8月26日 | 英语翻译 | 视频标题XSS,如何在NodeJs服务端将低危存储型XSS攻击变成高危RCE攻击
前言:可以帮助你看中文觉得没意思,看英文收获很大,吸引我兴趣的是哪一部分,我就可以专门去搜索关键词,并且查看。
目录选择:
翻译1:存储型XSS危害最大
Stored XSS attacks are probably the most common type of XSS attack. Stored XSS
attacks are interesting because they are the easiest type of XSS to detect, but often one
of the most dangerous because many times they can affect the most users.
Stored—XSS攻击是最常见的一种XSS攻击。存储型XSS攻击是非常有意思,因为这是检测最容易检测的XSS类型,
却是XSS种对所有用户最具有危害性的。
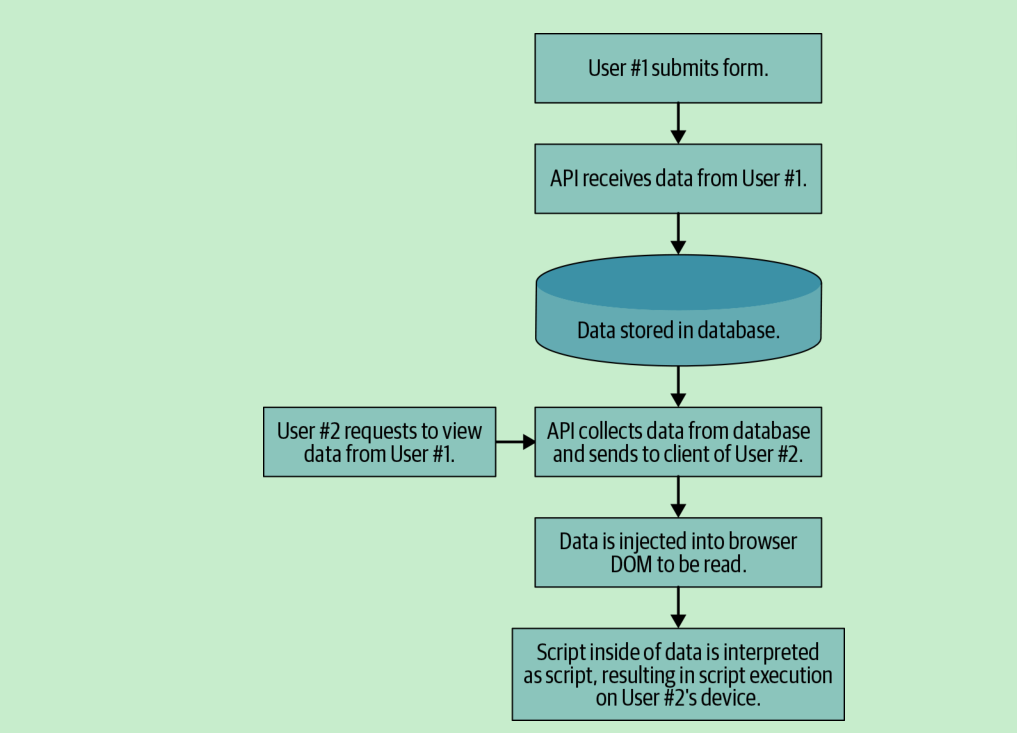
翻译2:与数据库的交互关系
Figure 10-1. Stored XSS—malicious script uploaded by a user that is stored in a data‐
base and then later requested and viewed by other users, resulting in script execution on
their machines
图10 - 1: 由用户上传存储在数据中的xss恶意脚本
然后当其他用户请求和查看时,会导致脚本在
他们的机器执行。
翻译3:XSS受攻击方法
A stored database object can be viewed by many users. In some cases all of your users
could be exposed to a stored XSS attack if a global object is infected.
If you operated or maintained a video-hosting site and “featured” a video on the front
page, a stored XSS in the title of this video could potentially affect every visitor for the
duration of the video. For these reasons, stored XSS attacks can be extremely deadly
to an organization.
