TCP数据包格式与实际抓包数据总结
TCP数据包格式与实际抓包数据总结
TCP(Transmission Control Protocol)传输控制协议,是一种面向连接的、可靠的、基于字节流的传输层通信协议。
所谓面向连接的、可靠的协议是:在传输数据前,会与对方进行确认,确认可行后,再传输。反言之就不面向连接、非可靠的的传输协议(UDP)。
这里需要强调的是,两种协议不能用优劣或好坏来评判,取决于应用场景。原因:面向连接的、可靠的协议性能是优点,反之也是缺点---就是婆婆妈妈的费时间,效率低;用在要求精确的一些数据传输较好。而非面向连接的、非可靠的协议,是不婆婆妈妈且效率高,缺点是容易丢数据,在一些场合就比较合适,如用在传送实时监控画面,连续感胜过清晰度(也就是看视频时,不卡顿比清晰度高好)。
TCP是端口到端口的连接协议。所谓端口到端口,就如住在两个小区的朋友,相互寄快递(如:上大路100弄80号),其中小区大门号100弄就相当于IP地址,但小区里的人家可多了,就得指定单元门牌号80,这样就能准确沟通,反过来寄快递也是如此。也就是一台电脑相当一个小区需要用IP地址标识,每台电脑上应用程序和服务多种多样需要用端口号PORT来标识。而这PORT端口号,有些是约定俗成的,有些完全可以由我们来指定。
查询端口号:
C:\Users\admin>netstat -na
活动连接
协议 本地地址 外部地址 状态
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP包结构:
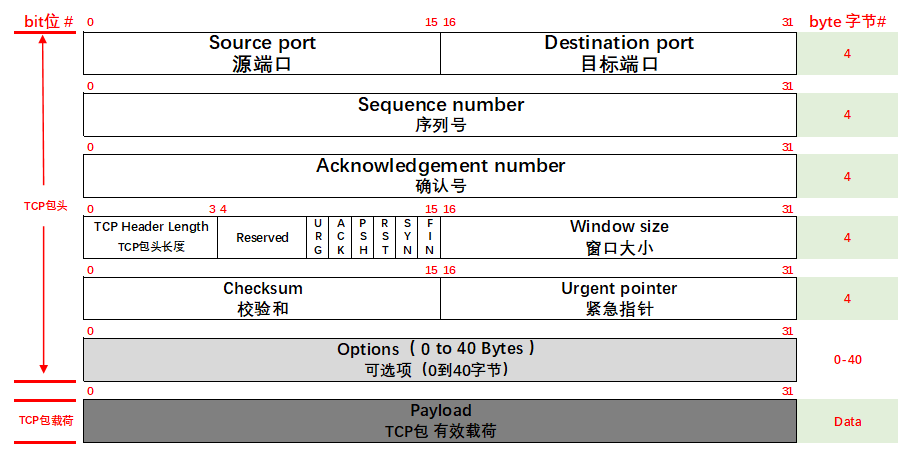
Source port 源端口发送端随机产生:端口是传输层与应用层的服务接口。
Destination port 目的端口为接收端服务的端口:端口是传输层与应用层的服务接口。
Sequence number 序列号:TCP连接中传送的数据流中的每一个字节都编上一个序号。序号字段的值则指的是本报文段所发送的数据的第一个字节的序号。
Acknowledgment number 应答号码:这两个编号用来保证数据的可靠性传输;是收到对方的下一个报文段的数据的第一个字节的序号。
Header length 头长度:TCP报文段的数据起始处距离 TCP报文段的起始处有多远。“
Flags 标志位解释
