Containerlab(转载)
Containerlab
什么是 Containerlab
随着容器化网络操作系统数量的不断增加,在用户定义的多功能实验室拓扑中轻松运行它们的需求也不断增长。
不幸的是,像 docker-compose 这样的容器编排工具不太适合这个目的,因为它们不允许用户在定义拓扑的容器之间轻松创建连接。
Containerlab 提供了一个 CLI,用于编排和管理基于容器的网络实验室。它启动容器,在容器之间构建虚拟线路,以创建用户选择的实验室拓扑并管理实验室生命周期。
快速开始
安装
获取Containerlab 非常简单。由于安装过程简单,它可以在任何基于 RHEL 或 Debian 的系统上在几秒钟内完成设置。
# download and install the latest release (may require sudo)
bash -c "$(curl -sL https://get.containerlab.dev)"
网络拓扑文件
# srlceos01.clab.yml
name: srlceos01
topology:
nodes:
srl:
kind: nokia_srlinux
image: ghcr.io/nokia/srlinux
ceos:
kind: ceos
image: ceos:4.32.0F
links:
- endpoints: ["srl:e1-1", "ceos:eth1"]
此拓扑会启动两个节点,并使用单个点对点接口相互互连节点
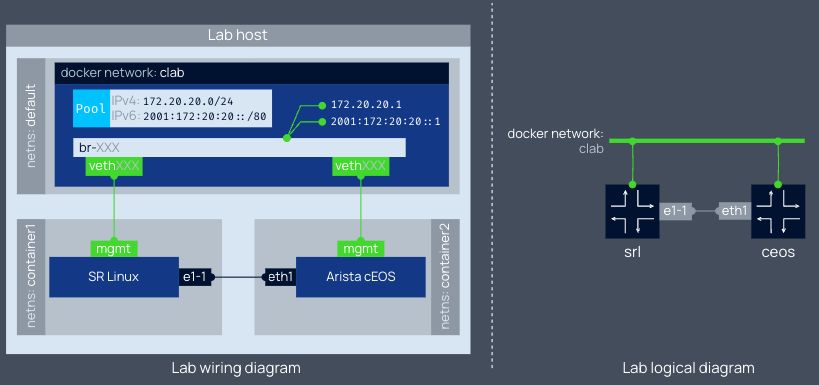
网络拓扑文件属性
- name: 拓扑必须有一个与其关联的名称。该名称用于区分一种拓扑与另一种拓扑,以允许在同一主机上部署多个拓扑而不会发生冲突。
- topology: 拓扑定义中的拓扑对象是该文件的核心元素。在拓扑元素下,您将找到拓扑的所有主要构建块,例如节点、类型、默认值和链接。
- nodes: 与所有其他拓扑一样,节点位于事物的中心。通过节点,我们可以定义要运行哪些实验室元素、以什么配置和风格运行。
- kind: kind 属性选择该节点属于哪种类型。种类本质上是告诉容器实验室如何考虑节点的特定风格来处理节点属性的一种方式。
- image: 公共镜像属性设置将用于启动节点的容器镜像名称。
- 更多
- links: 将节点互连以形成拓扑。 Containerlab 的目的之一是让节点的互连变得简单。
- nodes: 与所有其他拓扑一样,节点位于事物的中心。通过节点,我们可以定义要运行哪些实验室元素、以什么配置和风格运行。
部署服务
# checking that topology file is present in ~/clab-quickstart
❯ ls
srlceos01.clab.yml
# checking that container images are available
❯ docker images | grep -E "srlinux|ceos"
REPOSITORY TAG IMAGE ID CREATED SIZE
ceos 4.32.0F 40d39e1a92c2 24 hours ago 2.4GB
ghcr.io/nokia/srlinux latest b4daaa73edd1 4 weeks ago 2.73GB
# start the lab deployment
❯ clab deploy -t srlceos01.clab.yml
几秒钟后,您将看到已部署节点的摘要:
+---+---------------------+--------------+-----------------------+------+-------+---------+----------------+----------------------+
| # | Name | Container ID | Image | Kind | Group | State | IPv4 Address | IPv6 Address |
+---+---------------------+--------------+-----------------------+------+-------+---------+----------------+----------------------+
| 1 | clab-srlceos01-ceos | 2e2e04a42cea | ceos:4.32.0F | ceos | | running | 172.20.20.3/24 | 2001:172:20:20::3/80 |
| 2 | clab-srlceos01-srl | 1b9568fcdb01 | ghcr.io/nokia/srlinux | srl | | running | 172.20.20.4/24 | 2001:172:20:20::4/80 |
+---+---------------------+--------------+-----------------------+------+-------+---------+----------------+----------------------+
销毁服务
❯ clab destroy -t srlceos01.clab.yml
模拟交换
使用
Containerlab模拟二层交换机功能
拓扑
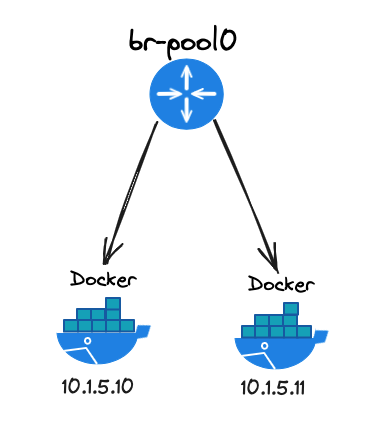
网桥配置
brctl addbr br-pool0
ip l s br-pool0 up
网络拓扑文件
# bridge.clab.yml
name: bridge
topology:
nodes:
br-pool0:
kind: bridge
server1:
kind: linux
image: harbor.dayuan1997.com/devops/nettool:0.9
exec:
- ip addr add 10.1.5.10/24 dev net0
server2:
kind: linux
image: harbor.dayuan1997.com/devops/nettool:0.9
exec:
- ip addr add 10.1.5.11/24 dev net0
links:
- endpoints: ["br-pool0:eth1", "server1:net0"]
- endpoints: ["br-pool0:eth2", "server2:net0"]
此拓扑会启动两个节点和一个网桥,两个节点的 net0 网卡和网桥进行连接,使用网桥二层功能进行数据交换
部署服务
# 部署网桥
> brctl addbr br-pool0
> ip l s br-pool0 up
# 检查配置文件
❯ ls
bridge.clab.yml
# 部署服务
❯ clab deploy -t bridge.clab.yml
几秒钟后,您将看到已部署节点的摘要:
INFO[0000] Containerlab v0.54.2 started
INFO[0000] Parsing & checking topology file: clab.yaml
INFO[0000] Creating lab directory: /root/wcni-kind/network/4-basic-netwotk/2-ip/1-bridge/clab-bridge
INFO[0000] Creating container: "server1"
INFO[0000] Creating container: "server2"
INFO[0000] Created link: br-pool0:eth1 <--> server1:net0
INFO[0000] Created link: br-pool0:eth2 <--> server2:net0
