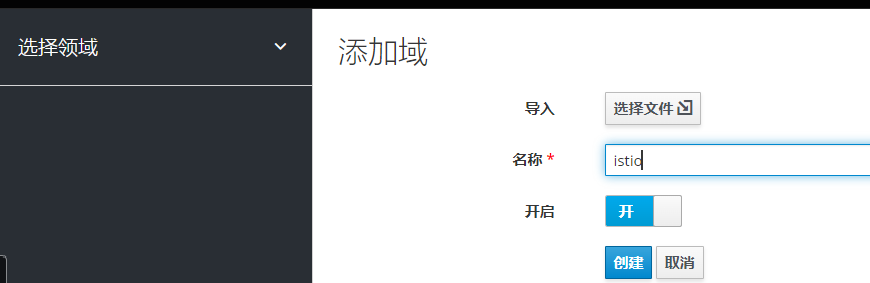
添加域
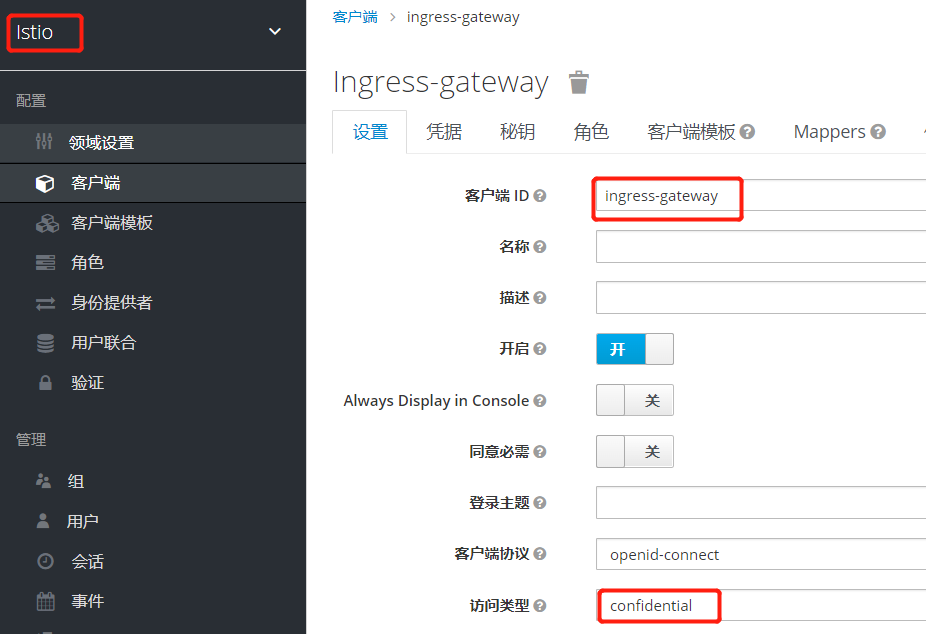
添加客户端
Keycloak上的Access Type共有三类:
◼ confidential:适用于需要执行浏览器登录的应用,客户端会通过client secret来获取access token , 多用于服务端渲染的web系统场景中;
◼ public:适用于需要执行浏览器登录的应用,多运用于使用vue和react实现的前端项目;
◼ bearer-only:适用于不需要执行浏览器登录的应用,只允许携带bearer token访问,多运用于RESTful API的使用场景;
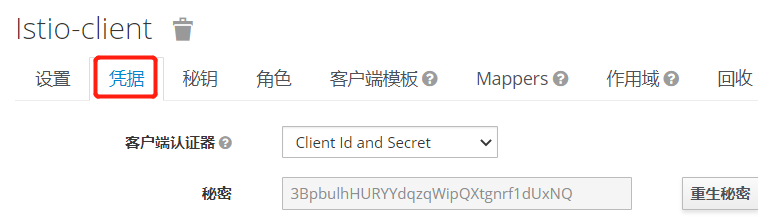
添加*

多出凭据
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# cat 01-deploy-oauth2.yaml apiVersion: v1 kind: Namespace metadata: name: oauth2-proxy labels: istio-injection: enabled --- apiVersion: v1 kind: Secret metadata: name: oauth2-proxy namespace: oauth2-proxy stringData: # change this to your Keycloak Realm Client Id OAUTH2_PROXY_CLIENT_ID: ingress-gateway # change this to your Keycloak Client Secret OAUTH2_PROXY_CLIENT_SECRET: QdbO5qR5OPNcHdedX6GFZSxlOmqKDKkm # Generate by command: openssl rand -base64 32 | tr -- '+/' '-_' OAUTH2_PROXY_COOKIE_SECRET: vEBMxbw7NXfaUIJR4klhdvB678GUPxWTd7tR9hq2m8w= --- apiVersion: v1 kind: Service metadata: name: oauth2-proxy namespace: oauth2-proxy spec: selector: app: oauth2-proxy ports: - name: http port: 4180 --- apiVersion: apps/v1 kind: Deployment metadata: name: oauth2-proxy namespace: oauth2-proxy spec: selector: matchLabels: app: oauth2-proxy template: metadata: labels: app: oauth2-proxy spec: containers: - name: oauth2-proxy image: quay.io/oauth2-proxy/oauth2-proxy:v7.2.1 args: - --provider=oidc - --oidc-issuer-url=http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio - --profile-url=http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/userinfo - --validate-url=http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/userinfo - --set-authorization-header=true - --http-address=0.0.0.0:4180 - --pass-host-header=true - --reverse-proxy=true - --auth-logging=true - --cookie-httponly=true - --cookie-refresh=4m - --cookie-secure=false - --email-domain="*" - --pass-access-token=true - --pass-authorization-header=true - --request-logging=true - --set-xauthrequest=true - --silence-ping-logging=true - --skip-provider-button=true - --skip-auth-strip-headers=false - --ssl-insecure-skip-verify=true - --standard-logging=true - --upstream="static://200" - --whitelist-domain=".magedu.com,.cluster.local" env: - name: OAUTH2_PROXY_CLIENT_ID valueFrom: secretKeyRef: name: oauth2-proxy key: OAUTH2_PROXY_CLIENT_ID - name: OAUTH2_PROXY_CLIENT_SECRET valueFrom: secretKeyRef: name: oauth2-proxy key: OAUTH2_PROXY_CLIENT_SECRET - name: OAUTH2_PROXY_COOKIE_SECRET valueFrom: secretKeyRef: name: oauth2-proxy key: OAUTH2_PROXY_COOKIE_SECRET resources: requests: cpu: 10m memory: 100Mi ports: - containerPort: 4180 protocol: TCP readinessProbe: periodSeconds: 3 httpGet: path: /ping port: 4180
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# kubectl get deploy -noauth2-proxy NAME READY UP-TO-DATE AVAILABLE AGE oauth2-proxy 1/1 1 1 71s
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# kubectl get svc -noauth2-proxy NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE oauth2-proxy ClusterIP 10.100.183.155 <none> 4180/TCP 3m7s
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# cat 02-istio-operator-update.yaml apiVersion: install.istio.io/v1alpha1 kind: IstioOperator spec: profile: demo meshConfig: extensionProviders: - name: oauth2-proxy #和下面配置同名 envoyExtAuthzHttp: service: oauth2-proxy.oauth2-proxy.svc.cluster.local port: 4180 timeout: 1.5s includeHeadersInCheck: ["authorization", "cookie"] headersToUpstreamOnAllow: ["x-forwarded-access-token", "authorization", "path", "x-auth-request-user", "x-auth-request-email", "x-auth-request-access-token"] headersToDownstreamOnDeny: ["content-type", "set-cookie"]
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# istioctl install -f 02-istio-operator-update.yaml
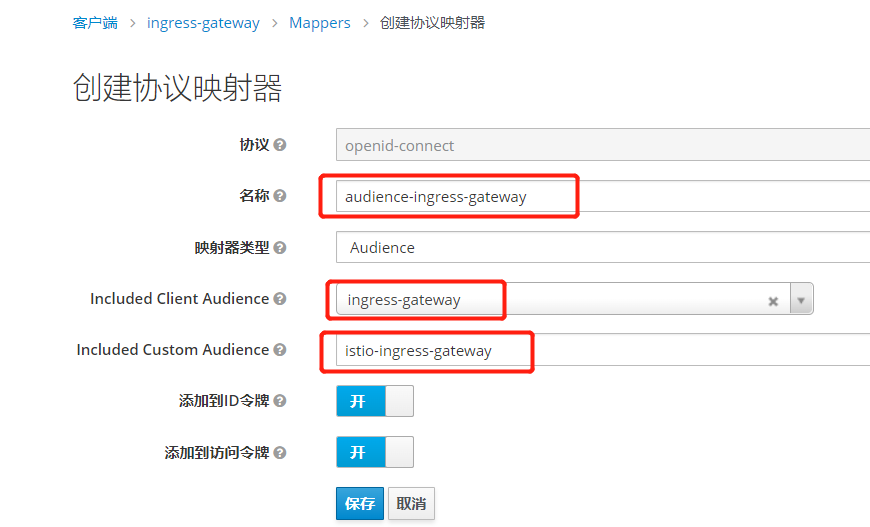
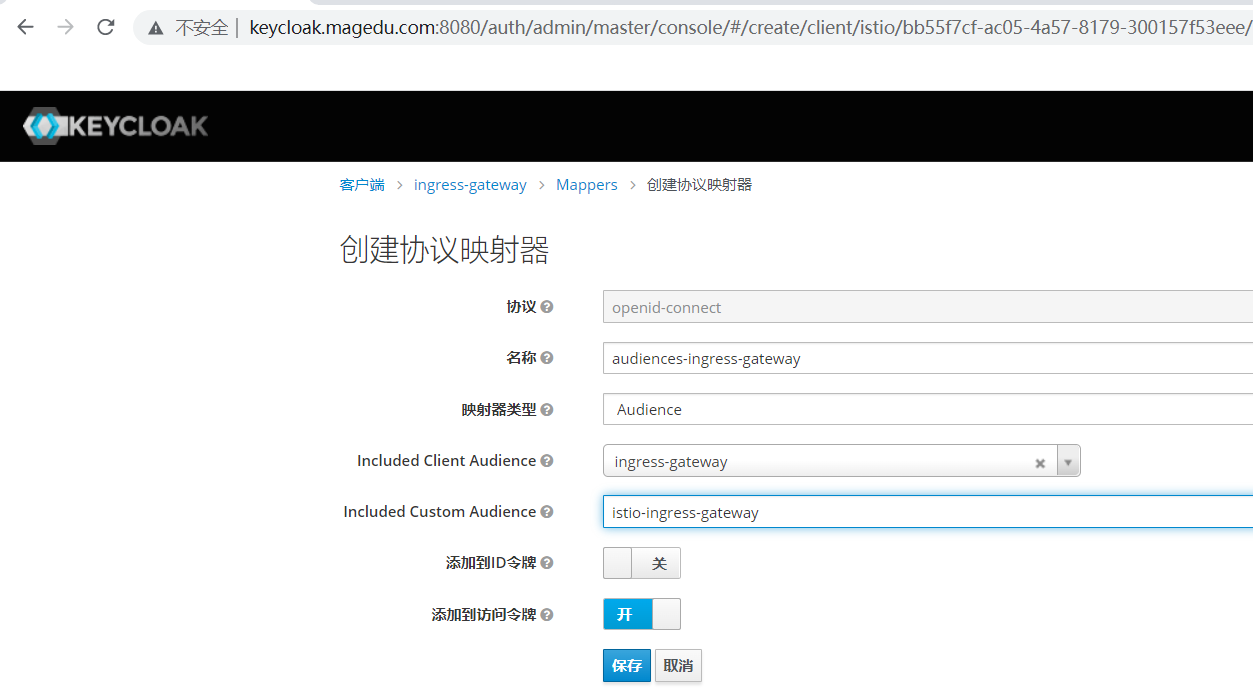
root@master01:/opt/istio-in-practise/Security/05-JWT-and-Keycloak# cat 03-ext-auth-ingress-gateway.yaml apiVersion: security.istio.io/v1beta1 kind: RequestAuthentication metadata: name: istio-ingressgateway namespace: istio-system spec: selector: matchLabels: app: istio-ingressgateway jwtRules: - issuer: http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio jwksUri: http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/certs #audiences: ["ingress-gateway","istio-ingress-gateway"] # Forward JWT to Envoy Sidecar #forwardOriginalToken: true # - issuer: http://keycloak.magedu.com:8080/auth/realms/istio # jwksUri: http://keycloak.magedu.com:8080/auth/realms/istio/protocol/openid-connect/certs --- apiVersion: security.istio.io/v1beta1 kind: AuthorizationPolicy metadata: name: ext-authz-oauth2-proxy namespace: istio-system spec: selector: matchLabels: app: istio-ingressgateway action: CUSTOM provider: # Extension provider configured when we installed Istio name: oauth2-proxy #和上面配置同名 rules: - to: - operation: hosts: ["kiali.magedu.com"] notPaths: ["/auth/*"]

自动跳转为
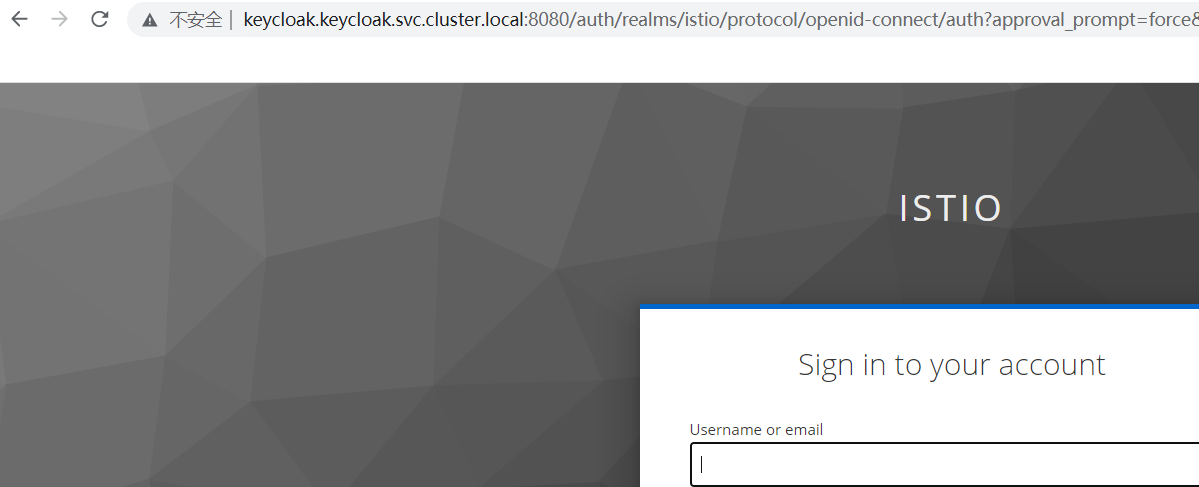
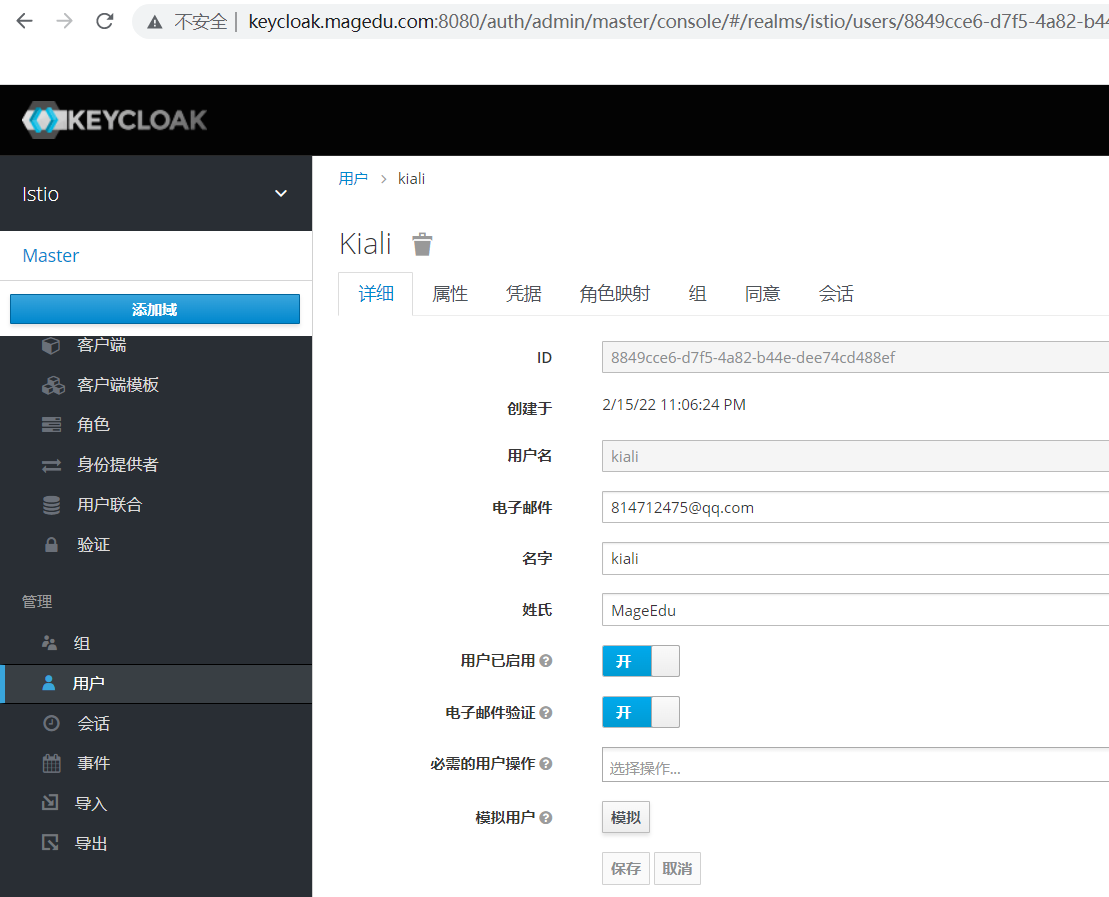
新建用户
新建密码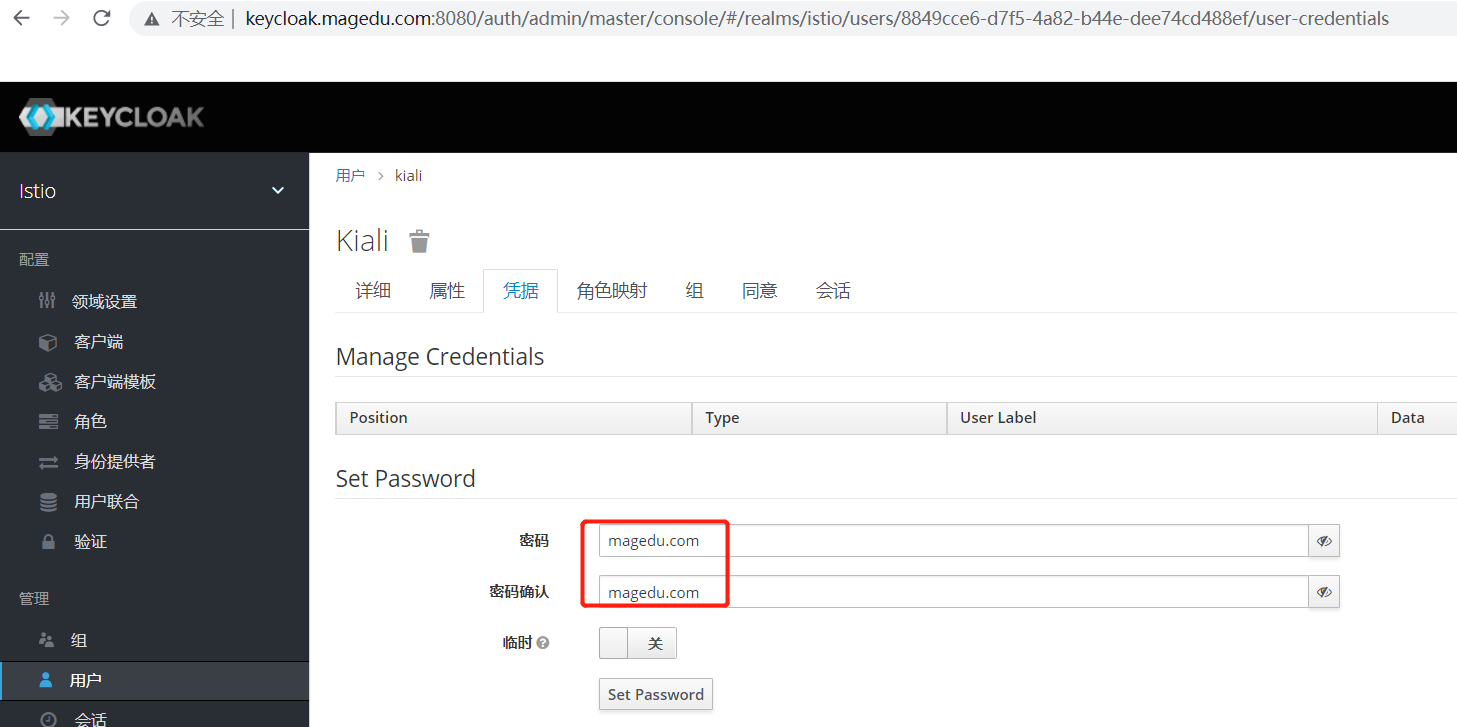
############
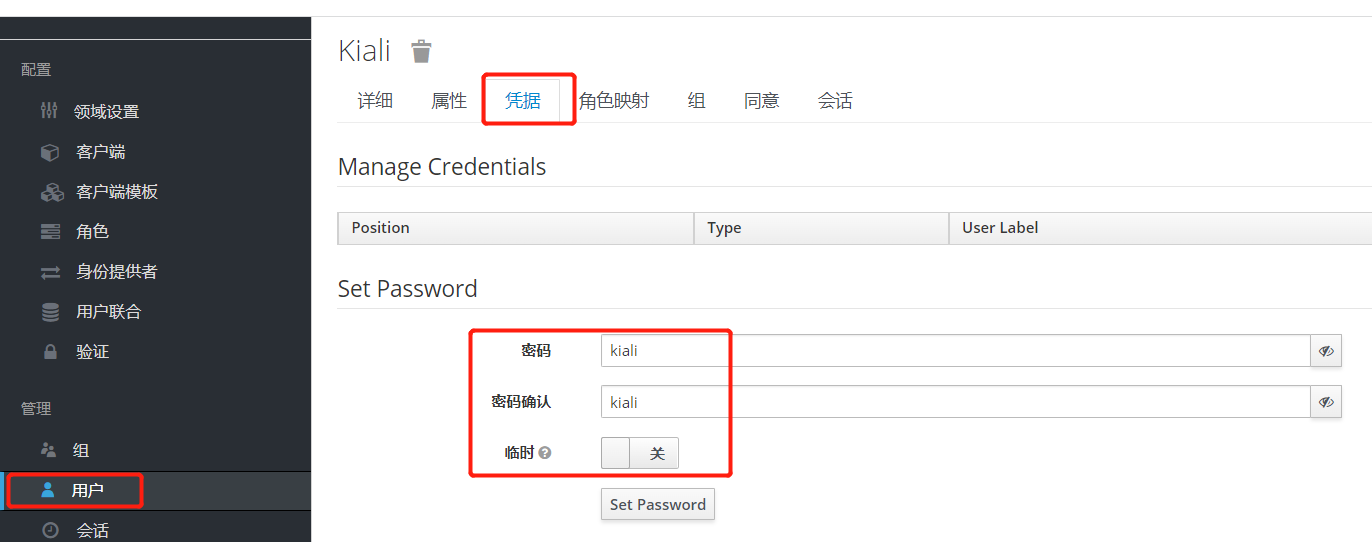
Set Password
root@client /# curl -s --data "username=kiali&password=magedu.com&grant_type=password&client_id=ingress-gateway&client_secret=jMK4wOOQfGlsDuuhUJ3p5KXsGoQfjQUl" http://keycloak.keycloak.svc.cluster.local:8080/auth/realms/istio/protocol/openid-connect/token {"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJzX1N6TGw0bEJkOXdEOTl3ZklWeHVCSFI3Y0hWMUt5bk1QUXRTaWI1UEdZIn0.eyJleHAiOjE2NDQ5Mzg1MjQsImlhdCI6MTY0NDkzODIyNCwianRpIjoiMzg3YTllOTctOTA4MC00MDY5LWI2MjctNTIwOWIwN2Q0MDZiIiwiaXNzIjoiaHR0cDovL2tleWNsb2FrLmtleWNsb2FrLnN2Yy5jbHVzdGVyLmxvY2FsOjgwODAvYXV0aC9yZWFsbXMvaXN0aW8iLCJhdWQiOlsiaW5ncmVzcy1nYXRld2F5IiwiYWNjb3VudCJdLCJzdWIiOiI4ODQ5Y2NlNi1kN2Y1LTRhODItYjQ0ZS1kZWU3NGNkNDg4ZWYiLCJ0eXAiOiJCZWFyZXIiLCJhenAiOiJpbmdyZXNzLWdhdGV3YXkiLCJzZXNzaW9uX3N0YXRlIjoiMzlkMjdmYzgtMmVlOS00Yzk1LTg5NDUtNjE5MDBmYjEzNWZhIiwiYWNyIjoiMSIsInJlYWxtX2FjY2VzcyI6eyJyb2xlcyI6WyJvZmZsaW5lX2FjY2VzcyIsInVtYV9hdXRob3JpemF0aW9uIiwiZGVmYXVsdC1yb2xlcy1pc3RpbyJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoiZW1haWwgcHJvZmlsZSIsInNpZCI6IjM5ZDI3ZmM4LTJlZTktNGM5NS04OTQ1LTYxOTAwZmIxMzVmYSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJuYW1lIjoia2lhbGkgTWFnZUVkdSIsInByZWZlcnJlZF91c2VybmFtZSI6ImtpYWxpIiwiZ2l2ZW5fbmFtZSI6ImtpYWxpIiwiZmFtaWx5X25hbWUiOiJNYWdlRWR1IiwiZW1haWwiOiI4MTQ3MTI0NzVAcXEuY29tIn0.QibbO0bqKZ19M4xMqCt0zgmh_qumB0-5gDFphqJ7oOHP1izO3r10gS_HreUCDff3J3U6ZCLIB-v-pFO3eiBFUlIdN1Eo_vmdd12X6W85cPiciFBpZgWYjsebIwGLr0wd8WrJpqzO7st3XqMSrOxjBXnP3fu9LrHfUOKn9JdJbCH57Q0UjydBOmRRtvffZVRcchBoQ7B8Pw9j7vObkWuU2p9BQxE-Csegd9KP3Uv2m_oKVJsP6YeWT_DzFT0-6AR1Rq-A3If5yI-aNzmZHCvAT_-imEP1XWv9blSxItQMe2Z-Av04P4vhMS0gHNaQ1mHs0fRcQn9R1wmlNMizOaiZ0Q","expires_in":300,"refresh_expires_in":1800,"refresh_token":"eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJmNzc4YTQxYi01NDU3LTQzZDUtYmIwZC0wZmMzOGY1MzdlMzIifQ.eyJleHAiOjE2NDQ5NDAwMjQsImlhdCI6MTY0NDkzODIyNCwianRpIjoiNDUwOTlmNTQtYzI1ZC00MzE0LTkyNDgtMDBlNzRjZmExMThhIiwiaXNzIjoiaHR0cDovL2tleWNsb2FrLmtleWNsb2FrLnN2Yy5jbHVzdGVyLmxvY2FsOjgwODAvYXV0aC9yZWFsbXMvaXN0aW8iLCJhdWQiOiJodHRwOi8va2V5Y2xvYWsua2V5Y2xvYWsuc3ZjLmNsdXN0ZXIubG9jYWw6ODA4MC9hdXRoL3JlYWxtcy9pc3RpbyIsInN1YiI6Ijg4NDljY2U2LWQ3ZjUtNGE4Mi1iNDRlLWRlZTc0Y2Q0ODhlZiIsInR5cCI6IlJlZnJlc2giLCJhenAiOiJpbmdyZXNzLWdhdGV3YXkiLCJzZXNzaW9uX3N0YXRlIjoiMzlkMjdmYzgtMmVlOS00Yzk1LTg5NDUtNjE5MDBmYjEzNWZhIiwic2NvcGUiOiJlbWFpbCBwcm9maWxlIiwic2lkIjoiMzlkMjdmYzgtMmVlOS00Yzk1LTg5NDUtNjE5MDBmYjEzNWZhIn0.T7XRrK-cg0ViLKxkRCFRZolvfqXCoXJCC59QALBIJ6o","token_type":"Bearer","not-before-policy":0,"session_state":"39d27fc8-2ee9-4c95-8945-61900fb135fa","scope":"email profile"}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号