Reserved 为保留字段——占6bit,保留为今后使用,但目前应置为0。
URG 为1表示高优先级数据包,紧急指针字段有效。
ACK 为1表示确认号字段有效
PSH 为1表示是带有PUSH标志的数据,指示接收方应该尽快将这个报文段交给应用层而不用等待缓冲区装满。
RST 为1表示出现严重差错。可能需要重现创建TCP连接。还可以用于拒绝非法的报文段和拒绝连接请求。
SYN 为1表示这是连接请求或是连接接受请求,用于创建连接和使顺序号同步
FIN 为1表示发送方没有数据要传输了,要求释放连接。
Window size 窗口尺寸:窗口尺寸用来控制对方发送的数据量,单位为字节。TCP连接的一端根据设置的缓存空间大小确定自己的接收窗口大小,然后通知对方以确定对方的发送窗口的上限。
Checksum 检验和:检验和字段检验的范围包括首部和数据这两部分。
Urgent pointer 紧急指针字段:紧急指针指出在本报文段中的紧急数据的最后一个字节的序号。
Opetions 可选项:TCP首部可以有多达40字节的可选信息,用于把附加信息传递给终点,或用来对齐其它选项。
Payload 有效载荷:这是为了使整个首部长度是4字节的整数倍。
TCP建立连接(三次握手建立连接)
关于建立连接,其实就是用标记位定义的意思,在两方来回问答,实现发送方与接收方两方数据传输前准备工作。
1. C电脑 发给 S电脑 一个SYN = 1信号,意思是我要同步一下(相当于连接请求信号)
2. S电脑 回传并发给 C电脑 一个ACK = 1, SYN=1 信号,意思是我同意同步(相当于你的连接请求,我确认可以;我也想连接可以不?)
3. C电脑 再发给 S电脑 一个ACK = 1信号,意思是我也同意(我也确认可以)
在此要注意的是,两台电脑,可能有很多个连接确认,那些应答进行配对呢?通过SEQ序列号来此标记(SEQ加不加1对于理解无所谓的,只是一种配对的确认算法):
从以上可以看出,C电脑有一次问,得到一次答;S电脑也有一次问,得到一次答;
只是第二步是将S电脑的要问的,及它的答复一次性给出,即两步并一步做了。
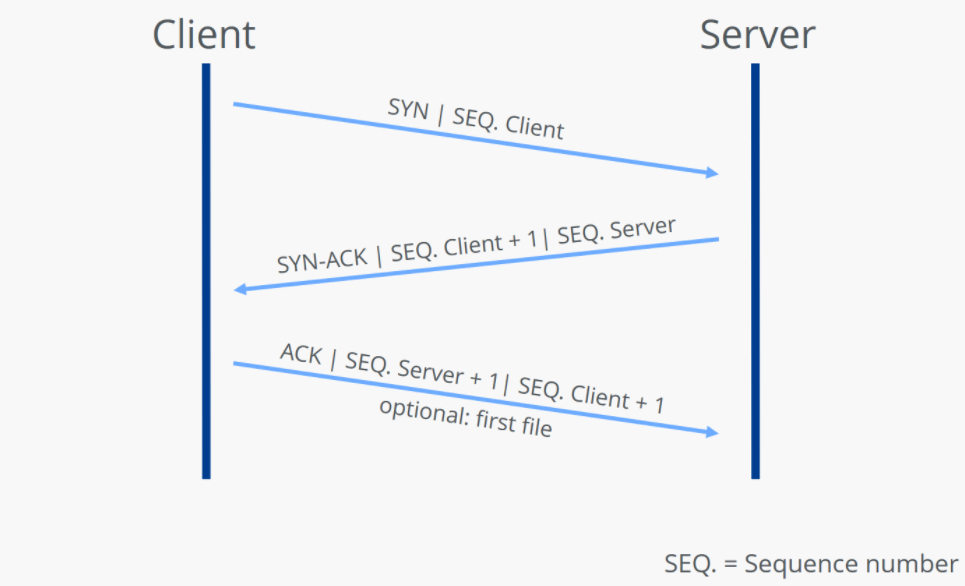
如下图,标识的同步为1,意思就是在问我要和您同步传输数据?其他标记位以此类推。

三次握手建立连接过程 (第二行 数据注意观察,一次发 SYN 和 ACK 标识,二步并一步做)
