k8s 使用RBAC鉴权
https://kubernetes.io/docs/reference/access-authn-authz/rbac/
kubectl create serviceaccount user1 -nchuan
serviceaccount/user1 created root@slave002:~/role# kubectl get secrets -nchuan NAME TYPE DATA AGE default-token-j5xbb kubernetes.io/service-account-token 3 27h user1-token-m8h8t kubernetes.io/service-account-token 3 6
root@slave002:~/role# cat user1_role.yaml kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: namespace: chuan name: user1-role rules: - apiGroups: ["*"] resources: ["pods/exec"] verbs: ["*"] ##RO-Role #verbs: ["get", "list", "watch", "create"] - apiGroups: ["*"] resources: ["pods"] #verbs: ["*"] ##RO-Role verbs: ["get", "list", "watch"] - apiGroups: ["apps/v1"] resources: ["deployments"] verbs: ["get", "list", "watch", "create", "update", "patch", "delete"] ##RO-Role #verbs: ["get", "watch", "list"]
root@slave002:~/role# kubectl get Role -nchuan NAME CREATED AT user1-role
root@slave002:~/role# cat user1_role_bind.yaml kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: role-bind-chuan namespace: chuan subjects: - kind: ServiceAccount name: user1 namespace: chuan roleRef: kind: Role name: user1-role apiGroup: rbac.authorization.k8s.io
root@slave002:~/role# kubectl get RoleBinding -nchuan NAME ROLE AGE role-bind-chuan Role/user1-role 32s
root@slave002:~/role# kubectl describe secrets user1-token-m8h8t -nchuan Name: user1-token-m8h8t Namespace: chuan Labels: <none> Annotations: kubernetes.io/service-account.name: user1 kubernetes.io/service-account.uid: b929fc62-fa9c-482d-ac24-ca70cfec5d8e Type: kubernetes.io/service-account-token Data ==== token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ikc1YlhjN0w1SkJhcmRIWkdwRnBzMlM2NFh4dWxWZ0hkVXVwU0I3dWtFWEEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJjaHVhbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1c2VyMS10b2tlbi1tOGg4dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1c2VyMSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImI5MjlmYzYyLWZhOWMtNDgyZC1hYzI0LWNhNzBjZmVjNWQ4ZSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpjaHVhbjp1c2VyMSJ9.BIsBsRAMgKcb8keG-_-2MsSNpIMZtqErzw4bA0_QCzQJYpwAS7xbSCkW2E4YrwnGcXDgTyMljYoayopZwxQrqGqxGY-zvaCzn-uRc3r5h8h2ENidVFDqxtNmhyXXokB-mZ-4ZR1ivqHpXqJN_0CfrTxJTFYI6yIoOt8V0STRUOjWCkhITmhsqvTbj9Ct8YJBUCND7RfJvMOCnfiI2epnCt37TJFCjlpBHy0dc-5H8BCB--2QU5guiNBz9uoPUWg8HowbNIFgCngqsRs4smHCdud7kTkhhA2ZAiw8vlVIoBNoa2DHEr_eVgG1AlTCRjHHqxlEkWVyWoXt95oegvt8Tw ca.crt: 1350 bytes namespace: 5 bytes
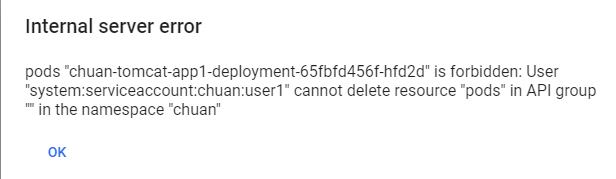
验证,无删除权限
root@slave002:~/role# cat user1_role.yaml kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: namespace: chuan name: user1-role rules: #- apiGroups: ["*"] # resources: ["pods/exec"] # verbs: ["*"] ##RO-Role #verbs: ["get", "list", "watch", "create"] - apiGroups: ["*"] resources: ["pods"] #verbs: ["*"] ##RO-Role verbs: ["get", "list", "watch"] - apiGroups: ["apps/v1"] resources: ["deployments"] verbs: ["get", "list", "watch", "create", "update", "patch", "delete"] ##RO-Role #verbs: ["get", "watch", "list"]
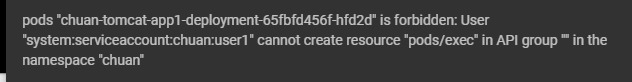
验证无创建pod权限
二:基于kube-config文件登录
1:创建csr文件:
root@slave002:~/pem# cat user1-csr.json { "CN": "China", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "ST": "BeiJing", "L": "BeiJing", "O": "k8s", "OU": "System" } ] }
2,签发证书
root@slave002:~/pem# cfssl gencert -ca=/etc/kubernetes/ssl/ca.pem -ca-key=/etc/kubernetes/ssl/ca-key.pem -config=/etc/kubeasz/clusters/k8s-01/ssl/ca-config.json -profile=kubernetes user1-csr.json | cfssljson -bare user1
root@slave002:~/pem# ls user1-csr.json user1-key.pem user1.csr user1.pem
3:生成普通用户kubeconfig文件
root@slave002:~/pem# kubectl config set-cluster cluster1 --certificate-authority=/etc/kubernetes/ssl/ca.pem --embed-certs=true --server=https://192.168.192.153:6443 --kubeconfig=user1.kubeconfig
4:设置客户端认证参数:
# cp *.pem /etc/kubernetes/ssl/ # kubectl config set-credentials user1 \ --client-certificate=/etc/kubernetes/ssl/user1.pem \ --client-key=/etc/kubernetes/ssl/user1-key.pem \ --embed-certs=true \ --kubeconfig=user1.kubeconfig
5:设置上下文参数
kubectl config set-context cluster1 \ --cluster=cluster1 \ --user=user1 \ --namespace=chuan \ --kubeconfig=user1.kubeconfig
6,验证