INFO[0001] Executed command "ip addr add 10.1.5.10/24 dev net0" on the node "server1". stdout:
INFO[0001] Executed command "ip addr add 10.1.5.11/24 dev net0" on the node "server2". stdout:
INFO[0001] Adding containerlab host entries to /etc/hosts file
INFO[0001] Adding ssh config for containerlab nodes
INFO[0001] 🎉 New containerlab version 0.55.0 is available! Release notes: https://containerlab.dev/rn/0.55/
Run 'containerlab version upgrade' to upgrade or go check other installation options at https://containerlab.dev/install/
+---+---------------------+--------------+------------------------------------------+-------+---------+----------------+----------------------+
| # | Name | Container ID | Image | Kind | State | IPv4 Address | IPv6 Address |
+---+---------------------+--------------+------------------------------------------+-------+---------+----------------+----------------------+
| 1 | clab-bridge-server1 | ba326af1a15e | harbor.dayuan1997.com/devops/nettool:0.9 | linux | running | 172.20.20.3/24 | 2001:172:20:20::3/64 |
| 2 | clab-bridge-server2 | bdd8706ca02d | harbor.dayuan1997.com/devops/nettool:0.9 | linux | running | 172.20.20.2/24 | 2001:172:20:20::2/64 |
+---+---------------------+--------------+------------------------------------------+-------+---------+----------------+----------------------+
测试服务
- 查看
ip信息
❯ lo clab-bridge-server1 ip a l
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
8: net0@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9500 qdisc noqueue state UP group default
link/ether aa:c1:ab:c5:ab:3c brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 10.1.5.10/24 scope global net0
valid_lft forever preferred_lft forever
inet6 fe80::a8c1:abff:fec5:ab3c/64 scope link
valid_lft forever preferred_lft forever
14: eth0@if15: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:14:14:03 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 172.20.20.3/24 brd 172.20.20.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 2001:172:20:20::3/64 scope global nodad
valid_lft forever preferred_lft forever
inet6 fe80::42:acff:fe14:1403/64 scope link
valid_lft forever preferred_lft forever
- 测试数据
> lo clab-bridge-server1 ping 10.1.5.11
PING 10.1.5.11 (10.1.5.11): 56 data bytes
64 bytes from 10.1.5.11: seq=0 ttl=64 time=0.075 ms
64 bytes from 10.1.5.11: seq=1 ttl=64 time=0.086 ms
64 bytes from 10.1.5.11: seq=2 ttl=64 time=0.164 ms
64 bytes from 10.1.5.11: seq=3 ttl=64 time=0.127 ms
^C
--- 10.1.5.11 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 0.075/0.113/0.164 ms
通过
ttl值可以判断通过二层交换机进行了数据交换,通过路由模式,ttl会自动减1
- 抓包信息
server2~$tcpdump -pne -i net0
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on net0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
03:17:55.849474 aa:c1:ab:c5:ab:3c > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 10.1.5.11 tell 10.1.5.10, length 28
03:17:55.849487 aa:c1:ab:23:a5:d1 > aa:c1:ab:c5:ab:3c, ethertype ARP (0x0806), length 42: Reply 10.1.5.11 is-at aa:c1:ab:23:a5:d1, length 28
03:17:55.849505 aa:c1:ab:c5:ab:3c > aa:c1:ab:23:a5:d1, ethertype IPv4 (0x0800), length 98: 10.1.5.10 > 10.1.5.11: ICMP echo request, id 69, seq 0, length 64
03:17:55.849517 aa:c1:ab:23:a5:d1 > aa:c1:ab:c5:ab:3c, ethertype IPv4 (0x0800), length 98: 10.1.5.11 > 10.1.5.10: ICMP echo reply, id 69, seq 0, length 64
销毁服务
❯ clab destroy -t bridge.clab.yml
转载文档
https://containerlab.dev/manual/topo-def-file/#kinds


 浙公网安备 33010602011771号
浙公网安备 33010602011771号