traefik安装
官网:https://doc.traefik.io/traefik/
1.Traefik 介绍
traefik 是一款反向代理、负载均衡服务,使用 golang 实现的。和 nginx 最大的不同是,它支持自动化更新反向代理和负载均衡配置。在微服务架构越来越流行的今天,一个业务恨不得有好几个数据库、后台服务和 webapp,开发团队拥有一款 “智能” 的反向代理服务,为他们简化服务配置。traefik 就是为了解决这个问题而诞生的。
Traefik 是一个开源的可以使服务发布变得轻松有趣的边缘路由器。它负责接收你系统的请求,然后使用合适的组件来对这些请求进行处理。
除了众多的功能之外,Traefik 的与众不同之处还在于它会自动发现适合你服务的配置。当 Traefik 在检查你的服务时,会找到服务的相关信息并找到合适的服务来满足对应的请求。
Traefik 兼容所有主流的集群技术,比如 Kubernetes,Docker,Docker Swarm,AWS,Mesos,Marathon,等等;并且可以同时处理多种方式。(甚至可以用于在裸机上运行的比较旧的软件。)
有了Traefik,就不需要维护和同步一个单独的配置文件:一切都会自动、实时地发生(没有重新启动,没有连接中断)。使用Traefik,您可以花时间在系统中开发和部署新特性,而不是配置和维护其工作状态。

二、概念Edge Router
Traefik 是一个边缘路由器,是你整个平台的大门,拦截并路由每个传入的请求:它知道所有的逻辑和规则,这些规则确定哪些服务处理哪些请求;传统的反向代理需要一个配置文件,其中包含路由到你服务的所有可能路由,而 Traefik 会实时检测服务并自动更新路由规则,可以自动服务发现。
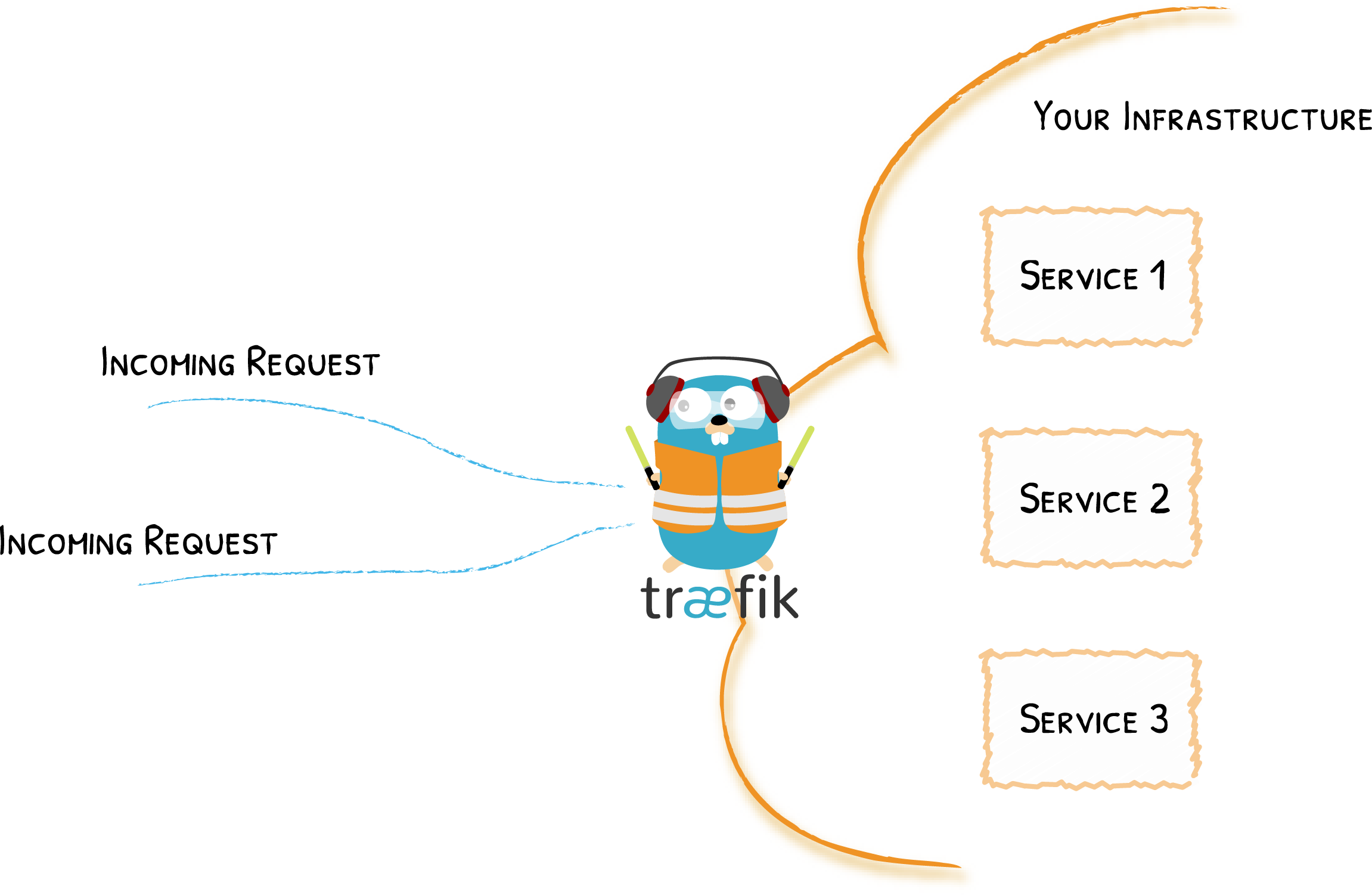
Auto Service Discovery
传统的边缘路由器(或反向代理)需要一个包含到服务的每个可能路由的配置文件,Traefik从服务本身获取它们。
在部署您的服务时,您需要附加一些信息,告诉Traefik服务可以处理的请求的特征。
这意味着在部署服务时,Traefik会立即检测到它并实时更新路由规则。反之亦然:当您从基础设施中删除服务时,路由将相应地消失。
您不再需要创建和同步混杂着IP地址或其他规则的配置文件。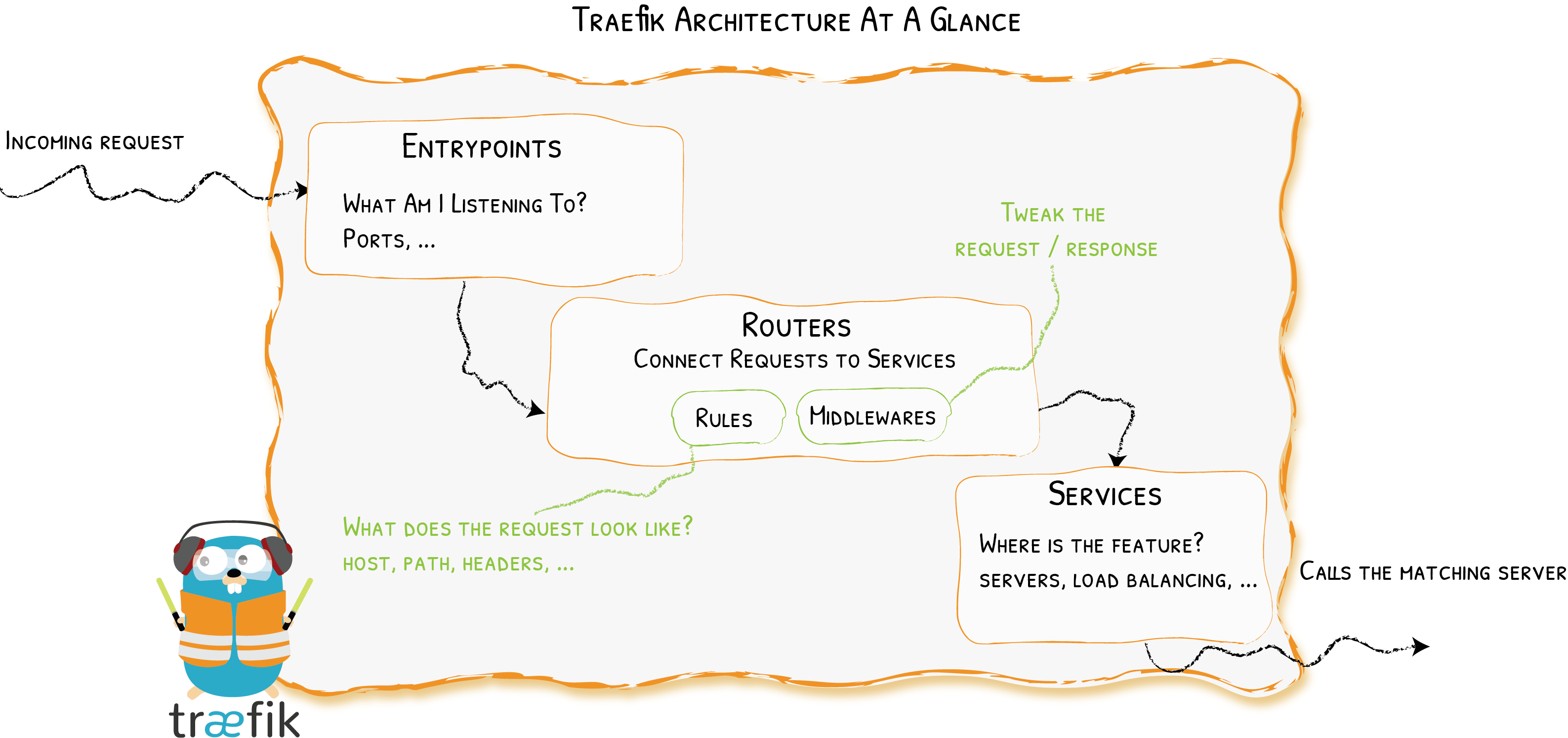
在了解 Traefik 之前有几个核心概念我们必须要了解:
Providers 用来自动发现平台上的服务,可以是编排工具、容器引擎或者 key-value 存储等,比如 Docker、Kubernetes、File
Entrypoints 监听传入的流量(端口等…),是网络入口点,它们定义了接收请求的端口(HTTP 或者 TCP)。
Routers 分析请求(host, path, headers, SSL, …),负责将传入请求连接到可以处理这些请求的服务上去。
Services 将请求转发给你的应用(load balancing, …),负责配置如何获取最终将处理传入请求的实际服务。
Middlewares 中间件,用来修改请求或者根据请求来做出一些判断(authentication, rate limiting, headers, …),中间件被附件到路由上,是一种在请求发送到你的服务之前(或者在服务的响应发送到客户端之前)调整请求的一种方法。
三、安装
由于 Traefik 2.X 版本和之前的 1.X 版本不兼容,而且1.X 已经停止更新了。我们这里选择功能更加强大的 2.X 版本来和大家进行讲解,我们这里使用的镜像是 traefik:2.3.2。
本文档使用KubernetesCRD 作为provider,所以需要创建CRD
3.1 创建 traefik-crd.yaml 文件
traefik-crd.yaml
# All resources definition must be declared apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: ingressroutes.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: IngressRoute plural: ingressroutes singular: ingressroute scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: middlewares.