文件上传闯关1-3关
PS:环境基于upload-labs(21关版本)
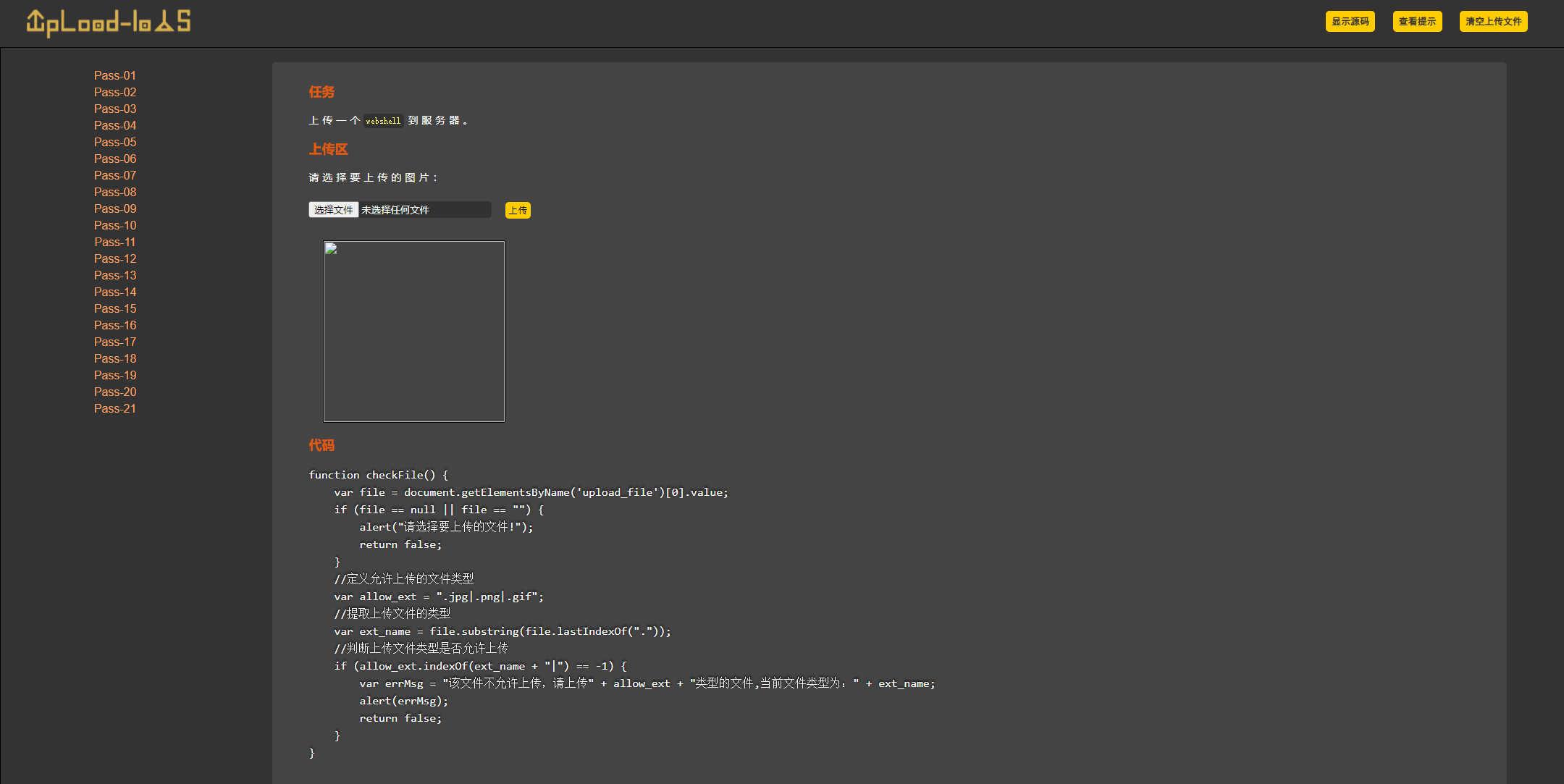
1、PASS-01:
学习目的,了解文件上传前端验证原理。
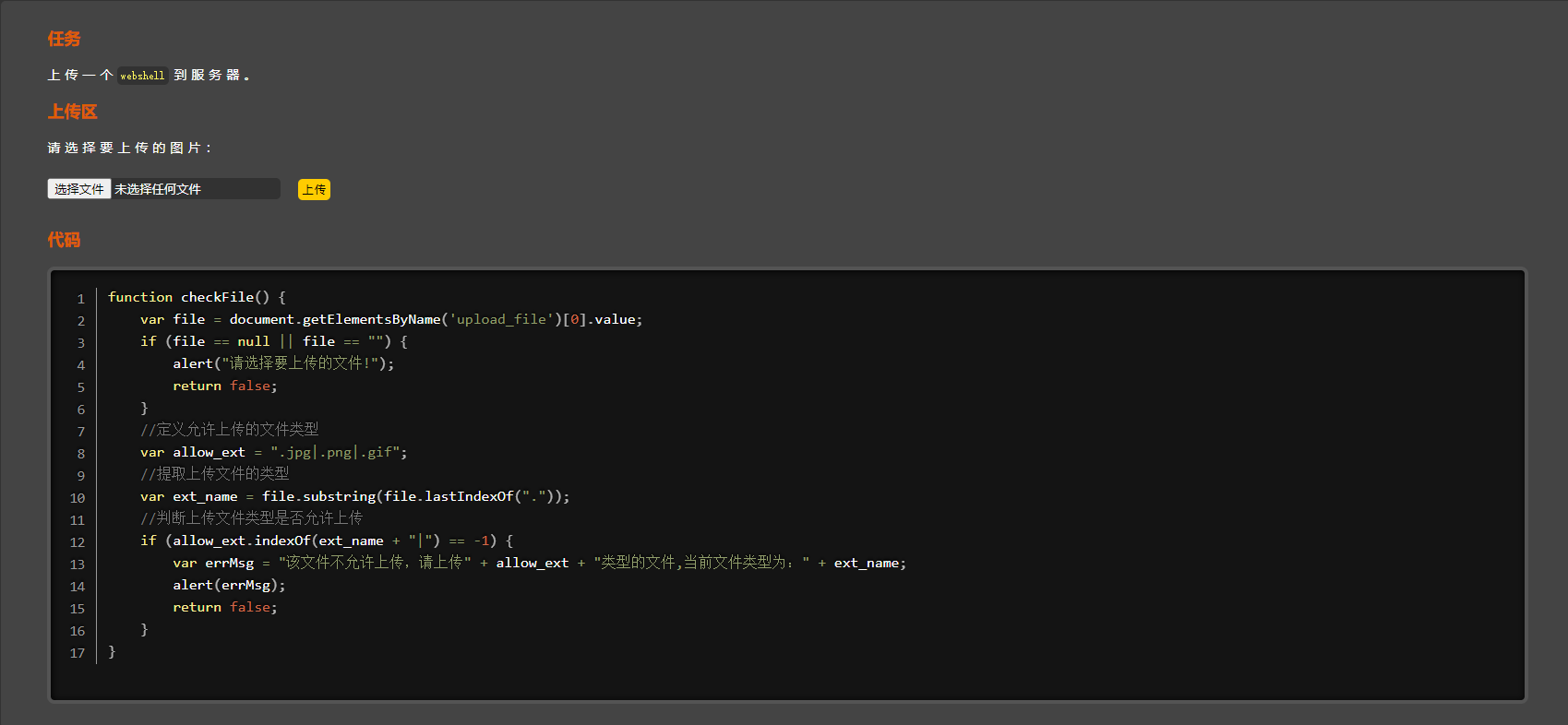
解题思路:从上述代码看出,上传文件验证在客户端完成,符合规则后再上传至服务器。
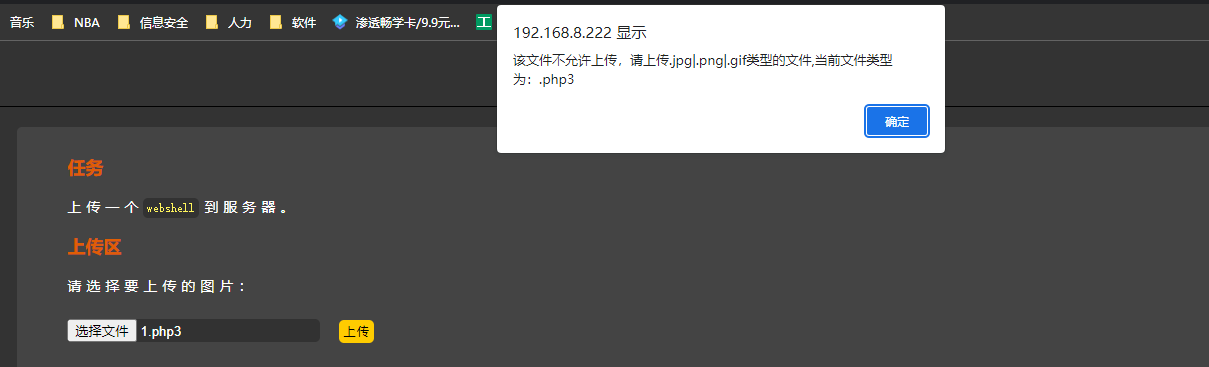
解题思路:前端验证一般通过JavaScript语言实现,
思路一:在浏览器上禁用javascript
google:
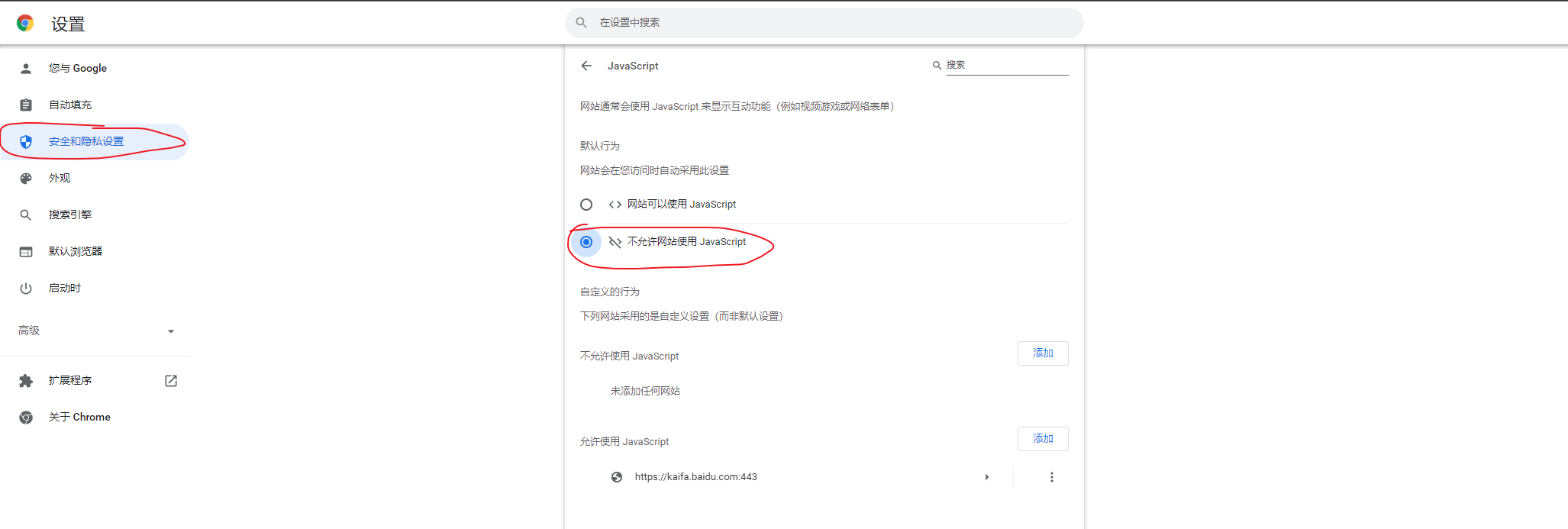
可禁用全部(一棍打死)或者设置黑白名单实现浏览器禁用javascript
再尝试上传后门脚本,此时即可成功。
思路二:将html文件下载到本地,删除javascript段代码后,通过action属性重定向到服务器。
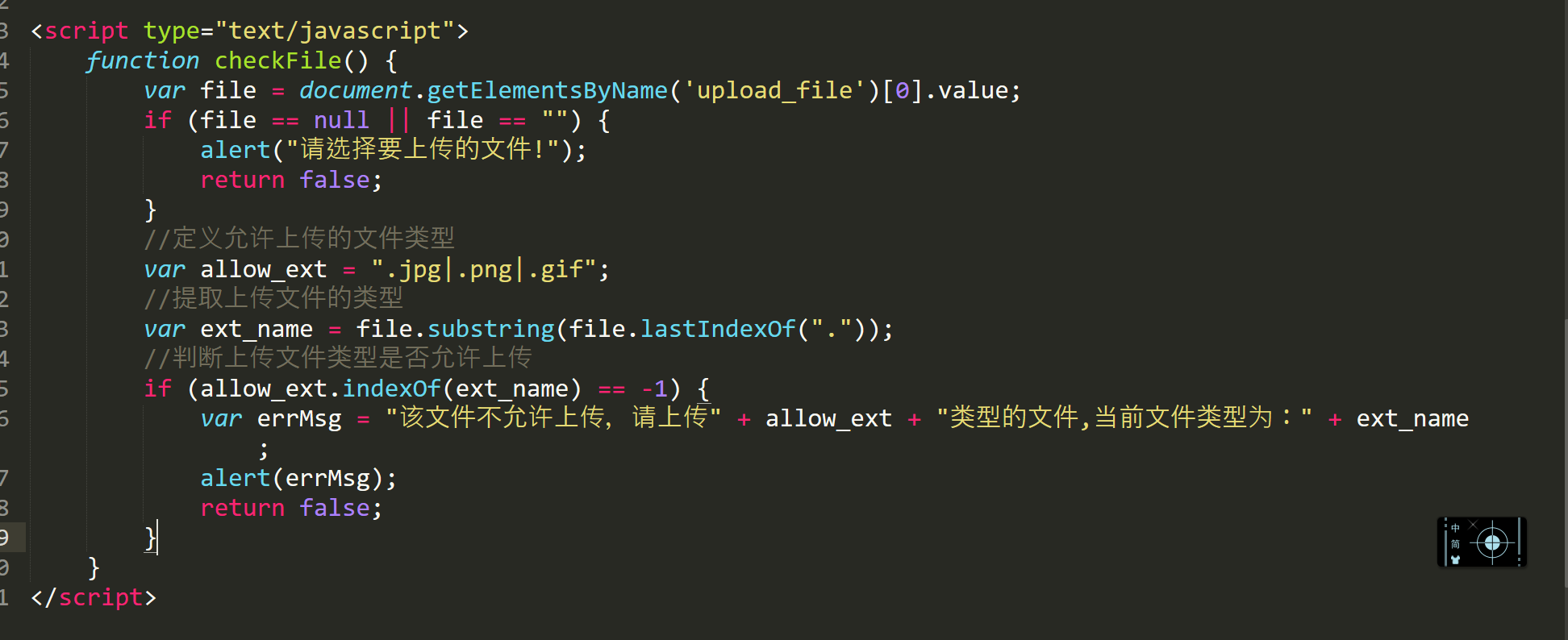
删除图中位置代码,并添加action属性
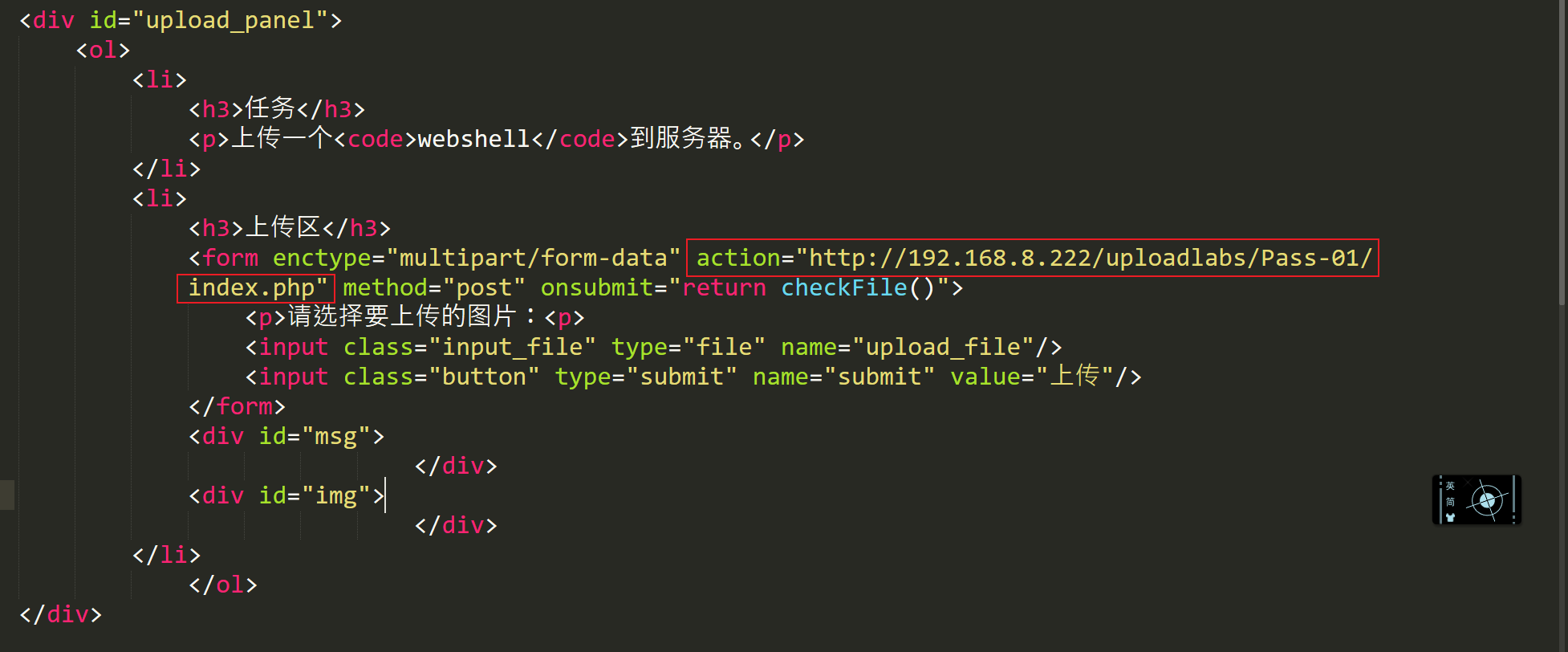
源代码为:
<html>
<head>
