[SUCTF2018]followme
[SUCTF2018]followme
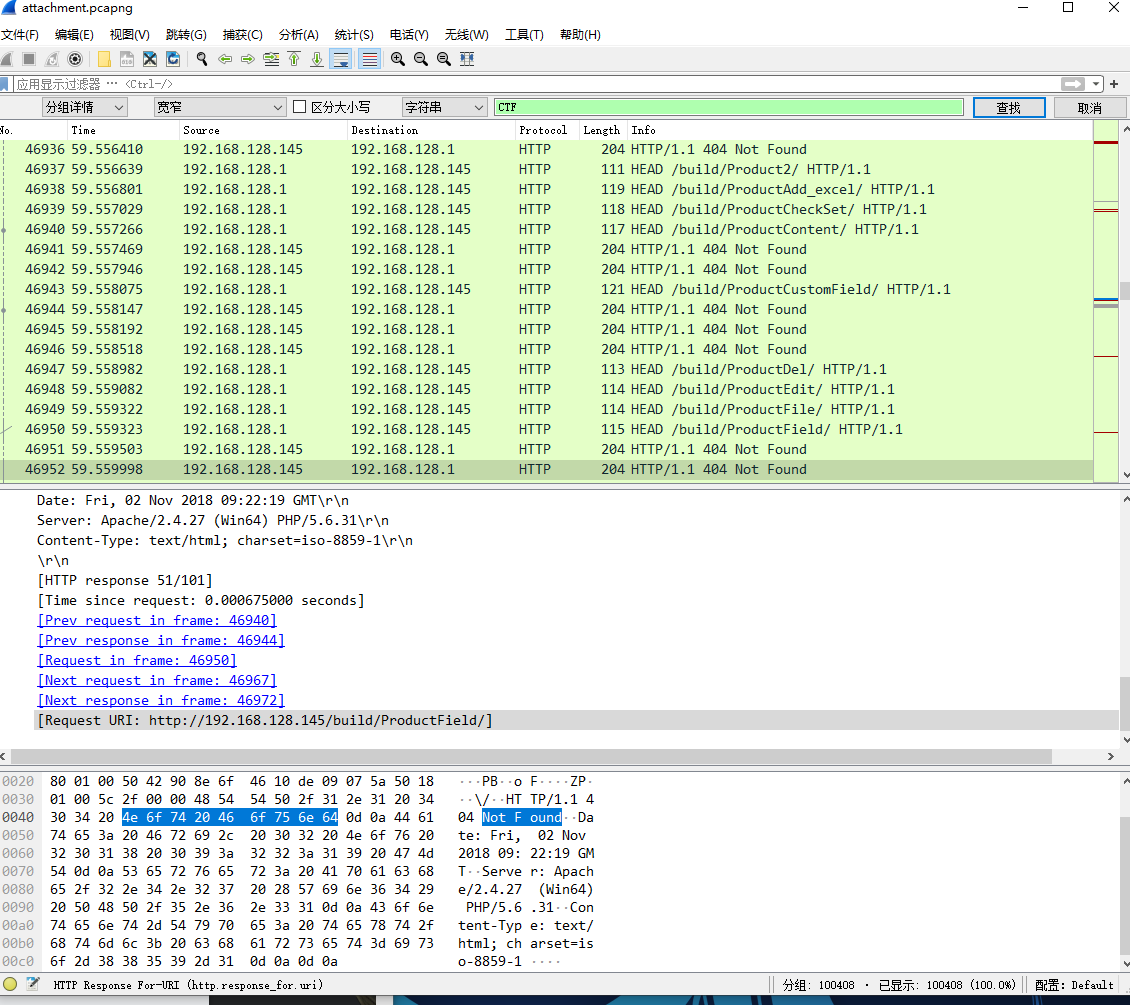
看起来像是在做渗透测试的时候抓的包,导出所有HTTP对象
大部分是类似这种的文件
login%3f_=6975b9a9f7a359d322e06c0e28db112b
login.php%3freferer=http%3A%2F%2F192.168.128.145%2Fbuild%2Fadmin%2F
<!DOCTYPE HTML>
<html class="no-js">
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="renderer" content="webkit">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>登录到Hello World - Hello World - Powered by Typecho</title>
<meta name="robots" content="noindex, nofollow">
<link rel="stylesheet" href="http://192.168.128.145/build/admin/css/normalize.css?v=17.10.30">
<link rel="stylesheet" href="http://192.168.128.145/build/admin/css/grid.css?v=17.10.30">
<link rel="stylesheet" href="http://192.168.128.145/build/admin/css/style.css?v=17.10.30">
<!--[if lt IE 9]>
<script src="http://192.168.128.145/build/admin/js/html5shiv.js?v=17.10.30"></script>
<script src="http://192.168.128.145/build/admin/js/respond.js?v=17.10.30"></script>
<![endif]--> </head>
<body class="body-100">
<!--[if lt IE 9]>
<div class="message error browsehappy" role="dialog">当前网页 <strong>不支持</strong> 你正在使用的浏览器. 为了正常的访问, 请 <a href="http://browsehappy.com/">升级你的浏览器</a>.</div>
<![endif]-->
<div class="typecho-login-wrap">
<div class="typecho-login">
<h1><a href="http://typecho.org" class="i-logo">Typecho</a></h1>
<form action="http://192.168.128.145/build/index.php/action/login?_=6975b9a9f7a359d322e06c0e28db112b" method="post" name="login" role="form">
<p>
<label for="name" class="sr-only">用户名</label>
<input type="text" id="name" name="name" value="" placeholder="用户名" class="text-l w-100" autofocus />
</p>
<p>
<label for="password" class="sr-only">密码</label>
<input type="password" id="password" name="password" class="text-l w-100" placeholder="密码" />
</p>
<p class="submit">
<button type="submit" class="btn btn-l w-100 primary">登录</button>
<input type="hidden" name="referer" value="http://192.168.128.145/build/admin/" />
</p>
<p>
<label for="remember"><input type="checkbox" name="remember" class="checkbox" value="1" id="remember" /> 下次自动登录</label>
</p>
</form>
<p class="more-link">
<a href="http://127.0.0.1/build/">返回首页</a>
</p>
</div>
</div>
<script src="http://192.168.128.145/build/admin/js/jquery.js?v=17.10.30"></script>
<script src="http://192.168.128.145/build/admin/js/jquery-ui.js?v=17.10.30"></script>
<script src="http://192.168.128.145/build/admin/js/typecho.js?v=17.10.30"></script>