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: Middleware plural: middlewares singular: middleware scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: ingressroutetcps.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: IngressRouteTCP plural: ingressroutetcps singular: ingressroutetcp scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: ingressrouteudps.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: IngressRouteUDP plural: ingressrouteudps singular: ingressrouteudp scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: tlsoptions.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: TLSOption plural: tlsoptions singular: tlsoption scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: tlsstores.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: TLSStore plural: tlsstores singular: tlsstore scope: Namespaced --- apiVersion: apiextensions.k8s.io/v1beta1 kind: CustomResourceDefinition metadata: name: traefikservices.traefik.containo.us spec: group: traefik.containo.us version: v1alpha1 names: kind: TraefikService plural: traefikservices singular: traefikservice scope: Namespaced
3.2 创建rbac权限
traefik-rbac.yaml
kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: traefik-ingress-controller rules: - apiGroups: - "" resources: - services - endpoints - secrets verbs: - get - list - watch - apiGroups: - extensions - networking.k8s.io resources: - ingresses - ingressclasses verbs: - get - list - watch - apiGroups: - extensions resources: - ingresses/status verbs: - update - apiGroups: - traefik.containo.us resources: - middlewares - ingressroutes - traefikservices - ingressroutetcps - ingressrouteudps - tlsoptions - tlsstores verbs: - get - list - watch --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: traefik-ingress-controller roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: traefik-ingress-controller subjects: - kind: ServiceAccount name: traefik-ingress-controller
3.3 创建traefik配置文件
在 Traefik 中的配置可以使用两种不同的方式:
动态配置:完全动态的路由配置
静态配置:启动配置
静态配置中的元素(这些元素不会经常更改)连接到 providers 并定义 Treafik 将要监听的 entrypoints。
在 Traefik 中有三种方式定义静态配置:在配置文件中、在命令行参数中、通过环境变量传递