<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/>
<link rel="icon" type="image/x-icon" href="/uploadlabs/img/favicon.png" />
<title>upload-labs</title>
</head>
<link rel="stylesheet" type="text/css" href="/uploadlabs/css/index.css">
<link rel="stylesheet" type="text/css" href="/uploadlabs/css/prism.css">
<body>
<div id="head">
<a href="/uploadlabs/"><img src="/uploadlabs/img/logo.png"/></a>
<div id="head_menu">
<a id="handle_code" href="javascript:show_code()">显示源码</a>
<a href="javascript:get_prompt()">查看提示</a>
<a href="javascript:clean_upload_file()">清空上传文件</a>
</div>
</div>
<div id="main"><div id="menu">
<ul id="menulist">
<li><a id="Pass-01" href="/uploadlabs/Pass-01/index.php">Pass-01</a></li>
<li><a id="Pass-02" href="/uploadlabs/Pass-02/index.php">Pass-02</a></li>
<li><a id="Pass-03" href="/uploadlabs/Pass-03/index.php">Pass-03</a></li>
<li><a id="Pass-04" href="/uploadlabs/Pass-04/index.php">Pass-04</a></li>
<li><a id="Pass-05" href="/uploadlabs/Pass-05/index.php">Pass-05</a></li>
<li><a id="Pass-06" href="/uploadlabs/Pass-06/index.php">Pass-06</a></li>
<li><a id="Pass-07" href="/uploadlabs/Pass-07/index.php">Pass-07</a></li>
