k8s-ingress nginx(https证书,ingress nginx常用语法,ingress设置方式)
目录
1、ingress种类
1、Nginx Ingress:实时将ingress配置清单的内容转变成nginx配置,类似动态nginx配置
2、treafik:原生支持k8s
3、istio:服务网格,解决问题:服务治理,流量策略转发,流量安全认证。超大型公司使用,超大流量,维护成本很高
2、ingress nginx
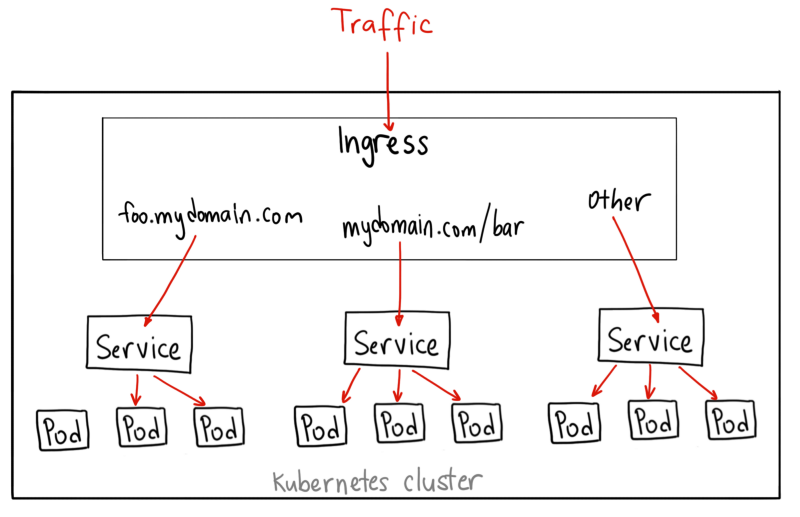
ingress主要作用
service主要作用:提供负载均衡
ingress主要作用:提供域名转发集群流量入口
ingress nginx工作原理
根据ingress配置清单,实时生成Nginx配置,并且使其生效,之后通过nginx反向代理转发流量到pod中。
Nginx配置文件:vi /etc/nginx/nginx.conf
nginx ingress : 性能强
traefik :原生支持k8s
istio : 服务网格,服务流量的治理
ingress:“反向代理”的一种抽象,简单的说就是一个全局的负载均衡器,可以通过访问URL定位到后端的Service
原理:根据ingress配置清单,实时生成Nginx配置,并且使其生效,之后通过nginx反向代理转发流量到pod中。
https://kubernetes.github.io/ingress-nginx/deploy/#bare-metal-clusters
官方下载部署ingress nginx
官方下载的镜像拉不下来,需要想办法
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.0.5/deploy/static/provider/baremetal/deploy.yaml
[root@sg-14 ingress]# cat deploy.yaml |grep image
image: k8s.gcr.io/ingress-nginx/controller:v1.0.5@sha256:55a1fcda5b7657c372515fe402c3e39ad93aa59f6e4378e82acd99912fe6028d
imagePullPolicy: IfNotPresent
image: k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1@sha256:64d8c73dca984af206adf9d6d7e46aa550362b1d7a01f3a0a91b20cc67868660
imagePullPolicy: IfNotPresent
image: k8s.gcr.io/ingress-nginx/kube-webhook-certgen:v1.1.1@sha256:64d8c73dca984af206adf9d6d7e46aa550362b1d7a01f3a0a91b20cc67868660
imagePullPolicy: IfNotPresent
#####k8s.gcr.io镜像会下载失败,替换
部署:kubectl apply -f deploy.yaml
# 下载
wget kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v0.47.0/deploy/static/provider/baremetal/deploy.yaml
329行spec下加一行:hostNetwork:true
332行修改阿里云image镜像:
阿里云镜像首页:http://dev.aliyun.com/去搜索ingress-nginx镜像
下载安装ingress-测试通过
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.19.0/deploy/mandatory.yaml
kubectl apply -f mandatory.yaml
检查:kubectl get pods -n ingress-nginx -o wide
详情:kubectl describe -n ingress-nginx svc default-http-backend
ingress部署
ingress.yaml
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress
namespace: default
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
rules:
- host: www.test.com
http:
paths:
- path: /
backend:
serviceName: service ## 指定service
servicePort: 80
- host: www.abc.com
http:
paths:
- path: /
backend:
serviceName: service_svc ## 指定service
servicePort: 80
service部署一个测试service将端口暴露出去
apiVersion: v1
kind: Service
metadata:
name: nginx
spec:
selector:
app: nginx
ports:
- name: http
port: 80
targetPort: 80
protocol: "TCP"
- name: https
port: 443
targetPort: 443
protocol: "TCP"
pod部署一个测试nginx
apiVersion: v1
kind: Pod
metadata:
name: nginx
labels:
app: nginx
spec:
containers:
- name: nginx
image: ngin
从ingress到pod的流程
从ingress到pod的流程:
ingress ---> endprints(HeadLess Service无头CluserIP service) ---> pod
