容器中安装dns-bind
安装dns-bind
yum install bind bind-utils
如果是在k8s 中部署,需要设置特权模式,否则用systemctl 启动的时候会报错
Failed to get D-Bus connection: Operation not permitted
apiVersion: apps/v1
kind: StatefulSet
metadata:
labels:
run: dns-bind
name: dns-bind
namespace: default
spec:
podManagementPolicy: OrderedReady
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
run: dns-bind
serviceName: nsqd
template:
metadata:
creationTimestamp: null
labels:
run: dns-bind
spec:
containers:
- command:
- /usr/sbin/init # 这里必须是init ,这样systemctl 才有权限
image: harbor.qima-inc.com/paas/base:dns-bind
imagePullPolicy: Always
name: dns-bind
resources: {}
securityContext:
capabilities:
add:
- NET_ADMIN
- SYS_PTRACE
privileged: true # 对 /usr/sbin/init开启 特权
procMount: Default
terminationMessagePath: /dev/termination-log
配置
named.conf
安装完成之后在 /etc目录下存在一个named.conf 文件
vim /etc/named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { any; }; # 端口监听的地址默认是127.0.0.1,这里改成any,表示所有
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; }; # 允许进行dns 查找的范围,这里改成any
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones"; # 这里配置dns 区块配置
include "/etc/named.root.key";
named.rfc1912.zones
vim /etc/named.rfc1912.zones
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "httpbin.com" IN { # 新增一个httpbin.com 区块
type master; #master dns 节点
file "httpbin.com.zone"; # 配置 dns 记录的文件
allow-update { none; };
};
httpbin.com.zone
cd /var/named/
# 必须加-a 参数
cp -a named.localhost httpbin.com.zone
vim httpbin.com.zone
为什么必须加-a 参数,看下图
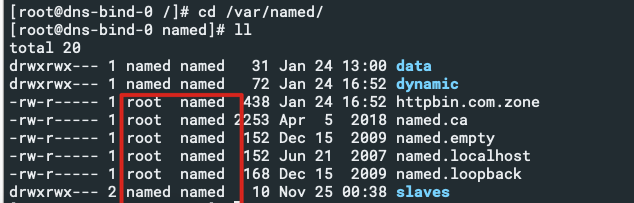
因为都是文件的属性是root 和named ,如果文件属性权限不对的话,dns 记录是无法使用的
$TTL 30s ;dns 缓存时长
@ IN SOA @ httpbin.com. ( ;必须要以 . 结尾
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 127.0.0.1
AAAA ::1
www IN A 10.2.1.28 ;会和httpbin.com 组合成www.httpbin.com
tls IN A 10.2.1.30
启动
systemctl start named
1. DNS域名解析中添加的各项解析记录
A记录: 将域名指向一个IPv4地址(例如:100.100.100.100),需要增加A记录
CNAME记录: 如果将域名指向一个域名,实现与被指向域名相同的访问效果,需要增加CNAME记录。这个域名一般是主机服务商提供的一个域名
MX记录: 建立电子邮箱服务,将指向邮件服务器地址,需要设置MX记录。建立邮箱时,一般会根据邮箱服务商提供的MX记录填写此记录
NS记录: 域名解析服务器记录,如果要将子域名指定某个域名服务器来解析,需要设置NS记录
TXT记录: 可任意填写,可为空。一般做一些验证记录时会使用此项,如:做SPF(反垃圾邮件)记录
AAAA记录: 将主机名(或域名)指向一个IPv6地址(例如:ff03:0:0:0:0:0:0:c1),需要添加AAAA记录
SRV记录: 添加服务记录服务器服务记录时会添加此项,SRV记录了哪台计算机提供了哪个服务。格式为:服务的名字.协议的类型(例如:_example-server._tcp)。
SOA记录: SOA叫做起始授权机构记录,NS用于标识多台域名解析服务器,SOA记录用于在众多NS记录中那一台是主服务器
PTR记录: PTR记录是A记录的逆向记录,又称做IP反查记录或指针记录,负责将IP反向解析为域名
显性URL转发记录: 将域名指向一个http(s)协议地址,访问域名时,自动跳转至目标地址。例如:将www.liuht.cn 显性转发到 www.itbilu.com 后,访问 www.liuht.cn 时,地址栏显示的地址为:www.itbilu.com。
隐性UR转发记录L: 将域名指向一个http(s)协议地址,访问域名时,自动跳转至目标地址,隐性转发会隐藏真实的目标地址。例如:将 www.liuht.cn 显性转发到 www.itbilu.com 后,访问 www.liuht.cn 时,地址栏显示的地址仍然是:www.liuht.cn 。