TCP拆除连接(四次握手拆除连接)(SEQ加不加1对于理解无所谓的,只是一种配对的确认算法)
1. C电脑 发给 S电脑 一个FIN = 1信号,意思是我要下线了(相当于下线请求信号)
2. S电脑 回传并发给 C电脑 一个ACK=1 信号,意思是我同意下线(相当于您的下线请求,我确认哈)
3. S电脑 又回传并发给 C电脑 一个FIN=1 信号,意思是我也下线(相当于回一个下线请求信号)
4. C电脑 再发给 S电脑 一个ACK = 1信号,意思是我也同意(我也确认下线)
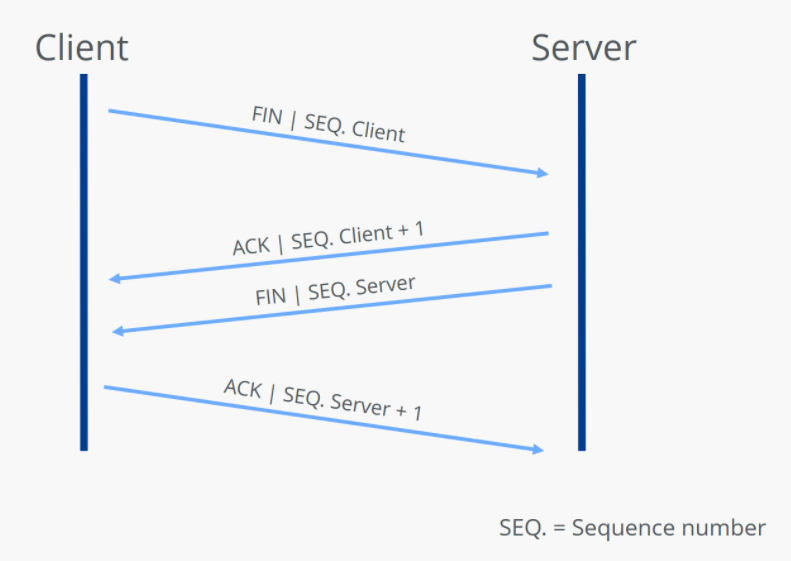
从以上可以看出,C电脑有一次问,得到一次答;S电脑也有一次问,得到一次答;
但与建立连接不同,是将S电脑的要回答的也要问的,分成两步做的,所以有共4步。
其实与建立连接是一个套路。就是中间有点差别:一个是两件事一步做,另一个两件事两步做。
如下图,标识的FIN下线信号为1,意思就是在问我要下线了?其他标记位以此类推。
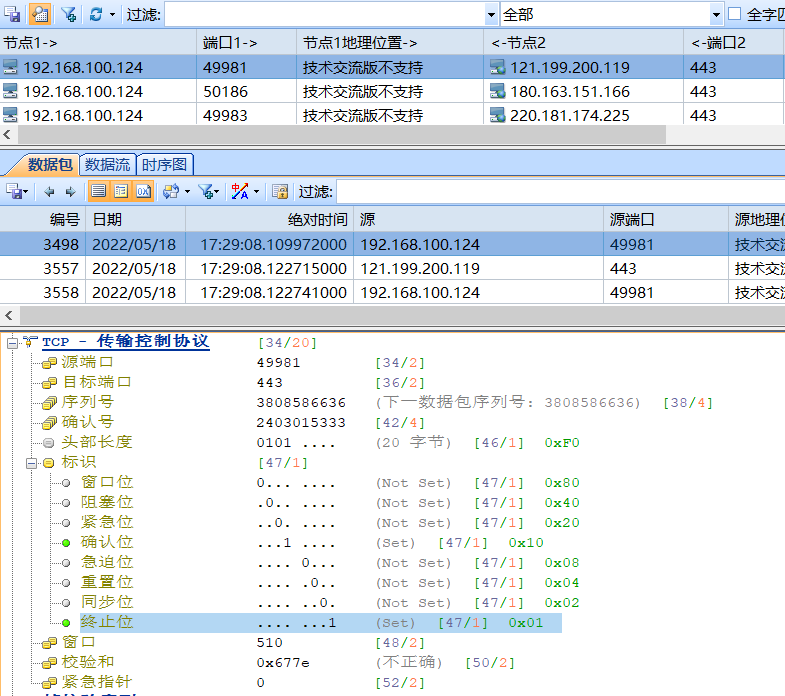
四次握手拆除连接(其中FIN标识发出的同时,多发了个ACK标识,不影响执行和理解)

以下是外网摘录的总结:
Summary of key facts about the Transmission Control Protocol
The TCP protocol has shaped the history and development of computer networks for nearly a half a century. TCP can be easily combined with Internet protocol (IP), which also has a long history, and it has many advantages over other alternatives such as UDP and SCTP. The most important features can be summarized as follows:
- TCP is connection-oriented and enables two-way communication between two endpoints after the three-way handshake.
