前面的博文中我们陆续讲到了向0个组织的网络中添加组织的并成功调用链码的步骤,下面我们来做一个实验,从0开始,向org1中添加用户并调用链码
一,配置文件准备:
下面列出了我们需要准备的配置文件
本文还是以fabric v1.4.3为版本进行实验
安装基础工具这里不做过多的讲解:
只是需要注意安装fabric-ca-client的工具包
hyperledger-fabric-ca-linux-amd64-1.4.3.tar.gz
下载地址前面的文章都有提过,请自行查询
需要准备的文件如下:
- configtx.yaml
- crypto-config-order.yaml
- crypto-config-orgs-extend.yaml
- crypto-config-orgs.yaml
- docker-fabric-dps-ca.yaml
- docker-fabric-dps-cli.yaml
- docker-fabric-dps-couchdb.yaml
- docker-orderer.yaml
- docker-peer0-org1.yaml
还有这次的实验我们以network006为网络名称
新建地址:/usr/local/gopath/src/github.com/hyperledger/fabric/network006
并将之前提到的软件包下载至此,并进行安装
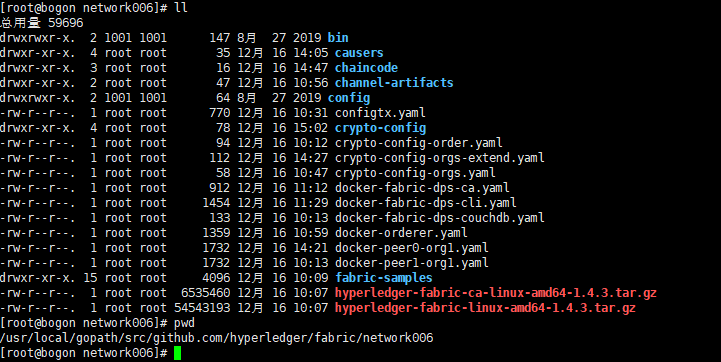
各文件内容如下:
configtx.yaml内容:
Organizations: - &OrdererOrg Name: OrdererOrg ID: OrdererMSP MSPDir: crypto-config/ordererOrganizations/example.com/msp Orderer: &OrdererDefaults OrdererType: solo Addresses: - orderer.example.com:7050 BatchTimeout: 2s BatchSize: MaxMessageCount: 10 AbsoluteMaxBytes: 98 MB PreferredMaxBytes: 512 KB Kafka: Brokers: - 127.0.0.1:9092 Organizations: Application: &ApplicationDefaults Organizations: Profiles: ZeroOrgsOrdererGenesis: Orderer: <<: *OrdererDefaults Organizations: - *OrdererOrg Consortiums: SampleConsortium: Organizations: ZeroOrgsChannel: Consortium: SampleConsortium Application: <<: *ApplicationDefaults Organizations:
crypto-config-order.yaml内容:
OrdererOrgs:
- Name: Orderer
Domain: example.com
Specs:
- Hostname: orderer
crypto-config-orgs-extend.yaml内容:
PeerOrgs:
- Name: Org1
Domain: org1.example.com
CA:
Hostname: ca
Template:
Count: 1
请注意这里的CA,通过测试在通过命令cryptogen extend去扩展组织时,指定不指定都会通过org1的ca 目录下的ca证书去签名,这里的CA中心指的是以org1ca为根证书的ca服务,每一个组织都会有自己的CA证书 ,通过工具cryptogen生成时,每个组织的ca目录下的证书信息都不一样,但是每个组织下的 peer节点和用户的都一样,这里需要注意,在遇到调用链码出现访问被禁止时,也可以查看创建的用户的cacerts目录下的证书是否和组织下的ca目录下的证书一样,如果不一样,说明你在生成用户是连接的ca服务器不是本组织的所以不对。
crypto-config-orgs.yaml内容:
PeerOrgs:
- Name: Org1
Domain: org1.example.com
这里我们没有指定template 和users,指定的化系统会用默认的工具生成组织的msp 所以我们不指定,后面我们会用CA中心创建user和扩展组织
docker-fabric-dps-ca.yaml内容:
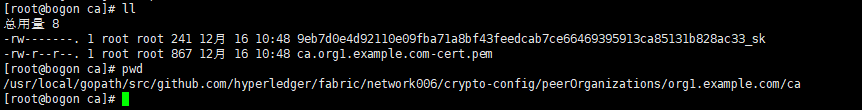
version: '2' services: ca: container_name: ca image: hyperledger/fabric-ca environment: - FABRIC_CA_HOME=/etc/hyperledger/fabric-ca-server - FABRIC_CA_SERVER_CA_NAME=ca - FABRIC_CA_SERVER_TLS_ENABLED=false - FABRIC_CA_SERVER_TLS_CERTFILE=/etc/hyperledger/fabric-ca-server-config/ca.org1.example.com-cert.pem - FABRIC_CA_SERVER_TLS_KEYFILE=/etc/hyperledger/fabric-ca-server-config/9eb7d0e4d92110e09fba71a8bf43feedcab7ce66469395913ca85131b828ac33_sk ports: - "7054:7054" command: sh -c 'fabric-ca-server start --ca.certfile /etc/hyperledger/fabric-ca-server-config/ca.org1.example.com-cert.pem --ca.keyfile /etc/hyperledger/fabric-ca-server-config/9eb7d0e4d92110e09fba71a8bf43feedcab7ce66469395913ca85131b828ac33_sk -b admin:adminpw -d' volumes: - ./crypto-config/peerOrganizations/org1.example.com/ca/:/etc/hyperledger/fabric-ca-server-config
