OpenSCAP的基础使用方法
大背景
信息安全态势日趋严重,对我们网络安全工作提出了更高的要求,遵循一定的网络安全框架的同时,我们需要在各个不同的环节部署不同的安全措施形成纵深防御体系。
服务器侧的安全基线在安全管理中是一个基础性的工作,是整个体系中不可缺少的一环,但是也是一个比较麻烦的工作,一方面是因为企业中通常服务器数量较多,有各种不同版本的操作系统;
另外一方面是因为企业通常没有能力去制定适合自己的安全基线,或者大多数的安全基线都是安全人员“想当然”制定的,从各种渠道摘抄汇总,然后进行取舍而来。带来的问题是基线缺失、基线不完整等等。
在没有购买商业产品的情况下,要么我们自己写脚本,要么使用开源工具对系统进行基线设置以及进行基线核查。
OpenSCAP的介绍
OpenSCAP 是一个获得SCAP认证的免费开源的自动化扫描,基线核查,报告和自动修复工具,目前主要由 Redhat 进行维护。
OpenSCAP 由 工具 和 基线库 两个部分组成,两者没有紧密的耦合关系,比如使用http://vuls.io也可以运行部分基线库,基线库部分功能也支持使用 ansible 和 bash 来执行。
SCAP,Security Content Automation Protocol,即安全内容自动化协议。是由NIST(National Institute of Standards and Technology,美国国家标准与技术研究院)提出,而且NIST还建立了信息安全类产品的SCAP兼容性认证机制。
SCAP包含了Protocol(协议)与Content(内容),协议是指SCAP由一系列现有的公开标准构成,这些公开标准被称为SCAP Element(SCAP元素),Protocol规范了这些Element之间如何协同工作。Content指按照Protocol的约定,利用Element描述的生成应用于实际检查工作的数据。
openscap由工具集(oscap)及基线库(SSG)组成,其中工具集包括如下:
- OpenSCAP Base 命令行工具,本地扫描
- OpenSCAP Daemon 守护进程工具,功能同 OpenSCAP Base
- SCAP Workbench 图形界面,功能同 SCAP Base,可视化操作
ssg 的xml默认保存目 /usr/share/xml/scap/ssg/content/
支持的扫描安全类型
- 通用漏洞披露 (CVE)
- 通用配置评估 (CCE)
- 通用平台评估 (CPE)
- 通用漏洞评分系统 (CVSS)
- 通用弱点枚举 (CWE)
- The Script Check Engine (SCE)
基础使用
这里主要介绍 OpenSCAP Base 的使用
安装工具
不同系统的略有区别
ubuntu
apt install libopenscap8 -y
Centos
yum install openscap-scanner -y
安装基线库
Centos
Centos的最好安装
yum install scap-security-guide -y
ubuntu
ubuntu需要下载离线包安装
主要下载两部分
- ssg-base
- ssg-debderived
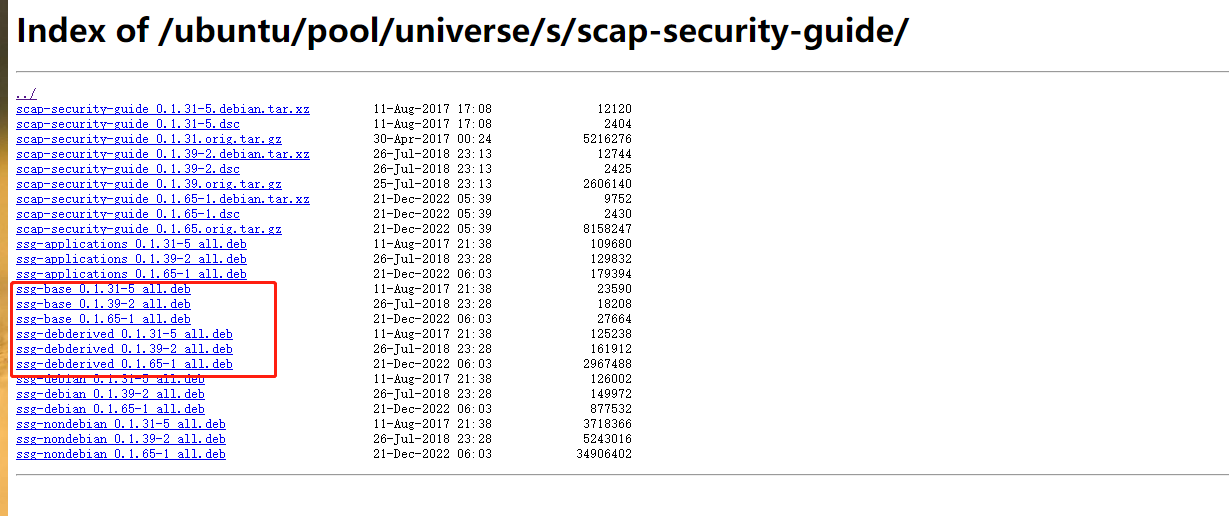
根据版本不同做取舍
ubuntu16.04
wget http://ftp.sjtu.edu.cn/ubuntu/pool/universe/s/scap-security-guide/ssg-base_0.1.39-2_all.deb
