用Firda Hook某app破解sign只需要静态分析
app用Charles抓包
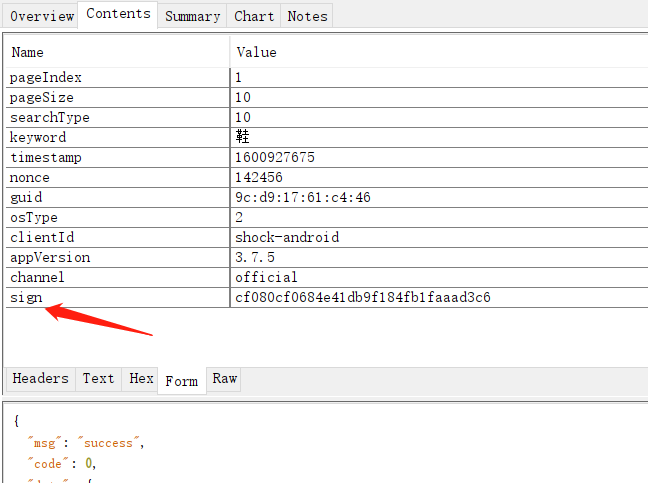
在搜索框中"sign"
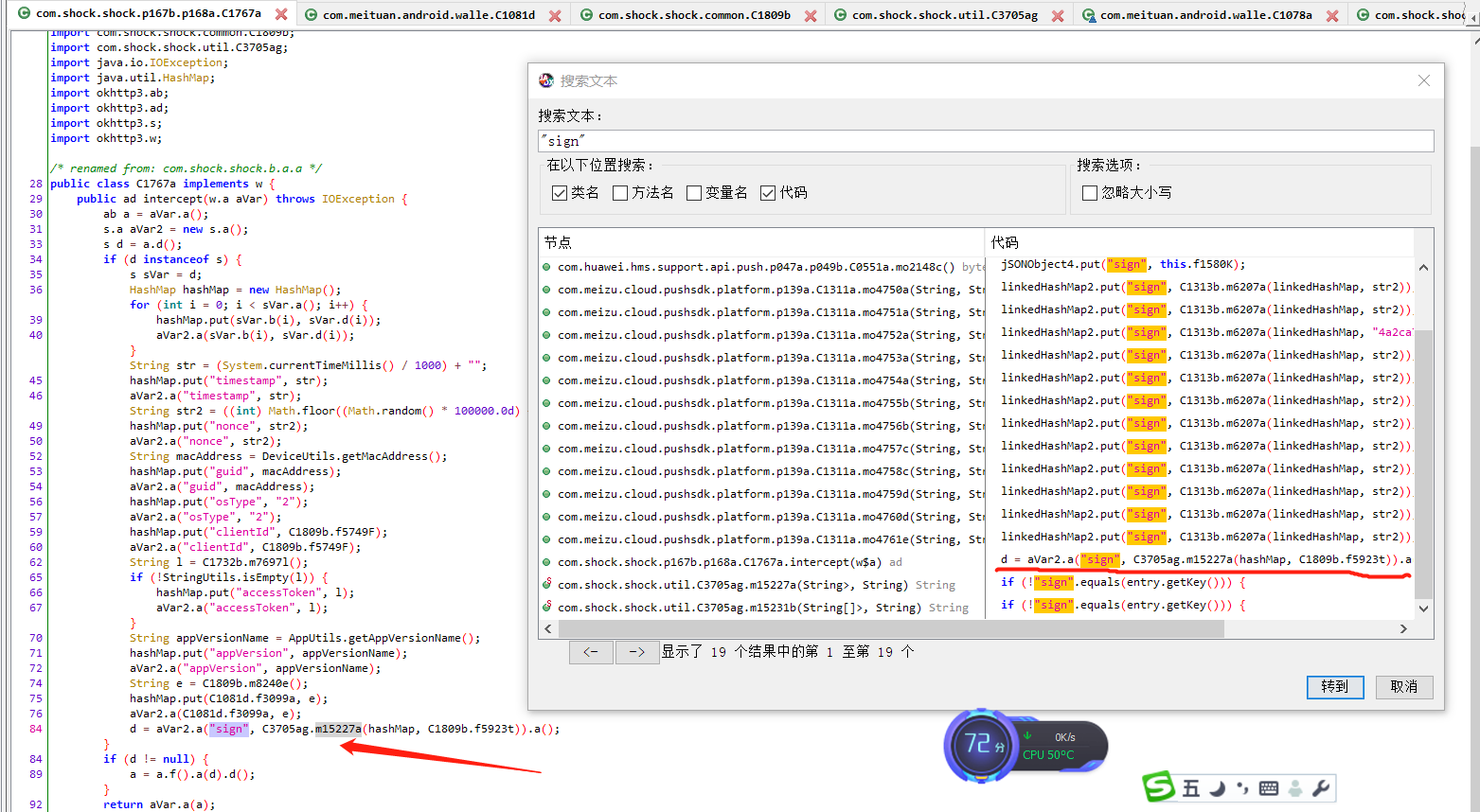
进入 m15227a 方法
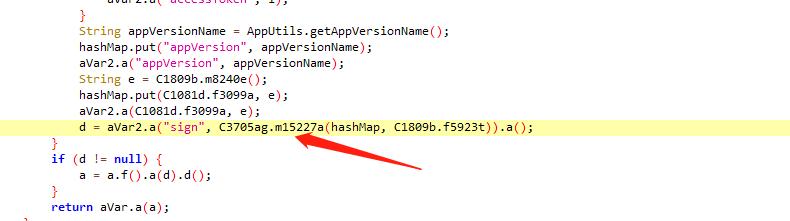
查看此方法 m15227a 传多少参数
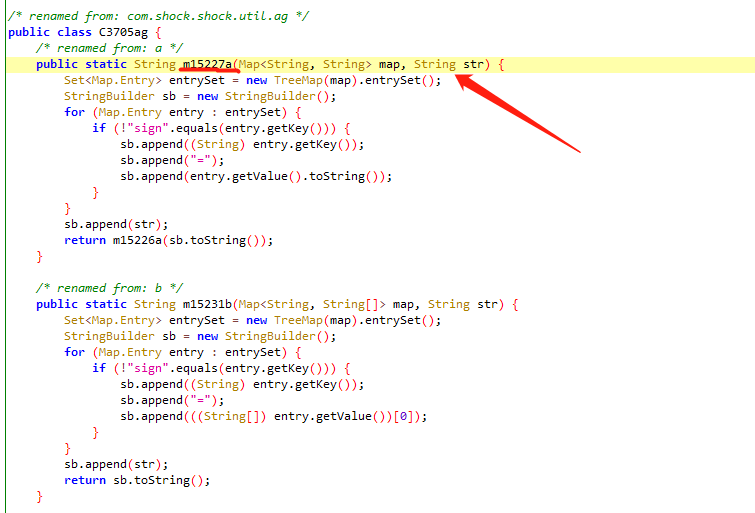
进入到m15227a
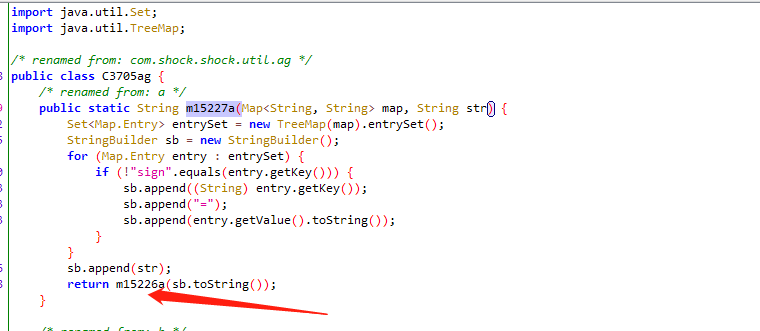
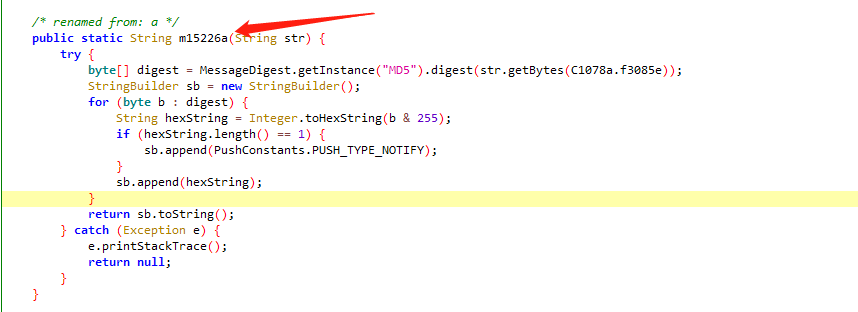
HOOK m15226a 此方法
public static String m15226a(String str)
sign 入参
EQ1OhXQsrbelQ6blcSU86KBURLZnowX1 此参数一步一步点击能找到
复制'appVersion=3.7.5channel=officialclientId=shock-androidguid=9c:d9:17:61:c4:46keyword=衣服snonce=142456sosType=2pageIndex=1spageSize=10searchType=10timestamp=1600927675EQ1OhXQsrbelQ6blcSU86KBURLZnowX1'
JS函数获取加密参数
复制Java.perform(function () {
var encrypt1 = Java.use("com.shock.shock.util.ag");
console.log(encrypt1);
encrypt1.a.overload("java.lang.String").implementation = function (args1) {
console.log("args1-1",args1);
var args = this.a(args1);
console.log("args-1", args1);
return args
}
});
HOOK 文件