此处的CA服务镜像配置当中的证书信息,是我们通过crypto-config-orgs.yaml文件生成的组织的ca信息,路径是在/usr/local/gopath/src/github.com/hyperledger/fabric/network006/crypto-config/peerOrganizations/org1.example.com/ca
docker-fabric-dps-cli.yaml内容:
version: '2' services: cli: container_name: cli image: hyperledger/fabric-tools tty: true environment: - GOPATH=/opt/gopath - CORE_VM_ENDPOINT=unix:///host/var/run/docker.sock - CORE_LOGGING_LEVEL=DEBUG - CORE_PEER_ID=cli - CORE_PEER_ADDRESS=peer0.org1.example.com:7051 - CORE_PEER_LOCALMSPID=Org1MSP - CORE_PEER_TLS_ENABLED=false - CORE_PEER_TLS_CERT_FILE=/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/server.crt - CORE_PEER_TLS_KEY_FILE=/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/server.key - CORE_PEER_TLS_ROOTCERT_FILE=/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls/ca.crt - CORE_PEER_MSPCONFIGPATH=/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/peerOrganizations/org1.example.com/users/Admin@org1.example.com/msp working_dir: /opt/gopath/src/github.com/hyperledger/fabric/peer volumes: - /var/run/:/host/var/run/ - ./chaincode/go/:/opt/gopath/src/github.com/hyperledger/fabric/network006/chaincode/go - ./crypto-config:/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/ - ./channel-artifacts:/opt/gopath/src/github.com/hyperledger/fabric/peer/channel-artifacts
docker-fabric-dps-couchdb.yaml内容:
version: '2'
services:
couchdb:
container_name: couchdb
image: hyperledger/fabric-couchdb
ports:
- "5984:5984"
docker-orderer.yaml内容:
version: '2' services: orderer.example.com: container_name: orderer.example.com image: hyperledger/fabric-orderer environment: - CORE_VM_DOCKER_HOSTCONFIG_NETWORKMODE=aberic_default - ORDERER_GENERAL_LOGLEVEL=debug - ORDERER_GENERAL_LISTENADDRESS=0.0.0.0 - ORDERER_GENERAL_LISTENPORT=7050 - ORDERER_GENERAL_GENESISMETHOD=file - ORDERER_GENERAL_GENESISFILE=/var/hyperledger/orderer/orderer.genesis.block - ORDERER_GENERAL_LOCALMSPID=OrdererMSP - ORDERER_GENERAL_LOCALMSPDIR=/var/hyperledger/orderer/msp - ORDERER_GENERAL_TLS_ENABLED=false - ORDERER_GENERAL_TLS_PRIVATEKEY=/var/hyperledger/orderer/tls/server.key - ORDERER_GENERAL_TLS_CERTIFICATE=/var/hyperledger/orderer/tls/server.crt - ORDERER_GENERAL_TLS_ROOTCAS=[/var/hyperledger/orderer/tls/ca.crt] working_dir: /opt/gopath/src/github.com/hyperledger/fabric command: orderer volumes: - ./channel-artifacts/genesis.block:/var/hyperledger/orderer/orderer.genesis.block - ./crypto-config/ordererOrganizations/example.com/orderers/orderer.example.com/msp:/var/hyperledger/orderer/msp - ./crypto-config/ordererOrganizations/example.com/orderers/orderer.example.com/tls/:/var/hyperledger/orderer/tls networks: default: aliases: - network006 ports: - 7050:7050
docker-peer0-org1.yaml内容:
version: '2' services: peer0.org1.example.com: container_name: peer0.org1.example.com image: hyperledger/fabric-peer environment: - CORE_LEDGER_STATE_STATEDATABASE=CouchDB - CORE_LEDGER_STATE_COUCHDBCONFIG_COUCHDBADDRESS=couchdb:5984 - CORE_PEER_ID=peer0.org1.example.com - CORE_PEER_NETWORKID=network006 - CORE_PEER_ADDRESS=peer0.org1.example.com:7051 - CORE_PEER_CHAINCODELISTENADDRESS=peer0.org1.example.com:7052 - CORE_PEER_GOSSIP_EXTERNALENDPOINT=peer0.org1.example.com:7051 - CORE_PEER_LOCALMSPID=Org1MSP - CORE_VM_ENDPOINT=unix:///host/var/run/docker.sock - CORE_VM_DOCKER_HOSTCONFIG_NETWORKMODE=network006 - CORE_LOGGING_LEVEL=DEBUG - CORE_VM_DOCKER_HOSTCONFIG_NETWORKMODE=network006_default - CORE_PEER_GOSSIP_SKIPHANDSHAKE=true - CORE_PEER_GOSSIP_USELEADERELECTION=true - CORE_PEER_GOSSIP_ORGLEADER=false - CORE_PEER_PROFILE_ENABLED=false - CORE_PEER_TLS_ENABLED=false - CORE_PEER_TLS_CERT_FILE=/etc/hyperledger/fabric/tls/server.crt - CORE_PEER_TLS_KEY_FILE=/etc/hyperledger/fabric/tls/server.key - CORE_PEER_TLS_ROOTCERT_FILE=/etc/hyperledger/fabric/tls/ca.crt volumes: - /var/run/:/host/var/run/ - ./crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/msp:/etc/hyperledger/fabric/msp - ./crypto-config/peerOrganizations/org1.example.com/peers/peer0.org1.example.com/tls:/etc/hyperledger/fabric/tls working_dir: /opt/gopath/src/github.com/hyperledger/fabric/peer command: peer node start ports: - 7051:7051 - 7052:7052 - 7053:7053 networks: default: aliases: - network006
准备文件已经完成:
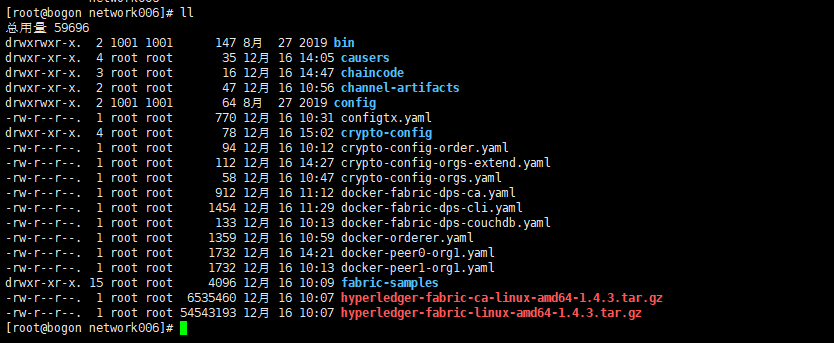
二,通过命令生成order和org的msp信息
生成order msp信息
cryptogen generate --config=./crypto-config-order.yaml
生成org1 mspx信息
cryptogen generate --config=./crypto-config-orgs.yaml
三,生成创世区块和通道交易文件
生成创世区块
configtxgen -profile ZeroOrgsOrdererGenesis -outputBlock ./channel-artifacts/genesis.block
生成通道交易文件
configtxgen -profile ZeroOrgsChannel -outputCreateChannelTx ./channel-artifacts/mychannel.tx -channelID mychannel
四,启动order节点,CA服务,couchDB
1 docker-compose -f docker-orderer.yaml up -d 2 docker-compose -f docker-fabric-dps-ca.yaml up -d 3 docker-compose -f docker-fabric-dps-couchdb.yaml up -d
五,通过CA中心扩展org1
1 cryptogen extend --config=./crypto-config-orgs-extend.yaml
此时生成的peer0节点就是通过 CA中心签名过的,所生成的msp信息里的cacerts里的内容就是ca中心的证书文件,自己可以对比下
六,启动peer0.org1节点,启动cli容器
1 docker-compose -f docker-peer0-org1.yaml up -d 2 docker-compose -f docker-fabric-dps-cli.yaml up -d
七,登录cli,此时连接的是peer0.org1节点,穿件通道区块,并加入组织org1
此处只列出命令,详细情况请阅读我的文章《向现有的 Fabric 区块链网络添加一个组织》
1 docker exec -it cli bash 2 peer channel create -o orderer.example.com:7050 -c mychannel -f ./channel-artifacts/mychannel.tx 3 peer channel fetch config config_block.pb -o orderer.example.com:7050 -c mychannel 4 configtxlator proto_decode --input config_block.pb --type common.Block | jq .data.data[0].payload.data.config > config.json
基于config.json添加Org1MSP信息生成updated_config.json:
内容如下:
{
"channel_group": {
"groups": {
"Application": {
"groups": {
"Org1MSP": {
"groups": {},