<script>
(function () {
$(document).ready(function() {
// 处理消息机制
(function () {
var prefix = '1b8f6179b474098fd98deba635351fe4',
cookies = {
notice : $.cookie(prefix + '__typecho_notice'),
noticeType : $.cookie(prefix + '__typecho_notice_type'),
highlight : $.cookie(prefix + '__typecho_notice_highlight')
},
path = '/build/';
if (!!cookies.notice && 'success|notice|error'.indexOf(cookies.noticeType) >= 0) {
var head = $('.typecho-head-nav'),
p = $('<div class="message popup ' + cookies.noticeType + '">'
+ '<ul><li>' + $.parseJSON(cookies.notice).join('</li><li>')
+ '</li></ul></div>'), offset = 0;
if (head.length > 0) {
p.insertAfter(head);
offset = head.outerHeight();
} else {
p.prependTo(document.body);
}
function checkScroll () {
if ($(window).scrollTop() >= offset) {
p.css({
'position' : 'fixed',
'top' : 0
});
} else {
p.css({
'position' : 'absolute',
'top' : offset
});
}
}
$(window).scroll(function () {
checkScroll();
});
checkScroll();
p.slideDown(function () {
var t = $(this), color = '#C6D880';
if (t.hasClass('error')) {
color = '#FBC2C4';
} else if (t.hasClass('notice')) {
color = '#FFD324';
}
t.effect('highlight', {color : color})
.delay(5000).fadeOut(function () {
$(this).remove();
});
});
$.cookie(prefix + '__typecho_notice', null, {path : path});
$.cookie(prefix + '__typecho_notice_type', null, {path : path});
}
if (cookies.highlight) {
$('#' + cookies.highlight).effect('highlight', 1000);
$.cookie(prefix + '__typecho_notice_highlight', null, {path : path});
}
})();
// 导航菜单 tab 聚焦时展开下拉菜单
(function () {
$('#typecho-nav-list').find('.parent a').focus(function() {
$('#typecho-nav-list').find('.child').hide();
$(this).parents('.root').find('.child').show();
});
$('.operate').find('a').focus(function() {
$('#typecho-nav-list').find('.child').hide();
});
})();
if ($('.typecho-login').length == 0) {
$('a').each(function () {
var t = $(this), href = t.attr('href');
if ((href && href[0] == '#')
|| /^http\:\/\/192\.168\.128\.145\/build\/admin\/.*$/.exec(href)
|| /^http\:\/\/192\.168\.128\.145\/build\/index\.php\/action\/[_a-zA-Z0-9\/]+.*$/.exec(href)) {
return;
}
t.attr('target', '_blank');
});
}
});
})();
</script>
<script>
$(document).ready(function () {
$('#name').focus();
});
</script>
</body>
</html>
大部分文件内容显示是在爆破admin密码,尝试整个文件夹找一下相关关键字,例如CTF、flag之类的
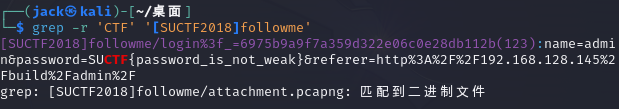
flag{password_is_not_weak}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号