- TCP is reliable because the protocol ensures that all data is fully transmitted and can be assembled by the receiver in the correct order.
- TCP allows data to be sent in individual segments of up to 1,500 bytes (including headers) in size.
- TCP is positioned at the transport layer (layer 4) of the OSI model.
- TCP is usually used in conjunction with the Internet Protocol (IP) and is commonly known as the TCP/IP protocol stack.
- The TCP header has a default size of 20 bytes. Up to 40 bytes of additional options can be added.

Structure of a TCP header
The individual components or fields of the header of the TCP protocol have the following meaning:
Source port (16 bits): Identifies the port number of the sender.
Destination port (16 bits): Identifies the port number of receiver.
Sequence number (32 bits): The sequence number specifies the first byte of attached payload data or is sent when the connection is established or terminated. It is also used for validating and sorting the segments after transmission.
Acknowledgment number (32 bits): This field contains the next sequence number that the sender is expecting. An ACK flag (in the “Flags” field) is a precondition for validity.
Offset (4 bits): The “Offset” field specifies the length of the TCP header in 32-bit words to highlight the starting point of the payload data. This starting point varies from segment to segment due to the variable “Options” field.
Reserved (6 bits): Reserved for future use according to RFC 793 and not yet in use. This field must always be set to 0.
Flags (6 bits): The six possible single bits in the “Flags” field enable various TCP actions for organizing communication and data processing. The following flags are either set or not set for these actions:
- URG: The "Urgent" flag signals to the TCP application that the payload data must be processed immediately up to the set Urgent pointer (see above).
- ACK: In combination with the acknowledgment number, the ACK flag acknowledges the receipt of TCP packets. If the flag is not set, the confirmation number is also invalid.
- PSH: The "Push" flag ensures that a TCP segment is immediately pushed through without first being sent to the buffer of the sender and receiver.
- RST: If there is an error during transmission, a TCP packet with the RST flag set can be used to reset the connection.
- SYN: Messages that have SYN flag set represent the first step of the three-way handshake, meaning they initiate the connection.
- FIN: The "Finish" flag signals to the other party that a sender is ending the transmission.
Window size (16 bits): This field specifies the number of bytes that the sender is willing to receive.
Checksum (16 bits): The Transmission Control Protocol can reliably detect transmission errors. The checksum calculated from the header, the payload data and the pseudo-header is used for this purpose.
Urgent pointer (16 bits): The urgent pointer indicates the position of the first byte after the payload data that is to be processed urgently. As a result, this field is only valid and relevant if the URG flag is set.
Options (0 - 320 bits): Use the Options field if you want to include TCP functions that don’t belong in the general header, for example if you want to define the maximum segment size. The length of the options must always be a multiple of 32, otherwise zero-bit padding is required.
What is Transmission Control Protocol (TCP)?