"mod_policy": "Admins",
"policies": {
"Admins": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "Org1MSP",
"role": "ADMIN"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
},
"Readers": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "Org1MSP",
"role": "MEMBER"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
},
"Writers": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "Org1MSP",
"role": "MEMBER"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
}
},
"values": {
"MSP": {
"mod_policy": "Admins",
"value": {
"config": {
"admins": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNHVENDQWIrZ0F3SUJBZ0lRWGlzbWdPblViVnFwNlpZQ2NMM0lyakFLQmdncWhrak9QUVFEQWpCek1Rc3cKQ1FZRFZRUUdFd0pWVXpFVE1CRUdBMVVFQ0JNS1EyRnNhV1p2Y201cFlURVdNQlFHQTFVRUJ4TU5VMkZ1SUVaeQpZVzVqYVhOamJ6RVpNQmNHQTFVRUNoTVFiM0puTVM1bGVHRnRjR3hsTG1OdmJURWNNQm9HQTFVRUF4TVRZMkV1CmIzSm5NUzVsZUdGdGNHeGxMbU52YlRBZUZ3MHlNREV5TVRZd01qUXpNREJhRncwek1ERXlNVFF3TWpRek1EQmEKTUZzeEN6QUpCZ05WQkFZVEFsVlRNUk13RVFZRFZRUUlFd3BEWVd4cFptOXlibWxoTVJZd0ZBWURWUVFIRXcxVApZVzRnUm5KaGJtTnBjMk52TVI4d0hRWURWUVFEREJaQlpHMXBia0J2Y21jeExtVjRZVzF3YkdVdVkyOXRNRmt3CkV3WUhLb1pJemowQ0FRWUlLb1pJemowREFRY0RRZ0FFMElQKzNvS2FiNllkUEpyU2JJQStOdmdpSFQzckU3NHIKRmU0MUtSUm5RbVAydXIvSEY0cVUrOHBLdTNPS2szdjNtMmszMzJaZDViY0RYb1UrMk5JMXg2Tk5NRXN3RGdZRApWUjBQQVFIL0JBUURBZ2VBTUF3R0ExVWRFd0VCL3dRQ01BQXdLd1lEVlIwakJDUXdJb0FnbnJmUTVOa2hFT0NmCnVuR292MFArN2NxM3ptWkdrNVdSUEtoUk1iZ29yRE13Q2dZSUtvWkl6ajBFQXdJRFNBQXdSUUloQUxCbHViT3oKTDA4WjlpRmxiYVZMZG56UUxjaVNqMmJUWERLbU9NZzRWOWNjQWlCTVk1ZHlGNU1ILzU0MVRtOWtaclYxRzJsLwpFUU5SSEJtb0paeHF1cW9jblE9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg=="
],
"crypto_config": {
"identity_identifier_hash_function": "SHA256",
"signature_hash_family": "SHA2"
},
"fabric_node_ous": null,
"intermediate_certs": [],
"name": "Org1MSP",
"organizational_unit_identifiers": [],
"revocation_list": [],
"root_certs": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNVakNDQWZpZ0F3SUJBZ0lSQUtZc3JWWkhVcGVMTU94Y1dZKzNMNjR3Q2dZSUtvWkl6ajBFQXdJd2N6RUwKTUFrR0ExVUVCaE1DVlZNeEV6QVJCZ05WQkFnVENrTmhiR2xtYjNKdWFXRXhGakFVQmdOVkJBY1REVk5oYmlCRwpjbUZ1WTJselkyOHhHVEFYQmdOVkJBb1RFRzl5WnpFdVpYaGhiWEJzWlM1amIyMHhIREFhQmdOVkJBTVRFMk5oCkxtOXlaekV1WlhoaGJYQnNaUzVqYjIwd0hoY05NakF4TWpFMk1ESTBNekF3V2hjTk16QXhNakUwTURJME16QXcKV2pCek1Rc3dDUVlEVlFRR0V3SlZVekVUTUJFR0ExVUVDQk1LUTJGc2FXWnZjbTVwWVRFV01CUUdBMVVFQnhNTgpVMkZ1SUVaeVlXNWphWE5qYnpFWk1CY0dBMVVFQ2hNUWIzSm5NUzVsZUdGdGNHeGxMbU52YlRFY01Cb0dBMVVFCkF4TVRZMkV1YjNKbk1TNWxlR0Z0Y0d4bExtTnZiVEJaTUJNR0J5cUdTTTQ5QWdFR0NDcUdTTTQ5QXdFSEEwSUEKQkJvd3hpeHpVelh5UWl1dnZjU2pCSThFVUYxTlgzampoMVRuMjNXb1lxSmdZdUhqenJIY0lWQXkzWkUrZHg1KwpLM2NPRUcyaTN6OTF6eVpYVVRSUml2aWpiVEJyTUE0R0ExVWREd0VCL3dRRUF3SUJwakFkQmdOVkhTVUVGakFVCkJnZ3JCZ0VGQlFjREFnWUlLd1lCQlFVSEF3RXdEd1lEVlIwVEFRSC9CQVV3QXdFQi96QXBCZ05WSFE0RUlnUWcKbnJmUTVOa2hFT0NmdW5Hb3YwUCs3Y3Ezem1aR2s1V1JQS2hSTWJnb3JETXdDZ1lJS29aSXpqMEVBd0lEU0FBdwpSUUloQU5RRUpwZ2treU4yYnZreVdqSFJXR1U1SVNCU0NwdzZ4RTdCa0kxZlJvR1dBaUJsUGMrOEh5bXlZTnd4CmdNZ2h2NXY3Vk5KNzBHMVJYNmNVdG5qbGdqMmU5Zz09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K"
