Istio Security 基础
环境
配置
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/02-demoapp-v11# cat deploy-proxy.yaml apiVersion: apps/v1 kind: Deployment metadata: name: proxy spec: progressDeadlineSeconds: 600 replicas: 1 selector: matchLabels: app: proxy template: metadata: labels: app: proxy spec: containers: - env: - name: PROXYURL value: http://demoapp:8080 image: ikubernetes/proxy:v0.1.1 imagePullPolicy: IfNotPresent name: proxy ports: - containerPort: 8080 name: web protocol: TCP resources: limits: cpu: 50m --- apiVersion: v1 kind: Service metadata: name: proxy spec: ports: - name: http-80 port: 80 protocol: TCP targetPort: 8080 selector: app: proxy ---
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/01-demoapp-v10# cat deploy-demoappv10.yaml --- apiVersion: apps/v1 kind: Deployment metadata: labels: app: demoappv10 version: v1.0 name: demoappv10 spec: progressDeadlineSeconds: 600 replicas: 3 selector: matchLabels: app: demoapp version: v1.0 template: metadata: labels: app: demoapp version: v1.0 spec: containers: - image: ikubernetes/demoapp:v1.0 imagePullPolicy: IfNotPresent name: demoapp env: - name: "PORT" value: "8080" ports: - containerPort: 8080 name: web protocol: TCP resources: limits: cpu: 50m --- apiVersion: v1 kind: Service metadata: name: demoappv10 spec: ports: - name: http port: 8080 protocol: TCP targetPort: 8080 selector: app: demoapp version: v1.0 type: ClusterIP ---
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/02-demoapp-v11# cat deploy-demoapp-v11.yaml --- apiVersion: apps/v1 kind: Deployment metadata: labels: app: demoappv11 version: v1.1 name: demoappv11 spec: progressDeadlineSeconds: 600 replicas: 2 selector: matchLabels: app: demoapp version: v1.1 template: metadata: labels: app: demoapp version: v1.1 spec: containers: - image: ikubernetes/demoapp:v1.1 imagePullPolicy: IfNotPresent name: demoapp env: - name: "PORT" value: "8080" ports: - containerPort: 8080 name: web protocol: TCP resources: limits: cpu: 50m --- apiVersion: v1 kind: Service metadata: name: demoappv11 spec: ports: - name: http-8080 port: 8080 protocol: TCP targetPort: 8080 selector: app: demoapp version: v1.1 type: ClusterIP ---
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/02-demoapp-v11# cat service-demoapp.yaml --- apiVersion: v1 kind: Service metadata: name: demoapp spec: ports: - name: http port: 8080 protocol: TCP targetPort: 8080 selector: app: demoapp type: ClusterIP ---
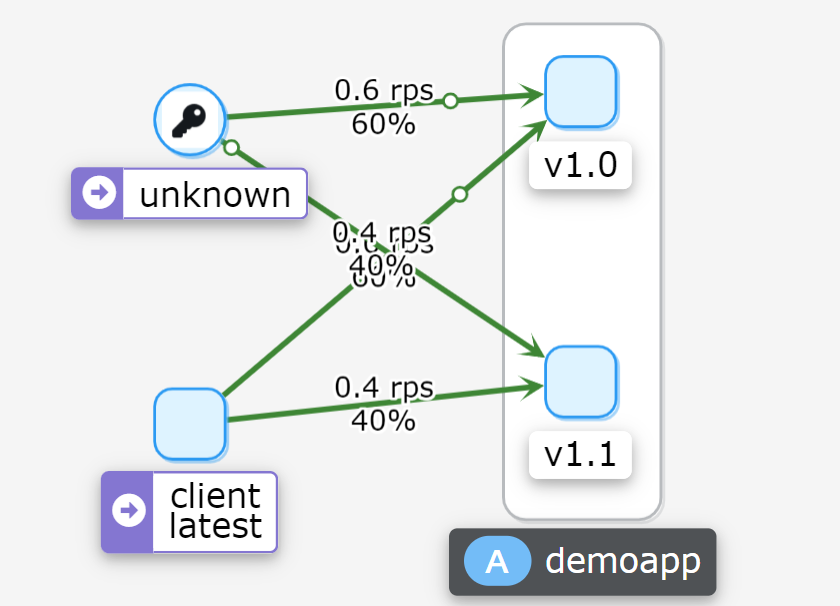