TCP (Transmission Control Protocol) is one of the main protocols of the Internet protocol suite.
It lies between the Application and Network Layers which are used in providing reliable delivery services.
It is a connection-oriented protocol for communications that helps in the exchange of messages between the different devices over a network.
Working of TCP
To make sure that each message reaches its target location intact, the TCP/IP model breaks down the data into small bundles and afterward reassembles the bundles into the original message on the opposite end. Sending the information in little bundles of information makes it simpler to maintain efficiency as opposed to sending everything in one go.
After a particular message is broken down into bundles, these bundles may travel along multiple routes if one route is jammed but the destination remains the same.
We can see that the message is being broken down, then reassembled from a different order at the destination
For example, When a user requests a web page on the internet, somewhere in the world, the server processes that request and sends back an HTML Page to that user. The server makes use of a protocol called the HTTP Protocol. The HTTP then requests the TCP layer to set the required connection and send the HTML file.
Now, the TCP breaks the data into small packets and forwards it towards the Internet Protocol (IP) layer. The packets are then sent to the destination through different routes.
The TCP layer in the user’s system waits for the transmission to get finished and acknowledges once all packets have been received.
Features of TCP
Some of the most prominent features of Transmission control protocol are
1. Segment Numbering System
TCP keeps track of the segments being transmitted or being received by assigning numbers to each and every single one of them.
A specific Byte Number is assigned to data bytes that are to be transferred while segments are assigned sequence numbers.
Acknowledgment Numbers are assigned to received segments.
2. Flow Control
Flow control limits the rate at which a sender transfers data. This is done to ensure reliable delivery.
The receiver continually hints the sender on how much data can be received (using a sliding window)
3. Error Control
TCP implements an error control mechanism for reliable data transfer
Error control is byte-oriented
Segments are checked for error detection
Error Control includes – Corrupted Segment & Lost Segment Management, Out-of-order segments, Duplicate segments, etc.
4. Congestion Control
TCP takes into account the level of congestion in the network
Congestion level is determined by the amount of data sent by a sender
Advantages
It is a reliable protocol
It provides an error-checking mechanism as well as one for recovery
It gives flow control
It makes sure that the data reaches the proper destination in the exact order that it was sent
Open Protocol, not owned by any organization or individual
It assigns an IP address to each computer on the network and a domain name to each site thus making each device site to be distinguishable over the network.
Disadvantages
TCP is made for Wide Area Networks, thus its size can become an issue for small networks with low resources
TCP runs several layers so it can slow down the speed of the network
It is not generic in nature. Meaning, it cannot represent any protocol stack other than the TCP/IP suite. E.g., it cannot work with a Bluetooth connection.
No modifications since their development around 30 years ago.
How exactly do TCP connections work?
TCP allows for transmission of information in both directions. This means that computer systems that communicate over TCP can send and receive data at the same time, similar to a telephone conversation. The protocol uses segments (packets) as the basic units of data transmission. In addition to the payload, segments can also contain control information and are limited to 1,500 bytes. The TCP software in the network protocol stack of the operating system is responsible for establishing and terminating the end-to-end connections as well as transferring data.
The TCP software is controlled by the various network applications, such as web browsers or servers, via specific interfaces. Each connection must always be identified by two clearly defined endpoints (client and server). It doesn’t matter which side assumes the client role and which assumes the server role. All that matters is that the TCP software is provided with a unique, ordered pair consisting of IP address and port (also referred to as "2-tuple" or "socket") for each endpoint.
The three-way handshake: How a TCP connection is established in detail
Prerequisites for establishing a valid TCP connection: Both endpoints must already have a unique IP address (IPv4 or IPv6) and have assigned and enabled the desiredport for data transfer. The IP address serves as an identifier, whereas the port allows the operating system to assign connections to the specific client and server applications.
The actual process for establishing a connection with the TCP protocol is as follows:
1.First, the requesting client sends the server a SYN packet or segment (SYN stands for synchronize) with a unique, random number. This number ensures full transmission in the correct order (without duplicates).