],
"signing_identity": null,
"tls_intermediate_certs": [],
"tls_root_certs": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNWekNDQWY2Z0F3SUJBZ0lSQUtpQWdlaVdRVURnc2g0WnVGcmh4VnN3Q2dZSUtvWkl6ajBFQXdJd2RqRUwKTUFrR0ExVUVCaE1DVlZNeEV6QVJCZ05WQkFnVENrTmhiR2xtYjNKdWFXRXhGakFVQmdOVkJBY1REVk5oYmlCRwpjbUZ1WTJselkyOHhHVEFYQmdOVkJBb1RFRzl5WnpFdVpYaGhiWEJzWlM1amIyMHhIekFkQmdOVkJBTVRGblJzCmMyTmhMbTl5WnpFdVpYaGhiWEJzWlM1amIyMHdIaGNOTWpBeE1qRTJNREkwTXpBd1doY05NekF4TWpFME1ESTAKTXpBd1dqQjJNUXN3Q1FZRFZRUUdFd0pWVXpFVE1CRUdBMVVFQ0JNS1EyRnNhV1p2Y201cFlURVdNQlFHQTFVRQpCeE1OVTJGdUlFWnlZVzVqYVhOamJ6RVpNQmNHQTFVRUNoTVFiM0puTVM1bGVHRnRjR3hsTG1OdmJURWZNQjBHCkExVUVBeE1XZEd4elkyRXViM0puTVM1bGVHRnRjR3hsTG1OdmJUQlpNQk1HQnlxR1NNNDlBZ0VHQ0NxR1NNNDkKQXdFSEEwSUFCQXorK3k0OHA5UmJ6aXpUUGZzZDdJNWFoaWNLMjhSKzErNlRtVUQ0VWhWM2pSdkpMYkNPNDZPcwpXbDY5RjVjNUgraUpsNTI1SjdxT2FiSkJRSHRZMFN1amJUQnJNQTRHQTFVZER3RUIvd1FFQXdJQnBqQWRCZ05WCkhTVUVGakFVQmdnckJnRUZCUWNEQWdZSUt3WUJCUVVIQXdFd0R3WURWUjBUQVFIL0JBVXdBd0VCL3pBcEJnTlYKSFE0RUlnUWdiTnRvZUh5aXlQZkVST1RhWXkyZk52bmVvOUUwQ0tBbHFLS3dxenVVOENzd0NnWUlLb1pJemowRQpBd0lEUndBd1JBSWdCNHU3eEtZdklrZVlNcmVDYmhGdjFFRlRlRU1BUnNaemE0VjEwMUFoMS9nQ0lDWlA3WkMzCnc3eklrMDVtaVp2SDcwVnlvVnhoblRzZzJLaWJUM2R2UERCZAotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg=="
]
},
"type": 0
},
"version": "0"
}
},
"version": "0"
}
},
"mod_policy": "Admins",
"policies": {
"Admins": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "MAJORITY",
"sub_policy": "Admins"
}
},
"version": "0"
},
"Readers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Readers"
}
},
"version": "0"
},
"Writers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Writers"
}
},
"version": "0"
}
},
"values": {},
"version": "1"
},
"Orderer": {
"groups": {
"OrdererOrg": {
"groups": {},
"mod_policy": "Admins",
"policies": {
"Admins": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "OrdererMSP",
"role": "ADMIN"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
},
"Readers": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "OrdererMSP",
"role": "MEMBER"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
},
"Writers": {
"mod_policy": "Admins",
"policy": {
"type": 1,
"value": {
"identities": [
{
"principal": {
"msp_identifier": "OrdererMSP",
"role": "MEMBER"
},
"principal_classification": "ROLE"
}
],
"rule": {
"n_out_of": {
"n": 1,
"rules": [
{
"signed_by": 0
}
]
}
},
"version": 0
}
},
"version": "0"
}
},
"values": {
"MSP": {
"mod_policy": "Admins",
"value": {
"config": {
