Cassandra--启用用户认证和用户管理
========================================================
启用用户认证和创建超级用户
需要针对每个节点进行配置修改和重启,但授权操作仅需要在任一节点进行即可。
// 修改配置文件 cassandra.yaml 并重启
authenticator: PasswordAuthenticator
authorizer: CassandraAuthorizer
// 使用默认账号登录
python27 ./cqlsh.py -u 'cassandra' -p 'cassandra' 192.168.1.101
// 修改system_auth,避免单点故障
ALTER KEYSPACE system_auth WITH REPLICATION = { 'class' : 'SimpleStrategy', 'replication_factor' : 3 };
// 创建带有超级权限的用户
CREATE ROLE cassandra_dba WITH SUPERUSER = true AND LOGIN = true AND PASSWORD = 'cassandra_dba.com';
// 使用新账号登录
python27 ./cqlsh.py -u 'cassandra_dba' -p 'cassandra_dba.com' 192.168.1.101
// 禁用默认账号
ALTER ROLE cassandra WITH SUPERUSER = false AND LOGIN = false;
========================================================
设置超级用户
// 创建超级用户 CREATE USER test WITH PASSWORD '123456' SUPERUSER; // 创建普通用户 CREATE USER test1 WITH PASSWORD '123456' NOSUPERUSER; // 修改用户 ALTER USER test WITH PASSWORD '654321' ( NOSUPERUSER |SUPERUSER ); // 删除用户 DROP USER test; // 列出所有用户 LIST USERS;
========================================================
用户创建和授权
permission_name: ALL/ALTER/AUTHORIZE/CREATE/DROP/MODIFY/SELECT resource: ALL KEYSPACES/KEYSPACE keyspace_name/TABLE keyspace_name.table_name // 对用户授权 GRANT permission_name ON resource TO user_name; // 对用户取消权限 REVOKE permission_name ON resource FROM user_name; // 列出用户权限 LIST permission_name ON resource OF user_name;
demo:
// 如创建exps_rw用户,并授予对数据库exps的读写权限 CREATE USER exps_rw WITH PASSWORD '123.com' NOSUPERUSER; GRANT SELECT ON KEYSPACE exps TO exps_rw; GRANT MODIFY ON KEYSPACE exps TO exps_rw; // 查看exps_rw用户在数据库exps上的权限 LIST ALL ON KEYSPACE exps OF exps_rw;
========================================================
授权数据存储
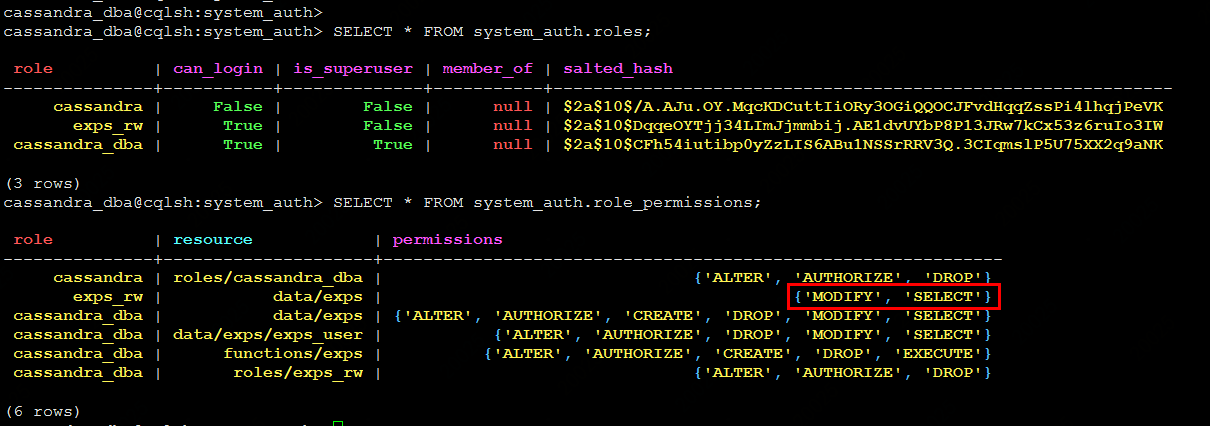
用户账号和用户权限存放在数据库system_auth中。
// 查看用户 SELECT * FROM system_auth.roles; // 查看用户权限 SELECT * FROM system_auth.role_permissions;
抄自:https://blog.csdn.net/a476585070/article/details/54962224