wget http://ftp.sjtu.edu.cn/ubuntu/pool/universe/s/scap-security-guide/ssg-debderived_0.1.39-2_all.deb
dpkg -i *.deb
ubuntu22.04
wget http://ftp.sjtu.edu.cn/ubuntu/pool/universe/s/scap-security-guide/ssg-base_0.1.65-1_all.deb
wget http://ftp.sjtu.edu.cn/ubuntu/pool/universe/s/scap-security-guide/ssg-debderived_0.1.65-1_all.deb
dpkg -i *.deb
基础使用
咱们使用这个工具的最基础需求肯定是扫描缺失,然后修复
查看相关信息
Centos
oscap info /usr/share/xml/scap/ssg/content/ssg-rhel7-ds.xml
Document type: Source Data Stream
Imported: 2023-03-07T22:52:18
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel7-xccdf.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-xccdf.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL7.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL7.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL7.xml.bz2' file which is referenced from datastream
Status: draft
Generated: 2023-03-07
Resolved: true
Profiles:
Title: C2S for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_C2S
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_nt28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_nt28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_nt28_intermediary
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_nt28_minimal
Title: CIS Red Hat Enterprise Linux 7 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: CIS Red Hat Enterprise Linux 7 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
Title: CIS Red Hat Enterprise Linux 7 Benchmark for Level 1 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1
Title: CIS Red Hat Enterprise Linux 7 Benchmark for Level 2 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2
Title: Criminal Justice Information Services (CJIS) Security Policy
Id: xccdf_org.ssgproject.content_profile_cjis
Title: Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171)
Id: xccdf_org.ssgproject.content_profile_cui
Title: Australian Cyber Security Centre (ACSC) Essential Eight
Id: xccdf_org.ssgproject.content_profile_e8
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Title: NIST National Checklist Program Security Guide
Id: xccdf_org.ssgproject.content_profile_ncp
Title: OSPP - Protection Profile for General Purpose Operating Systems v4.2.1
Id: xccdf_org.ssgproject.content_profile_ospp
Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_pci-dss
Title: RHV hardening based on STIG for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_rhelh-stig
Title: VPP - Protection Profile for Virtualization v. 1.0 for Red Hat Virtualization
Id: xccdf_org.ssgproject.content_profile_rhelh-vpp
Title: Red Hat Corporate Profile for Certified Cloud Providers (RH CCP)
Id: xccdf_org.ssgproject.content_profile_rht-ccp
Title: Standard System Security Profile for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_standard
Title: DISA STIG for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_stig
Title: DISA STIG with GUI for Red Hat Enterprise Linux 7
Id: xccdf_org.ssgproject.content_profile_stig_gui