复制# -*- coding: utf-8 -*-
import logging
import frida
import sys
logging.basicConfig(level=logging.DEBUG)
def on_message(message, data):
print(message)
with open('shock.js', 'r', encoding='utf-8') as f:
sta = ''.join(f.readlines())
rdev = frida.get_remote_device()
processes = rdev.enumerate_processes() # 安卓手机中的所有进程
print(processes)
# android.content.Intent android.content.Context android.view.ViewGroup java.lang.String, java.util.List [Ljava.lang.String;(String[]), javax.net.ssl.SSLSession SSLSession
session = rdev.attach("com.shock.shock")
print(session)
script = session.create_script(sta)
script.on("message", on_message)
script.load()
sys.stdin.read()
解密后爬取商品数据
复制url = "https://api.shockx.cn/search/search"
headers = {
# "User-Agent":random.choice(pc_user_agent_list),
"User-Agent": "Dalvik/2.1.0 (Linux; U; Android 6.0.1; Nexus 6 Build/MOB31S)",
"Content-Type": "application/x-www-form-urlencoded",
"Content-Length": "205",
"Host": "api.shockx.cn",
"Connection": "Keep-Alive",
"Accept-Encoding": "gzip",
}
data_num = 'appVersion=3.7.5channel=officialclientId=shock-androidguid=9c:d9:17:61:c4:46keyword=%snonce=1%sosType=2pageIndex=%spageSize=10searchType=10timestamp=%sEQ1OhXQsrbelQ6blcSU86KBURLZnowX1' % (
k_search, num_str, page, timestamp)
# print("data_num=", data_num)
signs = self.get_pwdmd5(data_num)
# print(signs)
data = {
"pageIndex": page,
"pageSize": "10",
"searchType": "10",
"keyword": k_search,
"timestamp": timestamp,
"nonce": "1" + str(num_str),
"guid": "9c:d9:17:61:c4:46",
"osType": "2",
"clientId": "shock-android",
"appVersion": "3.7.5",
"channel": "official",
"sign": signs,
}
# print("data参数=", data)
response = http_parse(url, method="post", data=data, headers=headers, verify=False, timeout=10)
result = json.loads(response.text)
如果您觉得阅读本文对您有帮助,请点一下“推荐”按钮,您的“推荐”将是我最大的写作动力!欢迎各位转载!
分类:
安卓逆向



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 从HTTP原因短语缺失研究HTTP/2和HTTP/3的设计差异
· 三行代码完成国际化适配,妙~啊~