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/03-demoapp-subset# cat destinationrule-demoapp.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: demoapp spec: host: demoapp subsets: - name: v10 labels: version: v1.0 - name: v11 labels: version: v1.1
root@master01:/opt/istio-in-practise/Traffic-Management-Basics/ms-demo/06-weight-based-routing# cat virtualservice-demoapp.yaml apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: demoapp spec: hosts: - demoapp http: - name: weight-based-routing route: - destination: host: demoapp subset: v10 weight: 90 - destination: host: demoapp subset: v11 weight: 10
1.1 Istio认证机制
Istio沿用了Envoy所支持的认证方式,它为网格内的服务提供两种身份验证机制
◼ Peer authentication:即service-to-service身份验证,或简称为服务认证,用以验证发起连接请求的客户端;为此,Istio支持双向TLS认证,即mTLS,以实现如下特性
◆ 为每个服务提供一个专用的可表示其角色的身份标识,以实现跨集群和跨云的互操作;
◆ 安全实现service-to-service通信;
◆ 提供密钥管理系统以自动完成密钥和证书生成、分发及轮替;
◼ Request authentication:也称为最终用户认证,它将发出请求的原始客户端认证为最终用户或设备;
◆ Istio基于JWT验证机制启用请求级身份认证功能
◆ 支持使用自定义的身份认证服务,或任何中OIDC认证系统,例如Keycloak、Auth0、Firebase Auth等
Istio将身份认证策略通过Kubernetes API存储于Istio configuration storage之中
◼ istiod负责确诊每个代理保持最新状态,并在适当时提供密钥;
◼ Istio的认证机制还支持许可模式(permissive mode)
1.2 Peer Authentication Policy 使用要点
Peer Authentication Policy负责为工作负载指定其作为服务器端时实施TLS通信的方式,它支持如下模式
◼ PERMISSIVE:工作负载支持mTLS流量和纯文本(明文)流量,通常仅应该于将应用迁移至网格过程中的过渡期间使用;默认
◼ STRICT:工作负载仅支持mTLS流量;
◼ DISABLE:禁用mTLS;
◼ UNSET:从上级继承认证策略的设定;
另外,在使用了非空selector(即特定于某工作负载)的Peer Authentication Policy上,还可以为不同的端口指定不同的mTLS设定;
1.3 默认都能访问,区别明文密文
root@client /# while true;do curl demoappv10:8080;sleep 1;done
root@master01:~# kubectl get po -owide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES client 2/2 Running 0 10m 10.200.59.214 192.168.80.203 <none> <none> root@master02:~# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.200.59.214 0.0.0.0 255.255.255.255 UH 0 0 0 calia7a3e029a7b
root@master02:~# tcpdump -i calia7a3e029a7b -nn -X tcp port 8080 #默认envoy全网格密文
端口 以数字的形式显示ip和端口 明文密文显示 协议和端口
0x0000: 4500 0468 7741 4000 4006 7c95 0ac8 3bd6 E..hwA@.@.|...;. 0x0010: 0ac8 f153 8196 1f90 512e 201f 3d2e 55cf ...S....Q...=.U. 0x0020: 8018 01f6 4714 0000 0101 080a 9af3 69ef ....G.........i. 0x0030: e878 8585 1703 0304 2f00 0000 0000 0000 .x....../.......
root@master01:~# kubectl run client-test --image=ikubernetes/admin-box:v1.2 --restart=Never -it -n test --command -- /bin/bash
root@client-test # while true;do curl demoapp.default:8080;sleep 1;done iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-6ff964cbff-9r4l7, ServerIP: 10.200.241.90! iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-6ff964cbff-gqdw8, ServerIP: 10.200.241.86!