Referenced check files:
ssg-rhel7-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel7-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
security-data-oval-com.redhat.rhsa-RHEL7.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-cpe-oval.xml
Ref-Id: scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL7.xml.bz2
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-rhel7-cpe-dictionary.xml
可以看到 Profiles 部分有很多项,分别有 Title 和 Id
这里的 Id 我们就使用 标准的 ,xccdf_org.ssgproject.content_profile_standard
ubuntu
ubuntu16.04
oscap info /usr/share/xml/scap/ssg/content/ssg-ubuntu1604-ds.xml
Document type: Source Data Stream
Imported: 2018-07-26T22:58:28
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-ubuntu1604-xccdf-1.2.xml
Generated: (null)
Version: 1.2
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu1604-xccdf-1.2.xml
Status: draft
Generated: 2018-07-26
Resolved: true
Profiles:
xccdf_org.ssgproject.content_profile_anssi_np_nt28_restrictive
xccdf_org.ssgproject.content_profile_standard
xccdf_org.ssgproject.content_profile_anssi_np_nt28_high
xccdf_org.ssgproject.content_profile_anssi_np_nt28_minimal
xccdf_org.ssgproject.content_profile_anssi_np_nt28_average
Referenced check files:
ssg-ubuntu1604-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-ubuntu1604-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu1604-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu1604-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu1604-cpe-oval.xml
