2019 SDN上机第6次作业
1.实验拓扑
实验拓扑图如下:
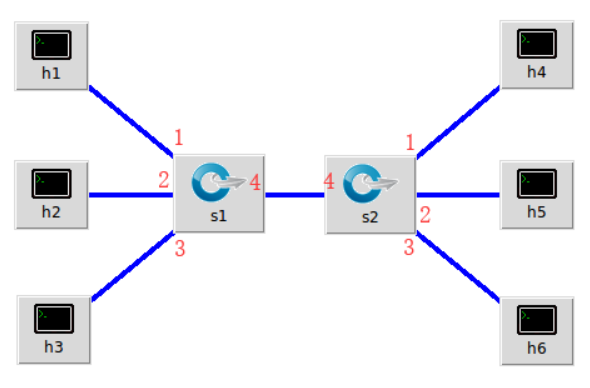
搭建代码如下:
创建py脚本文件,并编写代码,如下:
class MyTopo(Topo):
def __init__(self):
# initilaize topology
Topo.__init__(self)
# add hosts and switches
h1 = self.addHost('h1')
h2 = self.addHost('h2')
h3 = self.addHost('h3')
h4 = self.addHost('h4')
h5 = self.addHost('h5')
h6 = self.addHost('h6')
s1 = self.addSwitch('s1')
s2 = self.addSwitch('s2')
# add links
self.addLink(h1, s1, 1, 1)
self.addLink(h2, s1, 1, 2)
self.addLink(h3, s1, 1, 3)
self.addLink(s1, s2, 4, 4)
self.addLink(h4, s2, 1, 1)
self.addLink(h5, s2, 1, 2)
self.addLink(h6, s2, 1, 3)
topos = {'mytopo': (lambda: MyTopo())}
使用如下命令生成拓扑
sudo mn --custom topo.py --topo mytopo --controller=remote,ip=127.0.0.1,port=6633 --switch ovsk,protocols=OpenFlow13
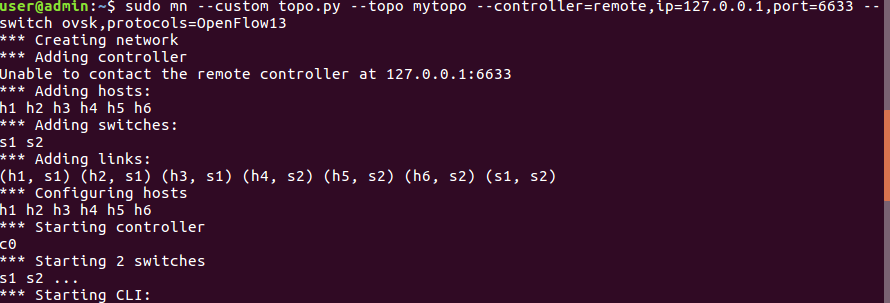
使用net查看拓扑
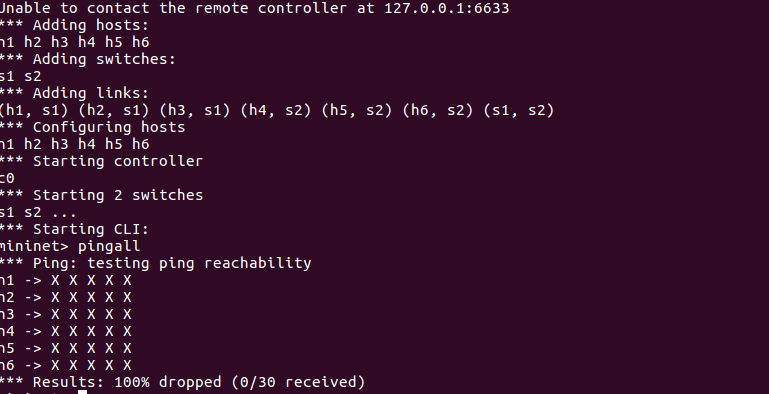
使用pingall命令测试连通性
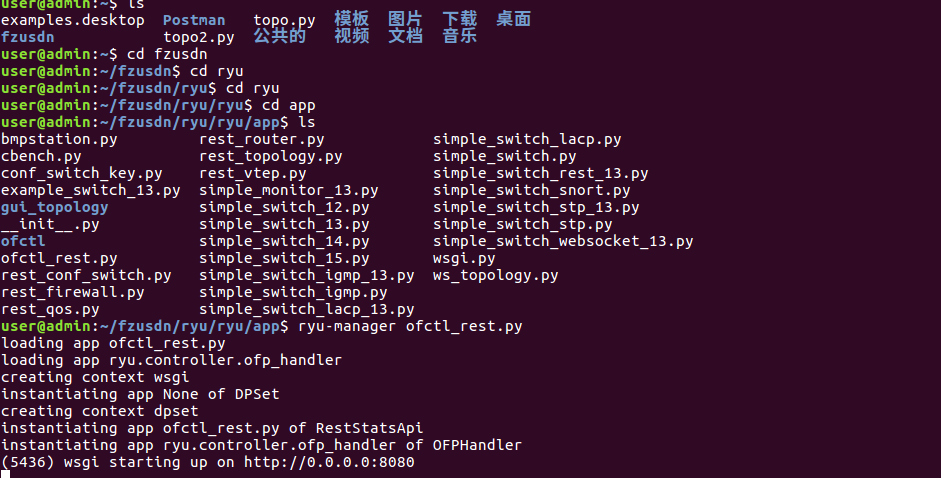
进入ryu文件夹的ryu文件夹下的app,通过以下的命令连接ryu控制器,结果如下图
ryu-manager ofctl_rest.py
2.使用Ryu的REST API下发流表实现和第2次实验同样的VLAN
按照实验二编写如下脚本,脚本为m.sh,内容如下:
#端口号1发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":1
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4096 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号2发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":2
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4097 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号3发来数据
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"in_port":3
},
"actions":[
{
"type": "PUSH_VLAN", # s1将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4098 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#向端口1转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "0"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 1
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口2转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "1"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 2
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口3转发