动态配置包含定义系统如何处理请求的所有配置内容,这些配置是可以改变的,而且是无缝热更新的,没有任何请求中断或连接损耗。
我们这里将通用的基本配置放到静态配置里面,以configmap 形式实现
traefik-config-cm.yaml
kind: ConfigMap apiVersion: v1 metadata: name: traefik-config data: traefik.yaml: |- serversTransport: insecureSkipVerify: true ## Traefik 忽略验证代理服务的 TLS 证书 api: insecure: true ## 允许 HTTP 方式访问 API dashboard: true ## 启用 Dashboard debug: false ## 启用 Debug 调试模式 metrics: prometheus: metrics ## 配置 Prometheus 监控指标数据,并使用默认配置 entryPoints: web: address: ":80" ## 配置 80 端口,并设置入口名称为 web websecure: address: ":443" ## 配置 443 端口,并设置入口名称为 websecure traefik: address: ":8090" ## 配置 8090 端口,并设置入口名称为 dashboard metrics: address: ":8082" ## 配置 8082 端口,作为metrics收集入口 tcpep: address: ":8000" ## 配置 8000 端口,作为tcp入口 udpep: address: ":9000/udp" ## 配置 9000 端口,作为udp入口 providers: kubernetescrd: ## 启用 Kubernetes CRD 方式来配置路由规则 ingressclass: traefik-v2.3 kubernetesingress: ## 启动 Kubernetes Ingress 方式来配置路由规则 ingressclass: traefik-v2.3 log: filePath: "/etc/traefik/logs/traefik.log" ## 设置调试日志文件存储路径,如果为空则输出到控制台 level: error ## 设置调试日志级别 format: "" ## 设置调试日志格式 accessLog: filePath: "/etc/traefik/logs/access.log" ## 设置访问日志文件存储路径,如果为空则输出到控制台 format: "" ## 设置访问调试日志格式 bufferingSize: 0 ## 设置访问日志缓存行数 filters: #statusCodes: ["200"] ## 设置只保留指定状态码范围内的访问日志 retryAttempts: true ## 设置代理访问重试失败时,保留访问日志 minDuration: 20 ## 设置保留请求时间超过指定持续时间的访问日志 fields: ## 设置访问日志中的字段是否保留(keep 保留、drop 不保留) defaultMode: keep ## 设置默认保留访问日志字段 names: ## 针对访问日志特别字段特别配置保留模式 ClientUsername: drop headers: ## 设置 Header 中字段是否保留 defaultMode: keep ## 设置默认保留 Header 中字段 names: ## 针对 Header 中特别字段特别配置保留模式 User-Agent: redact Authorization: drop Content-Type: keep
3.4 部署traefik
traefik-deploy.yaml
apiVersion: v1 kind: ServiceAccount metadata: name: traefik-ingress-controller --- kind: Deployment apiVersion: apps/v1 metadata: name: traefik-v2 labels: app: traefik-v2 spec: replicas: 2 selector: matchLabels: app: traefik-v2 template: metadata: labels: app: traefik-v2 spec: serviceAccountName: traefik-ingress-controller terminationGracePeriodSeconds: 1 containers: - name: traefik-v2 image: harbor.foxchan.com/traefik/traefik:v2.3 args: - --configfile=/config/traefik.yaml ports: - name: web containerPort: 80 - name: admin containerPort: 8090 - name: tcpep containerPort: 8000 - name: udpep containerPort: 9000 securityContext: capabilities: ## 只开放网络权限 drop: - ALL add: - NET_BIND_SERVICE volumeMounts: - mountPath: "/config" name: "config" - mountPath: /etc/traefik/logs name: logdir - mountPath: /etc/localtime name: timezone readOnly: true volumes: - name: config configMap: name: traefik-config - name: logdir hostPath: path: /data/traefik/logs type: "DirectoryOrCreate" - name: timezone hostPath: path: /etc/localtime type: File tolerations: - operator: "Exists" ## 设置容忍所有污点,防止节点被设置污点 hostNetwork: true ## 开启host网络,提高网络入口的网络性能 nodeSelector: ## 设置node筛选器,在特定label的节点上启动 IngressProxy: "traefik2.3" --- apiVersion: v1 kind: Service metadata: name: traefik-v2 spec: type: LoadBalancer selector: app: traefik-v2 ports: - protocol: TCP port: 80 name: web targetPort: 80 - protocol: TCP port: 8090 name: admin targetPort: 8090 - protocol: TCP port: 8000 name: tcpep targetPort: 8000 --- apiVersion: v1 kind: Service metadata: name: traefikudp-v2 spec: type: LoadBalancer selector: app: traefik-v2 ports: - protocol: UDP port: 9000 name: udpep targetPort: 9000
四、路由配置
4.1 配置 HTTP 路由规则
Traefik 已经部署完成,但是想让外部访问 Kubernetes 内部服务,还需要配置路由规则,这里用traefik dashboard 和 whoami 举例。
首先创建whoami 的 deployment
whoami.yaml
kind: Deployment apiVersion: apps/v1 metadata: name: whoami namespace: default labels: app: traefiklabs name: whoami spec: replicas: 2 selector: matchLabels: app: traefiklabs task: whoami template: metadata: labels: app: traefiklabs task: whoami spec: containers: - name: whoami image: traefik/whoami ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: whoami namespace: default spec: ports: - name: http port: 80 selector: app: traefiklabs task: whoami --- kind: Deployment apiVersion: apps/v1 metadata: name: whoamitcp namespace: default labels: app: traefiklabs name: whoamitcp spec: replicas: 