Textpattern CMS 4.8.8 Arbitrary File Upload Vulnerability
1、Access project address
2、Download project files for local setup

3、Accessing the backend address for login

4、Find the file upload location
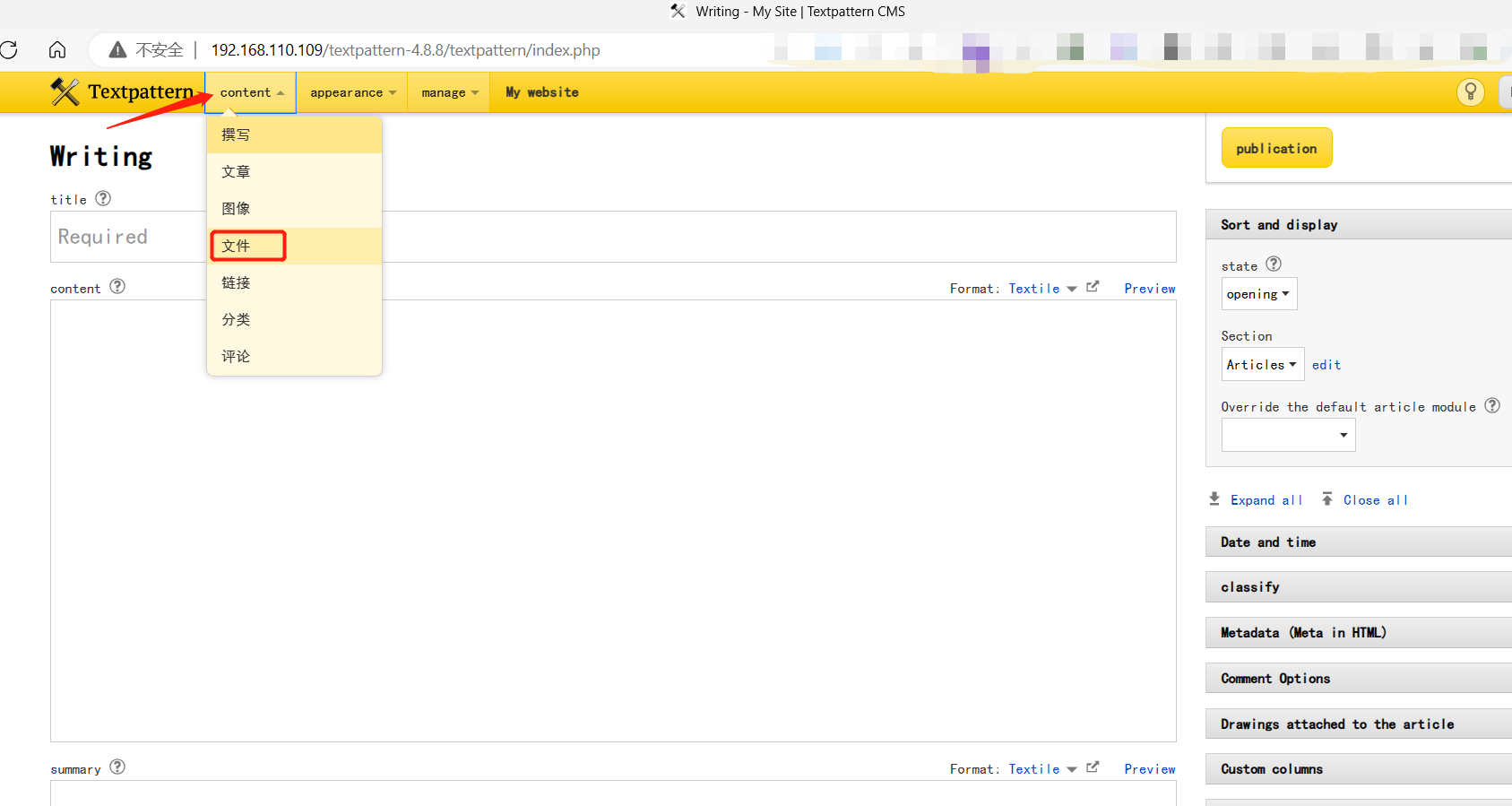
5、Upload malicious scripts
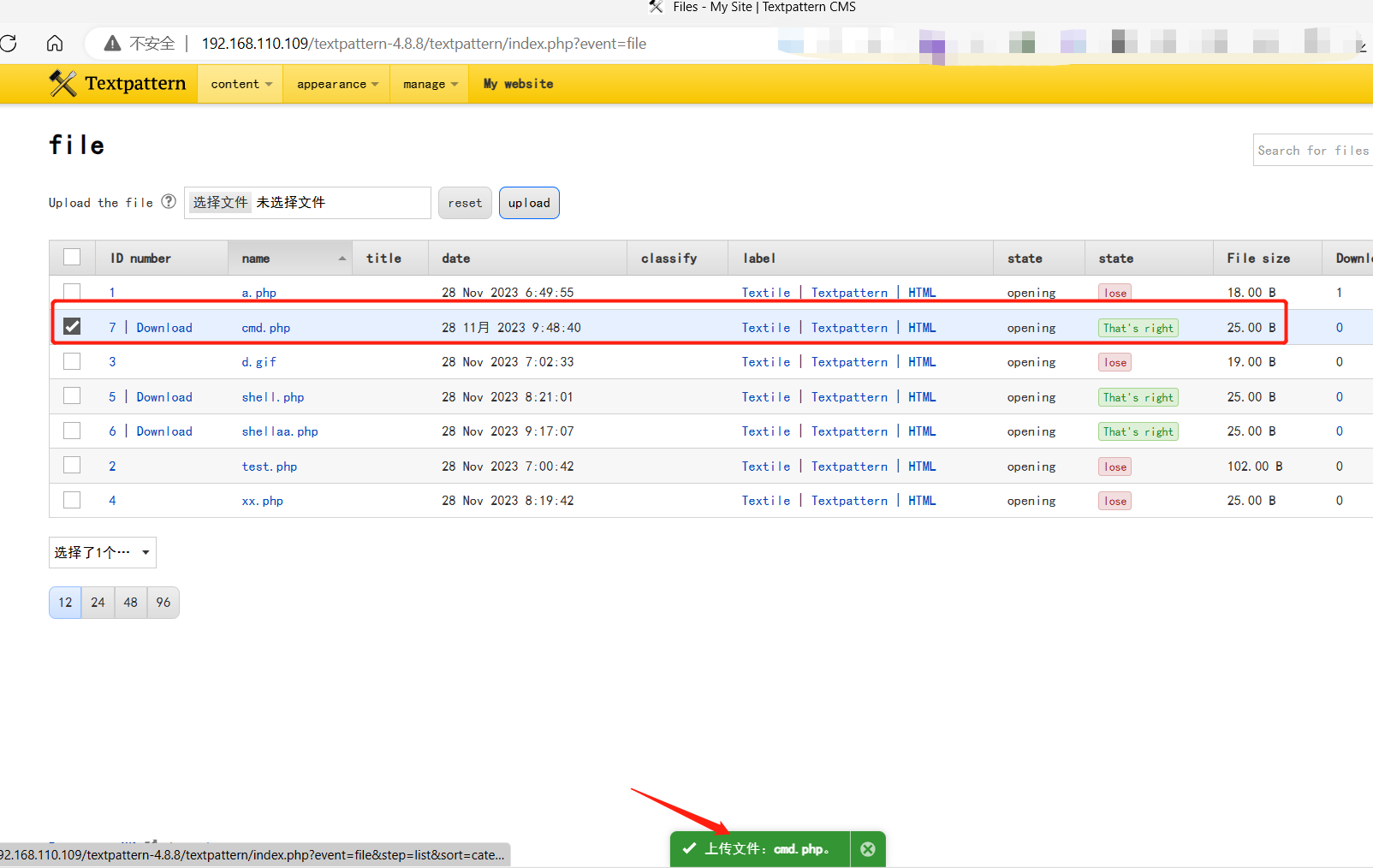
6、After uploading the file, save it to the fields directory, which can be accessed through the web