root@master03:~# tcpdump -i cali71173565fbc -nn -X tcp port 8080 #test 名称空间明文
PeerAuthentication CR
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 01-namespace-default-peerauthn.yaml --- apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: default namespace: default spec: mtls: mode: PERMISSIVE ---
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# kubectl get sa -A |grep default default default 1 2d19h istio-system default 1 47h kube-node-lease default 1 2d19h kube-public default 1 2d19h kube-system default 1 2d19h kubernetes-dashboard default 1 2d19h test default 1 4h50m
1.4 pa strict,同名称空间可以,不同名称空间不能访问
demoapp服务
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 03-destinationrule-demoapp-mtls.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: demoapp spec: host: demoapp trafficPolicy: loadBalancer: simple: LEAST_CONN # tls: # mode: ISTIO_MUTUAL subsets: - name: v10 labels: version: v1.0 - name: v11 labels: version: v1.1
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 02-demoapp-peerauthn.yaml --- apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: demoapp namespace: default spec: selector: matchLabels: app: demoapp mtls: mode: STRICT ---
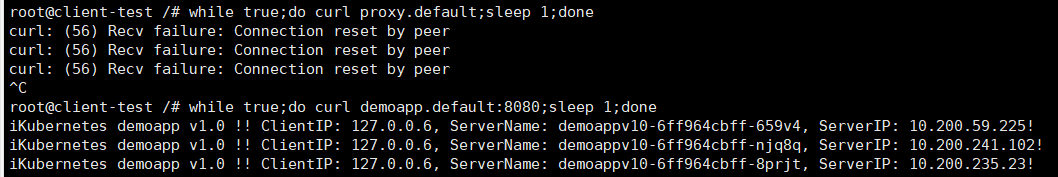
root@client /# while true;do curl demoapp:8080;sleep 1;done #能建立mtls的可以访问 iKubernetes demoapp v1.1 !! ClientIP: 127.0.0.6, ServerName: demoappv11-7984f579f5-8lw2z, ServerIP: 10.200.241.103! iKubernetes demoapp v1.0 !! ClientIP: 127.0.0.6, ServerName: demoappv10-6ff964cbff-njq8q, ServerIP: 10.200.241.102!
root@client-test /# while true;do curl demoapp.default:8080;sleep 1;done #不能建立mtls的禁止访问 curl: (56) Recv failure: Connection reset by peer curl: (56) Recv failure: Connection reset by peer
proxy服务
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 04-proxy-peerauthn.yaml --- apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: proxy namespace: default spec: selector: matchLabels: app: proxy mtls: mode: STRICT ---
1.5 DR+PA
客户端可用的TLS模式
◼ DISABLE:禁止同上游端点创建TLS连接;
◼ SIMPLE:向上游发起一个TLS连接(单向验证服务端的证书);
◼ MUTUAL:同上游建立双向认证的TLS连接,向上游提供客户端证书由clientCertificate字段指定;
◼ ISTIO_MUTIAL:同上游建立双向认证的TLS连接,但会使用由Istio自动生成的证书;因此,该模式要求
ClientTLSSettings字段中嵌套其它字段统统使用空值;
DestinationRule上的TLS客户端与PeerAuthentication上的TLS服务端的组合要点:
◆PeerAuthentication使用PERMISSIVE时,DestinationRule可以使用任意模式;
◆PeerAuthentication使用STRICT时,DestinationRule可以使用MUTUAL或ISTIO_MUTUAL;
◆PeerAuthentication使用DISABLE时,DestinationRule也需要使用DISABLE模式;
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# kubectl delete -f 02-demoapp-peerauthn.yaml --- apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: demoapp namespace: default spec: selector: matchLabels: app: demoapp mtls: mode: STRICT ---
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 03-destinationrule-demoapp-mtls.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: demoapp spec: host: demoapp trafficPolicy: loadBalancer: simple: LEAST_CONN tls: mode: ISTIO_MUTUAL subsets: - name: v10 labels: version: v1.0 - name: v11 labels: version: v1.1
不同名称空间密文通信
root@master01:/opt/istio-in-practise/Security/01-PeerAuthentication-Policy-Basics# cat 05-destinationrule-demoapp-tls-disable.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: demoapp spec: host: demoapp trafficPolicy: loadBalancer: simple: LEAST_CONN tls: mode: DISABLE subsets: - name: v10 labels: version: v1.0 - name: v11 labels: version: v1.1
不同名称空间也是明文通信
总结
PA定义服务端tls通信模式,DR定义客户端tls模式
PA STRICT 能建立mtls的可以访问,不能建立mtls的不能访问
PA PERMISSIVE DR mtls 都能访问,能建立双向mtls的加密访问,不能建立双向mtls的明文访问
PA PERMISSIVE DR disable 都能访问,能建立双向mtls的明文访问,不能建立双向mtls的明文访问




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!