2 selector: matchLabels: app: traefiklabs task: whoamitcp template: metadata: labels: app: traefiklabs task: whoamitcp spec: containers: - name: whoamitcp image: traefik/whoamitcp ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: whoamitcp namespace: default spec: ports: - protocol: TCP port: 8080 selector: app: traefiklabs task: whoamitcp --- kind: Deployment apiVersion: apps/v1 metadata: name: whoamiudp namespace: default labels: app: traefiklabs name: whoamiudp spec: replicas: 2 selector: matchLabels: app: traefiklabs task: whoamiudp template: metadata: labels: app: traefiklabs task: whoamiudp spec: containers: - name: whoamiudp image: traefik/whoamiudp:latest ports: - containerPort: 8080 --- apiVersion: v1 kind: Service metadata: name: whoamiudp namespace: default spec: ports: - port: 8080 selector: app: traefiklabs task: whoamiudp
dashboard.yaml
因为静态配置文件指定了ingressclass,所以这里的annotations 要指定,否则访问会404
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: traefik-dashboard namespace: default annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - web routes: - match: Host(`traefik.foxchan.com`) kind: Rule services: - name: api@internal kind: TraefikService
whoami-ingressroute.yaml
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: myingressroute namespace: default annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - web routes: - match: Host(`whoami.foxchan.com`) && PathPrefix(`/`) kind: Rule services: - name: whoami port: 80
接下来配置 Hosts,客户端想通过域名访问服务,必须要进行 DNS 解析,这里可以通过 DNS 服务器进行域名解析,也可以修改 hosts 文件将 Traefik 指定节点的 IP 和自定义 host 绑定
4.2 配置 HTTPS 路由规则
如果我们需要用 HTTPS 来访问我们这个应用的话,就需要监听 websecure 这个入口点,也就是通过 443 端口来访问,同样用 HTTPS 访问应用必然就需要证书,这里我们用 openssl 来创建一个自签名的证书:
$ openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=whoami.foxchan.com"
然后通过 Secret 对象来引用证书文件:
# 要注意证书文件名称必须是 tls.crt 和 tls.key $ kubectl create secret tls who-tls --cert=tls.crt --key=tls.key secret/who-tls created
这个时候我们就可以创建一个 HTTPS 访问应用的 IngressRoute 对象了:
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: ingressroutetls annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - websecure routes: - match: Host(`whoami.foxchan.com`) kind: Rule services: - name: whoami port: 80 tls: secretName: who-tls
4.3 配置 TCP 路由规则
whoami-tcp.yaml
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRouteTCP metadata: name: ingressroutetcpwho annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - tcpep routes: - match: HostSNI(`*`) services: - name: whoamitcp port: 8080
4.4 配置udp路由规则
whoami-udp.yaml
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRouteUDP metadata: name: ingressrouteudpwho annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - udpep routes: - services: - name: whoamiudp port: 8080
五、中间件
中间件是 Traefik2.0 中一个非常有特色的功能,我们可以根据自己的各种需求去选择不同的中间件来满足服务,Traefik 官方已经内置了许多不同功能的中间件,其中一些可以修改请求,头信息,一些负责重定向,一些添加身份验证等等,而且中间件还可以通过链式组合的方式来适用各种情况。
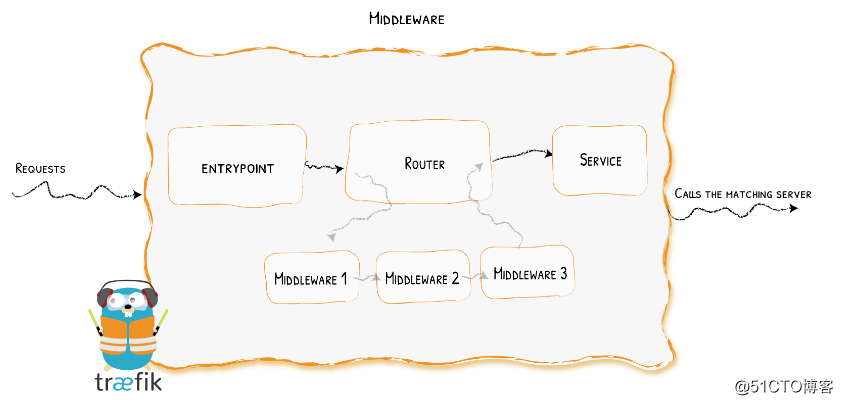
白名单举例
上面的dashboard属于重要信息,我们可以设置只能白名单的ip可以访问
创建白名单中间件
middleware-ipwhitelist.yaml
apiVersion: traefik.containo.us/v1alpha1 kind: Middleware metadata: name: gs-ipwhitelist spec: ipWhiteList: sourceRange: - 127.0.0.1 - 10.244.0.0/16 - 10.96.0.0/12 - 192.168.0.0/24
然后将这个中间件附加到 dashboard的服务上面去
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: traefik-dashboard namespace: default annotations: kubernetes.io/ingress.class: traefik-v2.3 spec: entryPoints: - web routes: - match: Host(`traefik.foxchan.com`) kind: Rule services: - name: api@internal kind: TraefikService middlewares: #这里添加中间件的名字 - name: gs-ipwhitelist
这个时候我们再去访问dashboard,不在白名单的就会报403,关于更多中间件的用法可以查看文档 Traefik Docs。
六、路由配置(高级)
在实际的生产环境,除了上线业务之外,还有更复杂的使用要求。
在开始traefik的高级用法之前,还需要了解一个TraefikService,通过把TraefikService注册到CRD来实现更复杂的请求设置。
TraefikService 目前能用于以下功能
servers load balancing.(负载均衡)
services Weighted Round Robin load balancing.(权重轮询)
services mirroring.(镜像)
6.1 负载均衡
创建k8s service
apiVersion: v1 kind: Service metadata: name: svc1 namespace: default spec: ports: - name: http port: 80 selector: app: v1 --- apiVersion: v1 kind: Service metadata: name: svc2 namespace: default spec: ports: - name: http port: 80 selector: app: v2
