先不说废话,资料先甩上来:
代码托管 github:
ATouch安卓APP源码:https://github.com/guanglun/ATouch 【开发环境:AndroidStudio】
ATouch板子源码:https://github.com/guanglun/ESP32_CH374U 【开发环境:Linux SDK:ESP-DIF3.2】
ATouch安卓后台程序源码: https://github.com/guanglun/ATouchService 【开发环境:android-ndk-r13b】
APP下载地址: https://github.com/guanglun/ATouch/blob/master/app/release/ATouchV1.0.apk
代码托管 gitee:
ATouch安卓APP源码:https://gitee.com/guanglunking/ATouch 【开发环境:AndroidStudio】
ATouch板子源码:https://gitee.com/guanglunking/ESP32_CH374U 【开发环境:Linux SDK:ESP-DIF3.2】
ATouch安卓后台程序源码: https://gitee.com/guanglunking/ATouchService 【开发环境:android-ndk-r13b】
APP下载地址: https://gitee.com/guanglunking/ATouch/blob/master/app/release/ATouchV1.0.apk
淘宝店铺:https://item.taobao.com/item.htm?id=595635571591
演示视频:https://www.bilibili.com/video/av53687214
说起这个项目的起源,可能大概也许是源于自己用手搓手机菜的抠脚吧,也或许是因为对开发的热情大过于玩的热情哈哈,反正这个东西反反复复得折腾了半年之久了,对这个东西的定位也渐渐从做一个人人都能玩的商品到单纯做一个有吃鸡功能的开发板。现在把他开源出来,也算是回报互联网上良多开源的资料教程吧!
光轮电子产品交流群:558343678 欢迎交流学习
从上面的资料可以看到有三份源码,其中两份(APP和板子源码)还可以理解,另外那个后台源码是啥东西?干啥的?这个还要从实现安卓模拟触屏的功能谈起,主要是因为手机APP无法实现触摸非己界面的功能,而我们有需要在游戏运行的时候触摸屏幕该怎么办呢?解决办法是使用android的ndk开发实现一段后台程序来对触屏文件/dev/input/event进行写操作来实现,所以相对要复杂一些,下面是整个交互的流程概括:
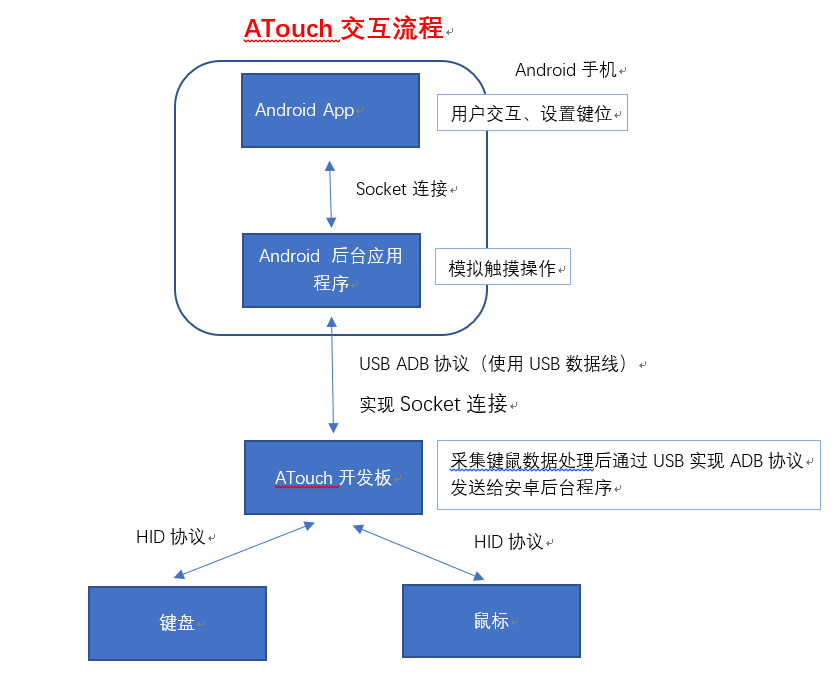
流程说明:
1.CH374U是一个支持8位并口或者SPI的3端USBHUB芯片,将他通过8位并口与ESP32连起来为ESP32实现了3个USB端口的操作。
2.ESP32通过CH374U模拟ADB协议与手机连接,手机需要打开开发者模式。连接成功后使用端口映射 adb forward tcp:local_port tcp:remote_port 来将安卓后台程序ATouchService与开发板ESP32_CH374U建立socket的通讯连接。
3.ESP32通过CH374U采集键盘鼠标数据(USB HID协议),如果已连接手机就将数据打包发送至手机后台程序ATouchService。
4.后台程序ATouchService将接收到的键鼠信息进行处理,如果此时APPATouch配置并开启了键鼠映射就将其键鼠对应的控制信息发送至手机的 /dev/input/event 文件模拟触摸操作。
程序问题总结:
1.源码中如下N E D P Q是如何算出来的?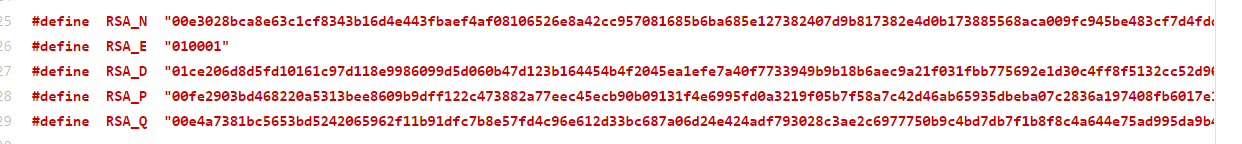
这是从私钥中解出的算子,使用openssl:
[root@docker121 ssl]# openssl rsa -in private.pem -text -noout #不输出私钥内容 Private-Key: (1024 bit) modulus: 00:aa:08:dd:7f:a1:46:96:be:38:cc:2d:ea:bb:0a: a3:cc:2e:84:ce:84:61:d1:aa:0c:18:59:48:54:15: 3a:33:3f:8a:bd:e1:4b:7b:b8:37:cb:55:2d:08:3b: 4a:b0:77:2e:26:a5:8e:8b:4b:8f:a5:2c:84:2d:54: 35:2b:6e:62:ae:17:cf:b4:e6:f3:f9:30:6f:ea:52: ab:fc:83:9e:f8:a6:2e:e7:f7:2b:be:61:e0:c6:10: 09:0b:9c:32:d1:a4:61:54:8b:06:f5:3e:56:2c:7c: 59:c9:bf:8e:b4:7a:64:fa:6d:c6:4e:56:11:7c:8f: f4:d3:74:e7:84:51:31:e9:15 publicExponent: 65537 (0x10001) privateExponent: 75:dd:61:55:18:81:6a:fa:ff:3a:21:d6:25:c3:b1: 59:57:21:be:5a:2b:c8:7f:9c:94:c0:47:0f:ea:0b: 06:fd:53:fa:5d:92:ca:77:1f:4d:f6:84:19:c1:a7: fb:7d:11:e3:be:3d:7a:37:6d:a2:6c:a2:4f:1d:a1: 21:b3:09:f9:4c:1c:0b:4f:3e:fa:82:13:85:02:42: 18:60:cb:6f:e3:e0:a5:54:2a:c3:26:b5:39:12:cf: 46:7d:b3:d6:f2:2e:1e:aa:f1:76:f5:bc:9b:17:f1: 25:9c:59:15:e0:96:7e:55:59:14:46:15:62:a1:f9: 2a:1d:b9:0a:90:a8:25:7d prime1: 00:df:a1:2c:95:d1:f6:e5:1c:37:89:a1:d6:14:49: 0e:9b:9d:2c:ec:1d:be:bd:b4:de:bb:0f:57:cc:65: 30:a3:28:89:7e:a7:31:1b:d0:b0:52:30:85:db:01: a8:97:e2:11:20:71:b3:47:e8:66:8c:ec:d4:9b:b6: ee:7d:85:26:87 prime2: 00:c2:a5:ac:a9:80:7d:53:97:f4:e8:dc:60:b2:90: 6e:7b:9b:91:87:ab:95:91:61:b9:f2:34:b3:6d:bc: fa:9e:e7:9b:b0:a6:54:8b:cf:b3:7c:d8:3a:77:ce: 23:10:68:60:33:08:d3:7a:b4:fd:eb:63:20:7d:b0: d1:47:91:be:83 exponent1: 45:fb:6d:35:71:60:7f:30:46:5d:06:cd:34:c9:ec: 0d:5c:b1:7b:2e:8f:cb:54:37:c3:78:38:b4:99:12: 10:6d:16:22:11:76:37:cb:25:f2:82:86:d1:13:82: cc:0d:0d:e9:06:4b:e1:7b:e3:e3:c4:15:80:a9:4d: 96:f0:3d:2f exponent2: 13:77:f4:b4:23:78:e5:92:8e:59:78:29:67:d2:d0: 6a:26:9e:40:be:a5:c0:1b:d1:38:6b:93:02:c7:e3: 1d:5f:b7:0f:cd:23:29:b4:c5:94:18:20:88:f9:22: 42:b2:dd:e4:5c:de:a2:28:56:39:63:f9:cc:f8:91: 86:22:0a:b7 coefficient: 00:95:69:1f:82:34:21:ac:6c:f8:b8:06:b4:46:dd: 79:e4:b0:0a:32:20:cf:21:48:3b:1b:fe:34:60:b2: f5:d9:a9:e0:8a:23:74:43:2e:cc:09:99:dc:54:d2: df:3a:5b:c4:0d:b3:4b:88:95:a8:3f:85:d9:4f:f4: cf:16:55:da:7c
2.ADB校验流程?
详见博客:https://www.cnblogs.com/guanglun/p/10126727.html