"admins": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNDakNDQWJHZ0F3SUJBZ0lSQUs0a1loLzJTTnhiTlk4QTh2d3dxdzh3Q2dZSUtvWkl6ajBFQXdJd2FURUwKTUFrR0ExVUVCaE1DVlZNeEV6QVJCZ05WQkFnVENrTmhiR2xtYjNKdWFXRXhGakFVQmdOVkJBY1REVk5oYmlCRwpjbUZ1WTJselkyOHhGREFTQmdOVkJBb1RDMlY0WVcxd2JHVXVZMjl0TVJjd0ZRWURWUVFERXc1allTNWxlR0Z0CmNHeGxMbU52YlRBZUZ3MHlNREV5TVRZd01qUTFNREJhRncwek1ERXlNVFF3TWpRMU1EQmFNRll4Q3pBSkJnTlYKQkFZVEFsVlRNUk13RVFZRFZRUUlFd3BEWVd4cFptOXlibWxoTVJZd0ZBWURWUVFIRXcxVFlXNGdSbkpoYm1OcApjMk52TVJvd0dBWURWUVFEREJGQlpHMXBia0JsZUdGdGNHeGxMbU52YlRCWk1CTUdCeXFHU000OUFnRUdDQ3FHClNNNDlBd0VIQTBJQUJNOE5Ja0RmL3hDeXU2M0YwTSs3UnB0RXZLR0I1cHF5Rjcrazh1bzJsbDNZQmh0VmxOcEEKRXhxcDlVNUNWR3NjRy9jbFV2NExKaWV0ak92MXpaeVllMitqVFRCTE1BNEdBMVVkRHdFQi93UUVBd0lIZ0RBTQpCZ05WSFJNQkFmOEVBakFBTUNzR0ExVWRJd1FrTUNLQUlMUy9wOFAwa1R4Y3F5L0c0dGhySUtHeURBNTNvekVqCkgvcjRaRFlYbHlHb01Bb0dDQ3FHU000OUJBTUNBMGNBTUVRQ0lFWHVnNzViUldkMjFEdzR4ZlBrd1FxVUc1Sm0KM2pUYno2U21NcGozM2FSVkFpQkpGQTJHMmZ2MFBaTHl0Vmh0bDNMb0labHlTZmxxOTZ5MjA1V0EvTk8wV2c9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg=="
],
"crypto_config": {
"identity_identifier_hash_function": "SHA256",
"signature_hash_family": "SHA2"
},
"fabric_node_ous": null,
"intermediate_certs": [],
"name": "OrdererMSP",
"organizational_unit_identifiers": [],
"revocation_list": [],
"root_certs": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNQVENDQWVPZ0F3SUJBZ0lRVVJpbngwOS9ldkpsVzFCb0g3ZW4xakFLQmdncWhrak9QUVFEQWpCcE1Rc3cKQ1FZRFZRUUdFd0pWVXpFVE1CRUdBMVVFQ0JNS1EyRnNhV1p2Y201cFlURVdNQlFHQTFVRUJ4TU5VMkZ1SUVaeQpZVzVqYVhOamJ6RVVNQklHQTFVRUNoTUxaWGhoYlhCc1pTNWpiMjB4RnpBVkJnTlZCQU1URG1OaExtVjRZVzF3CmJHVXVZMjl0TUI0WERUSXdNVEl4TmpBeU5EVXdNRm9YRFRNd01USXhOREF5TkRVd01Gb3dhVEVMTUFrR0ExVUUKQmhNQ1ZWTXhFekFSQmdOVkJBZ1RDa05oYkdsbWIzSnVhV0V4RmpBVUJnTlZCQWNURFZOaGJpQkdjbUZ1WTJsegpZMjh4RkRBU0JnTlZCQW9UQzJWNFlXMXdiR1V1WTI5dE1SY3dGUVlEVlFRREV3NWpZUzVsZUdGdGNHeGxMbU52CmJUQlpNQk1HQnlxR1NNNDlBZ0VHQ0NxR1NNNDlBd0VIQTBJQUJJem1WYVl5cEtPSHdZTzNSZG1LbkpwUnFRMWoKMGpROHRoWXQxN2lma25QdnREQ0lLU2g1WlJ2YkhHRlpTNzRVK3VNRTdnRG9nelliRU5OYzhpY1Q1SU9qYlRCcgpNQTRHQTFVZER3RUIvd1FFQXdJQnBqQWRCZ05WSFNVRUZqQVVCZ2dyQmdFRkJRY0RBZ1lJS3dZQkJRVUhBd0V3CkR3WURWUjBUQVFIL0JBVXdBd0VCL3pBcEJnTlZIUTRFSWdRZ3RMK253L1NSUEZ5ckw4YmkyR3Nnb2JJTURuZWoKTVNNZit2aGtOaGVYSWFnd0NnWUlLb1pJemowRUF3SURTQUF3UlFJaEFLSEp2STVpclg4LzdRVHd1Z2szMWxPTApnSWVuRGZ1TSsxTERyemhYWUo3RkFpQjFmUXd2dkZENlVoWUdHUE1BWktOeSs4b0Vhc1BBcmdsUUNITEdmczN4Ck1RPT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo="
],
"signing_identity": null,
"tls_intermediate_certs": [],
"tls_root_certs": [
"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNRekNDQWVxZ0F3SUJBZ0lSQUl1aGZFZWNidnF1SXY5b2FXeEdrdE13Q2dZSUtvWkl6ajBFQXdJd2JERUwKTUFrR0ExVUVCaE1DVlZNeEV6QVJCZ05WQkFnVENrTmhiR2xtYjNKdWFXRXhGakFVQmdOVkJBY1REVk5oYmlCRwpjbUZ1WTJselkyOHhGREFTQmdOVkJBb1RDMlY0WVcxd2JHVXVZMjl0TVJvd0dBWURWUVFERXhGMGJITmpZUzVsCmVHRnRjR3hsTG1OdmJUQWVGdzB5TURFeU1UWXdNalExTURCYUZ3MHpNREV5TVRRd01qUTFNREJhTUd3eEN6QUoKQmdOVkJBWVRBbFZUTVJNd0VRWURWUVFJRXdwRFlXeHBabTl5Ym1saE1SWXdGQVlEVlFRSEV3MVRZVzRnUm5KaApibU5wYzJOdk1SUXdFZ1lEVlFRS0V3dGxlR0Z0Y0d4bExtTnZiVEVhTUJnR0ExVUVBeE1SZEd4elkyRXVaWGhoCmJYQnNaUzVqYjIwd1dUQVRCZ2NxaGtqT1BRSUJCZ2dxaGtqT1BRTUJCd05DQUFSNnZkaGQvWW1xVG5TeFZlc2YKV0IzMGwwU29MWlNubUYyNWpIL0lFWkdTTkJLc21zNGsyTTdBaVhOWUc1T0MvR2cvYlhaSGlpL3l2cldZaWxsOQowdVg2bzIwd2F6QU9CZ05WSFE4QkFmOEVCQU1DQWFZd0hRWURWUjBsQkJZd0ZBWUlLd1lCQlFVSEF3SUdDQ3NHCkFRVUZCd01CTUE4R0ExVWRFd0VCL3dRRk1BTUJBZjh3S1FZRFZSME9CQ0lFSU9mcUpISzB1MzNSWTFGVFRoc0YKanEwa0xTS3YzNFBmbFlFYmJaV3FSNGpyTUFvR0NDcUdTTTQ5QkFNQ0EwY0FNRVFDSUFSTEdFYzZuT0lwb2g5MApGWnROcEdLWC9hSjZ2NlZBeEdJVkZFaGU0YTUzQWlCQXkwY050ZEV5cWFYVklrMitqZ1RvOTBWanBkMWduSGRWCi9yMXVRbVhBQ1E9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg=="
]
},
"type": 0
},
"version": "0"
}
},
"version": "0"
}
},
"mod_policy": "Admins",
"policies": {
"Admins": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "MAJORITY",
"sub_policy": "Admins"
}
},
"version": "0"
},
"BlockValidation": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Writers"
}
},
"version": "0"
},
"Readers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Readers"
}
},
"version": "0"
},
"Writers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Writers"
}
},
"version": "0"
}
},
"values": {
"BatchSize": {
"mod_policy": "Admins",
"value": {
"absolute_max_bytes": 102760448,
"max_message_count": 10,
"preferred_max_bytes": 524288
},
"version": "0"
},
"BatchTimeout": {
"mod_policy": "Admins",
"value": {
"timeout": "2s"
},
"version": "0"
},
"ChannelRestrictions": {
"mod_policy": "Admins",
"value": null,
"version": "0"
},
"ConsensusType": {
"mod_policy": "Admins",
"value": {
"metadata": null,
"state": "STATE_NORMAL",
"type": "solo"
},
"version": "0"
}
},
"version": "0"
}
},
"mod_policy": "",
"policies": {
"Admins": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "MAJORITY",
"sub_policy": "Admins"
}
},
"version": "0"
},
"Readers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Readers"
}
},
"version": "0"
},
"Writers": {
"mod_policy": "Admins",
"policy": {
"type": 3,
"value": {
"rule": "ANY",
"sub_policy": "Writers"
}
},
"version": "0"
}
},
"values": {
"BlockDataHashingStructure": {
"mod_policy": "Admins",
"value": {
"width": 4294967295
},
"version": "0"
},
"Consortium": {
"mod_policy": "Admins",
"value": {
"name": "SampleConsortium"
},
"version": "0"
},
"HashingAlgorithm": {
"mod_policy": "Admins",
"value": {
"name": "SHA256"
},
"version": "0"
},
"OrdererAddresses": {
"mod_policy": "/Channel/Orderer/Admins",
"value": {
"addresses": [
"orderer.example.com:7050"
]
},
"version": "0"
}
},
"version": "0"
},
"sequence": "1"
}
执行下面的命令完成添加组织的动作:
1 configtxlator proto_encode --input config.json --type common.Config >original_config.pb 2 configtxlator proto_encode --input updated_config.json --type common.Config >modified_config.pb 3 configtxlator compute_update --channel_id mychannel --original original_config.pb --updated modified_config.pb >config_update.pb 4 configtxlator proto_decode --input config_update.pb --type common.ConfigUpdate >config_update.json 5 echo '{"payload":{"header":{"channel_header":{"channel_id":"'mychannel'", "type":2}},"data":{"config_update":'$(cat config_update.json)'}}}' | jq . >config_update_in_envelope.json 6 configtxlator proto_encode --input config_update_in_envelope.json --type common.Envelope >"org1_update_in_envelope.pb"
签名并提交:
1 peer channel signconfigtx -f org1_update_in_envelope.pb -o orderer.example.com:7050 2 peer channel update -f org1_update_in_envelope.pb -c mychannel -o orderer.example.com:7050 --ordererTLSHostnameOverride orderer.example.com
完成后将peer0.org1加入通道当中:
1 peer channel join -b mychannel.block
退出cli。
八,创建org1的新用户:
org1管理员登录CA 中心
export FABRIC_CA_CLIENT_HOME=$CA_USER_HOME/admin fabric-ca-client enroll -u http://admin:adminpw@localhost:7054
注册新用户:
1 fabric-ca-client register --id.name usertest --id.affiliation org1.department1 2 fabric-ca-client enroll -u http://usertest:iyFKvrdKZwQb@localhost:7054 -M /usr/local/gopath/src/github.com/hyperledger/fabric/network006/causers/usertest
此时生成了用户的msp信息
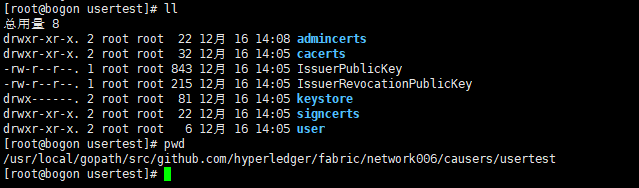
由于此信息中缺少了admincerts文件夹,我们将signcerts文件夹复制并改名为admincerts文件夹
1 cp -r ./signcerts ./admincerts
并将所有信息拷贝到目录/usr/local/gopath/src/github.com/hyperledger/fabric/network006/crypto-config/peerOrganizations/org1.example.com/users/usertest/msp/ 中,无此目录需要新建。还有一种不用拷贝的操作,只要在新用户enroll时将目录制定的crypto-config下的一个目录中即可,但是还是的做signcerts 拷贝到admincerts的动作。
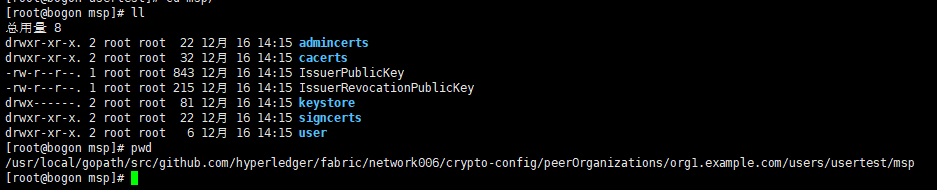
至此我们的用户创建完成
下面我们来安装链码并尝试用不同的用户去调用它
我们还是以官方的chaincode_example02为例
将chaincode_example02.go文件拷贝至/usr/local/gopath/src/github.com/hyperledger/fabric/network006/chaincode/go/chaincode_example02
登录cli,此时的用户是admin用户。
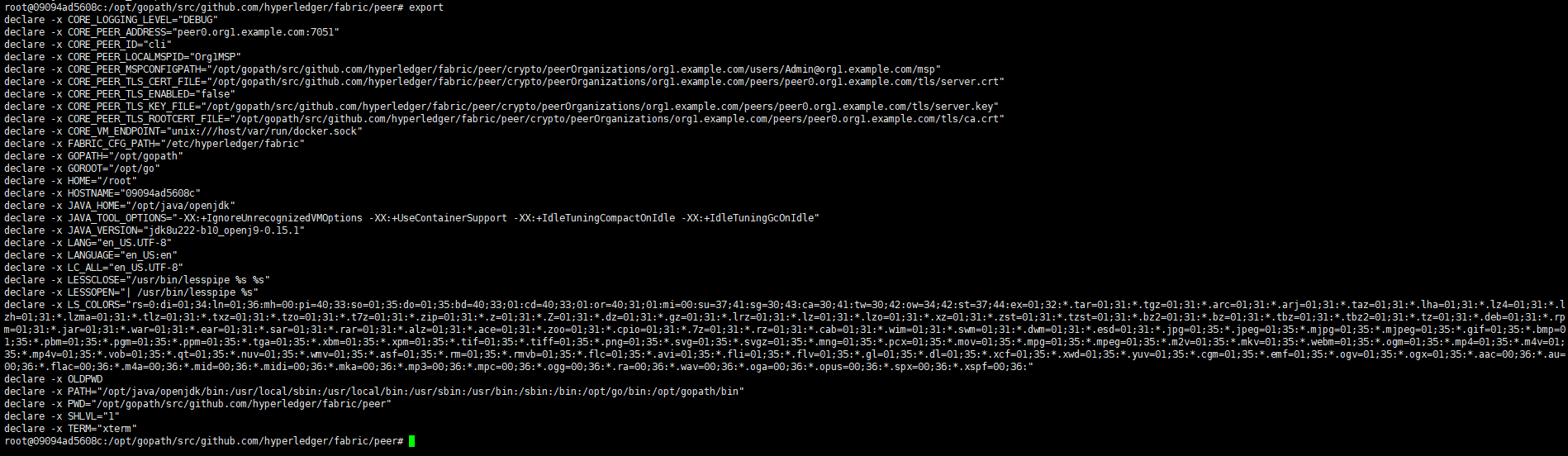
安装及实例化链码:
1 peer chaincode install -n mycc -p github.com/hyperledger/fabric/network006/chaincode/go/chaincode_example02 -v 1.0 2 peer chaincode instantiate -o orderer.example.com:7050 -C mychannel -n mycc -v 1.0 -c '{"Args":["init","a","100","b","200"]}' -P "OR ('Org1MSP.member')"
完成后尝试调用:
1 peer chaincode query -C mychannel -n mycc -c '{"Args":["query","a"]}'
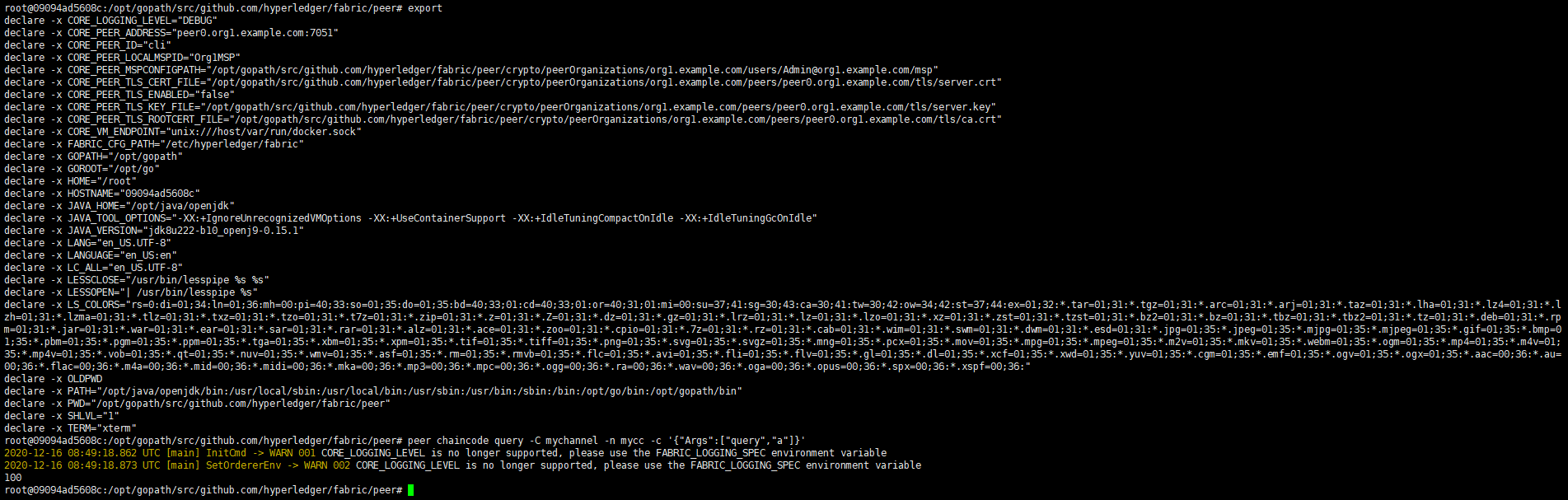
现在我们切换另外的用户usertest去调用这个链码看看是否可以成功:
export CORE_PEER_MSPCONFIGPATH="/opt/gopath/src/github.com/hyperledger/fabric/peer/crypto/peerOrganizations/org1.example.com/users/usertest/msp" peer chaincode query -C mychannel -n mycc -c '{"Args":["query","a"]}'
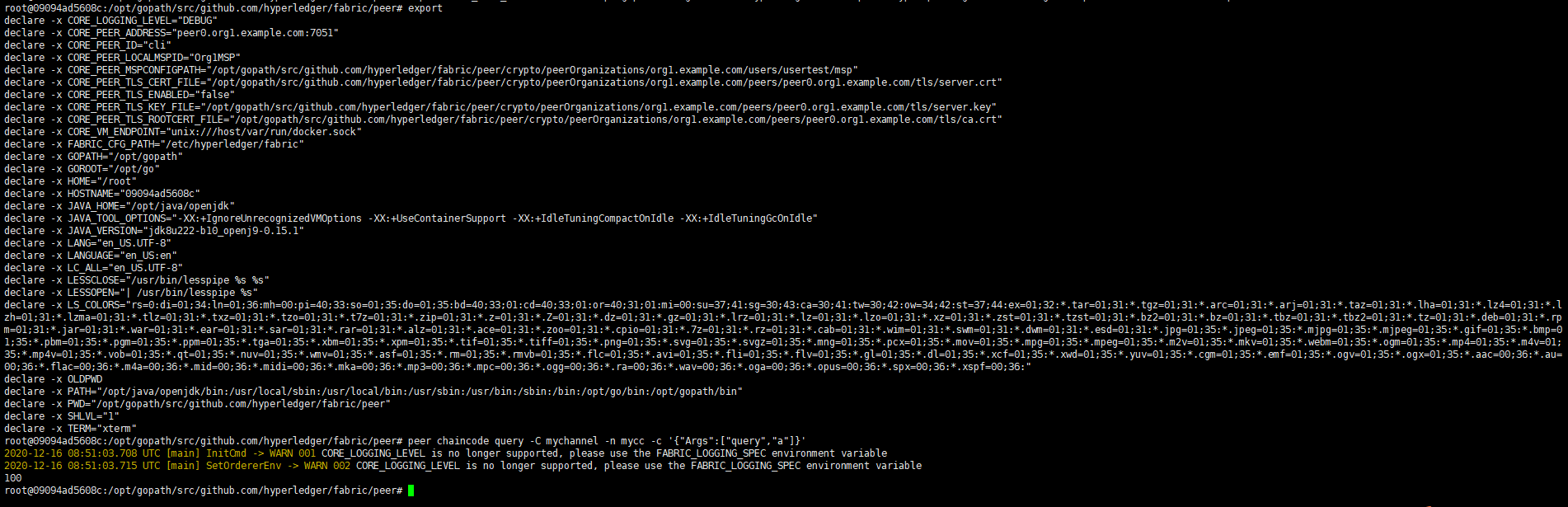
至此我们看到也调用成功,现在我们已经成功的为组织加入了用户。
注意:请留意红色的字体和细细揣摩他。
最后,谢谢大家阅读,欢迎下方留言讨论。
FABRIC_CA_SERVER_TLS_CERTFILE




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列:基于图像分类模型对图像进行分类
· go语言实现终端里的倒计时
· 如何编写易于单元测试的代码
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 零经验选手,Compose 一天开发一款小游戏!
· 一起来玩mcp_server_sqlite,让AI帮你做增删改查!!