创建IngressRoute
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: ingressroutelb namespace: default spec: entryPoints: - web routes: - match: Host(`whoami.foxchan.com`) kind: Rule services: - name: svc1 namespace: default - name: svc2 namespace: default
6.2 权重轮询
创建TraefikService
apiVersion: traefik.containo.us/v1alpha1 kind: TraefikService metadata: name: wrr namespace: default spec: weighted: services: - name: svc1 port: 80 weight: 3 # 定义权重 kind: Service # 可选,默认就是 Service - name: svc2 port: 80 weight: 1
创建IngressRoute
需要注意的是现在我们配置的 Service 不再是直接的 Kubernetes 对象了,而是上面我们定义的 TraefikService 对象
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: ingressroutewrr namespace: default spec: entryPoints: - web routes: - match: Host(`who.foxchan.com`) kind: Rule services: - name: wrr namespace: default kind: TraefikService
6.3 镜像
这里的流量复制演示2种
流量复制到k8s 的service
# Mirroring from a k8s Service apiVersion: traefik.containo.us/v1alpha1 kind: TraefikService metadata: name: mirror-k8s namespace: default spec: mirroring: name: svc1 # 发送 100% 的请求到 K8S 的 Service "v1" port: 80 mirrors: - name: svc2 # 然后复制 20% 的请求到 v2 port: 80 percent: 20
流量从Traefik Service 导入
# Mirroring from a Traefik Service apiVersion: traefik.containo.us/v1alpha1 kind: TraefikService metadata: name: mirror-ts namespace: default spec: mirroring: name: mirror-k8s #流量入口从TraefikService 来 kind: TraefikService mirrors: - name: svc2 port: 80 percent: 20
创建IngressRoute
apiVersion: traefik.containo.us/v1alpha1 kind: IngressRoute metadata: name: ingressroute-mirror namespace: default spec: entryPoints: - web routes: - match: Host(`who.foxchan.com`) kind: Rule services: - name: mirror-k8s namespace: default kind: TraefikService
helm安装方式
helm repo add --insecure-skip-tls-verify traefik https://helm.traefik.io/traefik helm repo update helm repo list helm install --insecure-skip-tls-verify traefik traefik/traefik
参考:https://www.cnblogs.com/heian99/p/14608414.html
https://blog.51cto.com/foxhound/2545116?source=dra