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu1604-cpe-dictionary.xml
这里我们也选择标准的 xccdf_org.ssgproject.content_profile_standard
ubuntu22.04
oscap info /usr/share/xml/scap/ssg/content/ssg-ubuntu2204-ds.xml
Document type: Source Data Stream
Imported: 2022-12-20T09:54:05
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-ubuntu2204-xccdf.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu2204-xccdf.xml
Status: draft
Generated: 2022-12-21
Resolved: true
Profiles:
Title: CIS Ubuntu 22.04 Level 1 Server Benchmark
Id: xccdf_org.ssgproject.content_profile_cis_level1_server
Title: CIS Ubuntu 22.04 Level 1 Workstation Benchmark
Id: xccdf_org.ssgproject.content_profile_cis_level1_workstation
Title: CIS Ubuntu 22.04 Level 2 Server Benchmark
Id: xccdf_org.ssgproject.content_profile_cis_level2_server
Title: CIS Ubuntu 22.04 Level 2 Workstation Benchmark
Id: xccdf_org.ssgproject.content_profile_cis_level2_workstation
Title: Standard System Security Profile for Ubuntu 22.04
Id: xccdf_org.ssgproject.content_profile_standard
Referenced check files:
ssg-ubuntu2204-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-ubuntu2204-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu2204-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu2204-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu2204-cpe-oval.xml
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-ubuntu2204-cpe-dictionary.xml
这里选择标准的 xccdf_org.ssgproject.content_profile_standard
扫描并输出检测报告
#centos