2.If the server has received the segment, it agrees to the connection by returning a SYN-ACK packet (ACK stands for acknowledgment) including the client's sequence number plus 1. It also transmits its own sequence number to the client.
3.Finally, the client acknowledges the receipt of the SYN-ACK segment by sending its own ACK packet, which in this case contains the server's sequence number plus 1. At the same time, the client can already begin transferring data to the server.
TCP connection establishment (Three way handshake)

TCP teardown: How a controlled TCP connection termination works
Both sides of a connection can terminate a TCP connection, and even one-sided termination is also possible. This is also known as a half-open connection, whereby the other side is still allowed to transfer data even if one side has already disconnected.
The individual steps of two-way termination (initiated by the client for the sake of simplicity in this example) can be summarized as follows:
1.The client sends a FIN segment to notify the server that it no longer wants to send data. It sends its own sequence number, just as it does when the connection is established.
2.The server acknowledges receipt of the package with an ACK segment that contains the sequence number plus 1.
3.When the server has finished the data transfer, it also sends a FIN packet, to which it adds its sequence number.
4.Now it is the client's turn to send an ACK packet including the sequence number plus 1, which officially terminates the TCP connection for the server.
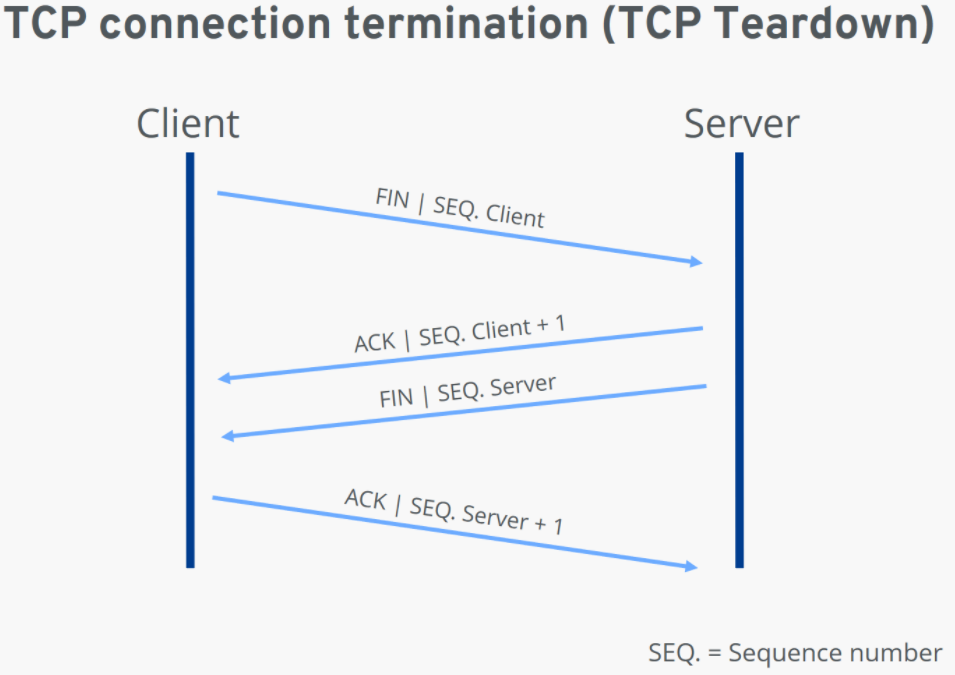
However, the connection is not immediately terminated for the side that sent the last ACK segment (in our case, the client). Since there’s no guarantee that the last packet sent has actually arrived, the client or server will initially remain in time-wait state until the maximum lifetimes of the ACK segment and any new FIN segments (according to RFC 793, two minutes for each segment) have expired.





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 三行代码完成国际化适配,妙~啊~
· .NET Core 中如何实现缓存的预热?