<li><a id="Pass-08" href="/uploadlabs/Pass-08/index.php">Pass-08</a></li>
<li><a id="Pass-09" href="/uploadlabs/Pass-09/index.php">Pass-09</a></li>
<li><a id="Pass-10" href="/uploadlabs/Pass-10/index.php">Pass-10</a></li>
<li><a id="Pass-11" href="/uploadlabs/Pass-11/index.php">Pass-11</a></li>
<li><a id="Pass-12" href="/uploadlabs/Pass-12/index.php">Pass-12</a></li>
<li><a id="Pass-13" href="/uploadlabs/Pass-13/index.php">Pass-13</a></li>
<li><a id="Pass-14" href="/uploadlabs/Pass-14/index.php">Pass-14</a></li>
<li><a id="Pass-15" href="/uploadlabs/Pass-15/index.php">Pass-15</a></li>
<li><a id="Pass-16" href="/uploadlabs/Pass-16/index.php">Pass-16</a></li>
<li><a id="Pass-17" href="/uploadlabs/Pass-17/index.php">Pass-17</a></li>
<li><a id="Pass-18" href="/uploadlabs/Pass-18/index.php">Pass-18</a></li>
<li><a id="Pass-19" href="/uploadlabs/Pass-19/index.php">Pass-19</a></li>
<li><a id="Pass-20" href="/uploadlabs/Pass-20/index.php">Pass-20</a></li>
<li><a id="Pass-21" href="/uploadlabs/Pass-21/index.php">Pass-21</a></li>
</ul>
</div>
<div id="upload_panel">
<ol>
<li>
<h3>任务</h3>
<p>上传一个<code>webshell</code>到服务器。</p>
</li>
<li>
<h3>上传区</h3>