oscap xccdf eval --profile standard --results-arf arf.xml --report report.html /usr/share/xml/scap/ssg/content/ssg-centos7-ds.xml
#ubuntu16.04
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_standard --results-arf arf.xml --report report.html /usr/share/xml/scap/ssg/content/ssg-ubuntu1604-ds.xml
#ubuntu22.04
oscap xccdf eval --profile standard --results-arf arf.xml --report report.html /usr/share/xml/scap/ssg/content/ssg-ubuntu2204-ds.xml
生成的report.html就是网页版报告
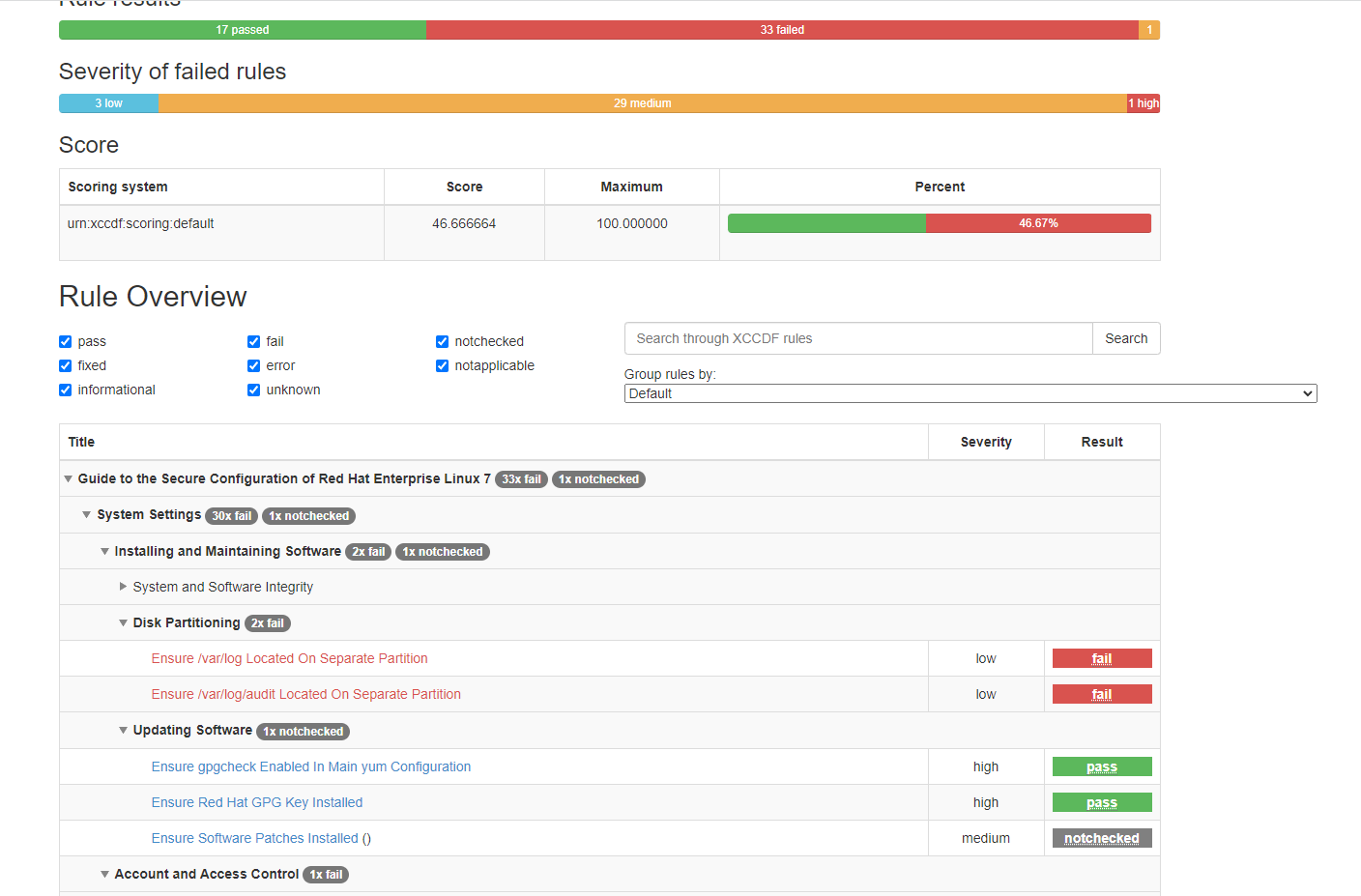
红色的表示需要修复的部分
会给出相应的处理办法以及脚本
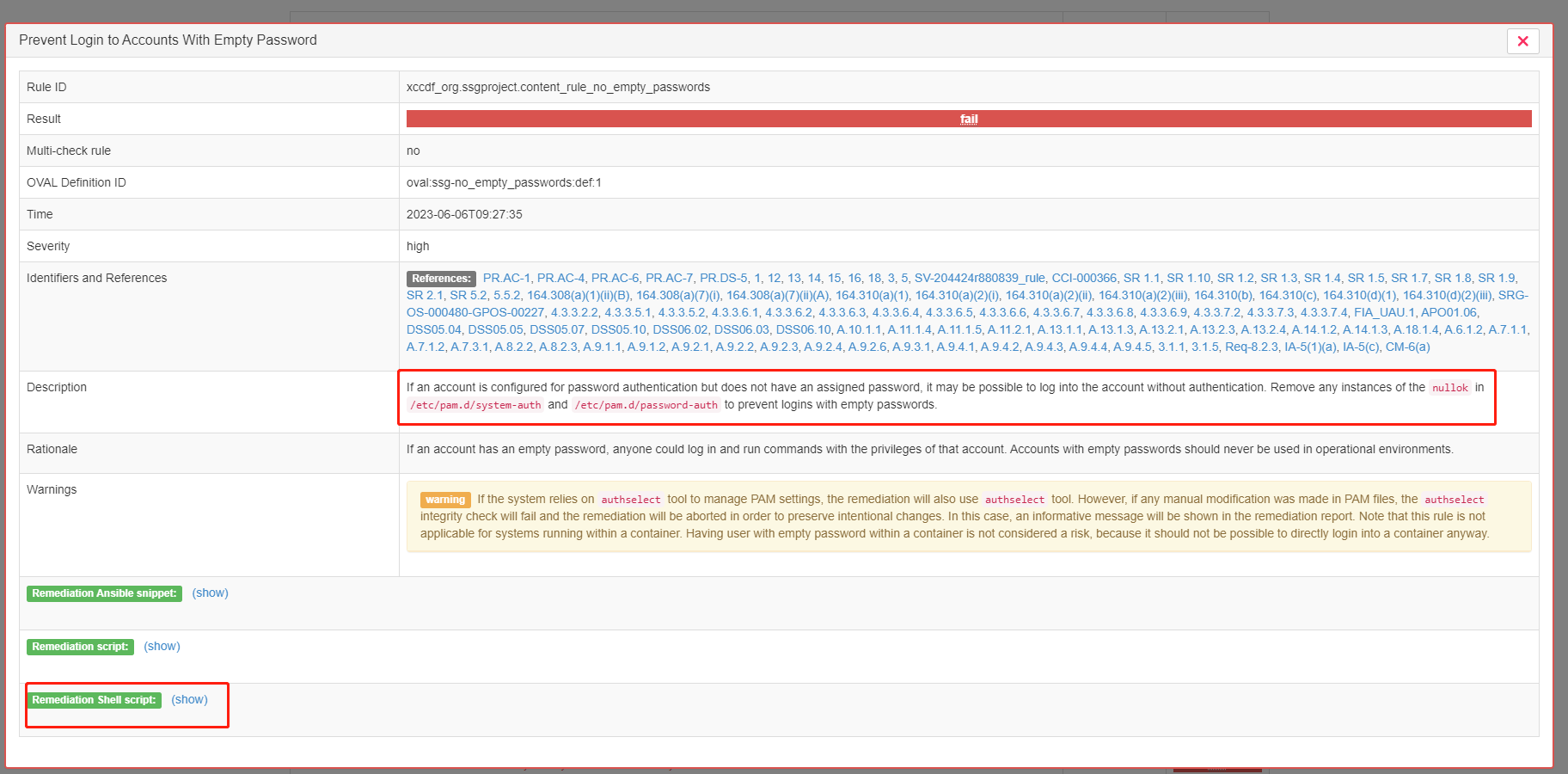
非常方便
扫描直接生成脚本
这里需要说明的是,ubuntu16.04测试了好多方法,是无法生成的,如果有大佬知道如何生成,可以评论补充下
ubuntu22.04
#扫描生成结果
oscap xccdf eval --profile standard --results results.xml --fetch-remote-resources /usr/share/xml/scap/ssg/content/ssg-ubuntu2204-ds.xml
#生成的结果文件
ll results.xml
-rw-r--r-- 1 root root 7433222 Jun 9 02:04 results.xml
#查看结果ID
oscap info results.xml
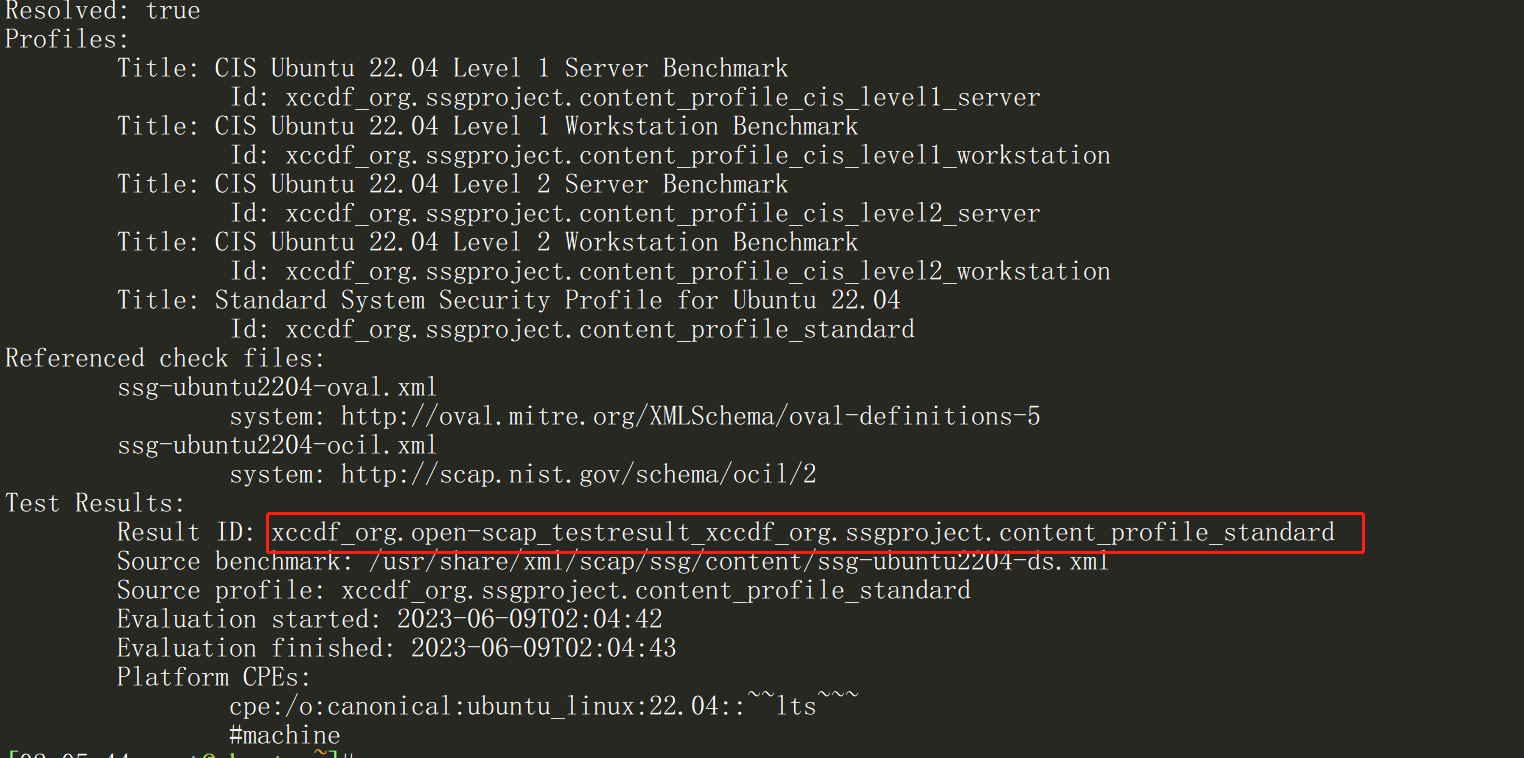
然后根据结果ID 生成脚本
oscap xccdf generate fix --fix-type bash --output my-remediation-script.sh --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_standard results.xml
centos
centos的也类似
oscap xccdf eval --profile standard --results results.xml --fetch-remote-resources /usr/share/xml/scap/ssg/content/ssg-centos7-ds.xml
oscap info results.xml
oscap xccdf generate fix --fix-type bash --output my-remediation-script.sh --result-id xccdf_org.open-scap_testresult_xccdf_org.ssgproject.content_profile_standard results.xml
本文来自博客园,作者:厚礼蝎,转载请注明原文链接:https://www.cnblogs.com/guangdelw/p/17468410.html

