k8s部署dashboard
k8s的web UI网页管理工具kubernetes-dashboard可提供部署应用,资源对象管理,容器日志查询,系统监控等常用的集群管理功能,如果想在页面上显示系统资源的使用情况,要求部署Metrics-server(这里没有部署)
第一步:
可以通过kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-rc5/aio/deploy/recommended.yaml进行部署
[root@master ~]# kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-rc5/aio/deploy/recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created
第二步:查看状态,确保两个pod状态为running
[root@master ~]# kubectl get pods -n kubernetes-dashboard NAME READY STATUS RESTARTS AGE dashboard-metrics-scraper-7b8b58dc8b-fjr5d 1/1 Running 0 105s kubernetes-dashboard-866f987876-zc5n2 1/1 Running 0 106s
第三步,查看svc,并修改svc访问模式(由clusterIP改为NodePort)
[root@master ~]# kubectl get svc -n kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.103.99.231 <none> 8000/TCP 3m8s kubernetes-dashboard ClusterIP 10.103.9.92 <none> 443/TCP 3m9s
修改(也可以用kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard):
[root@master ~]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kubernetes-dashboard service/kubernetes-dashboard patched [root@master ~]# kubectl get svc -n kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.103.99.231 <none> 8000/TCP 4m20s kubernetes-dashboard NodePort 10.103.9.92 <none> 443:32612/TCP 4m21s
第四步:浏览器访问,注意是https,端口号不要写错

第五步: 用token令牌来进行登录,下面token部分请复制
[root@master ~]# kubectl get secret -n kubernetes-dashboard NAME TYPE DATA AGE default-token-xp4hm kubernetes.io/service-account-token 3 7m59s kubernetes-dashboard-certs Opaque 0 7m59s kubernetes-dashboard-csrf Opaque 1 7m59s kubernetes-dashboard-key-holder Opaque 2 7m59s kubernetes-dashboard-token-msk6b kubernetes.io/service-account-token 3 7m59s [root@master ~]# kubectl describe secret kubernetes-dashboard-token-msk6b -n kubernetes-dashboard Name: kubernetes-dashboard-token-msk6b Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: kubernetes-dashboard kubernetes.io/service-account.uid: b37b4c53-eea7-4c4f-ac12-d42b18266dbb Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 20 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6InB1OTk0N09pSGpIdWtRSHh3QVFpWkxRZGRCbDJULWVLQnhUZFVHVUcxRlkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1tc2s2YiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImIzN2I0YzUzLWVlYTctNGM0Zi1hYzEyLWQ0MmIxODI2NmRiYiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.SV96hMZehQlQPc21bRQ61l_aTTZvQ5Ha4i5sgSifLhjwnRdWFQR5fqQfIGdPPLoTelL_iCasyARk8YIMxNw4F4akCGDqIFx1v6AM-s3JFd3sSWQAcBmUj1qcrkx1GNXEfmVQWk4buD_OlREoecTDrsoCwvAqR7414cE286PVuCpT6MWNySyYb5zMnmmmeHQIBj0mLhNqtYYs3sa-03HUAcv-w_UTUPO2oIZ_IdqTnFAWqTFb_BtENxNUsSwEG3p_KXoCFQYeB15H1lKrovqWZdJdAy3frIt2_O0HK1btcSdsvoyQqcQyrNXojr2c7gcDcHo3ZgCrhfkT_7mF9RVogg
第六步,复制到token令牌出,点击登录
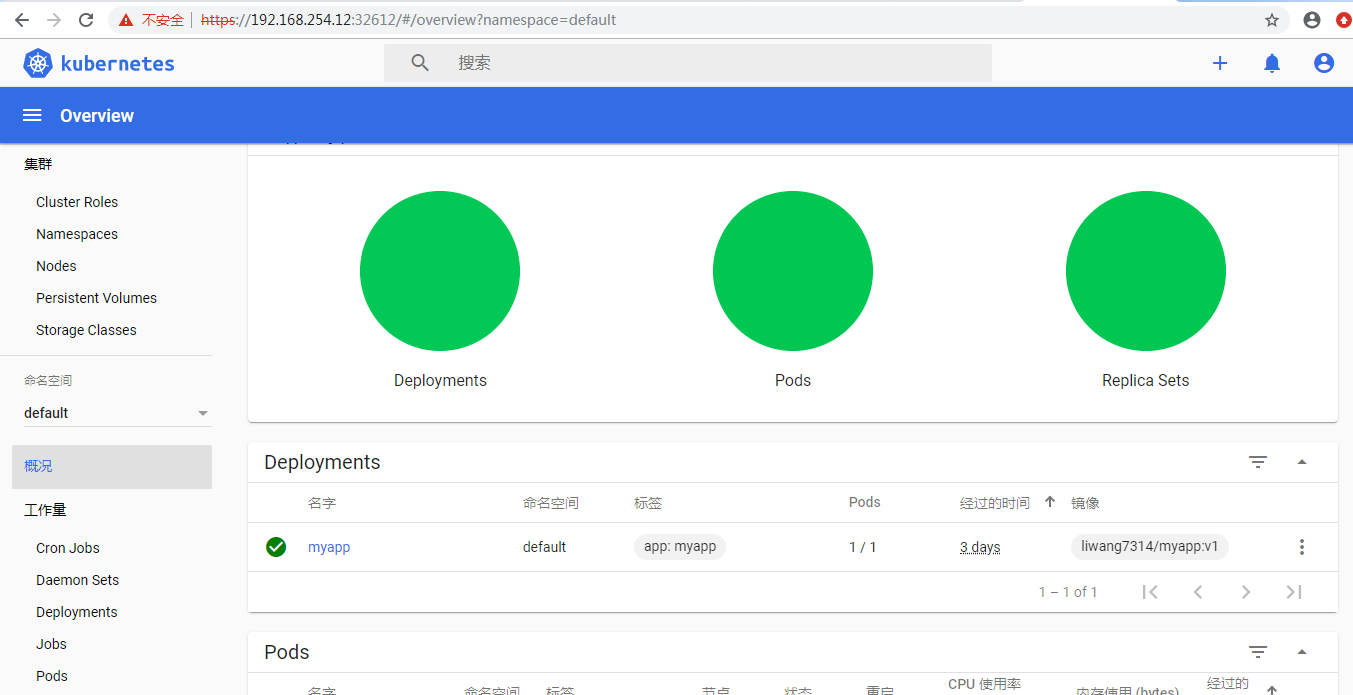
如果输入token进入到页面发现显示不出信息,说明你的token没有权限,可以自己创建一个,并赋予权限
1.添加serviceaccount账户,设置并使其可登陆 apiVersion: v1 kind: ServiceAccount metadata: name: aks-dashboard-admin namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: aks-dashboard-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: aks-dashboard-admin namespace: kube-system 2.创建完全管理权限 apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard labels: k8s-app: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kube-system apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard-head labels: k8s-app: kubernetes-dashboard-head roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: kubernetes-dashboard-head namespace: kube-system