<form enctype="multipart/form-data" action="http://192.168.8.222/uploadlabs/Pass-01/index.php" method="post" onsubmit="return checkFile()">
<p>请选择要上传的图片:<p>
<input class="input_file" type="file" name="upload_file"/>
<input class="button" type="submit" name="submit" value="上传"/>
</form>
<div id="msg">
</div>
<div id="img">
</div>
</li>
</ol>
</div>
</div>
<div id="footer">
<center>Copyright @ <span id="copyright_time"></span> by <a href="http://gv7.me" target="_bank">c0ny1</a></center>
</div>
<div class="mask"></div>
<div class="dialog">
<div class="dialog-title">提 示<a href="javascript:void(0)" class="close" title="关闭">关闭</a></div>
<div class="dialog-content"></div>
</div>
</body>
<script type="text/javascript" src="/uploadlabs/js/jquery.min.js"></script>
<script type="text/javascript" src="/uploadlabs/js/prism.js"></script>
<script type="text/javascript" src="/uploadlabs/js/prism-line-numbers.min.js"></script>
<script type="text/javascript" src="/uploadlabs/js/prism-php.min.js"></script>
<script type="text/javascript" src="/uploadlabs/js/index.js"></script>
</html>
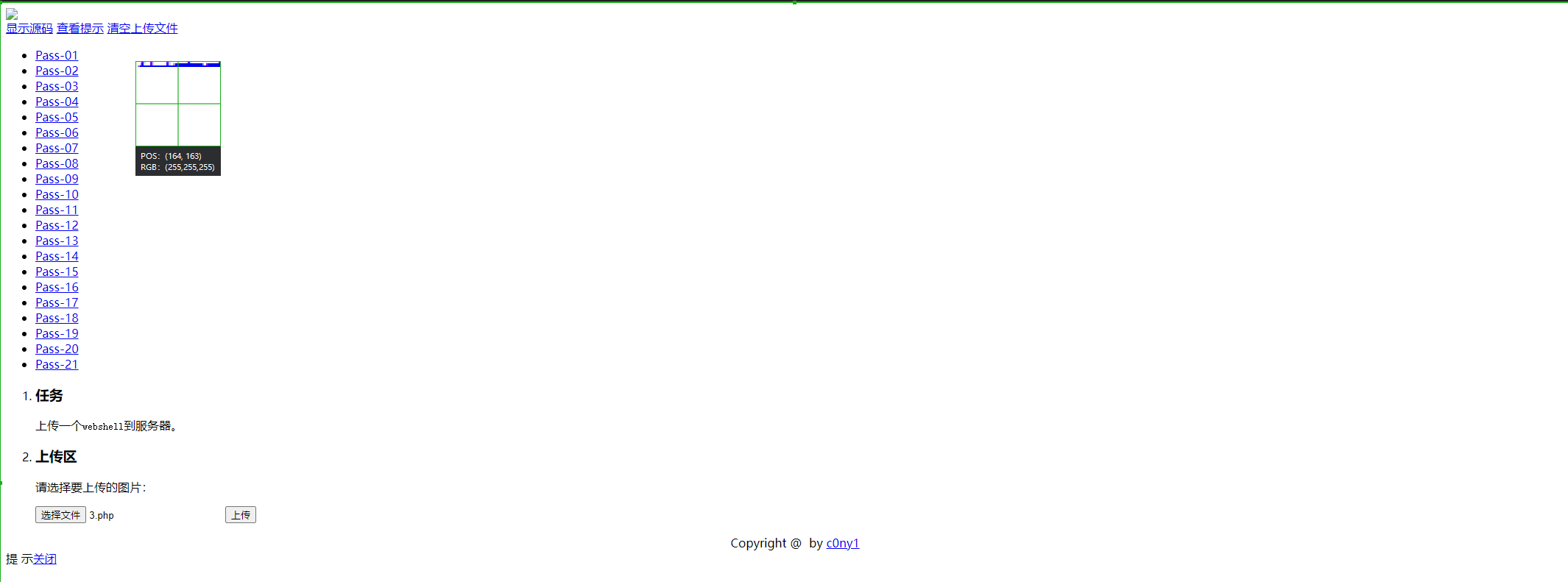
点击上传后
成功。
2.PASS-2