如果一个存储的数据库对象可以被许多用户查看。在某些情况下,您的所有用户
如果一个全局对象被感染,则可能暴露于已存储的XSS攻击。
如果你经营或维护一个视频托管网站,并作为“xss代码”一个视频
页面中,这个视频标题中存储的XSS可能会潜在地影响每个访问者
在视频持续期。由于这些原因,存储的XSS攻击是极其致命的
一个组织。
翻译4:存储XSS变RCE方法
On the other hand, the permanent nature of a stored XSS makes detection quite easy.
Although the script itself executes on the client (browser), the script is stored in a
database, aka server side. The scripts are stored as text server side, and are not evaluated
(except perhaps in advanced cases involving Node.js servers, in which case they
become classified as remote code execution [RCE], which we will cover later).
另一方面,存储XSS的永久特性使得检测非常容易。
尽管脚本本身在客户机(浏览器)上执行,但脚本存储在
数据库,又称服务器端。脚本存储为文本服务器端,不进行执行。
除了可能在高阶的情况下涉及Node.js服务器,在这种情况下,它们
被归类为远程代码执行[RCE],我们将在后面介绍
翻译5:XSS检测方法
Because the scripts are stored server side, regularly scanning database entries for
signs of stored script could be a cheap and efficient mitigation plan for a site that
stores many types of data provided by an end user.This is, in fact, one of many
techniques that the most security-oriented software companies today use to mitigate the risk of XSS.
We will soon discover that it cannot be a final solution, however, as
advanced XSS payloads may not even be written in plain text (e.g., base64, binary,
etc.). They also could potentially be stored in multiple places and only be dangerous
when concatenated by a specific service for use in the client. These are some tricks
that experienced hackers use to bypass defense mechanisms implemented by
developers.
因为脚本存储在服务器端,定期扫描数据库条目
对于以下站点,存储脚本的迹象可能是一种廉价而有效的缓解计划为那些
为终端用户提供了存储多种数据类型的网站。
事实上,这只是其中之一
当今大多数面向安全的软件公司都使用这种技术来降低XSS的风险。
然而,我们很快就会发现,这并不是一个最终的解决方案
高级的XSS有效负载甚至可能不是用纯文本编写的(例如,base64,二进制编码,
等等)。它们也可能被存储在多个地方,只有当由特定服务连接在
客户端中使用时会触发攻击危险。这是一些有经验的黑客用来绕过开发人员的防御机制。
翻译6:最常使用的XSS方法
The example we used earlier when demonstrating a stored XSS attack injected a script
tag directly into the DOM and executed a malicious script via JavaScript. This is the
most common approach for XSS, but also one that is most often mitigated by smart
security engineers and security-conscientious developers.
我们在前面演示存储的XSS攻击时使用的示例注入了一个脚本
标记直接进入DOM,并通过JavaScript执行恶意脚本。这是
这是XSS最常见的方法,但也是最常被使用的一种XSS
安全研究员和有安全意识的开发人员。
翻译7:什么是CSP规则:
A simple regex to ban script tags or a CSP rule to prevent inline script execution
would have halted this attack in its tracks.
The only requirement for an XSS attack to be categorized as “stored” is that the
payload must be stored in the application’s database. There is no requirement for this
payload to be valid JavaScript, nor is there a requirement for the client to be a web
browser. As mentioned earlier, there are many alternatives to script tags that will still
result in compromised data or script execution.
禁止脚本标记的简单regex或防止内联脚本执行的CSP规则
就能阻止这次袭击。
将XSS攻击归类为“存储”的唯一要求是,payload必须存储在应用程序的数据库中。
这没有要求有效负载是有效的JavaScript,也没有要求客户端是一个web
浏览器。正如前面提到的,还有许多替代脚本标签的方法会导致数据或脚本执行受损。
翻译8:存储型XSS污染浏览器:
Furthermore , there are many clients that request data via a web server that can be contaminated by a stored XSS—web browsers are just the most common target.
此外,许多通过web服务器请求数据的客户端可能会被存储的XSS-web浏览器所污染,这是最常见的目标。
Google存储型XSS实战:
存储型XSS比如评论啊,这些地方,他会放在数据库里面,以等待页面刷新的时候展现出来。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号