访问
添加本地hosts文件
192.168.0.214 www.test.com
访问:
192.168.0.214:31220
www.test.com:31220 都可以正常访问
3、模拟本地创建https证书
官方文档
https://kubernetes.github.io/ingress-nginx/user-guide/tls/
1、创建HTTPS证书
openssl genrsa -out tls.key 2048 //创建私钥
openssl req -new -x509 -key tls.key -out tls.crt -subj /C=CN/ST=ShangHai/L=ShangHai/O=Ingress/CN=www.test.com //创建证书
2、部署证书
kubectl -n default create secret tls ingress-tls --cert=tls.crt --key=tls.key
secret/ingress-tls created // 添加到secret资源
验证:
[root@sg-14 TLS]# kubectl get secrets -n ingress-nginx
NAME TYPE DATA AGE
default-token-bx64d kubernetes.io/service-account-token 3 4h12m
ingress-tls kubernetes.io/tls 2 81s
nginx-ingress-serviceaccount-token-tqb48 kubernetes.io/service-account-token 3 4h12m
3、创建Ingress
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
tls:
- hosts:
- www.test.com
- secretName: ingress-tls # secret名字
rules:
- host: www.test.com
http:
paths:
- path: /
backend:
serviceName: nginx
servicePort: 80
4、查看ingress暴露的443端口
[root@sg-14 ingress]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S)
nginx NodePort 192.163.51.88 <none> 80:31220/TCP,443:30306/TCP 6h13m
5、浏览器访问
https://www.test.com:30306/
4、nginx ingress常用语法
官方文档
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#permanent-redirect
域名重定向
# 域名重定向(不能重定向 / )
nginx.ingress.kubernetes.io/rewrite-target
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com/s?wd=nginx
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /
backend:
serviceName: wordpress-nginx
servicePort: 80
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/permanent-redirect: https://www.baidu.com
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /
backend:
serviceName: wordpress-nginx
servicePort: 80
设置ingress白名单
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/whitelist-source-range: 192.168.15.53,192.168.15.52
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /
backend:
serviceName: wordpress-nginx
servicePort: 80
使用正则的方式匹配
# 使用正则的方式匹配(支持的正则比较少)
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: ingress-ingress-nginx-tls
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/rewrite-target: https://www.baidu.com/s?wd=$1
spec:
rules:
- host: www.test-nginx.com
http:
paths:
- path: /search/(.+)
backend:
serviceName: wordpress-nginx
servicePort: 80
# nginx登录
https://kubernetes.github.io/ingress-nginx/examples/auth/basic/
5、设置ingress nginx常用用法的方式
有两种方式:
1、注解 : 当前ingress生效
2、configMap : 全局ingress生效
详细介绍见官方文档:
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/configmap/
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/
选择了IT,必定终身学习


 浙公网安备 33010602011771号
浙公网安备 33010602011771号