curl -X POST -d '{
"dpid": 1,
"priority":1,
"match":{
"dl_vlan": "2"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 3
}
]
}' http://localhost:8080/stats/flowentry/add
#端口号1发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":1
},
"actions":[
{
"type": "PUSH_VLAN", # s2将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4096 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号2发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":2
},
"actions":[
{
"type": "PUSH_VLAN", # s2将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4097 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#端口号3发来数据
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"in_port":3
},
"actions":[
{
"type": "PUSH_VLAN", # s2将从主机发来的数据包打上vlan_tag
"ethertype": 33024 # 帧类型0x8100(=33024): 表示IEEE 802.1Q的VLAN数据帧
},
{
"type": "SET_FIELD",
"field": "vlan_vid", # 设置VLAN ID
"value": 4098 # 设置vlan_id的值
},
{
"type": "OUTPUT",
"port": 4
}
]
}' http://127.0.0.1:8080/stats/flowentry/add
#向端口1转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "0"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 1
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口2转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "1"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 2
}
]
}' http://localhost:8080/stats/flowentry/add
#向端口3转发
curl -X POST -d '{
"dpid": 2,
"priority":1,
"match":{
"dl_vlan": "2"
},
"actions":[
{
"type": "POP_VLAN", # 给进入交换机的包去除 vlan_tag
},
{
"type": "OUTPUT",
"port": 3
}
]
}' http://localhost:8080/stats/flowentry/add
sudo chmod 777 m.sh
使用命令获取权限,然后运行sh文件,使用命令查看s1, s2流表
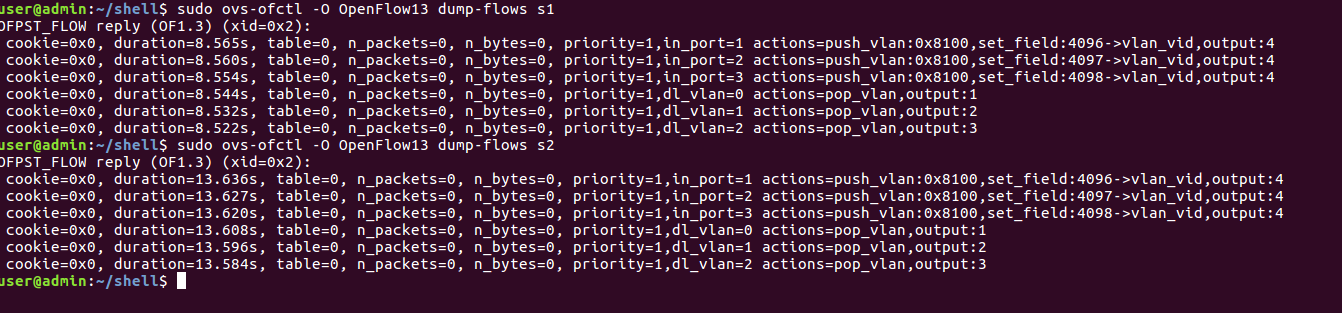
sudo ovs-ofctl -O OpenFlow13 dump-flows s1
sudo ovs-ofctl -O OpenFlow13 dump-flows s2
结果如下:
最后使用pingall命令查看连通性

3.对比两种方法,写出你的实验体会
实验二中使用的是ovs的命令,本次是用Ryu控制器来实现,个人感觉,相较第二次实验,本次实验通过编写shell脚本文件,运行后进行一次性下发无疑要快捷和方便,更容易理解和使用,出错了改起来也比较快。
实验中也遇到了一些问题,在连接RYU控制器的时候,出了些问题,导致RYU没有连接上,之后查看流表的时候出错了,只有重新连接,然后创建拓扑,查看流表,一定要认真仔细。