了解文件上传白名单后端MIME文件类型验证。
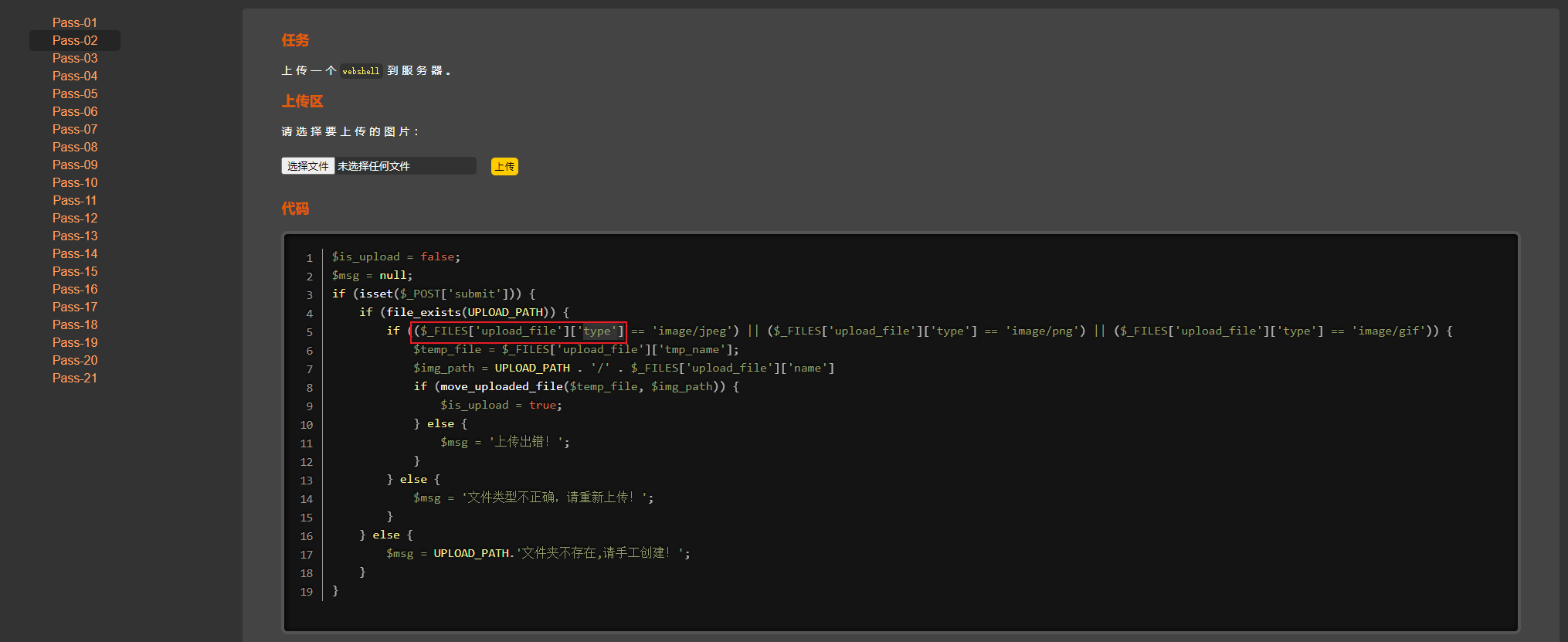
从上述源代码中可看出,本关是通过文件上传白名单验证实现,调用文件类型去匹配。通过抓包可以了解
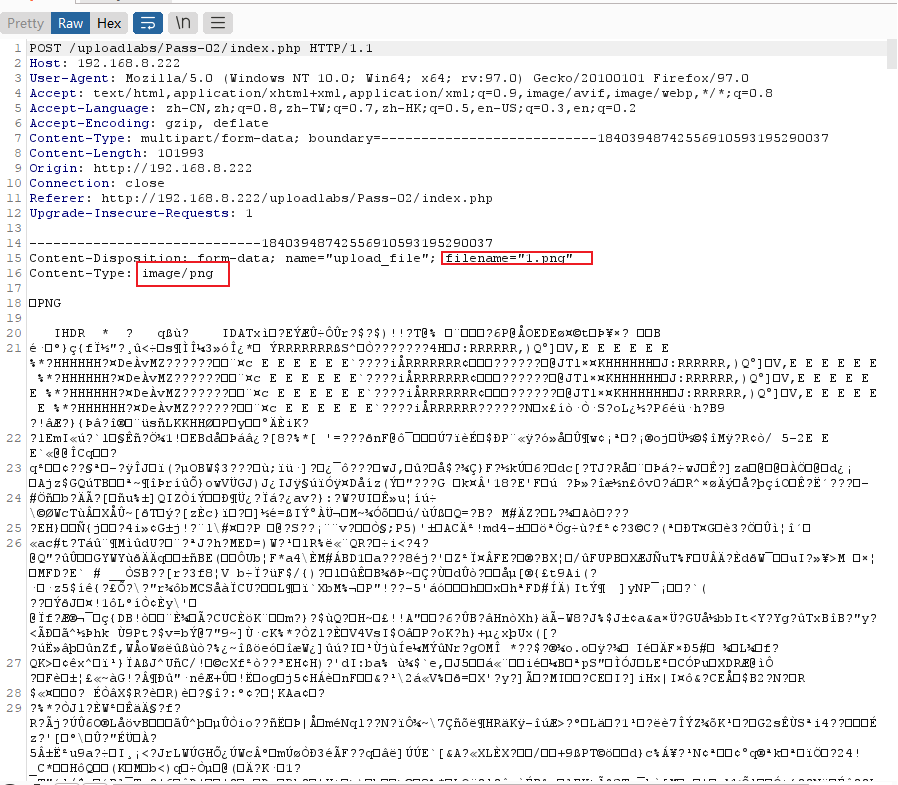
上传图片类型为image/png
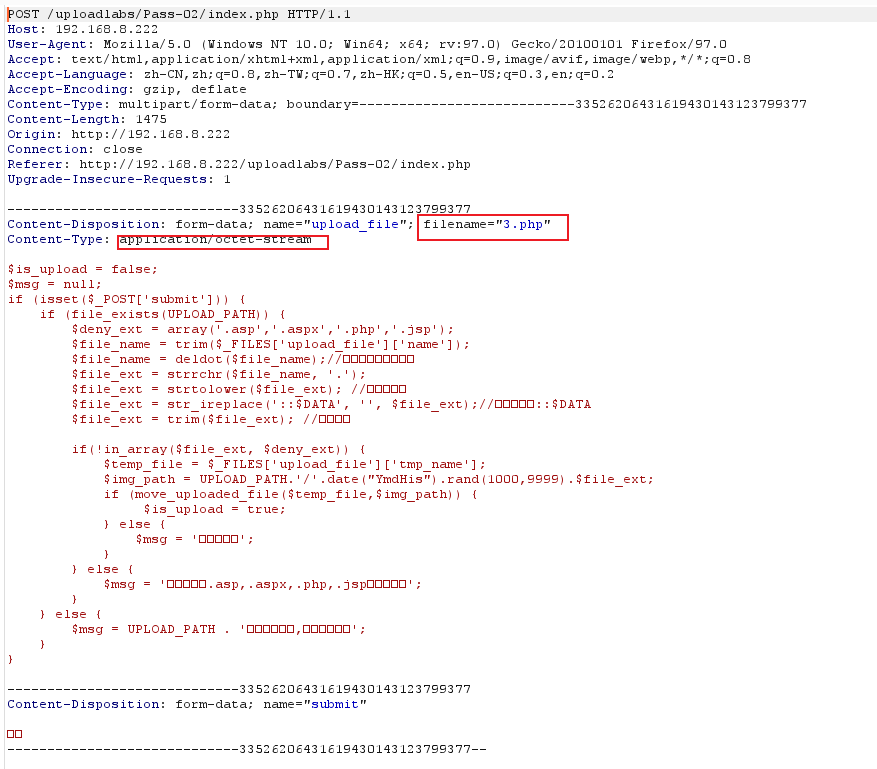
上传PHP文件类型为application/octet-scream
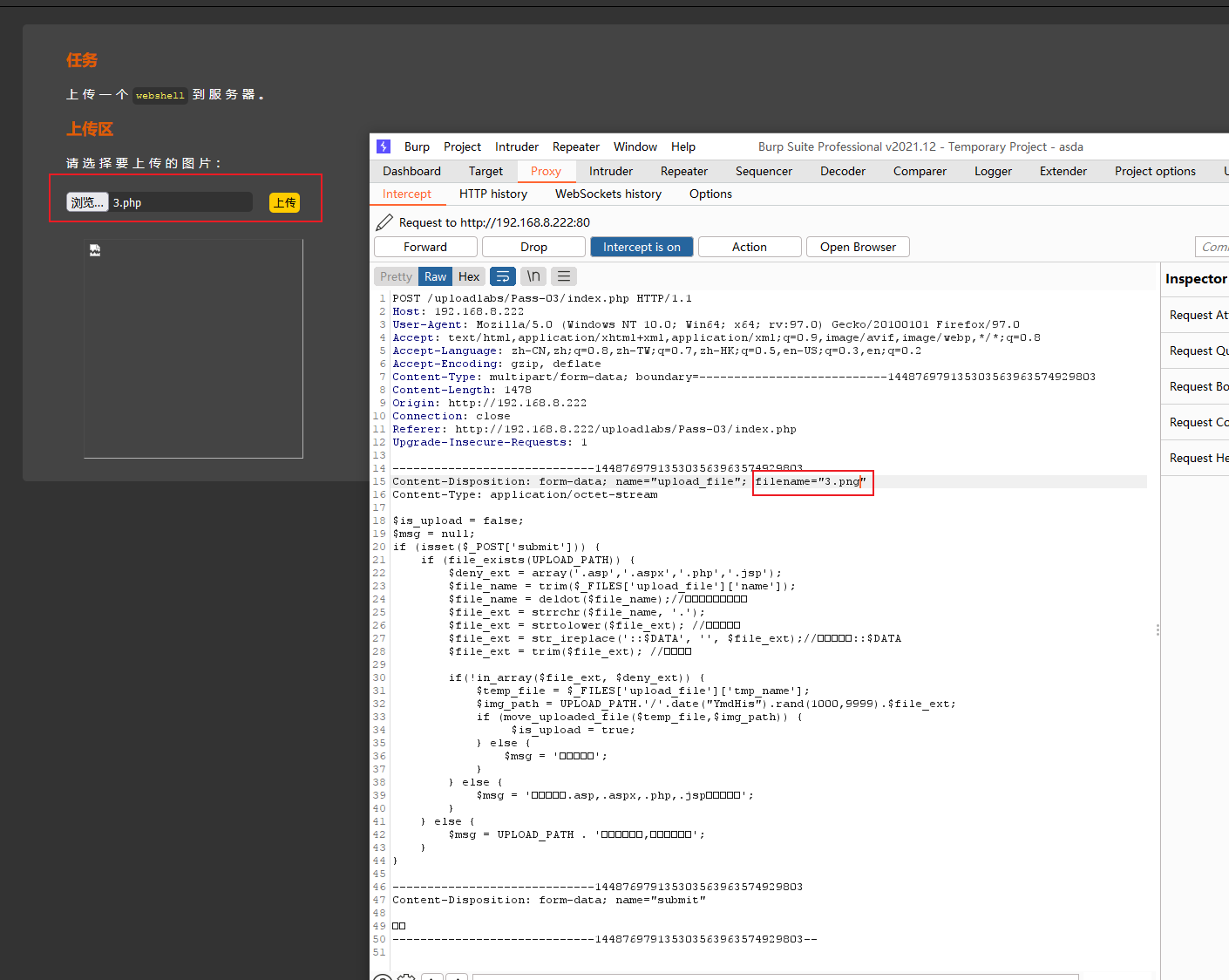
解题思路:通过burpsuite代理修改文件类型实现绕过。
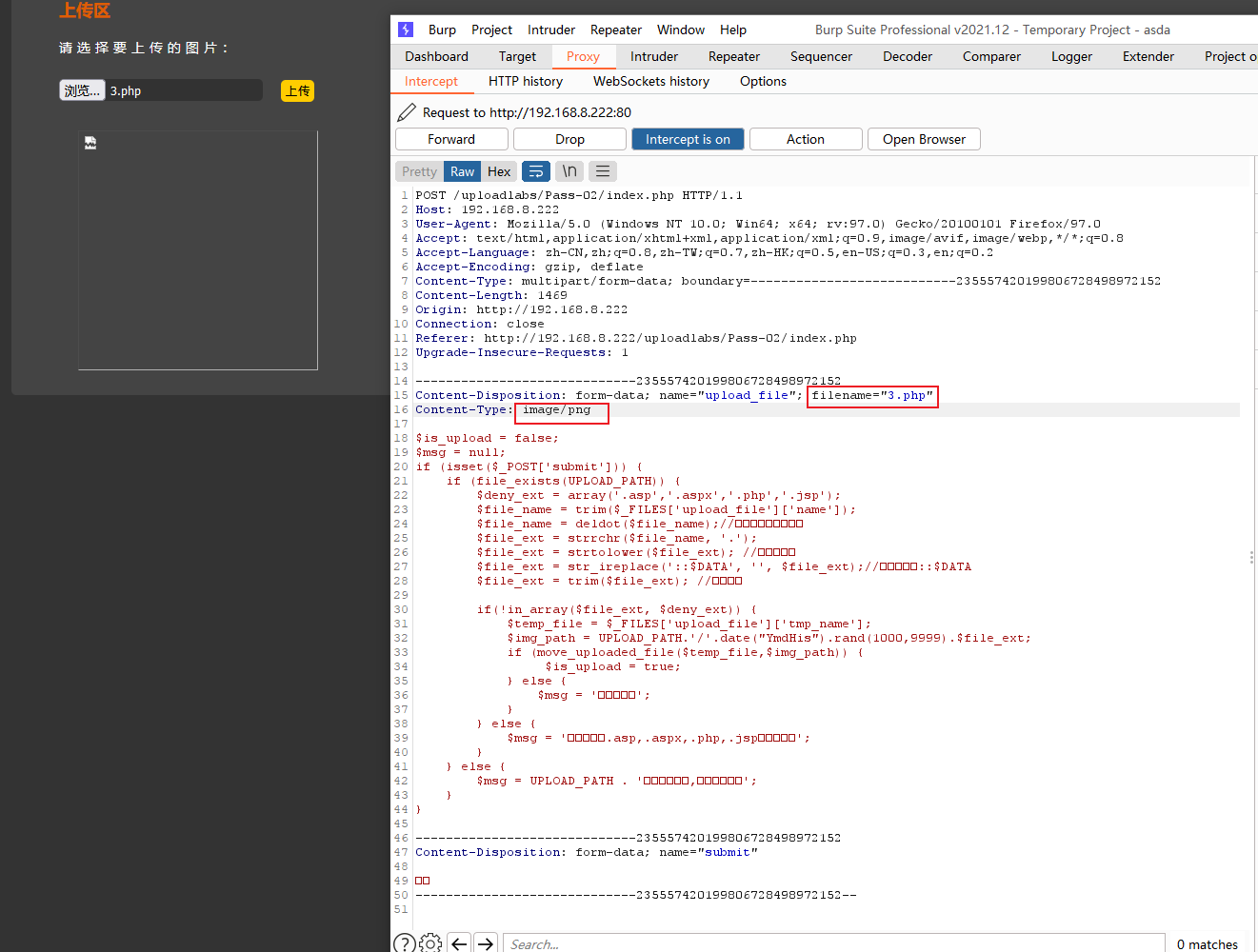
3.PASS-3
思路一:学习文件上传黑名单文件名验证方式。
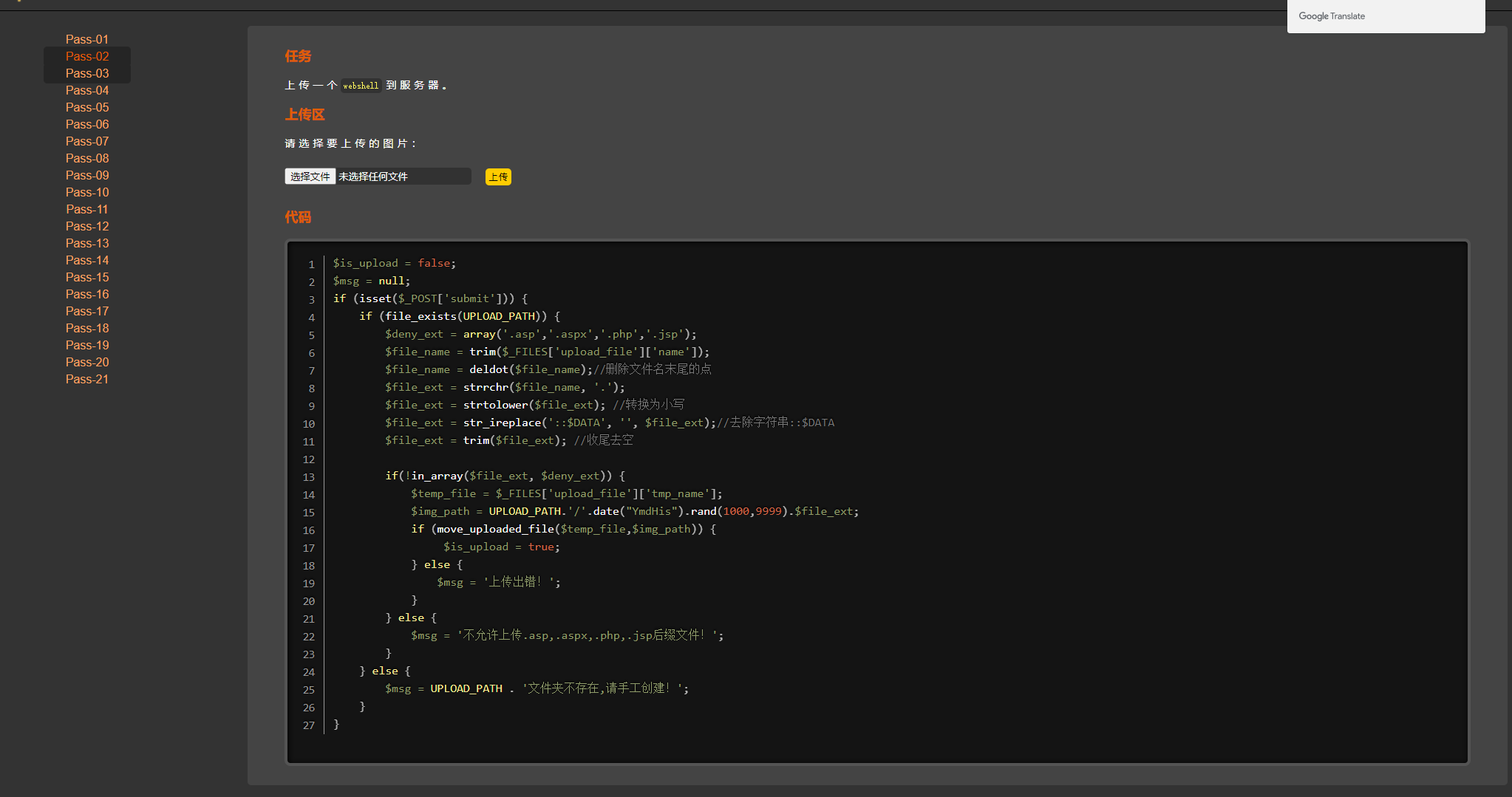
通过代码可以知道,本关是通过验证黑名单文件名实现,解题思路,通过burpsuite代理将后门文件名修改实现绕过。
思路二:源代码中只是限制php、jsp等文件上传,可通过替换文件后缀来实现绕过。php语言能执行php3和phphtml后缀格式文件,可通过php3和phphtml绕过。


